The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

It looks like it's cuffing season for AR hardware makers and telecommunications corporations. With AT&T aligned with Magic Leap as its exclusive wireless retailer on the high-end AR side, Verizon has also reached a master reseller agreement with Vuzix, according to a filing with the Securities Exchange Commission.

Apple has finally released iOS 12 for everyone to enjoy, and there are plenty of cool features to go around. Perhaps the coolest feature, at least, for those of us with an iPhone X, is the return of an oft-used gesture we loved on other model iPhones.

Augmented reality app developer Laan Labs has shared a preview of a beta app that achieves 3D scanning with just an iPhone and produces highly-detailed models for sharing with others.

Burning Man 2018 is underway, but Intel and the Smithsonian American Art Museum are giving those not in attendance the ability to view the art from the event through Snapchat.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Apple's lead marketing tool for the iPhone X, 3D Animoji that you control with your facial and head movements, are once again in the spotlight in a new commercial the company posted on its Korean YouTube account this week.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

The Tesla-riding Starman that was launched into space via Elon Musk's SpaceX last week will miss its Mars target and is instead headed toward a lonely asteroid belt in the void of space. But if you missed the initial launch and would like to get a taste of what Starman is seeing, you can now take a short ride along thanks to a new Snapchat Lens.

In another move that pushes Meta 2 toward becoming a legitimate workplace tool, Meta Company has partnered with Dassault Systèmes to bring augmented reality support to the latter's Solidworks 3D CAD software.

Although expected to be only a modest upgrade over the S8, we can't help but be excited about the Galaxy S9's unveiling late next month. Among the many rumors and questions we're looking to see addressed, one of the biggest queries we have is, of course, with the price tag. We might not have to wait a month for the goods, however, thanks to a new pricing announcement out of South Korea.

Samsung has kept us busy with their Android 8.0 Oreo beta testing program for the Galaxy S8, and most recently, the Galaxy Note 8. As the beta continues to receive new updates, stability has improved continuously, and new features keep on creeping in for both devices.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Razer took to the stage this month to unveil their new flagship phone, fittingly called the Razer Phone. The device is targeted at gamers, but has a list of specs that make it an intriguing daily driver for any user. Its headlining feature is an 120 Hz IGZO display, the first of its kind in a flagship smartphone released in the US. Tonight, Razer officially opened up orders for the new phone on their website.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

San Francisco-based startup AstroReality is putting the AR in lunar with a high-detailed model of the moon that comes to life through an accompanying augmented reality mobile app.

Measuring a room has never been so easy thanks to Apple's ARKit. SmartPicture 3D is known for its quick measurements based on pictures from your smartphone. Recently, they released a video of the company measuring a room using the ARKit.

Screen mirroring app iDisplay has arrived for Vuzix M300 Smart Glasses. With the app installed on the M300 and the companion software running on a Mac or Windows computer, users can mirror or extend the computer's desktop to the headset's display, which is connected to the computer via Wi-Fi or USB cable. The app does not yet appear on Vuzix's app store.

