We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

Almost 125 million people worldwide suffer from what is known as psoriasis, the skin disease that's marked by red, itchy, and scaly patches that are hurtful, if not visually god-awful. There can be a little hope though for psoriasis sufferers. Though you can treat and control psoriasis, characterized by dry scaly patches of skin, the progress is often erratic and cyclical, so be patient and consistent in executing these steps.

Speeding tickets are one of the worst things a driver fears on the highway, aside from wrecking, of course. But you can get home safe without getting a ticket. You just need to keep your vehicle off the radar by following these stealthy driving techniques.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Magic Leap's legal battle against Nreal has taken an intriguing turn this week, as Magic Leap set a date to discuss the matter with Nreal. But a new partnership struck by Nreal adds another wrinkle to the duel between the two AR wearable makers.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Filmic Pro harnesses the full native power of your iPhone or Android phone — and then some. If your smartphone shoots in 4K resolution, Filmic Pro will let you choose that resolution. However, it's not all about the pixels — bit rate is an essential factor in determining the overall quality of your 720p, 1080p, or 4K video, something Filmic Pro gives you full control over.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

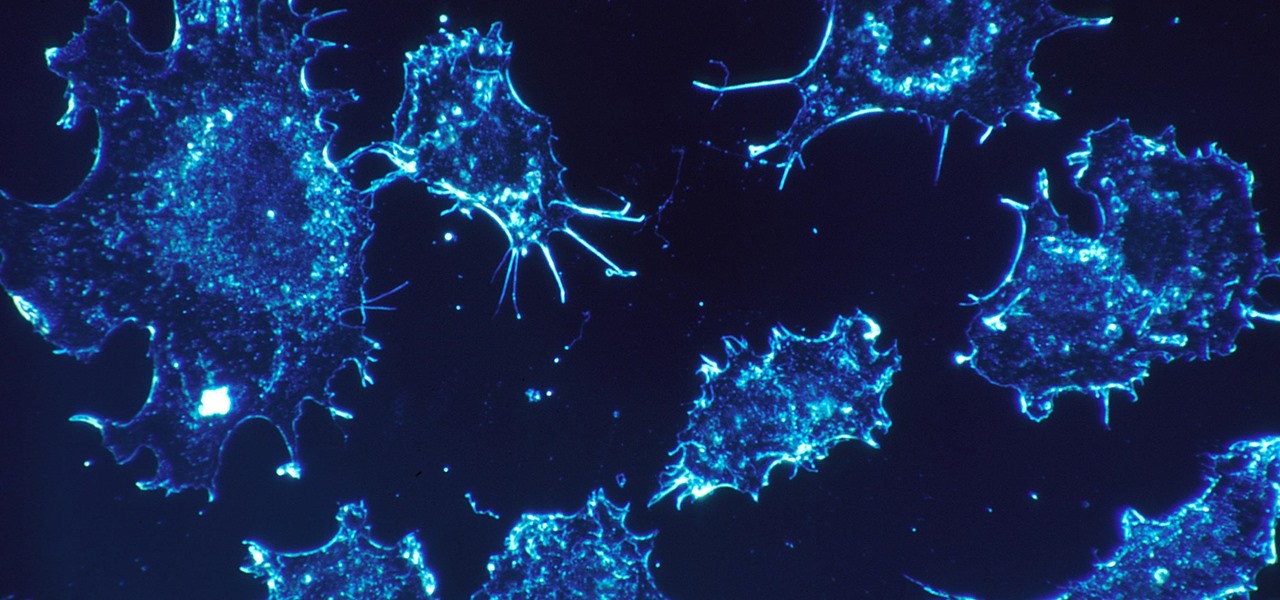
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

