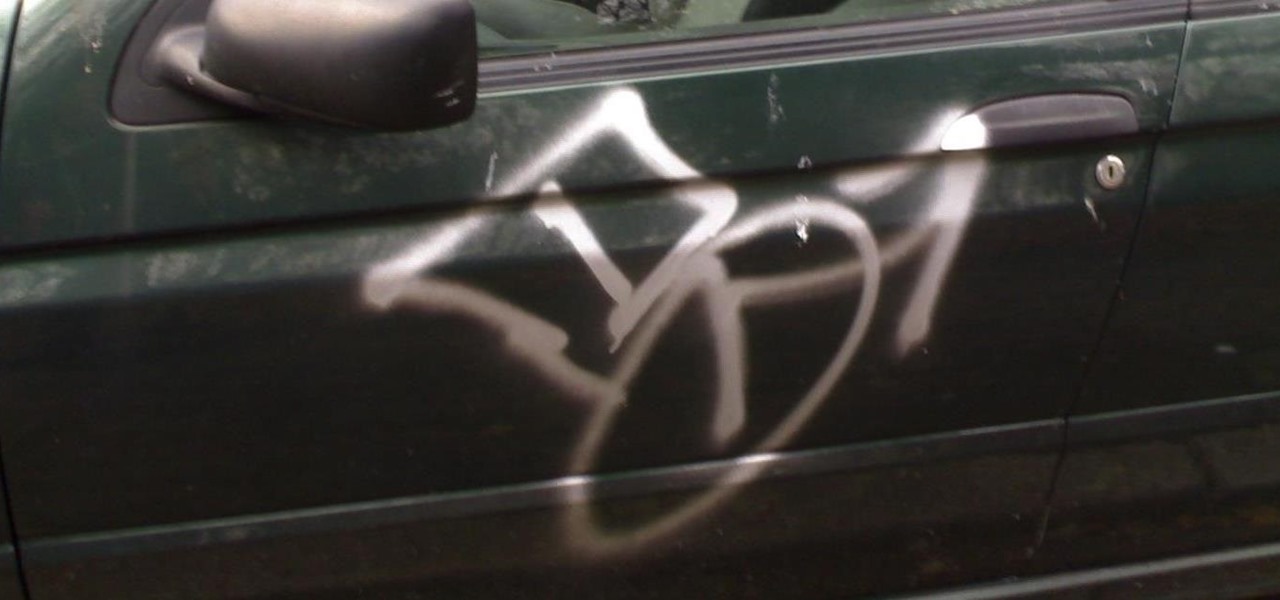All across the country, retailers like Best Buy, Target, and Walmart are gearing up for their Black Friday sales. Brick and mortar stores are already packed to the brim with inventory in anticipation of the craziness that will strike as soon as the doors open the day after Thanksgiving.

Microsoft's HoloLens may the coolest new advancements in technology we've seen in quite some time, and anyone (with deep pockets) can buy one right now. But so far it's been an isolated platform where you experience mixed reality alone and others watch you air tap nothing but air. Developers are working to change that, and we're seeing the first examples crop up online already.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

Virtual reality and horror were meant for each other. You'll get all the positive aspects of experiencing a terrifying situation such as excitement and an adrenaline rush, without any of the real-life consequences, like being ripped to shreds by a herd of flesh-eating monsters.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