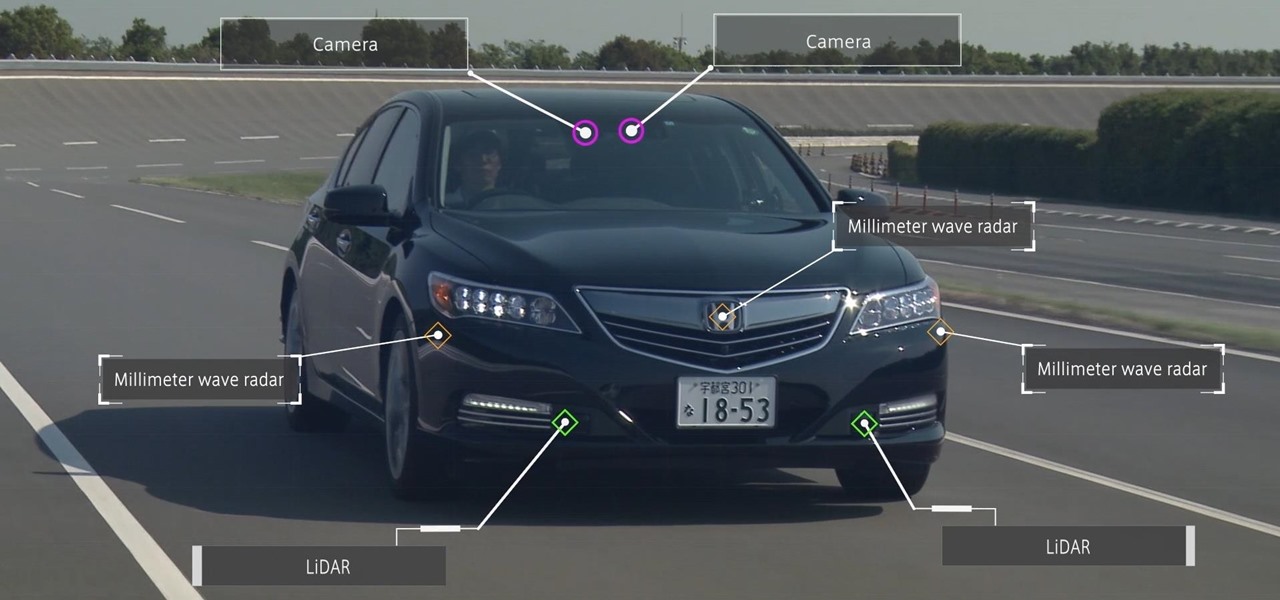
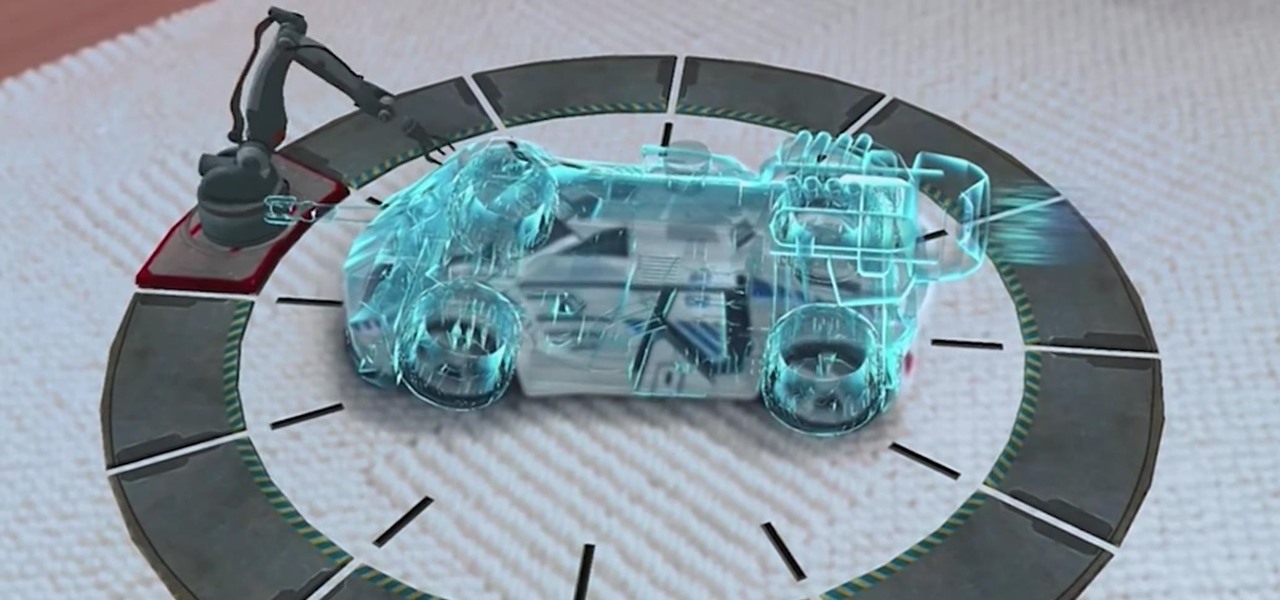
Honda president Takahiro Hachigo has just announced that Honda will complete development of fully self-driving cars by 2025. While the company aims to have level 3 — or conditionally autonomous cars requiring human intervention only in emergencies — on the road in time for the 2020 Tokyo Olympics, these level 4 cars would require no intervention in most environments and thus bring Honda one step closer to producing fully driverless cars.

