Watch this video guide that shows you the steps to drawing your very own Flipper-like friend— the dolphin. It's a very easy drawing to accomplish, and the video illustrates, step-by-step, the process of creating a dolphin portrait. It's a simple one, so grab you cocktail napkin and pencil. "Delfín" is the Spanish translation of dolphin.
Peter John, an accomplished expert in palmistry, demonstrates how to properly understand what it means when your palm reading subject has a long hand and long lines on the palm. He indicates what to look for to indicate intelligence and good communication skills in your subject.

Making fake wounds is an art form, and this girl is, if not a master, at least a very accomplished journeywoman. In this video she teaches us how to create a realistic-looking fake wound using only liquid latex, facepaint, and other simple materials. The end result is creepy and gross, and will make a perfect addition to your next Halloween costume or hot date.
New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

It's pretty standard when creating a document that requires some basic page layout formatting, that you're going to want to wrap or flow text around images. In this Apple tutorial, you'll see how easy it is to accomplish in Pages '08.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

This video will show you two different ways on how to make an end on a coaxial cable TV wire. We will show you how to use a tool that makes it very easy to strip the coax cable to expose the metal and bare wire so that you can adapt the end on, and how to also use just a razor blade to accomplish this.

This video will show how to recreate my Blue Forest Berry nail art design. A fashionable way to make a lasting style statement, this awesomely design is easily accomplished with the help of this easy visual tutorial. So look smart and try this design at home today.

Are you tired of the old windsor knot and need something new? Well, try the Eldredge knot on for size. Easy to follow along animated video for you to easily accomplish this intricate necktie knot.

You shouldn't have to labor for hours on end to achieve great hair. And if you have to wake up early for school or work it's even more important that you don't lose your precious ZZZs just to make sure that French braid is perfectly plaited and pinned up.

Looking for a way to speed up the boot time on your favorite programs in Windows? This video will show you a little tweak to make your most-used applications start up in no time. Basically, you just go to the "Shortcut" tab in the program's properties menu. Then add " /prefetch:1" to the end of the target location in the "Target" box. This tweak works on PCs running Windows 7, XP or Vista.

This video will show you how to perform a really cool, easy coin trick with only two different coins and your hands. The effect is that you throw one of the coins up in the air, catch it, and reveal the other coin, which the audience has not seen yet. You accomplish this by switching the second coin from one hand to the other while the first is in the air, then stashing the first coin in your pocket while showing your audience the second. Easy and impressive.

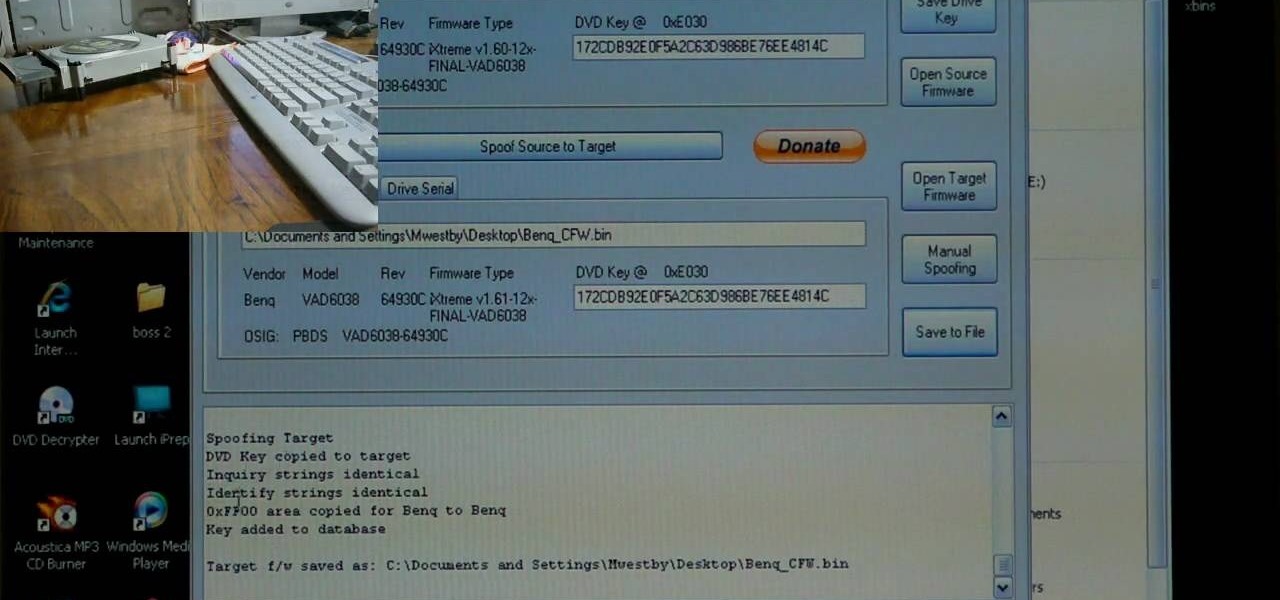
If you've already flashed your XBox 360's disc drive, then congratulations, you've accomplished the most challenging step involved in hacking you XBox. You aren't done though. As Microsoft keeps updating it's firmware to try and fend off hackers, you must keep updating your custom firmware to thwart their efforts. This video will show you how to upgrade your flashed BenQ XBox 360 disc drive's firmware to IXtreme 1.61 using Jungle Flasher 1.61. NOw you can play your burned games with a greater...