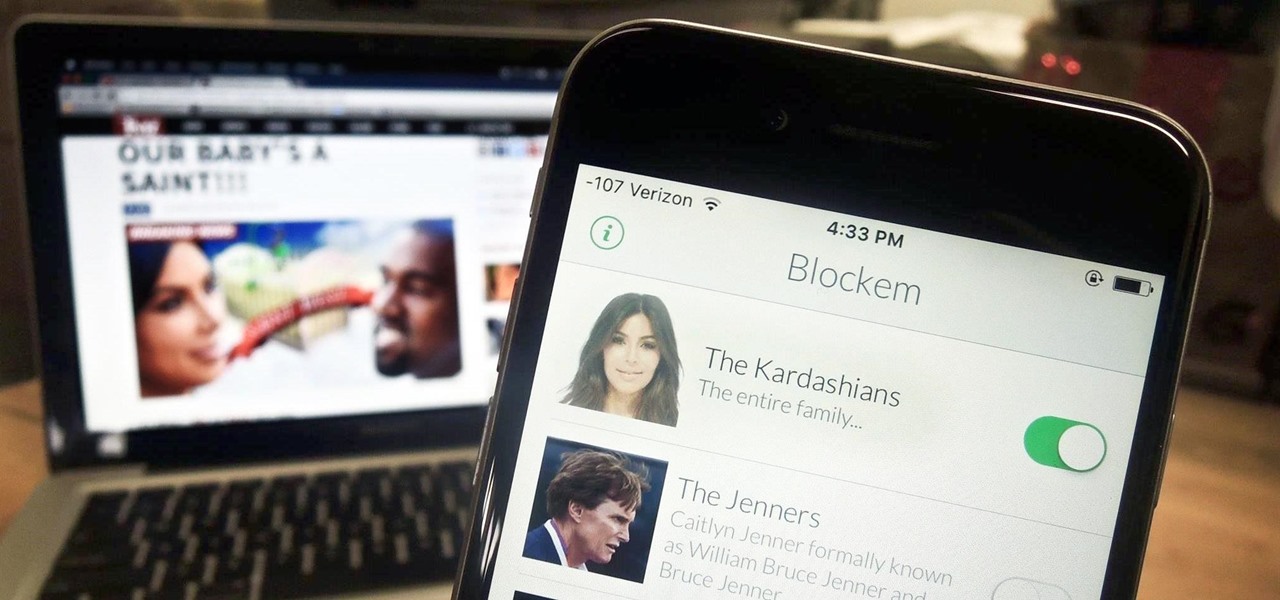
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Hello again, ***UPDATE: Adding links to the other Two articles****

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!
Welcome back Hackers\Newbies!

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

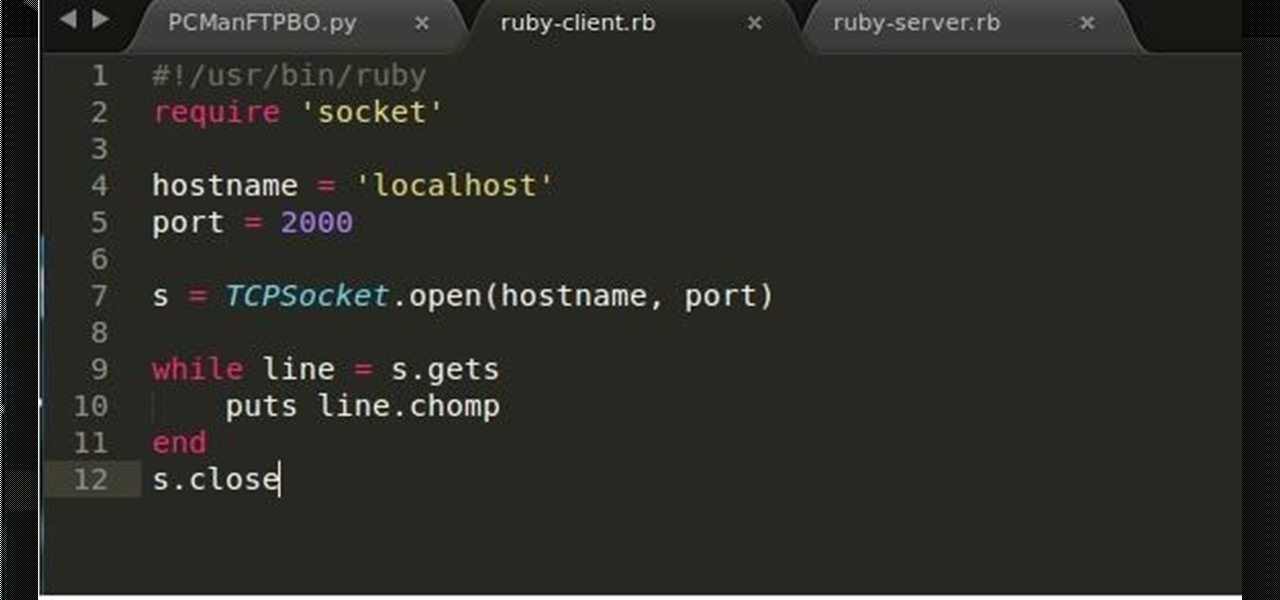
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