In an effort to make its services more accessible to users who live in developing countries, Facebook has released a streamlined version of its messenger app. Messenger Lite, at less than 5 MB, is much smaller than its regular 25 MB counterpart and was developed for use on older and lower-end phones. Finally, the app is now available for download in the US.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

In response to the flurry of doubtful headlines about Magic Leap today, set off by an unflattering article from The Information, Magic Leap CEO Rony Abovitz released a short blog post quickly detailing what to expect from the company over the next year. The gist comes down to this: big things are happening in 2017.

In mid-November, Vuforia officially released Vuforia 6.1, which has full support for the Microsoft HoloLens. They also released their AR Starter Kit to the Unity Asset Store, which contains scenes that show you how to use Vuforia features. While I have yet to find any confirmation, I believe it is safe to assume that the AR Starter Kit will work with the HoloLens. I already had a Vuforia tutorial planned for this week, so as soon as I know for sure, I will begin working on it.

In the past, some of Google's Nexus devices have had root methods even before the phones hit shelves. The Google Pixel and Pixel XL are basically Nexus devices from a software standpoint, so why have we gone more than a week since release without a working root method or custom recovery?

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

When casting a flyrod, in most cases, tight loops will allow the fly to travel farther, more accurately, and with less effort. To cast these tight loops, the tip of the rod must travel in a straight line path, slack must be eliminated, and there must be a constant acceleration to a sudden stop. The most common mistake is using the wrist to move the rod which causes the tip to travel in a half circle or windshield wiper type motion.

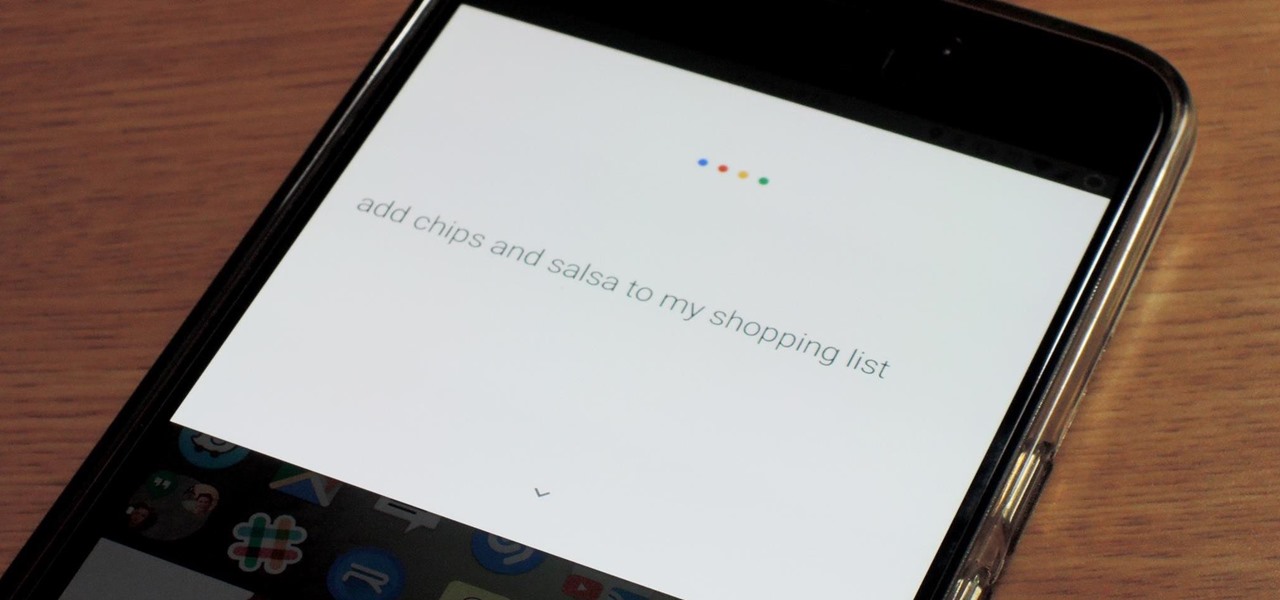
If you use Google Keep, you'll be happy to know that you can add items to lists and even start new ones with "OK Google" voice commands on Android, and it works fairly well. (Hat tip to Reddit user rambantu for finding this trick.)

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.