Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

In this Make Magazine podcast Bre Pettis makes a theremin from a kit by Harrison Instruments. A theremin is a super cool musical instrument invented in Russia in 1918.

In this instructional video, Tim brews up 5 gallons of Kombucha - a fermented tea drink from Russia with healing properties, with a slight alcohol content, and a most original flavor. Watch this video tutorial and learn how to brew traditional Russian kombucha.
Hey, in Russia, Adidas is a huge designer label! Show your fandom of this popular sports line by turning their logo into your playercard emblem. This tutorial shows you step by step how you can make your own quite easily.

Blintzes are thin pancakes that have their origins in Russia. Like French crepes, they can be eaten with either savory or sweet toppings. Some examples of what you might add to a blintz are honey, sour cream, butter, cottage cheese, and even caviar.

On August 1, 2008 a rare total solar eclipse will appear in the skies over parts of Canada, Greenland, Russia, Mongolia, and China. During this spectacular event, the moon will cross in front of the sun, completely blocking out the sun's disk, and casting a shadow over part of the Earth. While only people in a small area of the world will be able to see the eclipse in person, viewers all across the globe can view the eclipse as it happens on NASA TV.

This is a two part video on how to brew up a big batch of Kombucha - a slightly medicinal, slightly alcoholic, and very unique drink from Russia. In part 1 of the video Tim brews the tea and mixes in the Kombucha mother.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Learn how to make a caipiroska. The caipiroska is the Russian cousin of Brazil’s national drink, the caipirinha. In this version, vodka stands in for the traditional cachaca sugarcane liquor.

To become a bounty hunter, you will want to first check your state's laws to see if you need to be a licensed private investigator. If you live in Florida, South Carolina, Oregon, Wisconsin, or Kentucky, don't even try it--bounty hunting is not allowed! Otherwise, your first step is to find a client who needs a target to be caught. Bail bond agents employ bounty hunters to track down people who have refused to show up to court. Find out who your target is. Assemble a file, look into any recor...

From Instagram bot farms in China all the way to vending machines in Moscow that promise to sell you fake followers — the Facebook-owned empire is attracting the attention of the world around. When it comes to Russia especially, the country seems to be developing a little crush on the glorious IG queen.

To do a hippie jump on a skateboard, first find a good hippie jump target. A good target is something that your board can easily fit under. Approach the target rolling at a comfortable speed. When you are near the target, jump straight up so your skateboard continues rolling under the target. You will then land on your skateboard on the other side of the target and roll away. Make sure that you don't jump forward because it will cause your skateboard to roll backwards and you will not be able...

The Recon character class in Battlefield Bad Company 2: Vietnam is a thinly veiled sniper, and utilizing their target-spotting functionality is key to effective sniping in this game. This video is a complete guide to effective Recon play, teaching you about all your abilities, guns, and how you can spot targets to make yourself much more effective from much further away.

With the 2018 FIFA World Cup underway in Russia, soccer (aka "football") fans worldwide can show support for their favorite teams and players in augmented reality via Snapchat and Facebook.

The silent film era ended long before anyone had conceived of something like machinima, so your machinima movie had better have some talking! This movie will teach you how to use morph target in 3DS MAX to give your imported World of Warcraft characters facial expressions and animate their mouths to make them appear to be talking. You'll also learn how to make your model sneer, smile, and perform other facial actions.

