When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.
Software needed: Voodoo motion tracker, virtual dub and blender

First of all you have to understand that this exercise is very versatile and you can actually target different areas of your chest just by twisting your wrists. First of all lie down on the bench and hold the dumbbells in your hands. You can do this upper chest exercise to build your upper chest muscles using dumbbells. Now bring your dumbbells down and then again take them up. While bringing your dumbbells you have to twist your wrists towards inside such that your palms are facing away from...
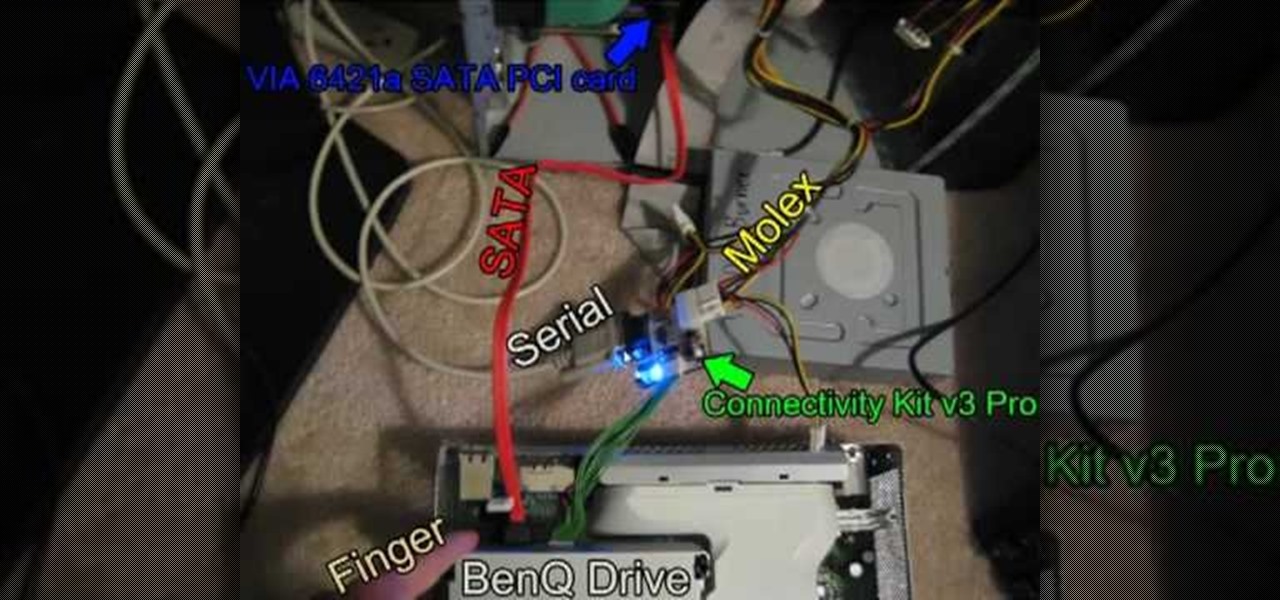
In this Video Games video tutorial you are going to learn how to flash the Benq VAD6038 Xbox 360 DVD drive. This video will show how to do this with the connectivity kit and the jungle flasher. You will need a compatible card for this. VIA 6421a SATA PCI card is probably the best card. Install the VIA card and make the connections as shown in the video. Before you power on the connectivity kit, install the port IO 32 drivers and also the USB drivers for the connectivity kit if you are using U...

If you're tired of getting sand kicked in your face at the beach because of your tiny chest muscles then the dumbell press exercise is for you. This professional tutorial demonstrates the simple workout that can build up your pectoral muscles in a healthy manner. The dumbell bench press is an awesome functional, athletic movement for you athletes. You will work the target muscle better by visualizing the target muscle. Go slow (a 3-1-3 tempo), and visualize that you are squeezing water out of...

