After announcing at Google I/O 2019 that augmented reality content would come to Search, Google revealed how it would make that happen with the latest round of updates to ARCore.

After launching its first augmented reality title for Angry Birds on the Magic Leap One, Rovio has doubled back to the platform that made its franchise famous.
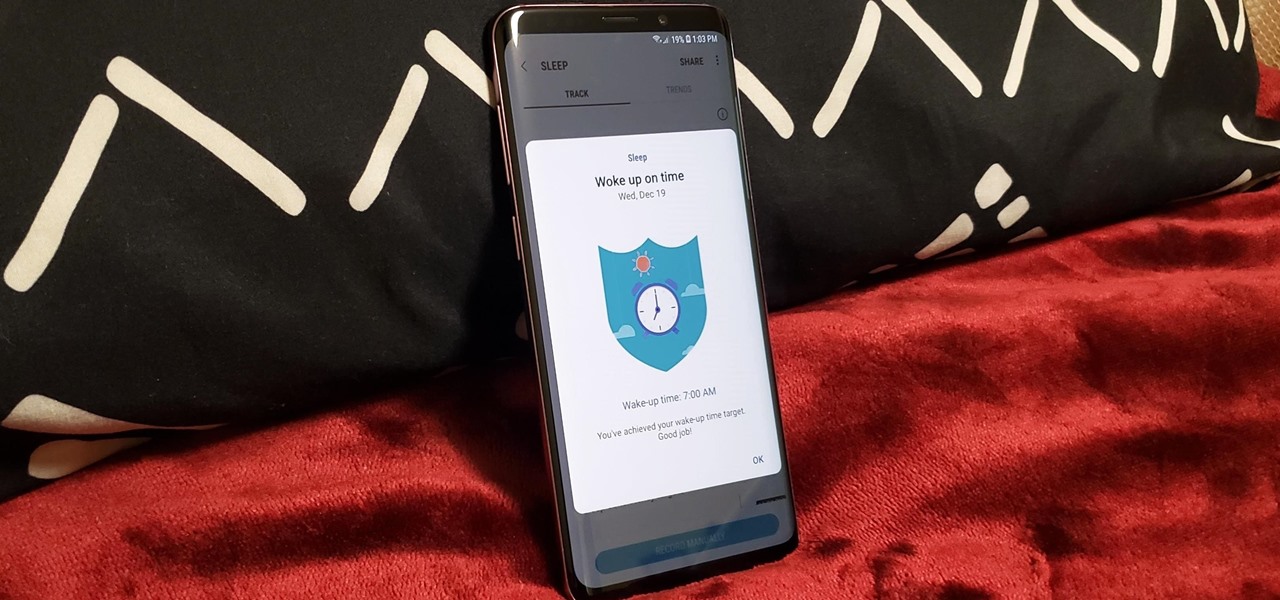
The quality and length of your sleep will almost always dictate how the rest of your day unfolds. Sleeping fewer hours increases your chances of spending the day in a tired and cranky state, while having a restful night's sleep contributes greatly to being alert and productive. Luckily, if you want to track your sleep patterns to figure out how you can improve your circadian rhythm, Samsung Health has you covered.
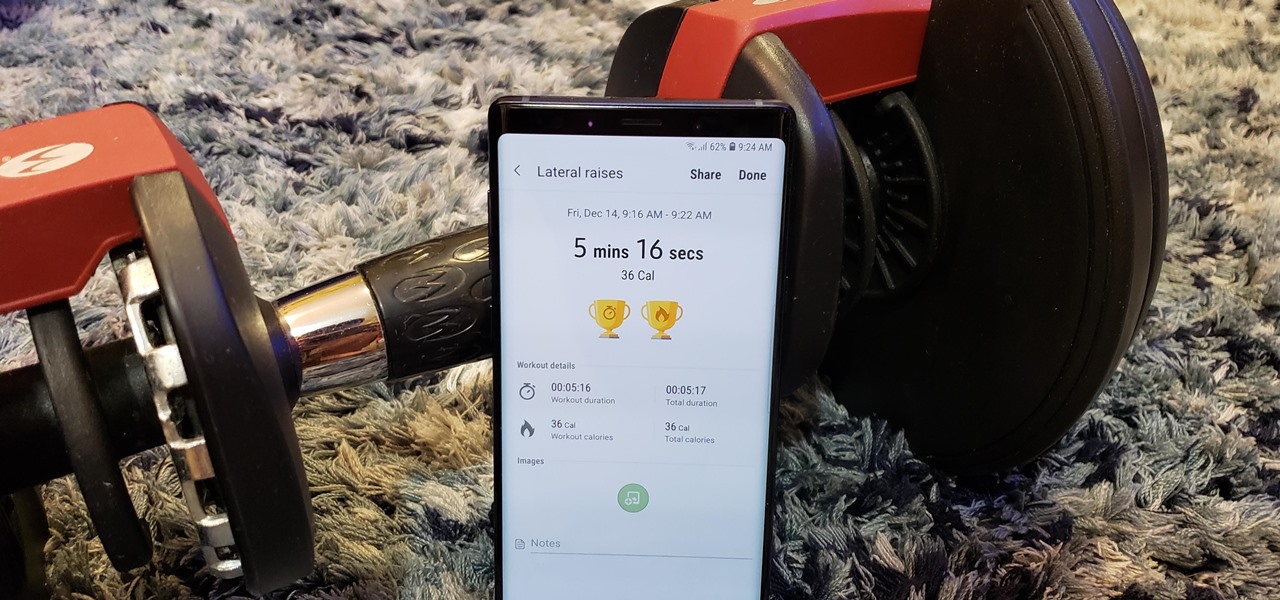
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

