Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.
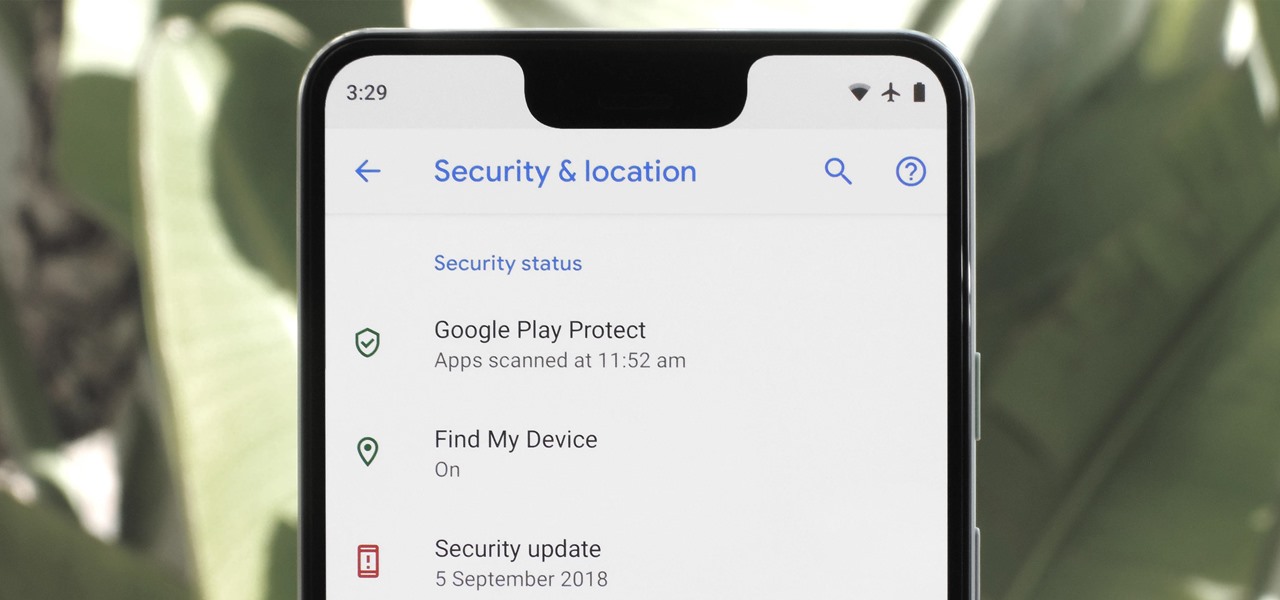
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

One of the best things about Android is the ability to customize your phone to your liking. From changing the layout of icons to finding the perfect wallpaper to reflect your current mood, there's a wide range of tools to make your phone yours.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

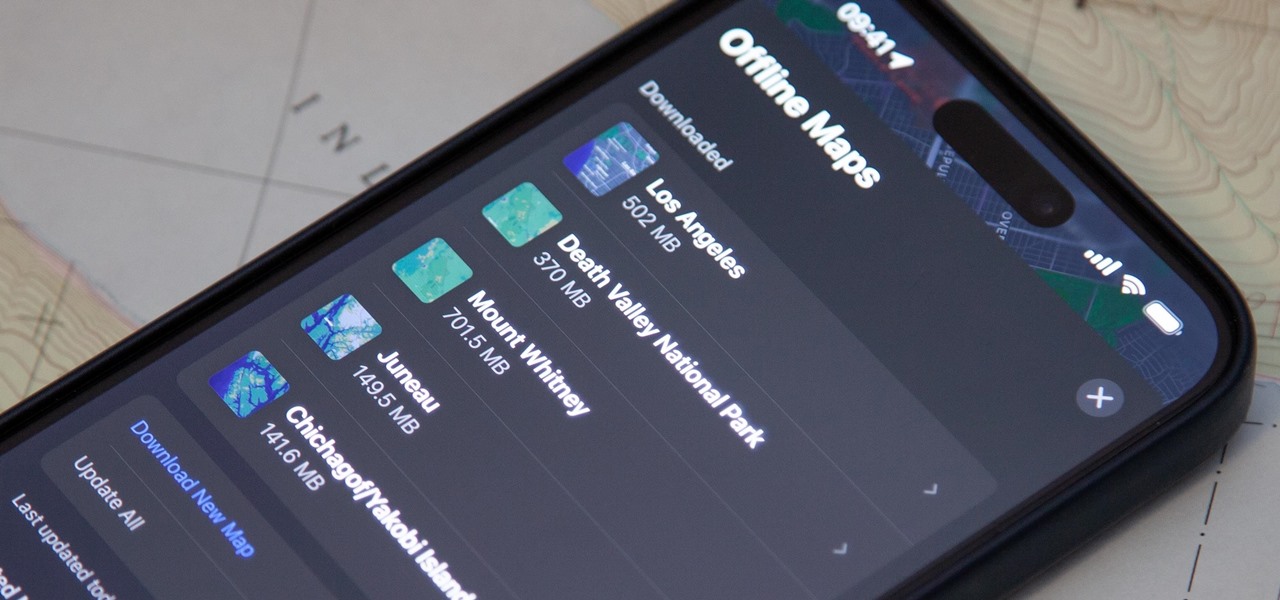
Offline maps help you get around an unfamiliar area whenever you anticipate encountering bad cellular reception and no internet connectivity. Google Maps and other map apps have had offline maps for a while now. But Apple Maps only had a little-known caching workaround to produce something even remotely similar to full offline maps — until now.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