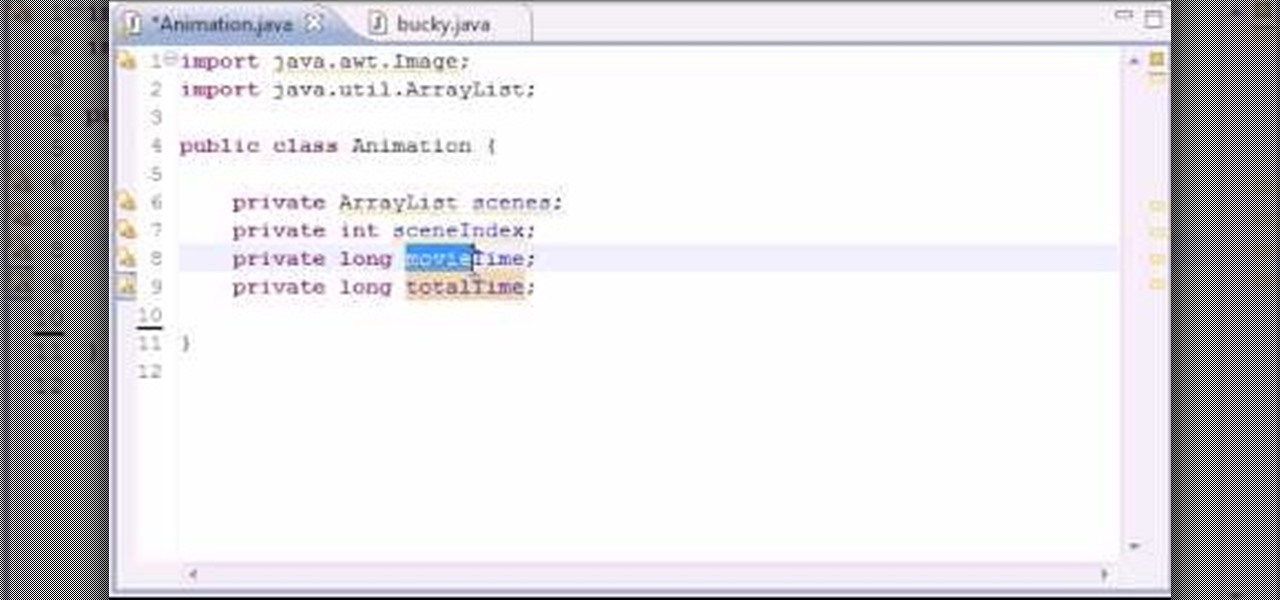
Want to write Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will help you on your merry way to accomplishing just that. Specifically, this lesson will demonstrate how to make a simple animation loop. For detailed instructions, watch this programmer's guide.