For the most part, when you're copying text on your Android device, it's because you intend on pasting it into a different app than the one you're currently using. For instance, you might be looking at a posting on Craigslist. So you copy the seller's phone number, then head to your home screen, switch over to your phone app, paste it into your dialer, and finally make the call.

Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.

In today's world, we're constantly switching back and forth between all of our internet-connected devices. A PC may be great while you're at your desk, but the living room couch is tablet territory, and nothing beats the portability of a pocket-sized smartphone while you're on the go.

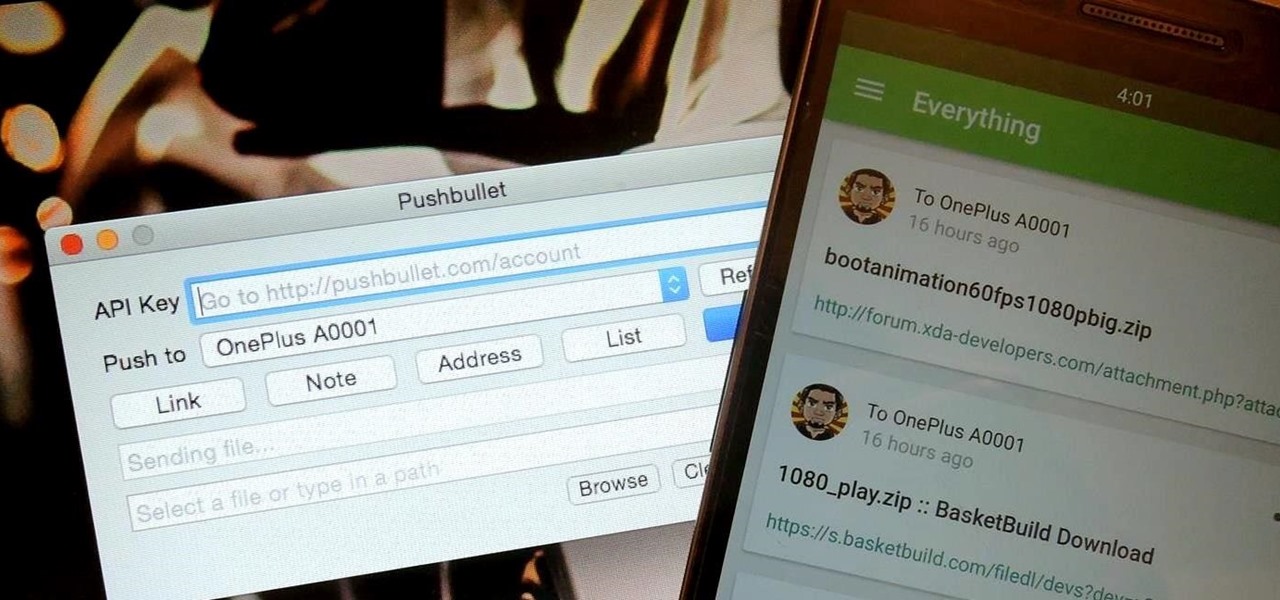
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

