Ever wish there were a way to upload a video to YouTube without making it available to anyone with an Internet connection? While you might know about the option to make your uploaded clips private, limiting their viewing to 25 users of your choosing, you might not know about the newly introduced "Unlisted" status, which allows your videos to be viewed by only those people who know the video's direct URL. For more information, watch this free video guide from Tekzilla.

John Park poses a kitty conundrum: Who's going to feed the cat while you're on vacation? Using a motor from an old VCR, he creates an automated feline feeder. While building this Make: magazine project, John learned that newer VCRs have safeguard technology, limiting access to the motor. Watch John as he demonstrates his solutions to this challenge.

Selene Yeager takes you through an interval cycling workout called 3-2-1 for hill surges. The format of the workout is to do repeated hard short bursts with increasing intensity. This type of workout will help when you're biking up hills or trying to overcome your limits.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

The Galaxy S20's Wireless PowerShare is a must-use feature. With even the base model packing a 4,000 mAh battery, you have more than enough juice for all your Qi-enabled devices. The default settings make it so that in certain situations, you may have to choose between your phone or wireless earbuds, but you can change that.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

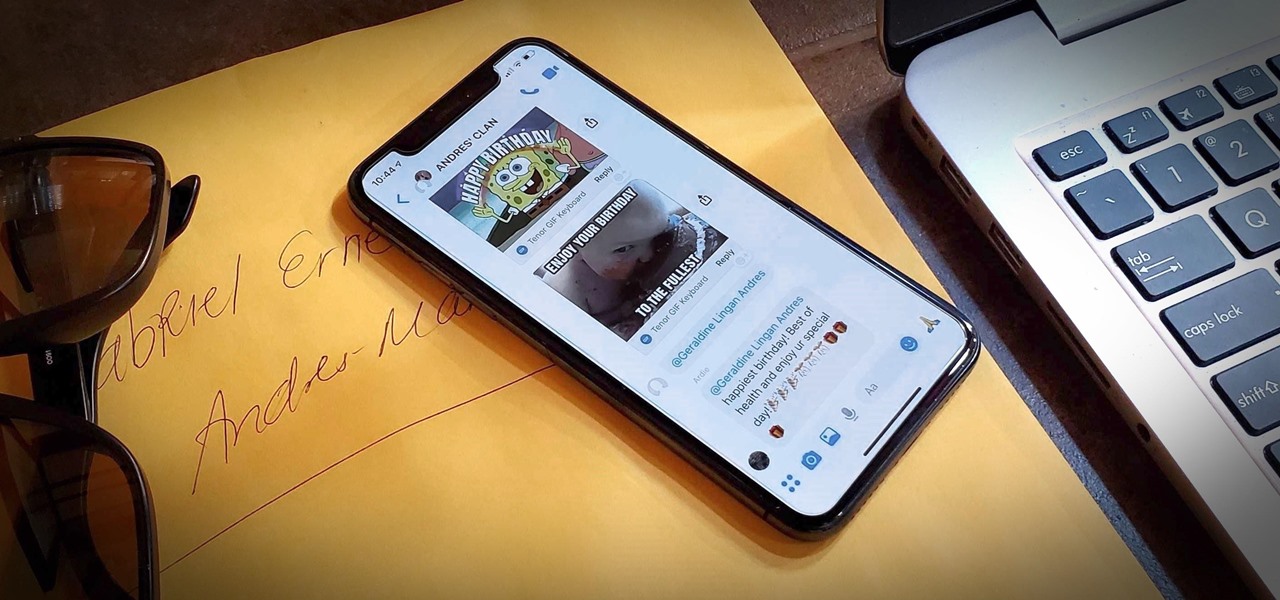
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