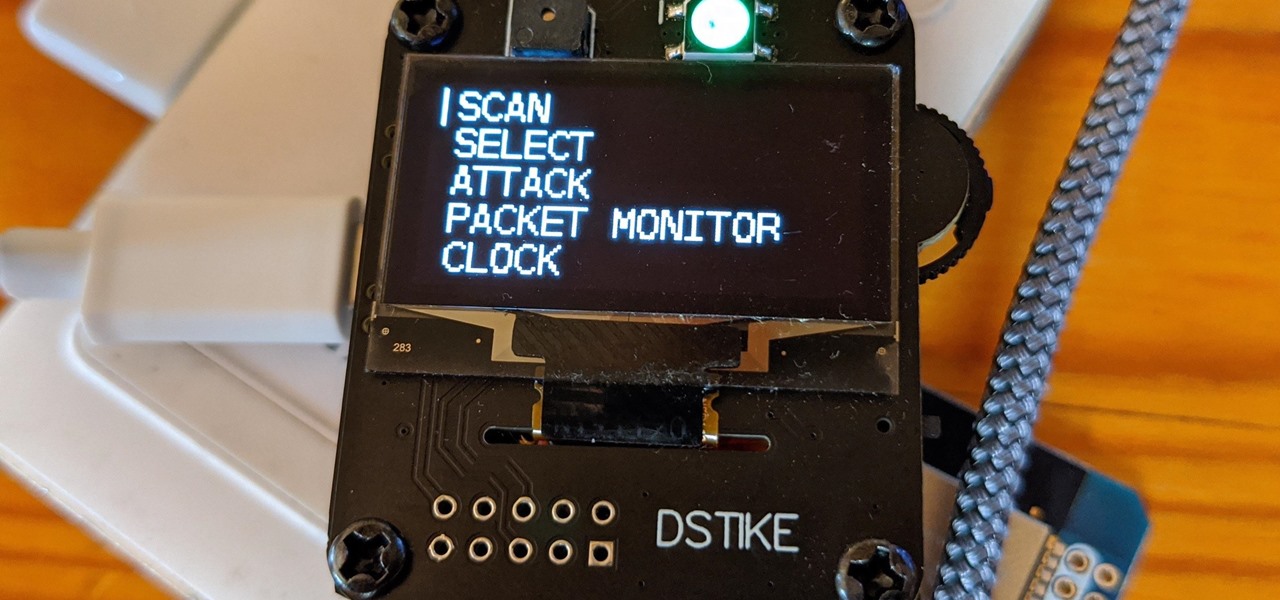
The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting things that the Wi-Fi Deauther can do without plugging it into a device.

Even though the Music app took a backseat during Apple's initial iOS 14 announcements, there's a lot going on in the updated app. Some of the new features and changes apply only to Apple Music subscribers, while others apply to your own music library, so there's something for everyone.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Feel beautiful from the inside out with targeted exercises, like these exercises for your feet. This how-to video has a few simple exercises that will strengthen your toes and relieve some foot discomfort. Keep your feet in good shape so you can wear those high heeled shoes all night.

This workout video gives an exercise for you butt or gluteus muscles to tone and strengthen them. Most weight-bearing leg exercises will work out your gluteus muscles to a degree. The same is true with various gym classes, running, rollerblading and ice skating. You can decide to omit targeted exercises for your gluteus muscles from your regular workouts entirely, but it’s good to stretch (particularly if you have a day job which requires sitting on a chair), to strengthen and to tone this mu...

