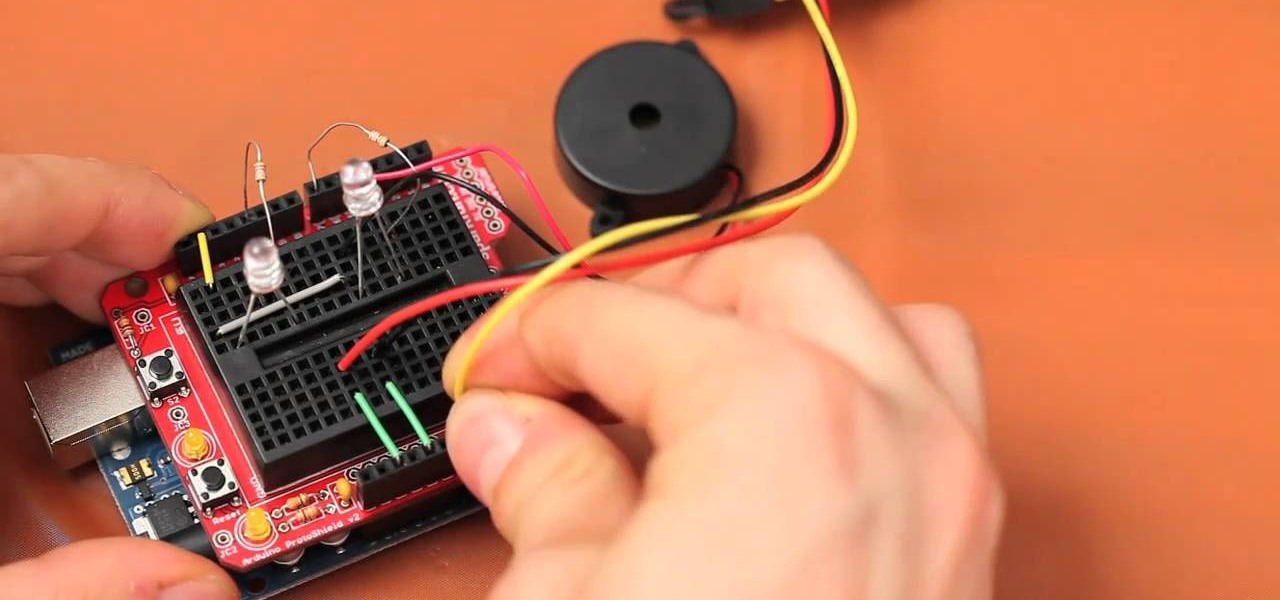
High speed photos are very artistic and look awesome, but taking them without special equipment is nearly impossible. Without this hack and an Arduino, that is. This video will teach you how to use an Arduino and other electronic components to make a DIY high speed photo trigger and take more awesome shots.
The Arduino Ethernet Shield is a wonderful device for DIY electronics projects, and this project is really creative and awesome. In this video you will learn how to use an Arduino, a promixity sensor, and some LED lights to make a proximity-sensing, LED-lit, evil Jack-o'-Lantern that will terrorize your neighborhood and probably get stolen if you don't watch it like a hawk.

Aimed at people who have never created a website before, this tutorial shows you how to use a graphics program to create a website that will have an impact, load quickly and index easily with various search engines. You won't even need to know much coding!