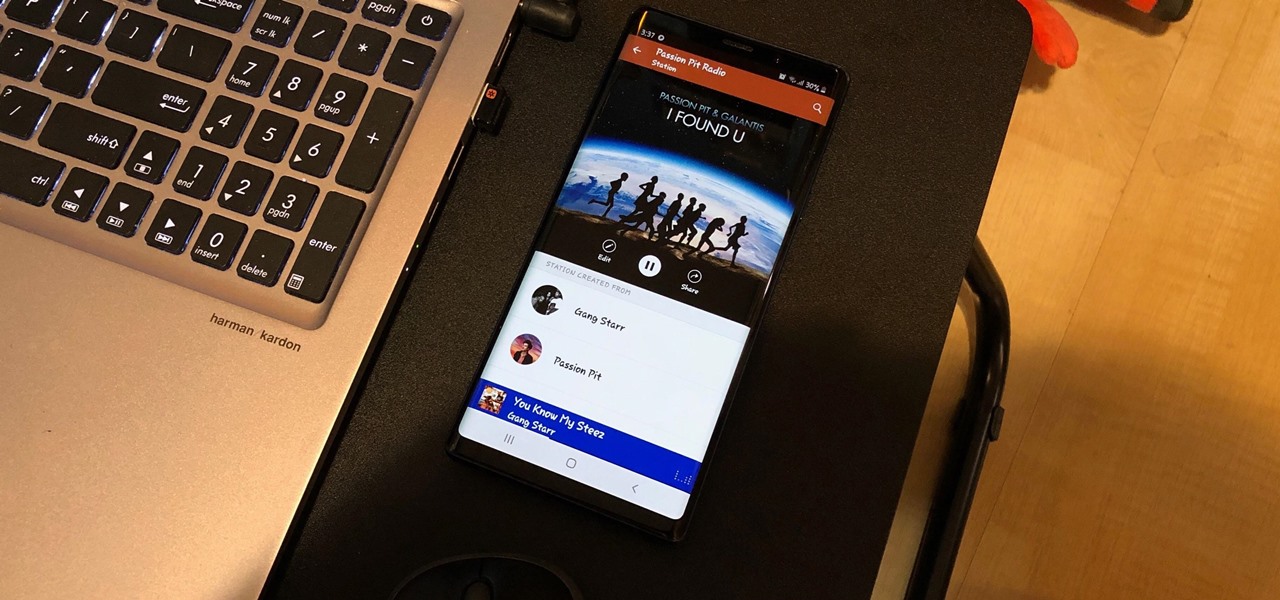
Whether you're out for a drive, commuting to work, or just taking a stroll, listening to your favorite tracks on Pandora takes the legwork out of choosing which songs to play next. After a while, however, you go-to playlist can get repetitive, as the same songs from the same artists seem to play over and over. Luckily, Pandora makes it easy to add variety to your stations in just a few taps.

Cosmetics augmented reality specialist ModiFace appears to be really benefiting from the brand power of L'Oréal, which acquired the company last year.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

We've seen a variety of AR experiences related to athletic footwear over the years, but Puma is betting sneakerheads will buy into a version of interactive design where sneakers are the augmented reality experience

Move over, cosmetics companies. The athletic footwear industry wants to be able to give their customers the opportunity to try on products in augmented reality as well.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.