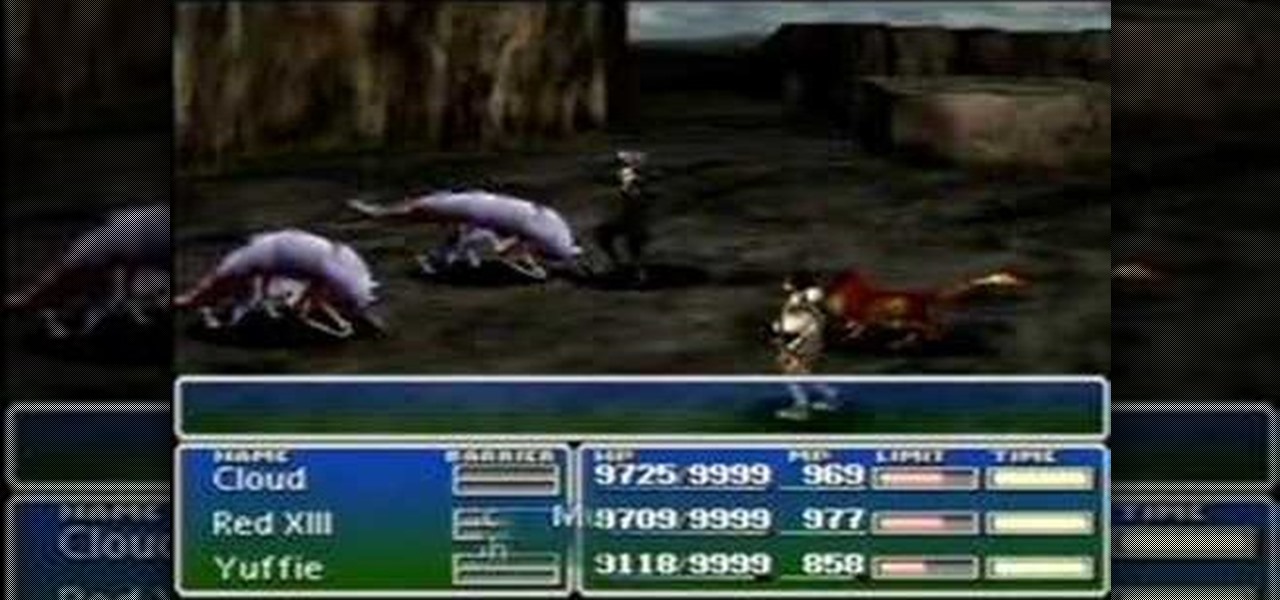
In Final Fantasy VII, it's possible to max out vitality without any store-related progress needed if your strength stat has already been maxed. Take a look at this video and learn how to max out vitality simply by targeting an enemy called "spiral".

Get rid of your water-wasting sprinkler system— but not entirely! Keep your landscape and garden maintained by converting those sprinklers into eco- and pocket-friendly drip irrigation. In this how-to video, Paula Mohadjer from the Cascade Water Alliance explains how you can easily convert your sprinklers into a drip irrigation system.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Another major retailer is putting all its chips in on the relentless rise of selfie culture. Sally Beauty is rolling out kiosks to try-on "some of its best" hair dyes in 500 of its stores throughout the US. The in-store augmented reality-powered kiosks invite you to view yourself on video, overlay a punky (or otherwise) hair color, and snap a selfie on the screen to share your #glowup with friends.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

After parting ways with Papa John's, the National Football League has drafted Pizza Hut as its official pizza purveyor, and the company has hit the field with an augmented reality game to entertain hungry football fans.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