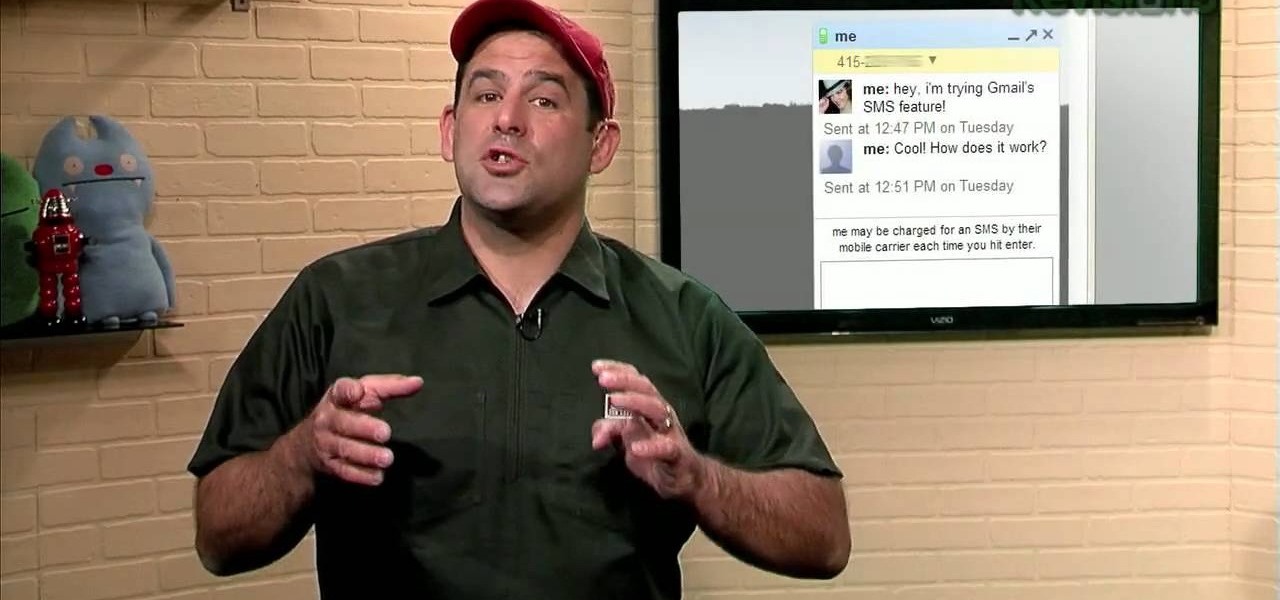
G-mail can do a lot of things. It is a state of the art, awesome e-mail system, and to top it all off now you can learn to send text messages through it - for free!

In this Pets & Animals video tutorial you will learn how to train your dog to perform the "cop-cop" trick. In this trick the dog learns to put its feet on your feet. Step 1 – teach the dog to target a book or a mat with their feet by offering them some treat. You can do this either by appreciating or clicking when both the feet touch the book. The next step is getting the dog to target the book with their feet while they are between your legs. You have to continually reinforce the dog to ma...

Fruit flies are the biggest pain in the you know what. They come out of nowhere, swarm in packs and are virtually impossible to get rid of without tearing your kitchen apart. Don't you wish there was a simpler way to rid yourself of these annoying pests?

Are flies ruining your summer BBQs? Did you know there is an incredibly simple solution? This tutorial will show you how to get rid of pesky flies with nothing more than a ziploc bag, water and a few pennies.

Not only does "Andy Field Magic" go about showing the effect in a professional manner, he does so in a personable and thorough demonstration. Agreed, the effect is not magic in essence, but does show off quite the slight of hand. I appreciated that lack of jargon in the demo; the performer visually made sure that you understood what he was doing step by step. It makes for an easier learning environment when you know exactly how the effect is achieved through a slower paced demo. He seems to b...

This is a quick and easy to make dish for any meat lover. Lamp chops with cucumbers on a bed of rice, a sophisticated meal, here you'll slowly go step by step. Chef Micheal Clark, gives us a easy to accomplish wonderful dinner meal for you and the family.

Learn Newton's laws of motion from the utmost authority on aeronautics -- NASA aka National Aeronautics and Space Administration. See how Newton's laws apply to aircrafts from the powerhouse of space exploration. They talk about thrust force as applied to aviation.

Hello all of you fellow pool shooters. This video tutorial is designed to help you look like a real pool shooter. There are no pool tricks here, but great and informative basic information on playing pool. This will help you become the accomplished billiards man you've always wanted.

This is Hydroponics: At Home for Beginners.

This is a video tutorial on how to cancel your Verizon contract without having to pay an early termination fee (ETF).

Looking to work on your form? Try this free video golfing lesson for size. In short: When putting, to be able to release the putter down the line to your target, the club must travel slightly inside the target line. For a complete overview of how to become a better putter, watch this video guide.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.