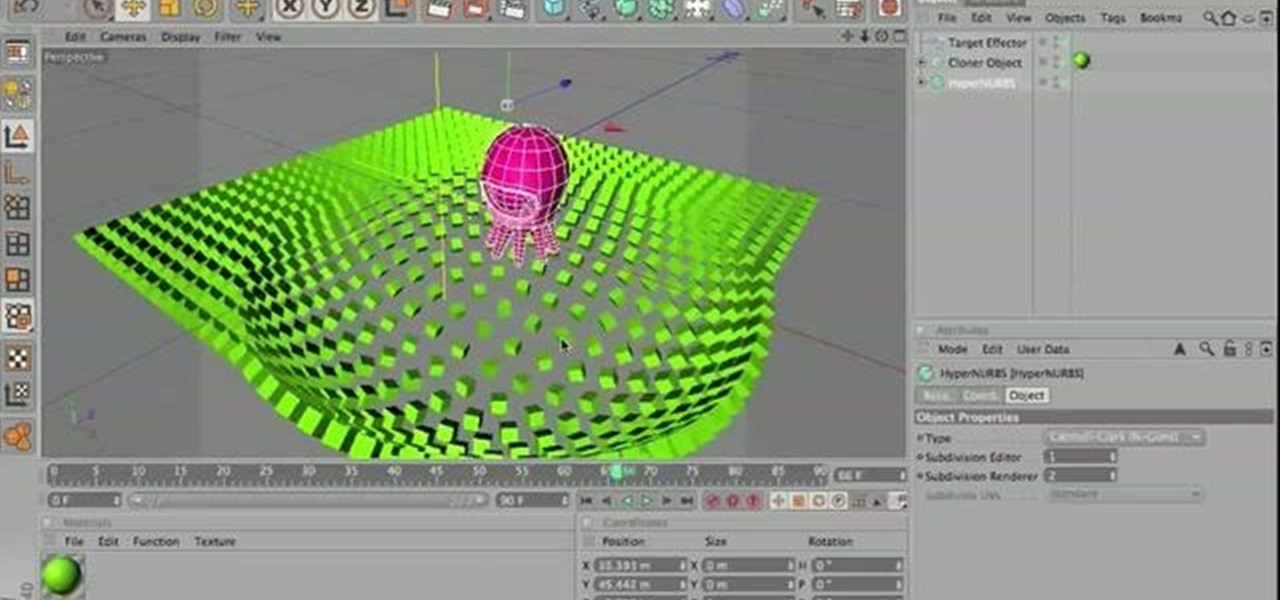
In this Cinema 4D tutorial, you'll see how to create a Target Effector MoGraph which is amazing. With only 4 simple steps, you can create a very special scene. Primitive Object, Cloner Object and Target Effector will be used in this tutorial. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get sta...

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

In this video tutorial, Chris Pels shows how to create a Cross Page PostBack in ASP.NET, where a control on a source page raises a PostBack event to a different target page. First, learn how to configure a Button control to PostBack to a different target page. Then, learn how to get information from controls on the source page with the PreviousPage property and the FindControl method. Then, learn how to use public properties on the source page to expose data to the target page, and learn how ...

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Want to perform an unplugged version of Blink 182's "Easy Target"? See how it's done with this free video guitar lesson, which presents a complete breakdown of the song and its chords. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Easy Target" on your own acoustic guitar, take a look!

Traveling often is super fun, but sitting through 13 hours on the flight from California to Bangkok is killer on your skin, especially since the airplane recycles air and therefore dries out your skin.

