Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

A good prank requires decent effort, creativity, and impeccable timing. If you're in the office, there are plenty of hilarious pranks to play on coworkers, and for your family and friends, there's everything from toothpaste-filled Oreos, to solid milk, to impossible-to-solve Rubik's Cubes and smartphone-friendly pranks.

The streets of Tokyo are about to get a lot scarier (or more awesome), after Suidobashi Heavy Industries unveiled their latest project: a 13-foot tall, customizable, piloted robot. It's armed to the teeth with a water bottle rocket launcher and a BB Gatling gun capable of firing 6,000 rounds a minute; all for the very reasonable price tag of around 1.35 million dollars.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

Snapchat parent company Snap credits its popular augmented reality experiences and its flourishing Lens Studio creator community to its user growth throughout the year.

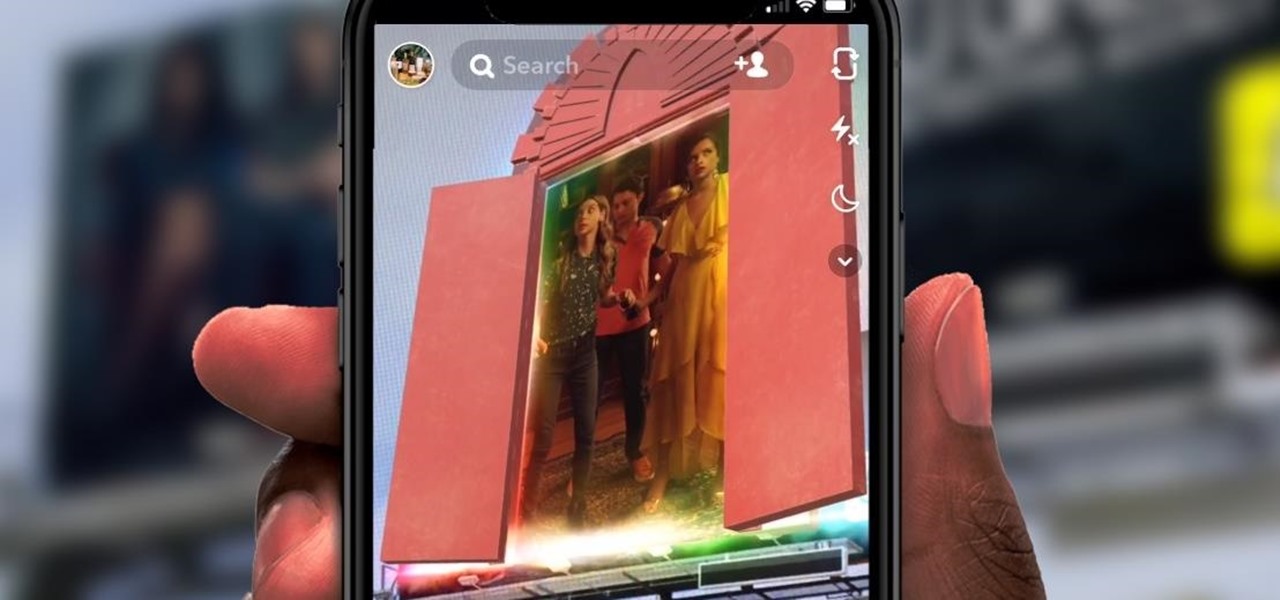
It looks like Snap's foray into augmented reality billboards last year was successful, as the company has returned with two more outdoor advertisements for its Snap Originals series.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

While The New York Times' augmented reality section has largely been dormant in 2019 (so far), USA Today has continued to crank out AR news stories.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

Not content to let NFL's official pizza sponsor corner the market for feeding football fans, 7-Eleven has taken a page out of Pizza Hut's playbook with a promotional augmented reality game.

Fans attending the US Open Tennis Championships in Queens, New York, which kicks off on Monday, will have the opportunity to meet tennis star Venus Williams in an augmented reality game sponsored by American Express.

