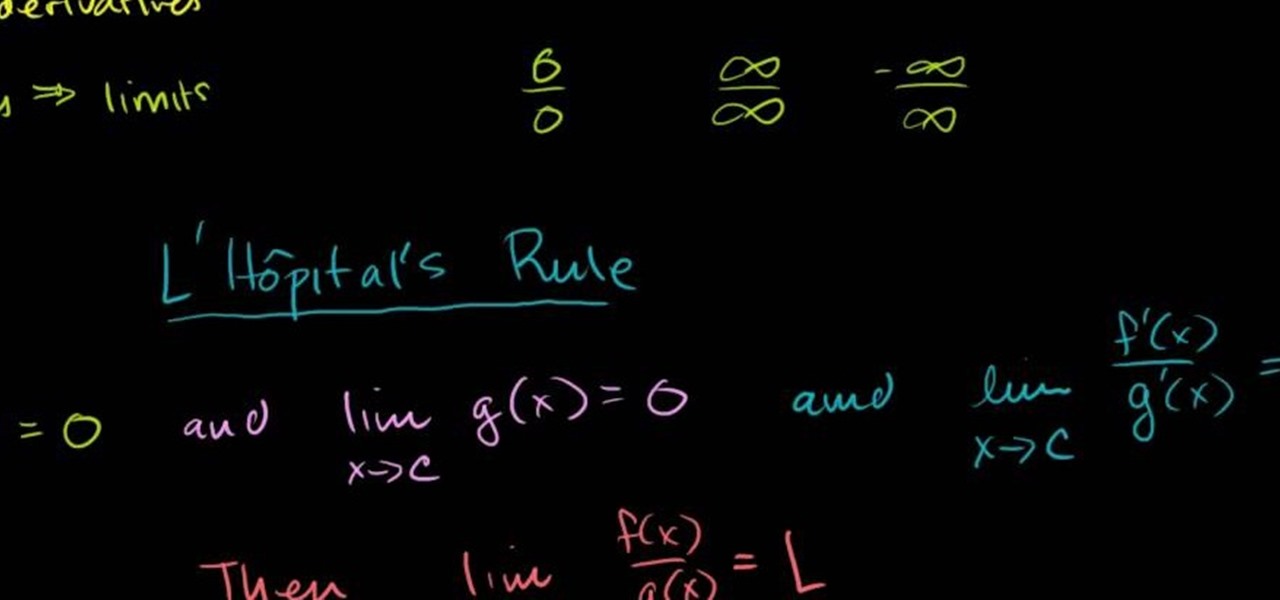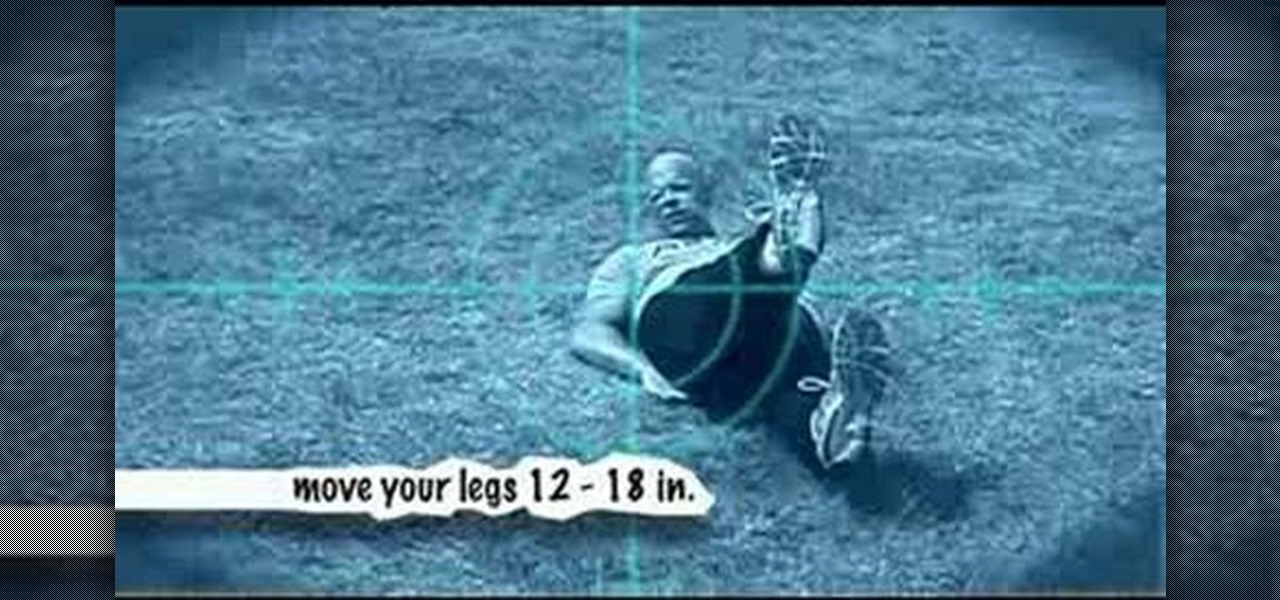
Want to get great abs, thighs, and a butt all by doing just one exercise? Then save time while still getting awesome results by doing the flutter kick exercise, which involves kicking your legs one on top of the other while keeping them at a 45 degree angle.