WaveOptics, makers of diffractive waveguides, has inched closer toward getting products featuring its technology to market through a production partnership with a consumer electronics company whose clients include Google, Microsoft, and Sony.

Now that we've had a few days to recover from the VR geek versus augmented reality nerd battle between Oculus founder Palmer Luckey and Magic Leap founder Rony Abovitz, we can get back to taking a closer look at the Magic Leap One. This time, we take a very brief dip into the Abductor app.

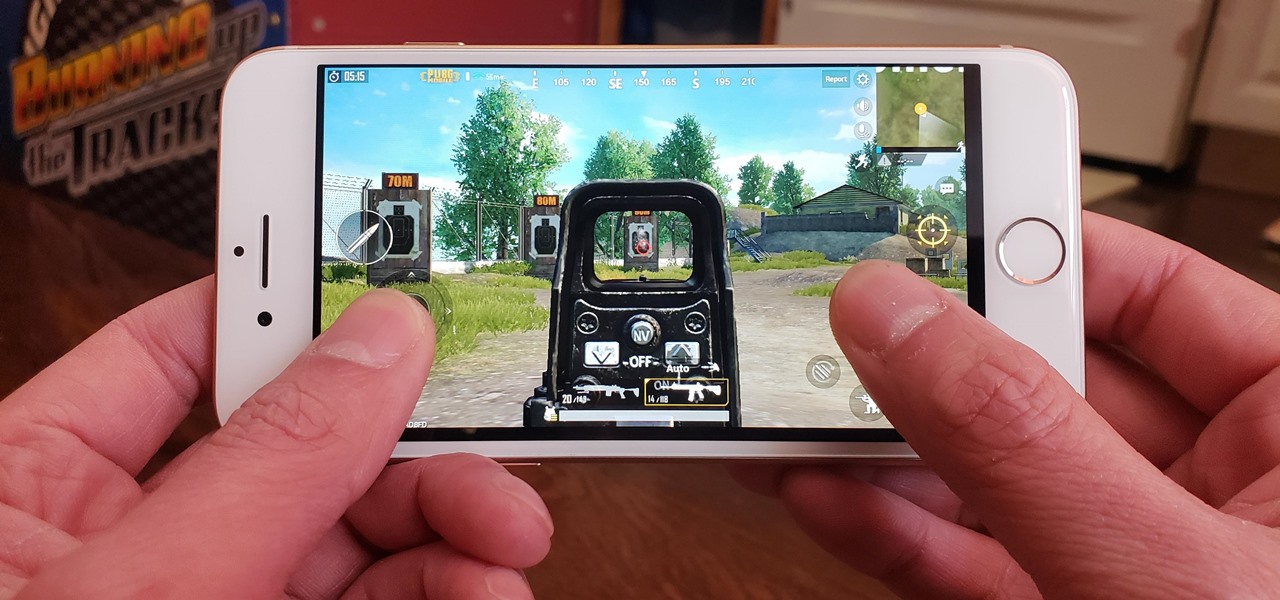
PUBG is continually getting better and more intuitive with each update, and version 0.4.0 is no exception. Besides a new training map to help you practice and a faster-paced arcade mode for on-the-go gaming, the newest version of PUBG now includes a feature that exclusively caters to iPhones from the 6S on up.

This week, saw two companies leaning on AR to prop up their financial futures. On one hand, Apple made quite a bit of AR-related news ahead of its quarterly earnings report next week. On the other hand, Vuzix launched a pre-order program for its Blade smartglasses and closed the largest financing deal in the company's history to fuel its ongoing headset production.

For those who thought the action in Pokémon Go was a bit too pedestrian, Father.io wants to recruit you for a multi-player, first-person shooter that unfolds on the streets of your own city.