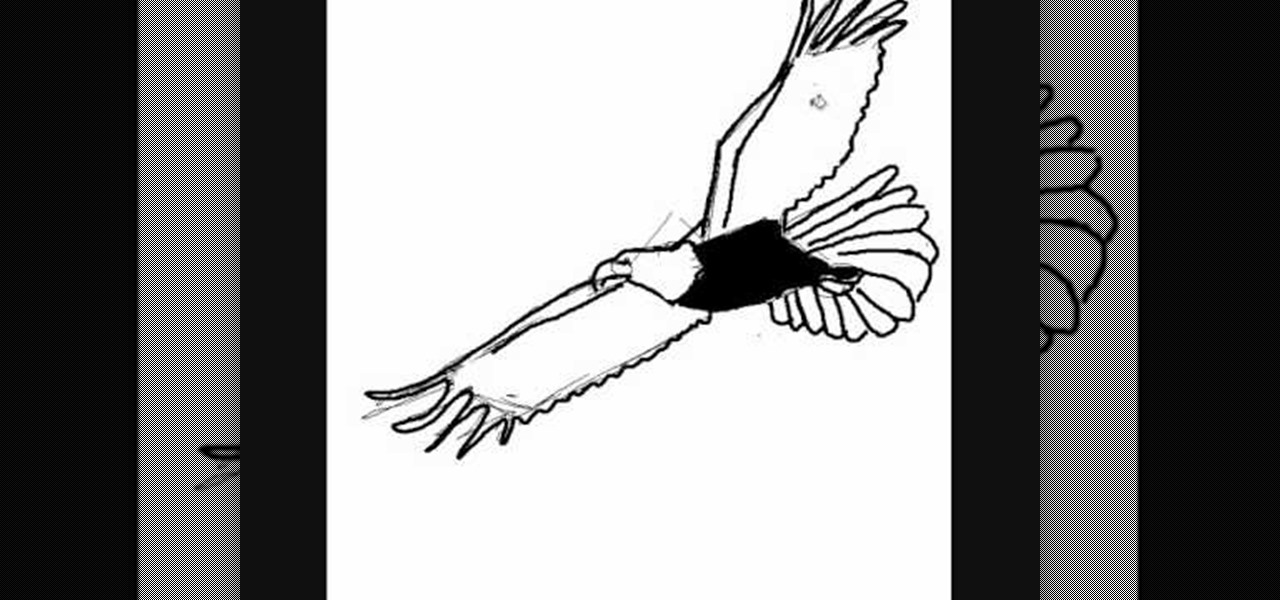
Learn to draw the mighty bird of prey, the eagle. Eagles tend to frequent national symbols like the "Coat of Arms", for countries like Egypt, Mexico, Germany, Austria, Russia and Armenia. It's more famous as The Great Seal of the United States. So, eagles seem to be one of the most influential birds in the world, so why wouldn't you want to learn how to draw it? This how-to illustrates the step-by-step details to drawing an eagle, "Águila" is the Spanish translation of eagle.

Big-box retailer Target has been on a bit of an augmented reality advertising shopping spree via Snapchat lately.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

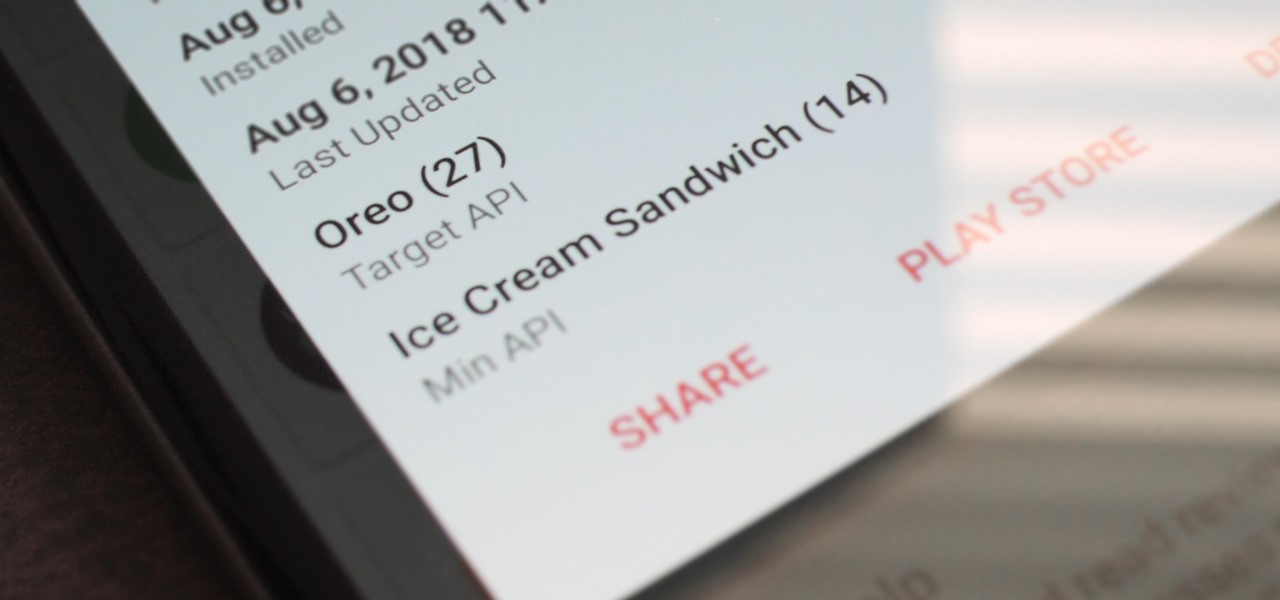
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