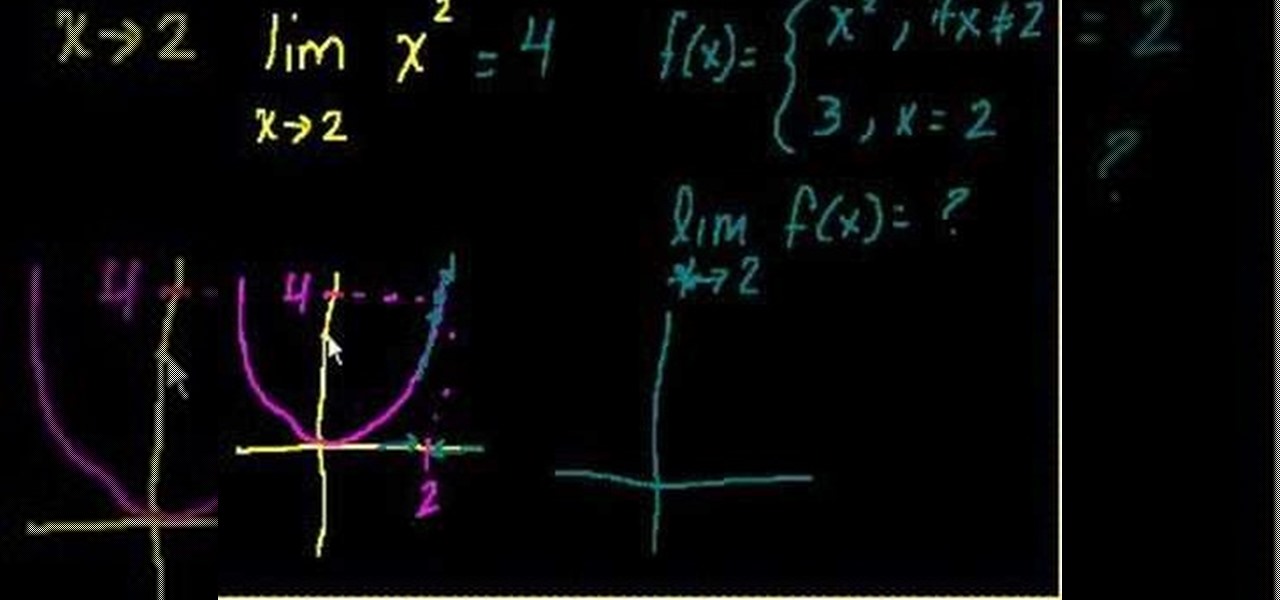
Can't quite get your head around limits? You're in luck. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to work with limits in calculus.

The runaway chainsaw family of glitches for Gears of War 2 enable the player to chainsaw a target to death instantly, without having to wait through the tedious process of watching their victim being sawed in half vertically. This video will teach you how to use the glitch in multiplayer, whether hosting or not. Like most of the game's glitches, this isn't all that useful in the game, but if you've finished all the other content, it's time to turn to the glitches!

This video shows you how to generate random numbers with decimals in Microsoft Excel.When generating random numbers you must have a lower and upper limit, so that your number will be generated between the two limits. For a number without decimals, you only have to use the "=randbetween" function. If you want to use decimals, you will have to use a different but similar function. Start by typing "=rand()". Next, you multiply this by the difference between the limits and add the lower limit. Fo...