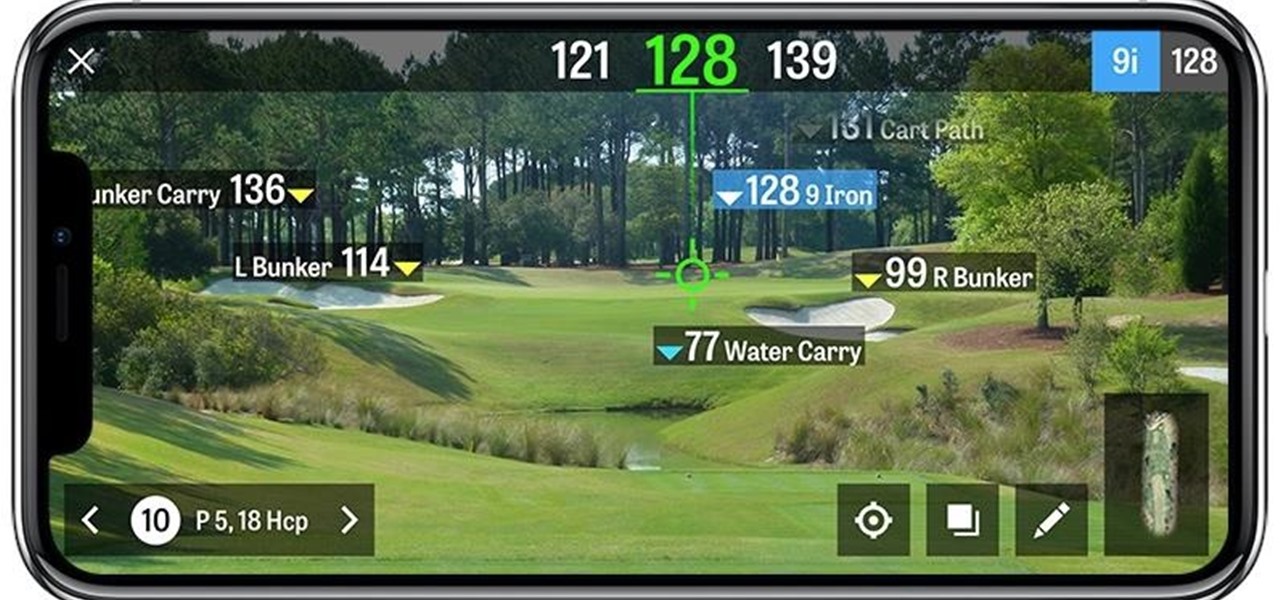
Although some look to golf for some quick off-the-grid time, the scenic hills and blue skies of your local putting green are not immune from the ever-expanding reach of augmented reality. A new update to the Golfshot mobile app brings new AR features to iPhones and iPads designed to help golfers determine shot distances during course play.

Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

At its F8 developers conference on Tuesday, Facebook announced new tools and features coming in a new version of AR Studio, including the integration of 3D content aggregator Sketchfab's Download API.

Assassin's Creed Rebellion is a welcome addition to the popular gaming franchise, garnering great reviews so far. Unfortunately, the game has been stuck in soft-launch limbo for almost a year, with no firm release date in sight. With a little legwork, however, you can try the game out for yourself right now.

As part of its ARCore release announcement, Google also revealed a forthcoming app that's sure to excite those who celebrate '80s pop culture.

Moviegoers who arrive at the theater early are no longer a captive audience for the ads, trivia, and miscellaneous content that precede the movie trailers than run before the feature presentation, as the ubiquity of the smartphone has become the preferred distraction for early birds at the theater.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.