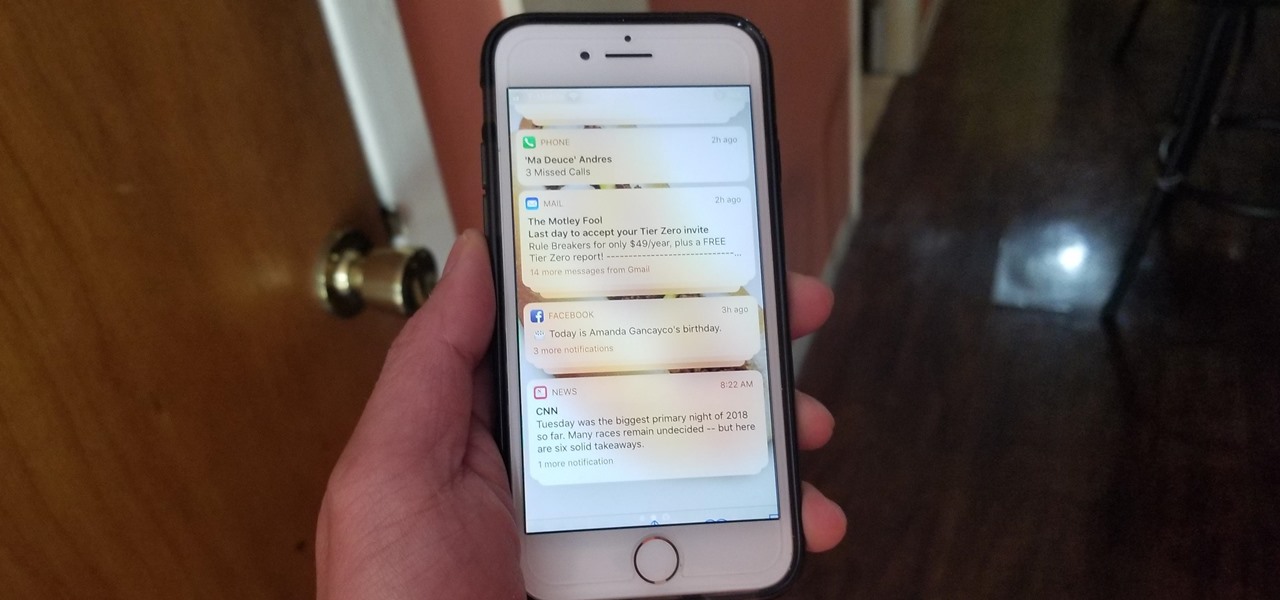
When you first update to iOS 12 on your iPhone, notifications on the lock screen and in the history will be grouped automatically into stacks based on a variety of factors for each app. For example, articles from Apple News will be stacked together based on sites. But you can also change this so that all alerts from a particular app will be grouped in one bundle, not separate ones.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

At its F8 developers conference on Tuesday, Facebook announced new tools and features coming in a new version of AR Studio, including the integration of 3D content aggregator Sketchfab's Download API.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Moviegoers who arrive at the theater early are no longer a captive audience for the ads, trivia, and miscellaneous content that precede the movie trailers than run before the feature presentation, as the ubiquity of the smartphone has become the preferred distraction for early birds at the theater.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

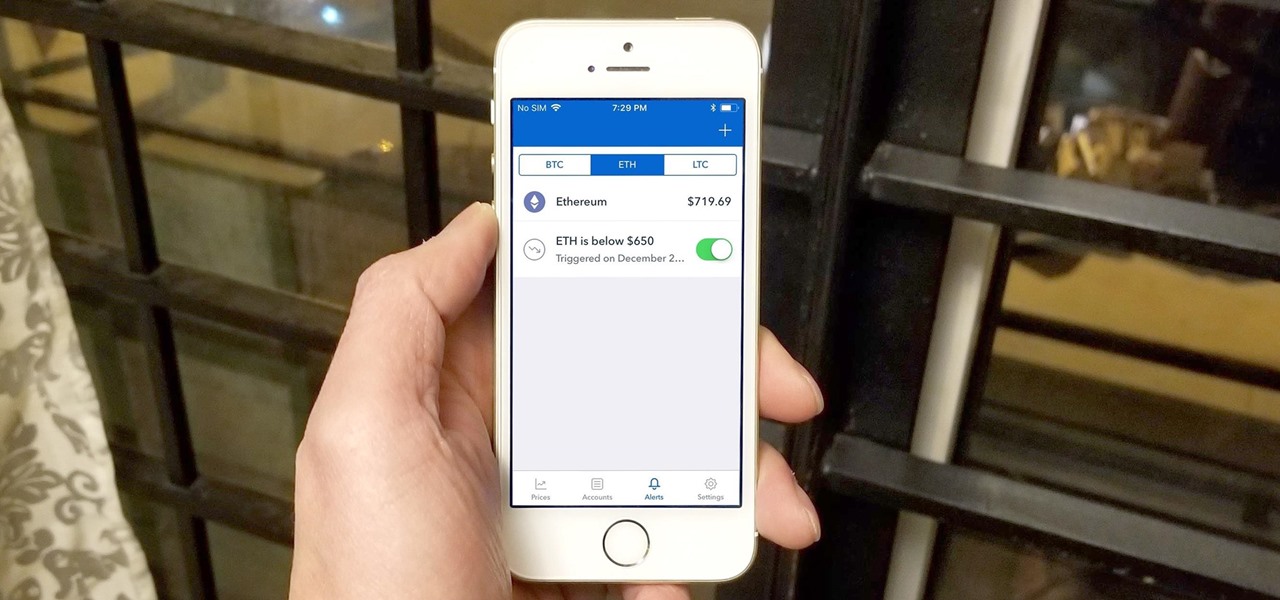
Bitcoin's wild price fluctuations — and by extension, Bitcoin Cash, Litecoin, and Ethereum — can be terrifying if you're new to trading cryptocurrency. Seasoned traders, however, see these price movements as opportunities to maximize their holdings and profits. With Coinbase, you can trade cryptocurrencies more efficiently.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