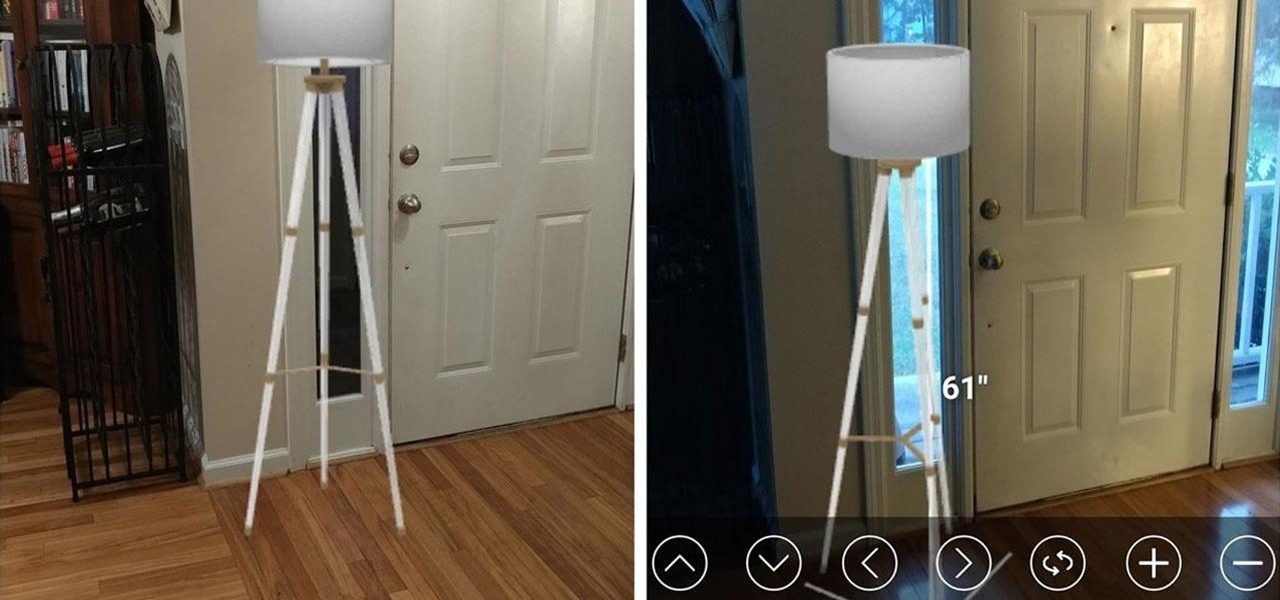
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

In this free video exercise lesson, you'll learn a popular variant on the push-up, one designed to target your triceps. With pushups, as with any body-sculpting exercise, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this exercise yourself, watch this handy home-fitness how-to.