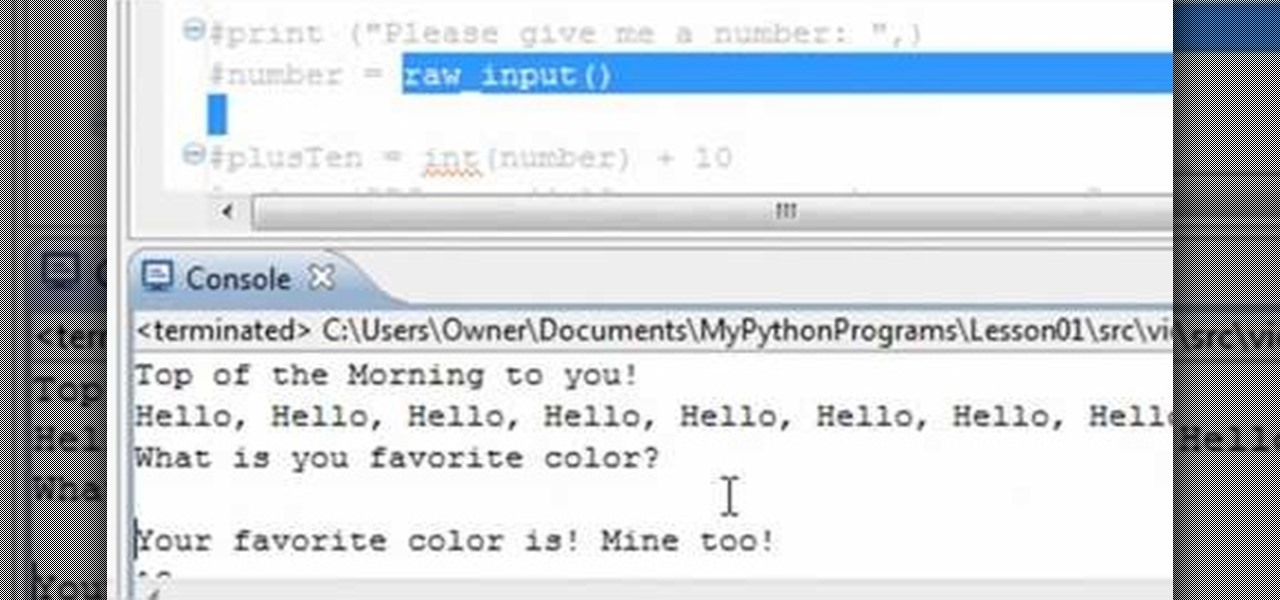
In this clip, you'll learn the ins and outs of using variables and strings when writing code in Python 2. Whether you're new to the Python Software Foundation's popular general purpose programming language or a seasoned developer looking to better acquaint yourself with the features and functions of Python 2, you're sure to benefit from this free video programming lesson. For more information, including detailed, step-by-step instructions, watch this video guide.
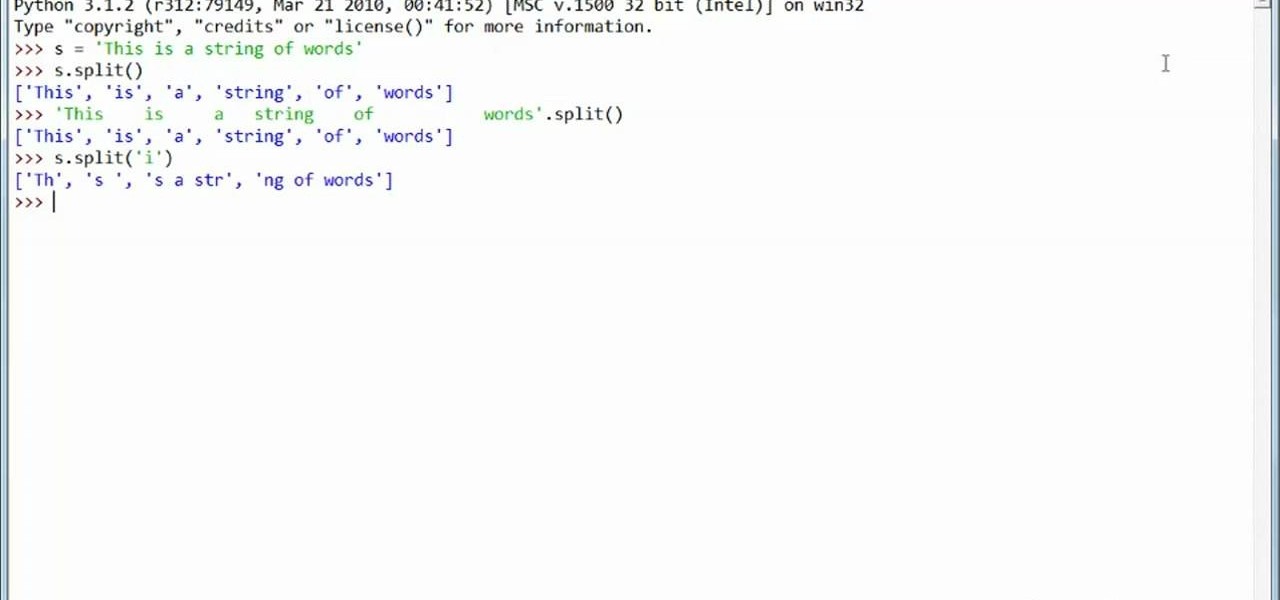
In this clip, learn how to split and join strings when coding in Python 3. Whether you're new to the Python Software Foundation's popular general purpose programming language or a seasoned developer looking to better acquaint yourself with the new features and functions of Python 3.0, you're sure to benefit from this free video programming lesson. For more information, including detailed, step-by-step instructions, watch this video guide.
