
News: International Sanctions
Due to the recent developments in Iran and the westernized world, I would like to talk a little about sanctions. There are several kinds of sanctions:


Due to the recent developments in Iran and the westernized world, I would like to talk a little about sanctions. There are several kinds of sanctions:
The niches are the foundation of a successful marketing strategy. You need to focus on the niches in a market and develop a strategy for each niche. You'll attract more targeted traffic that way, which will result in more sales.

Finally! Gardening! Many have been waiting for ages for this invention to come true, and now it has! Come experience it for yourselves in the Test Realm (instructions on getting there will be added)! When you enter, go the Moolinda Wu and she will teach you how to start gardening. Easy as that! You can plant many things, and monsters drop seeds, too. You can plant indoors or outdoors. Garden now on the Test Realm!Here's the complete article Professor Moolinda Wu wrote:

The future of technology promises more and more seamless daily interactions. Pee on your phone, test for STDS. Or perhaps more widely appealing, ditch your wallet for all-in-one easy mobility.

How many gallons of gas does it take to get from Kansas City to New York? Depends on what you're driving. In this custom-modded Indy race car designed by students at the DeLaSalle Education Center? About four.

Do you know your constitutional rights if stopped by the police? Washington Post recently ran an interesting article on "10 Rules", a docudrama produced by the D.C. nonprofit Flex Your Rights.

The gluteal muscles, or glutes, can be targeted with donkey kicks. This exercise is easy to perform and does not require any fancy equipment. The donkey kick is a classic "butt" exercise, and there are many variations of the original donkey kick. Instructions for the donkey kick exercise are listed below:
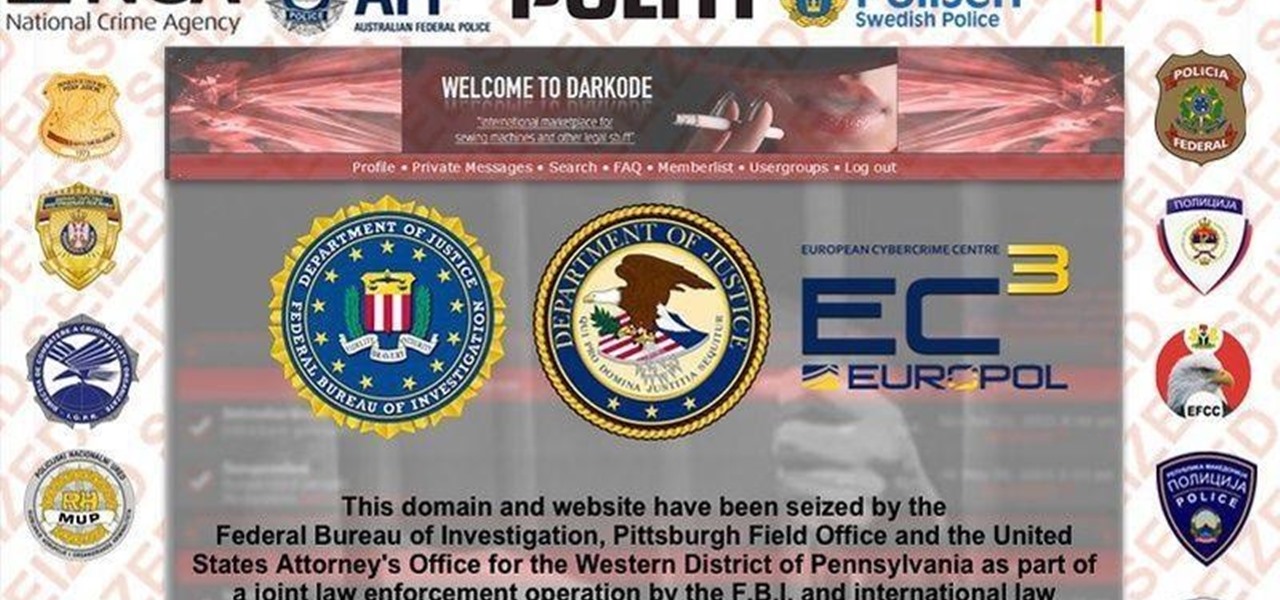
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

On October 7th, the IndieCade Conference will open its doors to some of the most innovative minds in the independent gaming industry. The three day event located in Culver City, California includes presentations by notable indie designers, workshops, galleries, and mixers. On the following day, however, the IndieCade Festival begins. Unlike the conference, the festival includes events targeted at gamers and the general public. While a $15 wristband will grant you access to keynotes, events, a...

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...
This article describes the very basics of compiling a program on Linux. It is targeted at the absolute beginner. Sometimes beginners search for programs on the web for their Linux systems, and is faced with the reality that they have to compile the program themselves, either because there exists no binary for their architecture, or the author of the program just doesn't release any binaries at all, but only sources.