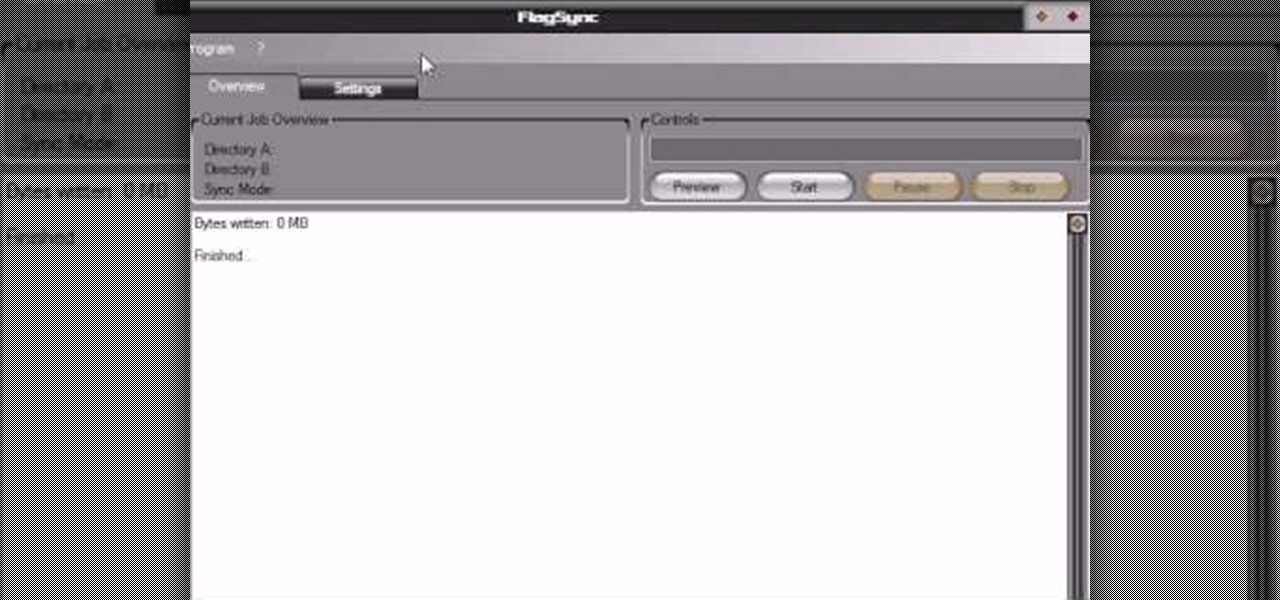
Video demonstrates how to synchronize two folders on windows without doing much of copy pasting and does the job easily. This is a free wear, “FlagSync”.

Get ready for the boss fight of your lifetime in the Xbox 360 game Darksiders. In the boss fight in Twilight Cathedral, spar against Tiamat. When you reach the bat queen Tiamat she will take offf into the air immediately. Quickly dash to the Inert Bomb Growth around the edge of the arena closest to the flying and then throw it at Tiamat. Now you need to use your Crossblade and target a flaming urn then the bomb you stuck onto Tiamat to light the bomb on fire. Once you detonate the bomb on her...

Keep your crossblade near for this level of the Xbox 360 game Darksiders, In the sub-boss fight in Twilight Cathedral - The Jailor, make sure to target the sores. This grotesque monstrosity towers over War. It is almost as wide as it is tall. You'll want to keep your distance from the Jailer as it has a powerful attack in which it slams the cage it carries onto the ground. You'll want to spend most of you time here with the monster targeted while you backpedal away from it. The biggest annoya...

Caged Fighter: Make your way across town and you'll find an injured soldier on the rooftops that gives you some new information on finding Bartolomeo, who should in turn help you with Silvio. You get a large green area added to your map, but note that it's overlapped by a restricted area. Expect trouble.

Knowledge Is Power: But can power be knowledge, too? Pay a visit to Leonardo and he'll cook up a new weapon for you based on a mystery codex. After the cut scene, move out to the yellow map marker and you'll get some directions on how to use your new pistol. Lock onto the three dummies across the river and shoot 'em. Holding down the fire button builds up your accuracy, making it possible to hit the distant targets. When all three targets are shot, return to Leonardo to complete the mission. ...

Infrequent Flier: Fly through this episodic mission and take control. As you take flight, immediately pause the game and check out your map. You can see the locations of all of the fires in the city, as well as the target to the far, far southeast. If you make a simple beeline for the target, the Palazzo Ducale, you won't get the updrafts you need to maintain your height and infiltrate the fortress. Instead, you need follow the trail of fires that lead you east and then north before finally t...