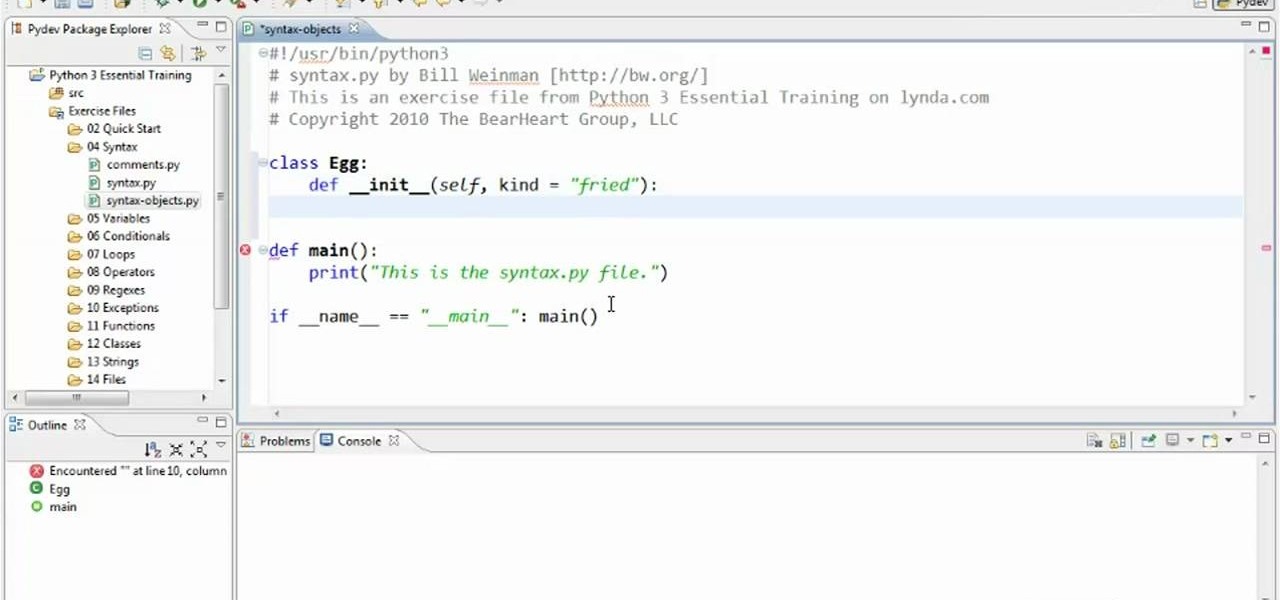
In this clip, learn how to generate and employ objects when coding in Python 3. Whether you're new to the Python Software Foundation's popular general purpose programming language or a seasoned developer looking to better acquaint yourself with the new features and functions of Python 3.0, you're sure to benefit from this free video programming lesson. For more information, including detailed, step-by-step instructions, watch this video guide.

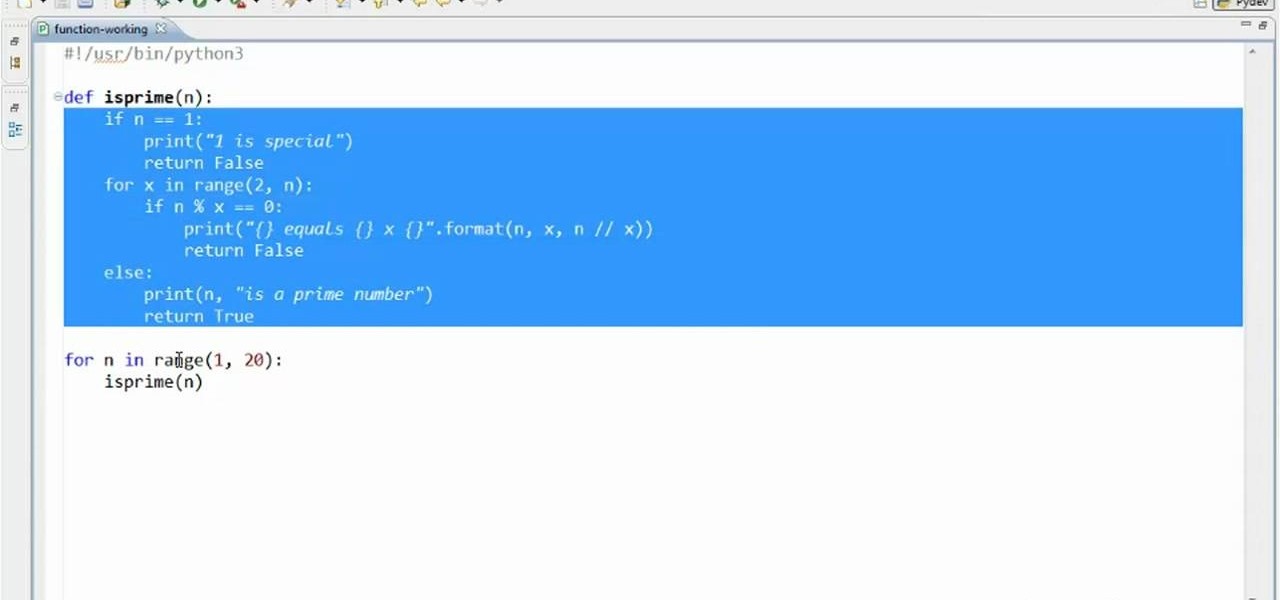
In this clip, you'll learn how to create and call simple functions when coding in Python 3. Whether you're new to the Python Software Foundation's popular general purpose programming language or a seasoned developer looking to better acquaint yourself with the new features and functions of Python 3.0, you're sure to benefit from this free video programming lesson. For more information, including detailed, step-by-step instructions, watch this video guide.