Donny Gruendler, a faculty member at Musicians Institute, has become and expert at performing with backing tracks, manually triggering samples, and playing with loops (both live and in the studio). In this installment from his video tutorial series in which he discusses the fundamentals of playing with loops, Donny provides tips for complimenting a drum loop (and thus avoiding "target practice").

Skittles is an old European target sport that is very much like bowling. Discover how to make home made skittles with just a tennis ball, glue, empty water bottles, water, paint, and newspaper. Watch this kids activities how to video tutorial to get ideas for a great rainy day kids activity.

Short Plank is derived from original pilates exercises in order to teach proper abdominal and torso support in the push up position. The exercise in this how to video will strengthen your core, strengthen your shoulder girdle stabilizers and target the deep muscles of the abdomen and spine to protect your lower back. Watch this fitness tutorial and you will be toning your body with the Short Plank pilates move.

This video tutorial goes over methods for defining the topology of an organic object in Adobe Photoshop. This is helpful as a planning stage before you begin your 3ds Max 8 digital 3D modeling to make sure that your have proper distribution of faces and your target mesh will deform nicely. So, if you're using Autodesk's 3D Studio Max for awesome 3D graphics, this could help you out with Photoshop topology.

Don't have time to workout? Then watch this how to video and learn how to do a five minute workout that will workout your abs. Start by doing a in-betweens, bicycles, and toe touches. Finish with side reaches which target your obliques.

Adolfo explains how to use the double end bag. This will help your boxing by allowing you to learn the timing and coordination between your hand and target. You always have to be thinking offense and defense.

Targeting Notes and Creating Harmonies Using MIDI -- Jeff Dykhouse shows us how to use MIDI to tell Auto-Tune which notes to tune. In addition, you can use this technique to create harmonies. Antares Auto-Tune is the fastest, easiest, and highest quality tool for pitch correction. Use this in conjunction with DigiDesign's Pro Tools for awesome sounds.

Let Deb Cross and John Hendron demonstrate how to paste text on a Macintosh without keeping the style information (font size, color) in your target application.

Increase web traffic with these 10 steps in this how to guide. Learn how to generate free targeted website traffic and dominate your niche.

Sadie Nardini shows you how to transform the basic sun salutation yoga exercise into a core-targeting exercise that burns calories.

Sadie Nardini demonstrates a 10-minute yoga sequence that targets your abs, waist, and lower back.

The Swiss ball brings an element of instability to basic exercises like the straight leg bridge. This stimulates and conditions your deep core muscles improving spinalstability. In addition to these small but important joint stabilizer muscles the Straight Leg Bridge also targets larger prime movers in your back, glutes and hamstrings.

Get ready for one heck of a battle in the Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

Need to evaluate limits involving indefinite forms? See how it's done with this free video calculus lesson. Need help finding the From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series...

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Smartwatches are an excellent way to keep track of our smartphone's notifications as well as our own fitness. However, these devices are not usually cheap. If you'd rather not pay a premium for a piece of wearable technology, check out all the Black Friday deals on smartwatches — we've got all the best ones listed right here.

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

Black Friday is fast approaching, and just like every other day-after-Thanksgiving, there will be too many tech deals you won't want to pass up. If you've been saving up all year just for this sometimes-chaotic shopping holiday, we'll help you figure out the best tech sales to take advantage of and when, whether it's Black Thursday, Black Friday, or Black Friday weekend.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Buyers can't wait for their Tesla Model 3 to be delivered. But with no clear arrival date in sight, buyers are starting to get a little antsy waiting to see what the Tesla Model 3 will look like up close. Luckily, Tesla accessories seller EVANNEX partnered with technology firm Kinetic Vision to try and satisfy buyers for a while by creating an app that lets you view an augmented reality Tesla Model 3 that's nearly life sized.

Augmented reality (AR) generally exists through the lens of our smartphones as information layered on top of what the camera sees, but it doesn't have to. Developer Jon Cheng worked with an indoor climbing facility in Somerville, Massachussetts, called Brooklyn Boulders, to turn rock climbing into a real-world video game where participants compete in a time trial to hit virtual markers on the wall.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Don't throw away your dead light bulbs, they may come in handy one day. This video will show you how to start a fire using a dead lightbulb. And no electricity. The tricky part is emptying out the insides, but this can be done with sticks and stones, assuming you're in a survival situation and just happen to have a light bulb with you for whatever reason.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.