Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...
In this video Chris Pels shows how to create an MSBuild project that orchestrates the execution of the aspnet_compiler and aspnet_merge utilities for an ASP.NET web site. First, learn the fundamentals of the compilation process for an ASP.NET web site and the role of the two command line utilities. Next, see how to create an MSBuild project file and the primary elements such as PropertyGroup and Target. Then learn the details of how to execute the aspnet_compiler and aspnet_merge utilities fr...

A hooking knee strike is legal in Thai boxing, not kickboxing. Learn the skills of Muay Thai in this tutorial on competitive kickboxing moves. When performing the

All day we use our calf muscles when we walk, run, and climb stairs. As a result calf muscles are popular massage targets. Learn the art of giving massage in this diet and health how-to video.

Pilates is great for strengthening and toning the body. This piltes how-to video illustrates the Single Leg Stretch exercise. It targets the transversus abdominus, rectus abdominus, obliques, scapular stabilizers and hip stabilizers.

This Pilates Side Bend exercise is used to enhance lateral mobility of the spine. It primarily targets the transversus abdominis, obliques and scapular stabilizers. Attention should be paid to the abdominal contraction to maintain rib connection and prevent the hips and shoulders from rotating. The cervical spine should stay aligned with the thoracic spine.

This pilates how-to video illustrates the Pilates Spine Twist exercise. This exercise is great for spinal rotation.

This pilates how-to video illustrates the Obliques exercise. This exercise is great for rotation, flexion and strengthening pelvic stability.

This pilates how-to video illustrates the Obliques Roll Back exercise. This is a challenging rotational pilates exercise for athletes and advanced clients.

Firebug is an essential Firefox extension for web designers and developers. You are able to quickly target any element on a page to see the markup, the CSS, the layout, and the DOM in an instant. Not only can you see all of this juicy information, you can edit and see the results directly in the browser window. This makes Firebug the go-to tool for debugging CSS trouble. Also indispensable for Javascript programmers. So all you Internet website designers out there, pay close attention to this...

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

The UK has officially exited the European Union, completing the long and tumultuous Brexit story and putting the storied nation once again on its own on the international stage.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Baseball fans can now leave their wallets behind at specific stadiums throughout the country. A new upgrade by Appetize to the foodservice and retail technology used at ballparks means you can now use Apple Pay to make purchases at 5 Major League Baseball stadiums.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

training with a head target wall mirror. Learn how to use target mirrors to practice jabs and hooks in this free video for boxers.

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

Getting a good break in life is always nice. But when you're playing pool, it's essential. You Will Need

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

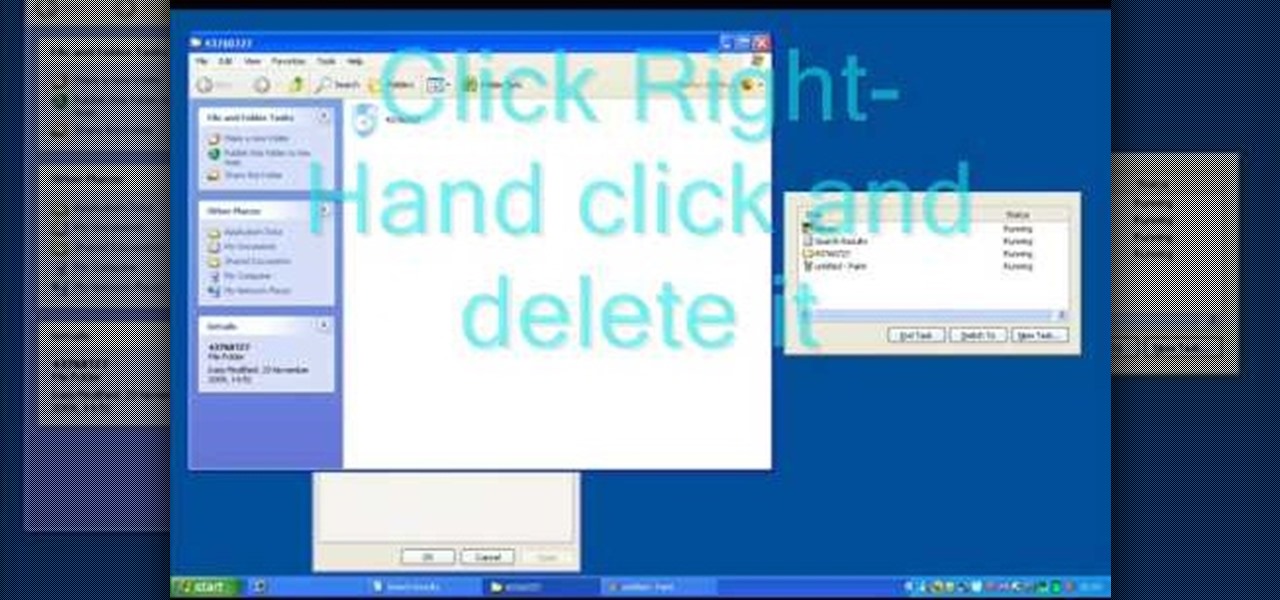
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

No matter what kind of business you have, small or big, online-based or not, when you're dealing with email marketing, the number one things your targets will see is the subject line, and if your subject line looks spammy or uninteresting, it's not going to help you one bit.

In this tutorial, we learn how to throw a crazy gyroball in wiffle ball. You will first stand still with the ball in your hand grasping it lightly, when you go to throw the ball, throw with force and spin your body around. This should make the ball go straight into the target almost every time you throw it. Keep practicing this until you have the hand placement correct. Try moving your hand in different positions around the ball so that the grasp makes the ball move in the right direction. Af...

In this Golf video tutorial you will learn how to avoid slicing with your driver off the tee in golf. First and foremost make sure that your grip is correct. The next point is allowing the club to sit on the ground the way the manufacturer wanted it. The next important lesson is to ensure that your feet and your shoulders are aligned straight down the target. And the last and the most important point to remember is to swing back to the ball with your hips first. Don’t use your arms first. If ...

Jim McLean shows us how to do an eight step swing in this video. You start the swing in the "address" or universal position. The first step is to move the club three feet back from the ball in a uniform motion. Position two is moving the club half way back where the club is pointing down the target line. Position three is a three quarter golf swing is when your elbows are level and the shaft of the club is pointing into the plane line. Position four is preparing to swing forward. Position fiv...

This video is on Golf and will show you how to use the variable tee drill to cure a pull shot in golf. This video is from Golf Link. A typical problem for somebody who tends to pull the ball is they position the ball too far forward. So, when they are setting up, the shoulders are actually looking left. By the time the club head reaches the ball during the swing, they are swinging around to the left producing the pull. The variable ball position drill will cure this problem. Place a club on t...

In this video tutorial, viewers learn how to use the hand rollover to cure a hook shot in golf. A reason why people hit hook shots is because when they come to impact, they roll their hands too early and too much. Therefore closing the club face and causing the ball to go left. To correct this, when you're coming to impact, rotate into a position where the back of the left hand is facing the target. This will square the club face. This video will benefit those viewers who enjoy playing golf a...