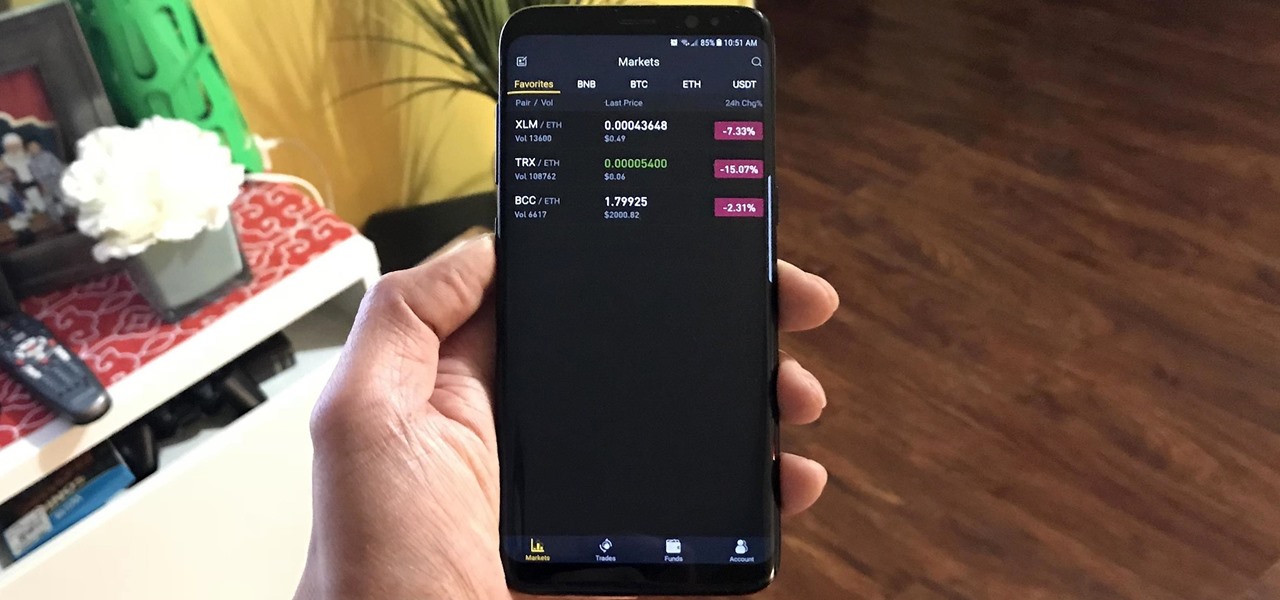
With the sheer number of alt-coins that you can buy and sell on Binance — Ripple (XRP), Stellar (XLM), and NEO to name a few — keeping track of coins you're interested in is a hassle. But with the tap of a button, you can mark trades and alt-coins that are on your radar for quick access on your Binance account.

Android's share intents system is great in theory, but the execution can sometimes be frustrating. When you tap the "Share" button next to a link, app, or file, you see a list of apps you can share that item with. But it seems like every time you use this function, the list of apps is in a different order — especially when it comes to the Direct Share targets at the top.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

Smartwatches are an excellent way to keep track of our smartphone's notifications as well as our own fitness. However, these devices are not usually cheap. If you'd rather not pay a premium for a piece of wearable technology, check out all the Black Friday deals on smartwatches — we've got all the best ones listed right here.

Our smartphones have outlived the Walkman, iPod, and even stereo systems, to some degree. So it makes sense to treat your iPhone or Android device to a quality pair of headphones, whether you're a hardcore audiophile or just an everyday music lover. This doesn't come cheap, of course, so why not buy them on Black Friday?

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

There's a good chance that an iPhone is on one of your Christmas shopping lists, but these things are uber-expensive now, making it hard to justify as a holiday gift — even for yourself. That's what Black Friday is for, though, which can help you save a little bit of cash on an iPhone purchase — or at least, give you something in return to help you get even more holiday presents.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

Tim Cook claimed 85% of new iPhone buyers are switchers from Android back in 2015. Now, after financial analysts noted a drop in the company's stock prices, Apple has unleashed a series of ad campaigns directly targeting the users it needs to win over. That's you, Android lovers.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

Greetings my fellow hackers.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

If you're the de facto tech support person in your family or circle of friends, you know how frustrating it can be to have to hold someone's hand and walk them through every troubleshooting step. Luckily, several options now exist for you to remotely access a Mac or Windows PC, which effectively skips the middle man and lets you get straight to fixing the issue yourself.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.