Christmas came early for Apple, as the company was awarded more than 40 patents by the US Patent and Trademark Office on Tuesday, including one covering a system for compositing an augmented reality construct based on image recognition.

A survey by ABI Research revealed that only 25 percent of businesses have implemented augmented reality technology in some form or fashion.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

Tom Clancy games, like Rainbow Six and Ghost Recon: Wildlands, are famous for their realistic and immersive gameplay that focuses on covert, low-intensity warfare. Ubisoft now appears to be testing the overcrowded waters of mobile gaming with the release of ShadowBreak, and has soft released the game for both iOS and Android in Canada for further development, which means that with a little tinkering, you can play ShadowBreak in any country.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

Nintendo's first ever game for Android has finally touched down (unless you actually count the abomination that is Miitomo). Fire Emblem Heroes, a classic turn-based RPG optimized for mobile gaming, has come out for Android and iOS in Australia, Europe, and Japan, and is due out in North America and other worldwide locales very soon. Due to Nintendo's staggered release, the game isn't available to us in the United States at the time of this writing, but fret not—there's another way to downloa...

Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

As a commercial and potentially consumer product, one might assume it very unlikely to see the Microsoft HoloLens in the military marketplace. And that assumption would be completely wrong. One company from the Ukraine is currently working on using the mixed reality head-mounted computer for 360-degree vision inside armored tanks. If a tank crew could see the entire battlefield there are in, they would likely have a better chance of accomplishing their mission and avoiding damage. Tanks are l...

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.

The Nexus 7 is a huge jump in screen size when coming from a phone, but obviously this tablet is still smaller than some of the major players such as the Nexus 10, Galaxy Tab, etc. One way to squeeze out a little more space is to eliminate the navigation and status bars.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Today we're going to draw Spongebob! He's going to be facing forward, so even beginners should find drawing this guy to be a piece of cake! 1) Begin by sketching out a rectangle with a broader top and a narrow bottom, make sure it's not too skinny though. This will be the base of Spongebob's body.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

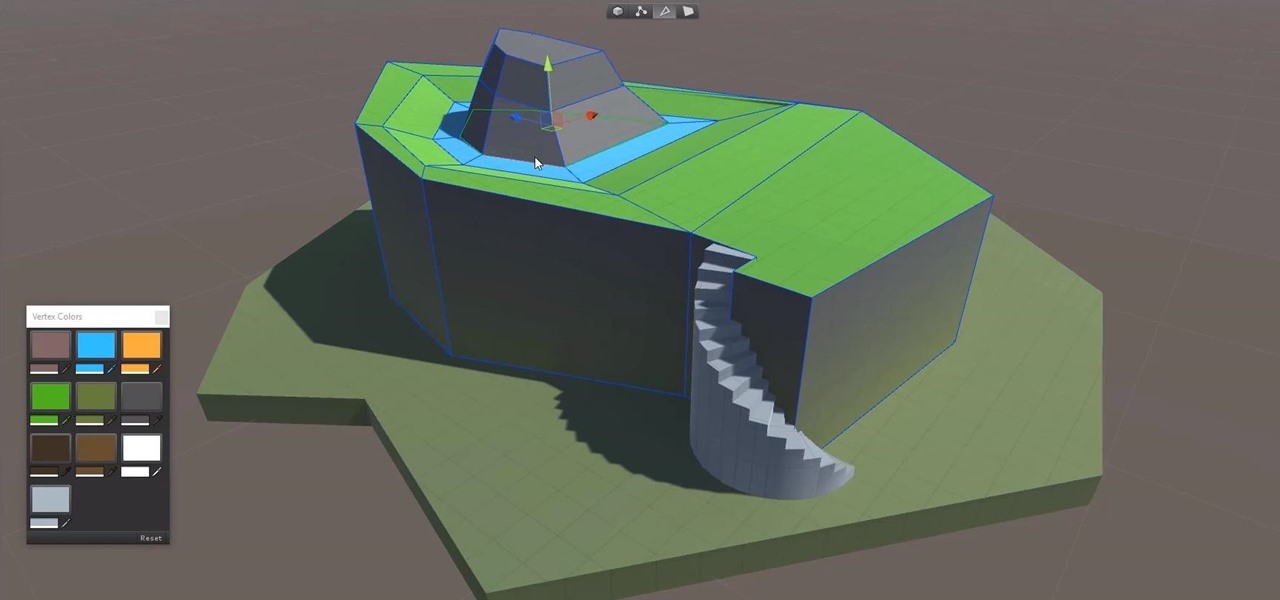
Continuing to take the steps necessary to reign supreme among the top game engines of the world, with a steady stream of major updates, enhancements, and new features, the team at Unity are keeping the user base in a regular state of surprise. At this rate, it's almost like Christmas every few days.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.