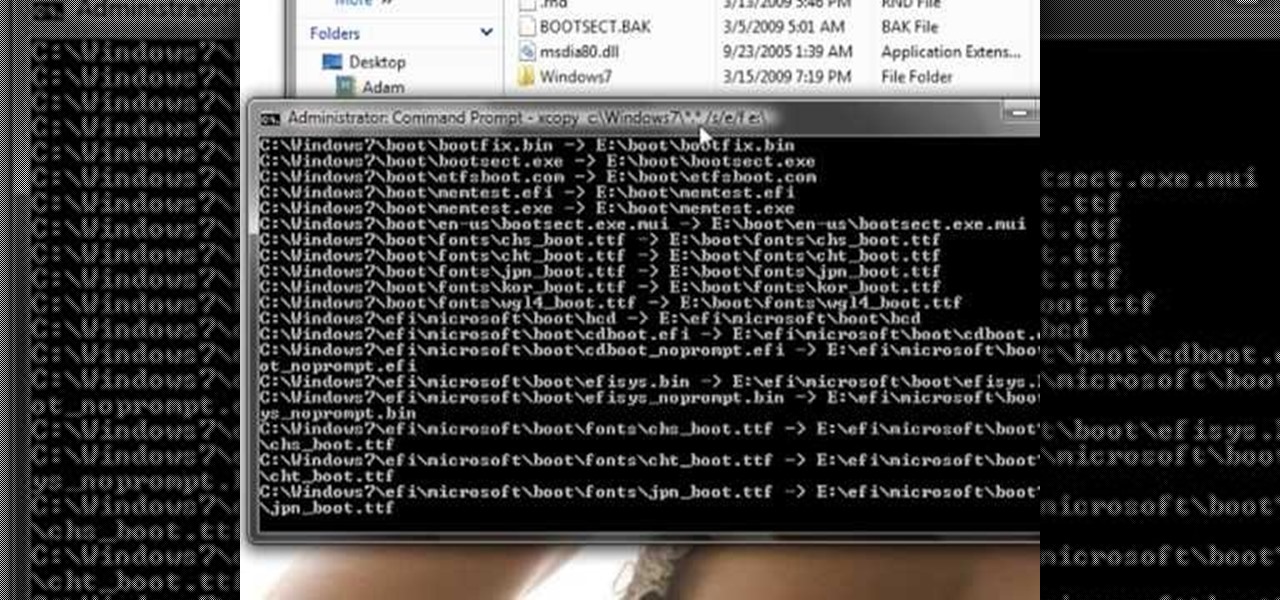
This guide works 100% for Vista & Windows 7, unlike most of the guides out there. The method is very simple and hassle free. Needless to say, your motherboard should support USB Boot feature to make use of the bootable USB drive.

AdSense. It's a beautiful thing, isn't it? Google AdSense is something every website owner or blogger should use… it's what every blog needs… if you plan on making any money and surviving. So, how much traffic do you need to actually start making money via AdSense? This video will try and answer that question for you. You must have targeted traffic to drive your blog.

Tired of seeing all of those ads in your browser? The flashing ones make for a terrible browsing experience, and those rollover ones are just downright annoying. If you don't want to be bothered by them again, you've got a few choices, depending on what web browser you're using.

Moving a 2000 pound safe isn't easy... I was working as manager for a construction company that was performing an up fit on a century old building in downtown Concord, N.C. The owners wanted us to move a two thousand pound (that's a ton!) safe up to the second story so that it could be displayed in their new office. The safe was located between the first and second floors in a small office that was used for accounting purposes in the old days when said building had been a hardware store.

This video will show you how to give a quick and easy massage targeted at the neck and shoulder. No experience required; the movie will show you how to do everything. Learn how to help your family and friends relieve stress! Give neck and shoulder massages.

This video introduces the concept of symbols and instances in Flash. It shows you that symbols are objects that can be reused as instances, and targeted with ActionScript code. The tutorial shows you the difference between graphic, movie clip, and button symbols, and how to modify both symbols and instances in different ways. Create and use symbols and instances in Flash CS3 Pro.
DARPA is at it again. This time, the Defense Advanced Research Projects Agency has announced plans to create nanochips for monitoring troops health on the battlefield.

In a recent address, Obama supports drone attacks against people 'on the list'. He talks about the people on the list being known of 'going to attack Americans', and who have a 'track record of terrorism'. Let me tell you, targeted strikes will, 90% of the time, have civilian casualties. There is no such thing as a clean strike. But I'll let you decide.
Type: Digital, Landscapes Theme: Incredible Landscapes, "Beyond the Mundane"
Type: Digital, avian Theme: Bird portraits, "The Avian Persona", wild or in captivity

In a recent survey of more than 5000 UK jobseekers by TotalJobs.com, it was found that 60% spend less than two hours working on each application following a job search, all inclusive of the time it takes to write a CV and covering letter, and to prepare for an interview.

This quick 3D modeling software tutorial explains how to bake a normal map in modo 301. Learn how to bake a normal map mesh to mesh using high-res meshes targeted to a low res mesh in modo 301. Bake a normal map.

Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut down some of the games that offer web users a giant share of their online fun. World of Warcraft, League of Legends, EVE Online, and Bethesda Softworks have all been targeted by LulzSec's hacking efforts in the last week,...

More than 100 missions targeted at Earth's moon have been launched by space explorers since the late-1950s. NASA landed a total of 12 men on the lunar surface, collecting more than 800 pounds of moon rocks and lunar soil samples. But still, the moon remains a mystery, especially its formation. NASA's new mission aims to find out exactly how the moon came to be with the Gravity Recovery and Interior Laboratory, or GRAIL, part of NASA's Discovery Program.
One of the most effective ways to sift out weak programs is to do market research. Take some time to study the market you are interested in by reading reports, reviews, and market studies. This should help you to determine whether or not the particular affiliate products or services you will be campaigning for is actually worth your time. A successful affiliate marketing program will be targeted at a broad population while offering products or services that are highly in demand or exclusive. ...
Water Purification Device Prompts TSA to Close Down Minneapolis Airport In another stupendous incident of comical over-reaction, the TSA ordered the evacuation of two airport terminals in Minneapolis after a water purification device was found in a woman’s luggage.