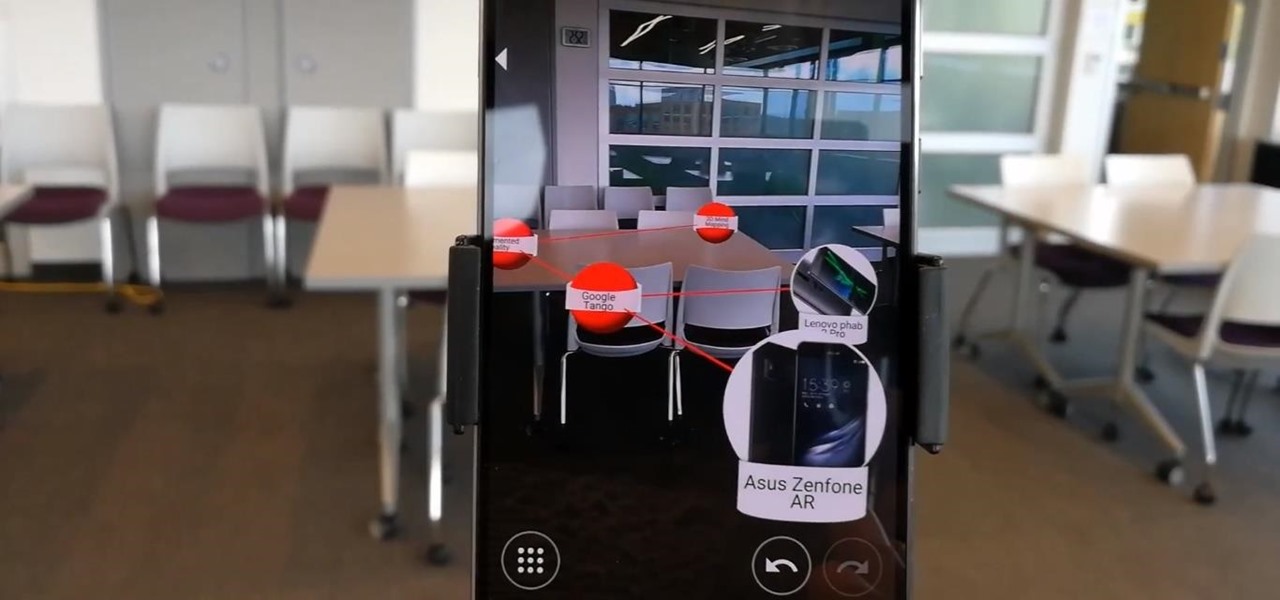
When Google announced its ARCore augmented reality toolkit for Android as its answer to Apple's ARKit for iPhones and iPads, the question from many observers was, "What about Tango?"

Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

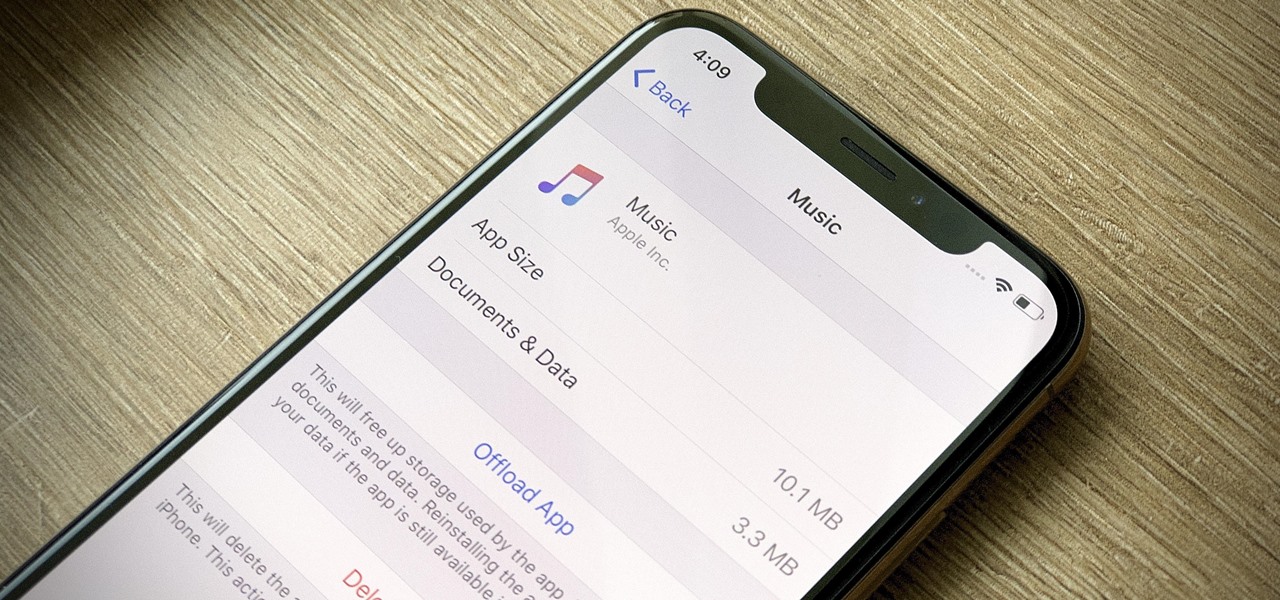
While smartphones are increasing their built-in storage every year, they're also giving you more features that consume all that extra space quickly, like when you shoot 4K videos. So while you may have a load of gigabytes for all your music, it may get eaten up quickly by apps, photos, and videos. Luckily, Apple Music has an auto-delete feature, so you don't have to manage anything manually.

After applying augmented reality as a solution for the sale and marketing of sneakers, Nike is taking the next step in its adoption of AR to improve the customer experience.