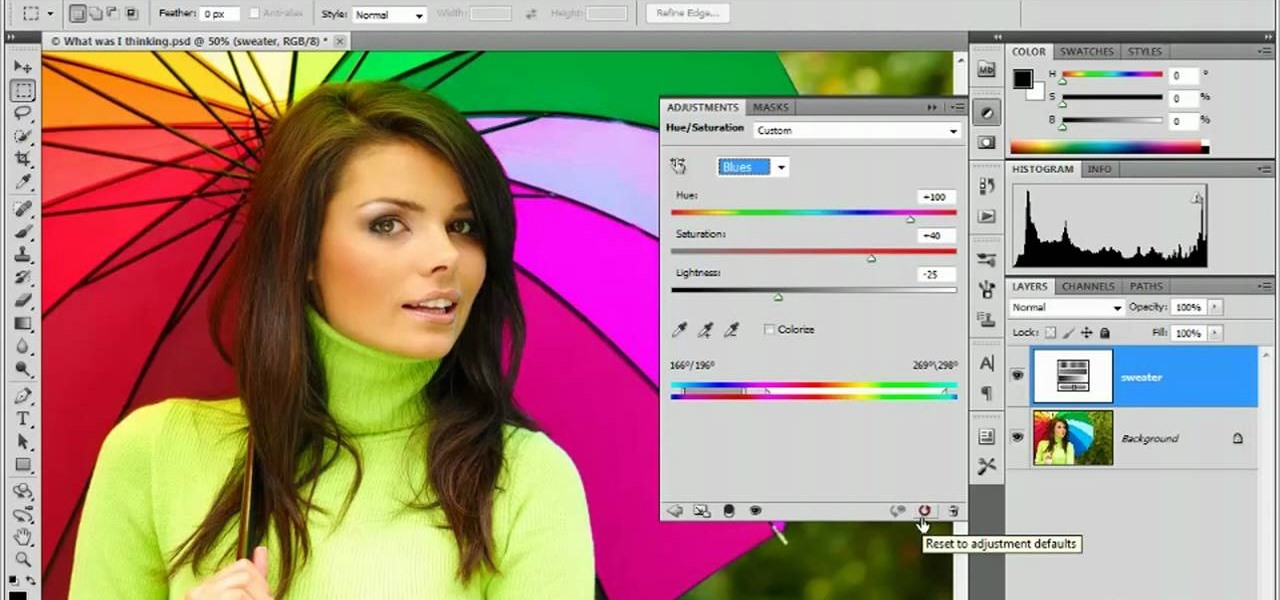
Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

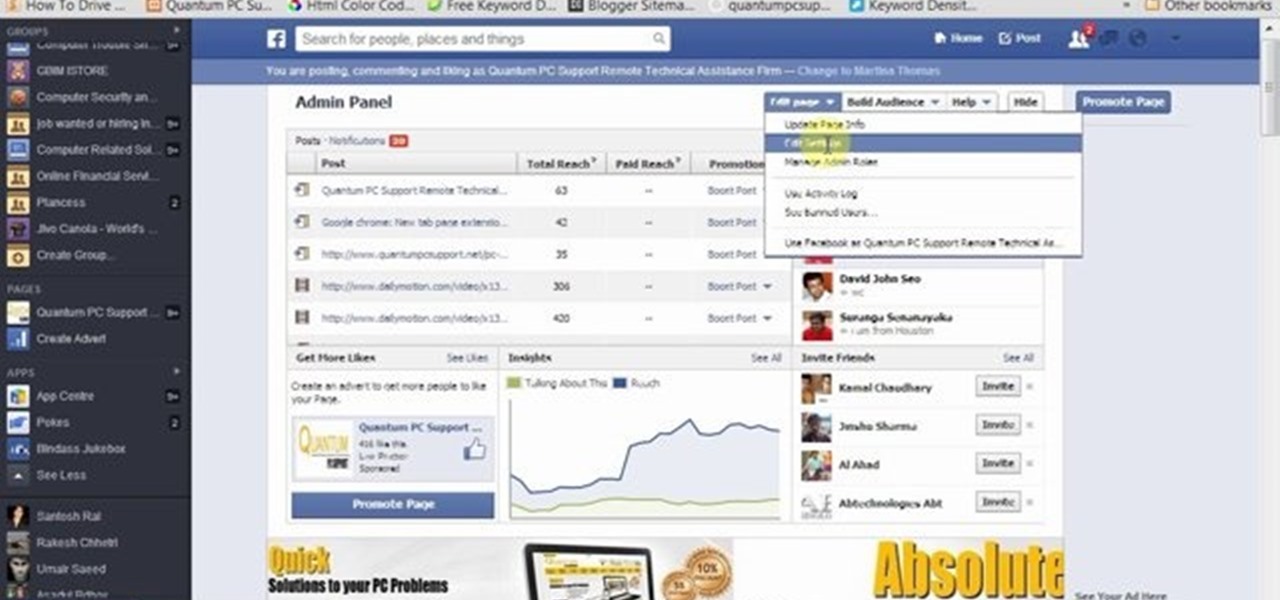
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.