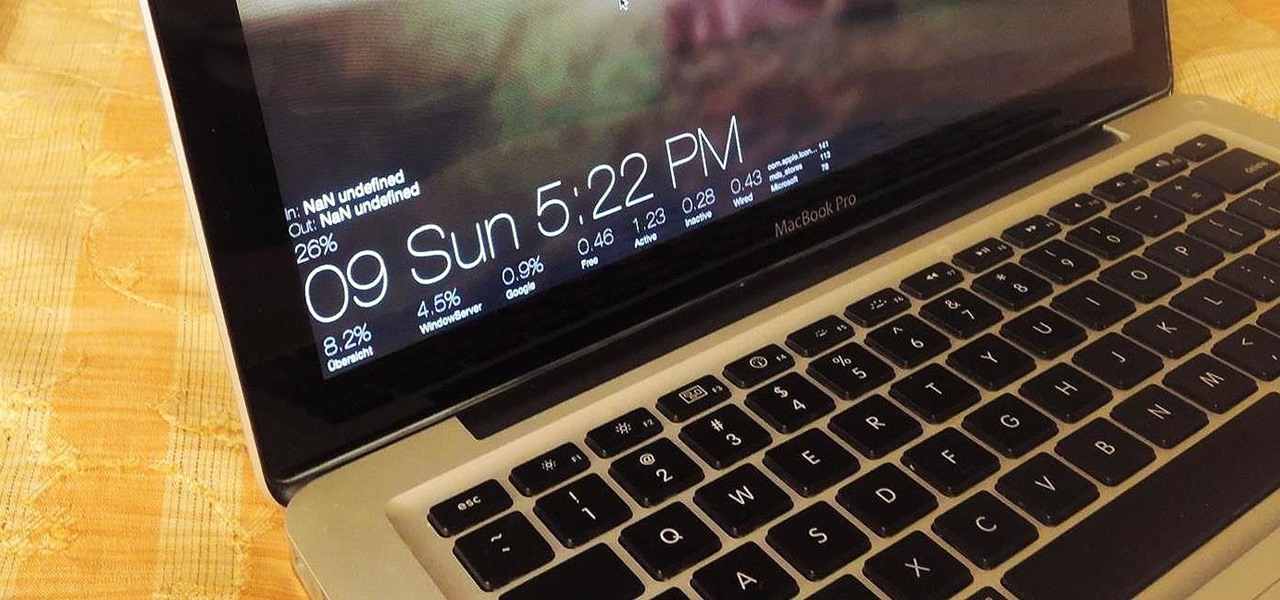
Apple hasn't been the most avid supporter of widgets over the years. Yes, they added them to the Notification Center in Yosemite, but that requires a drawer to be opened and closed whenever you want to check them. In my search for a better solution, I came across Ubersicht by developer Felix Hageloh.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

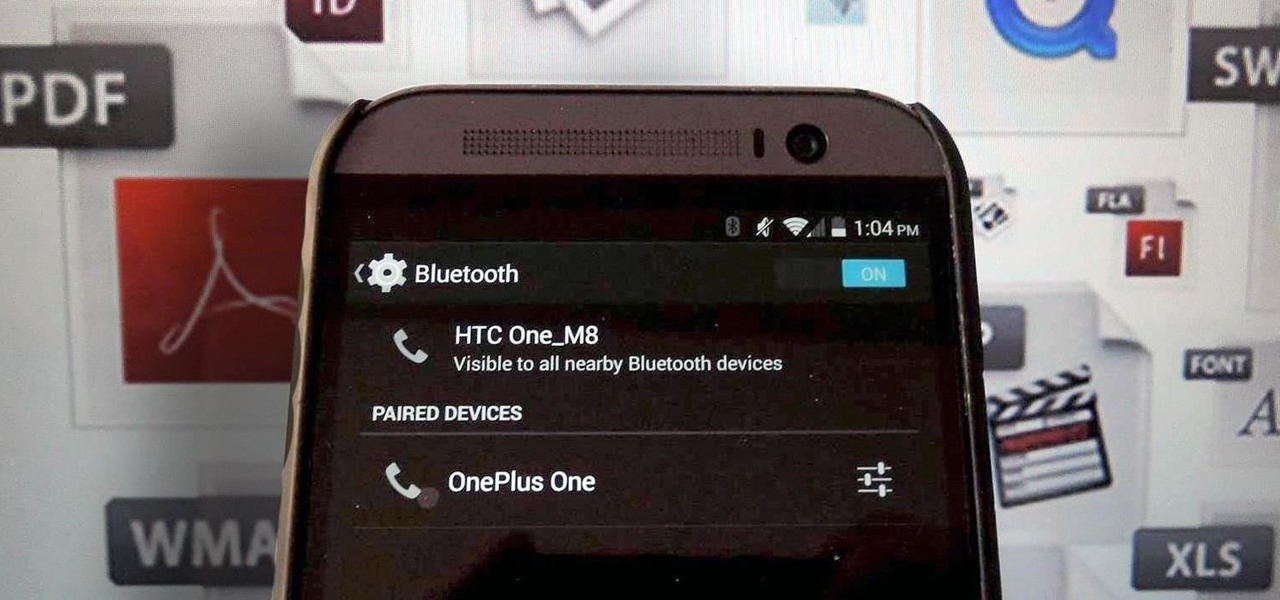
Bluetooth has been a staple on every Android smartphone ever since they began taking over our lives. Despite the fact that every device seems to have the ability to share files with one another, there is a limit to the types of files that can be shared between them.