This a simple drawing video targeted for and taught by a young girl. The instructor demonstrates how she sketches out female figures, either little girls or women, on her drawing board. She makes additional remarks about hoe to modify and personalize these renderings. So gather up some pens or pencils and paper, and check out this cute little video. You'll learn how to sketch people in no time!

Aerobics are targeted by total physical fitness: strength, flexibility and cardiovascular fitness. Aerobics can be taken in classes and are usually done with music. To practice aerobics you should follow an instructor, stay in motion, use arms to lower or raise intensity, and strengthen heart rate. With this how to video soon you will be able to practice aerobics.

Have you tried working out with a swiss ball? A swiss ball and outer thigh lifts are an essential part of toning your legs and strength training. This fitness how-to video demonstrates how to target the outside of your thighs with outside thigh lifts. Learn about muscle training and exercises in this video workout.

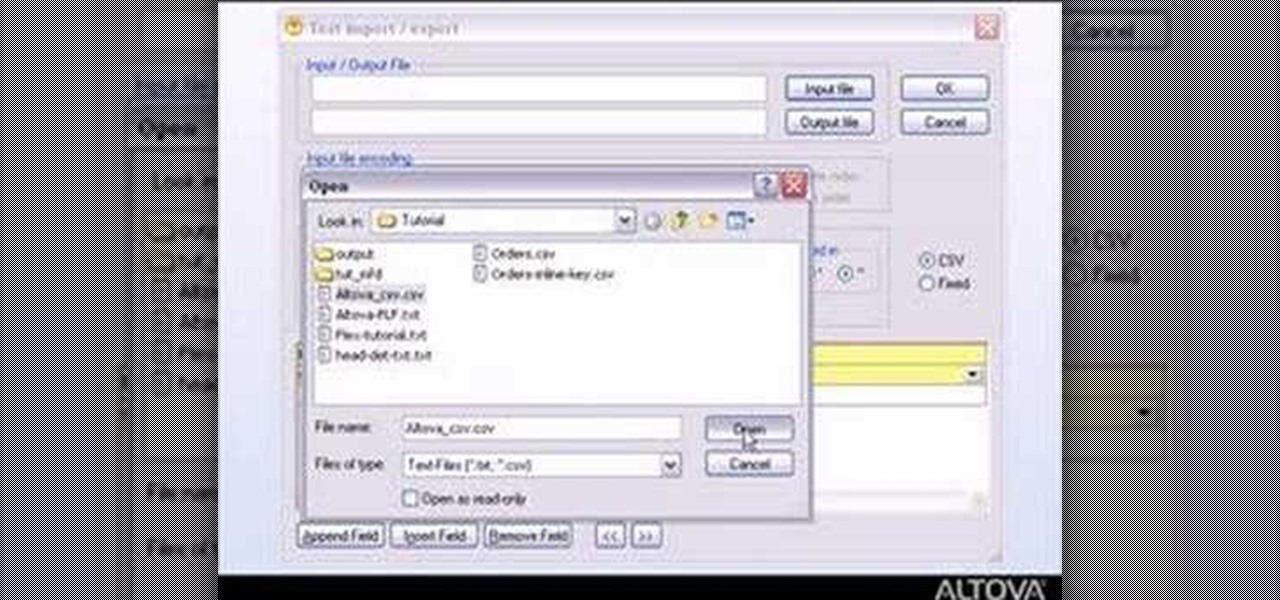
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

This three part how to video shows you a butt workout that will help you tone and tighten your glutes with three of the best butt sculpting exercises to target your butt, hips and thighs. Do these exercises and you will be able to get in great shape.

This tutorial demonstrates a weight training workout for your triceps. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your triceps and the rest of your arms.

This tutorial demonstrates a weight training workout that develops your deltoids. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your shoulders.

This tutorial demonstrates a weight training workout for the chest. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your pecs.

This tutorial demonstrates a weight training workout for your biceps. The how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your biceps.