The promise of augmented reality when it comes to gaming is the conversion of the player's real-world environment into a virtual playground.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Though the Microsoft HoloLens' release to the consumer market is still a distant thought at the moment, Ubisoft is preparing for the future with the unveiling of AR video game prototypes.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

A new dating advice site, WittyThumbs, launched today that lets users offer advice to others as well as seek it; the site combines that collaboration with advice from designated dating experts.

Another entrant — Aryzon — has joined the competition to be crowned as the "Cardboard of AR." The Netherlands-based startup launched their Kickstarter campaign Monday (May 29) and the campaign has already surpassed its funding goal. The company expects to ship units to backers in September.

4DViews, the volumetric capture company that films actors and performers in augmented and virtual reality for things like movies, TV series, and applications, has just released the app 4DViews: Raise Virtual to Reality, to demonstrate its technology for smartphones.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.

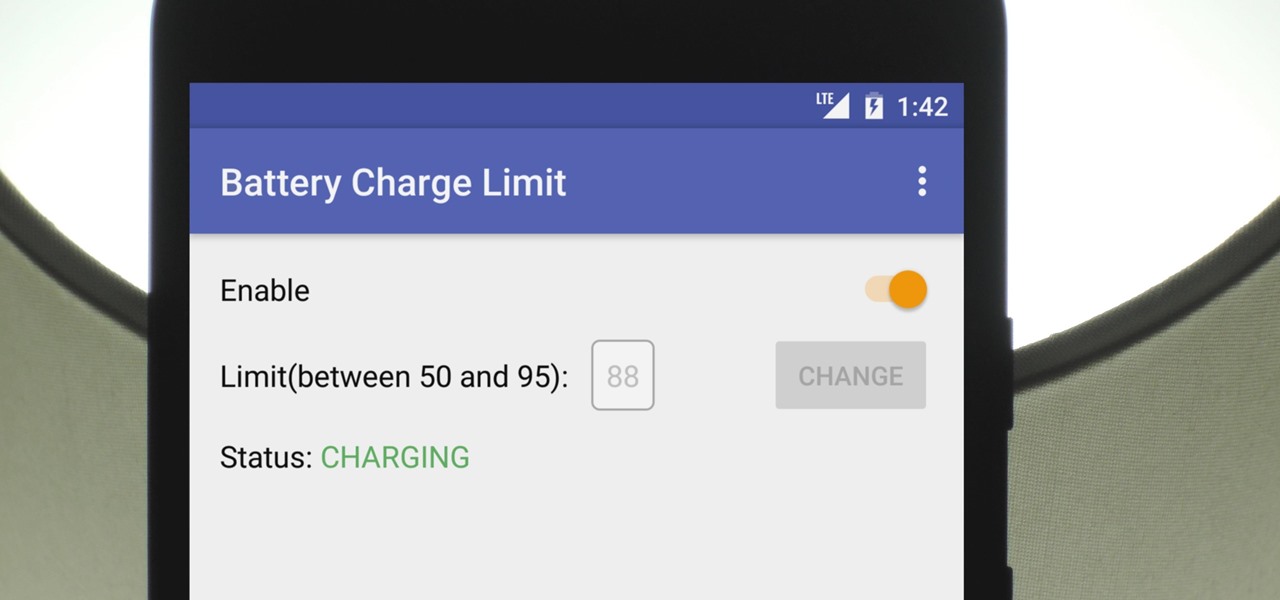
There's a lot of conflicting information out there when it comes to the best habits for charging a smartphone's battery, so let's clear some of that up right off the bat. Lithium ion batteries (the type used in most modern electronics) start to lose their ability to hold a charge over time, and the two biggest factors that contribute to this are excess heat and overcharging.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.