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

Running multiple applications at the same time is one of the Samsung Galaxy S3's and S4's biggest advantages over Apple devices, and it's a fact that Samsung certainly harps on constantly in their well-targeted commercials.

Thanks to its dedicated ImageChip, the HTC One has one of the best cameras out of all the smartphones currently on the market. Their branded UltraPixel Camera can take full resolution photos while shooting video, has superior auto-focusing, and provides great overall quality for everything from low-light to action shots.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

There are some really talented graffiti artists out there. Some of them are good enough that businesses hire them to paint advertisements, rather than hiring someone to scrub their work off the side of the building.

Search Engine Optimization is important for every successful SEO or blogging campaign. Therefore it is required to be implemented in the correct manner. Google consider many factors while ranking a webpage and it keeps on changing. Some of the common SEO mistakes which you must avoid are as follows:

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

In college, I enjoyed eating, sleeping and making my roommate's life a living hell. My most satisfying prank involved 500 red cups stapled together, filled with water, and strewn across his bedroom floor. He was not happy. To clean up, he had to unstaple each cup, carry it to the bathroom, and dump the water. He was furious, but I was okay with sacrificing our friendship in exchange for a fantastic story that I'll probably tell my grandkids one day. If you're not as cruel as me, there are oth...

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

This video clip shows you how to hit a straight tee shot in golf. There are two parts to this shot. There is the swing path and the face direction. Using a line of golf balls as illustration the demonstrator shows you the path that the head of the club should take as it approaches the ball. Just before impact the head will square up and look in the direction of the target impact. This is called the face direction. There are thus two aspects to a straight shot. The path must be in the correct ...

In this Diet & Health video tutorial you will learn how to check your own blood pressure. Checking blood pressure is a very important part of your personal health routine. Using machines that are widely available, you can easily and quickly check your blood pressure. The target figure will be 140 over 90. The other parameter is the pulse rate. If you are higher than these figures, you need to take a second opinion and consult your GP. Wrap the arm band around the upper arm above the elbow. Pl...

In this video tutorial, viewers learn how to hit a golf ball with a backspin. All golf balls are hit with a backspin, especially with irons. Begin by properly bringing the club backwards. Then return by rotating the hip and release the club with a swing at the target. Finish by raising the club high with a curved shape. The higher that the iron is, the better the backspin will be. Driver clubs do not produce as good of a backspin as an iron club. This video will benefit those viewers who enjo...

Kevin Craft takes us through the steps of throwing a football so that you don't have to be a professional to know how to throw the ball. The UCLA quarterback shows how to hold the ball with one's fingertips. He also goes over how to square one's feet toward the target before actually throwing the ball. A short step movement is followed by a hand motion in the shape of a letter J. Craft makes throwing a football look simple and with some consistent practice, anyone can look like a pro doing it.

This is a video in the Adobe Flash family advances the Flash Action script from 2.0 to 3.0. This video teaches you how to make a flash action script 3.0 button using frames and adding the flash action script coding. Starting with a box and adding text and adding flash coding events, specifically a mouse event and an indication that the button was clicked. Then the programmer adds a variable to the button. She also gives us a hint for the next tutorial which includes a target.