The Fake Adult Website Prank is an incredible trick if you happen to have the necessary access and work in the internet industry. Luckily, I had both.

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

Optional sections to add to your resume can help fill in the gap where needed and enhance the skills and proficiencies already listed on your resume. Completion of this how to video will discuss the optional resume sections such as profile, technical skills, certifications, awards, memberships and community involvement. Make your own amazing resume today.

In this article I am going to take a look at the Google keyword tool, which is one of many keyword tool programs that you can use to find your keywords.

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

The Xbox 360 is America's video game system. It was designed in America, it has better market share in America than anywhere else, and it has the most overtly macho game catalog of any console. For many Xbox fanboys, gaming heaven is shooting hordes of really well-animated things in the most intuitive way possible. Trouble Witches NEO - Episode 1: Daughters of Amalgam, released last week on Xbox Live Arcade (XBLA) for $10 by Japanese developer Adventure Planning Service, is a typical Xbox 360...
Proposition 22 Prohibits the state from borrowing or taking funds used for transportation, redevelopment, or local, government projects and services. Initiative constitution amendment.

Uh oh. Somebody screwed up big this time. It has recently been reported that Iraqi insurgents have used $26 software to intercept live video feeds from U.S. drones located in Middle East conflict zones. The drone (a remotely piloted aircraft) is considered one of the U.S. military's most sophisticated weapons. Apparently not sophisticated enough, however.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not have been aware of before.

ACTION MOVIES The Hunger Games (2012)
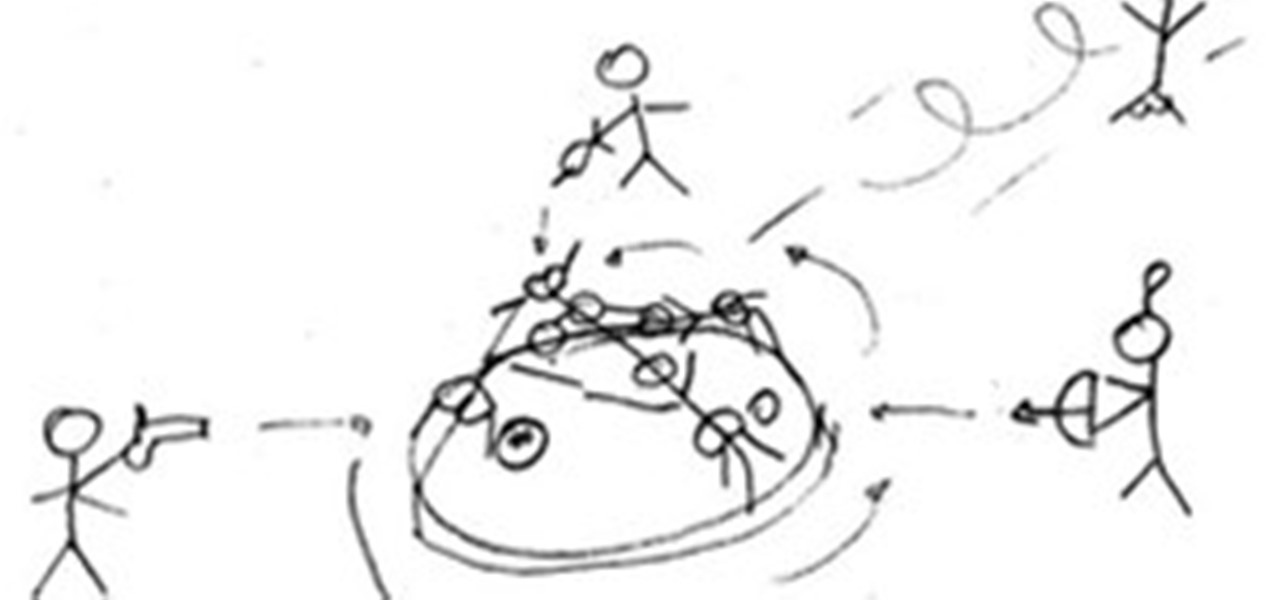
It is a game that includes a children's play wheel, paint guns, bows, arrows and darts. At the wheel will be spinning the participants with the ass in the air, every ass has a punctuation recorded and will be targeted with an air gun, dart or arrow. Each buttock punctuation will have a 100, 500 and the dimple will be maximum of 1000 points punctuation every 8 seconds and increase the speed of the wheel, so to complete the minutes or 10000-pointers in the asses of the participants or until you...

Step 1. Have the victims of the prank just engaging in a normal everyday activity such as going out to eat at a restraunt or whatever.