Scripting languages, like coding languages, are among the most complicated and daunting aspects of computer use to master. If you can do it, however, they allow you to do nearly anything you want with a computer. This video will introduce you to the popular scripting language Actionscript 3. This language is crucial to using Flash successfully to create games, movies, and websites, so get this stuff down and then go watch our other Actionscript tutorials!

If you find yourself viewing a lot of Flash content, you've probably seen a moving object or cursor that has a ghostly likeness trailing behind it. Have you ever wanted to create that effect yourself? Now you can, quickly and easily. This video will teach you how to create a ghost effect without having to create a bunch of separate movie files.

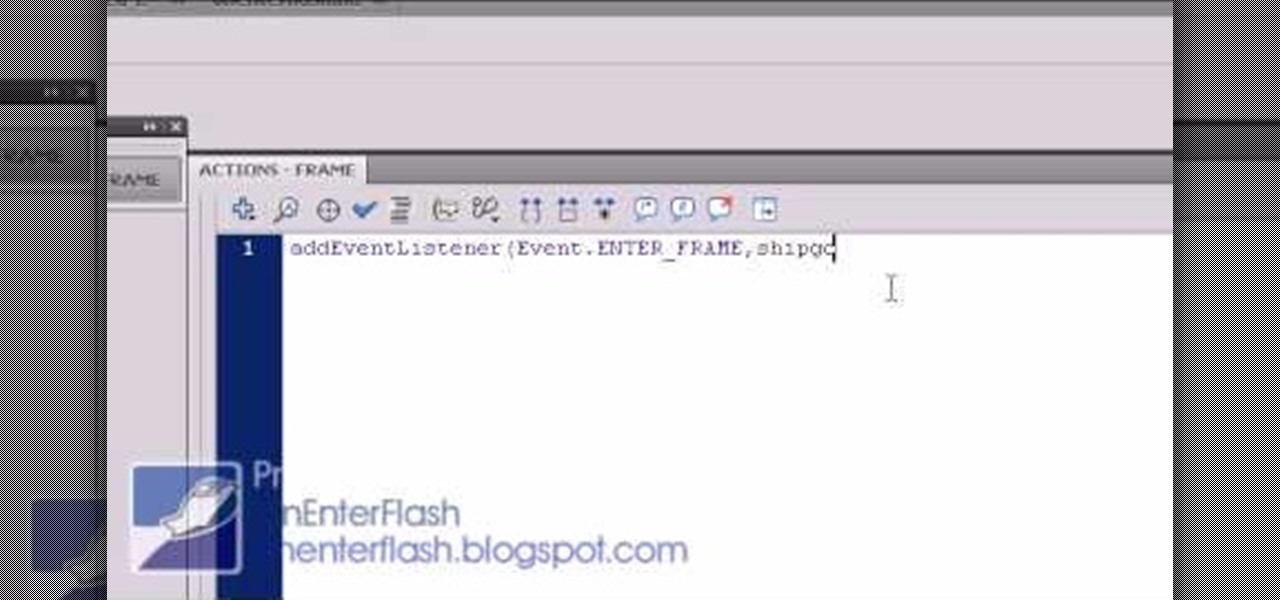
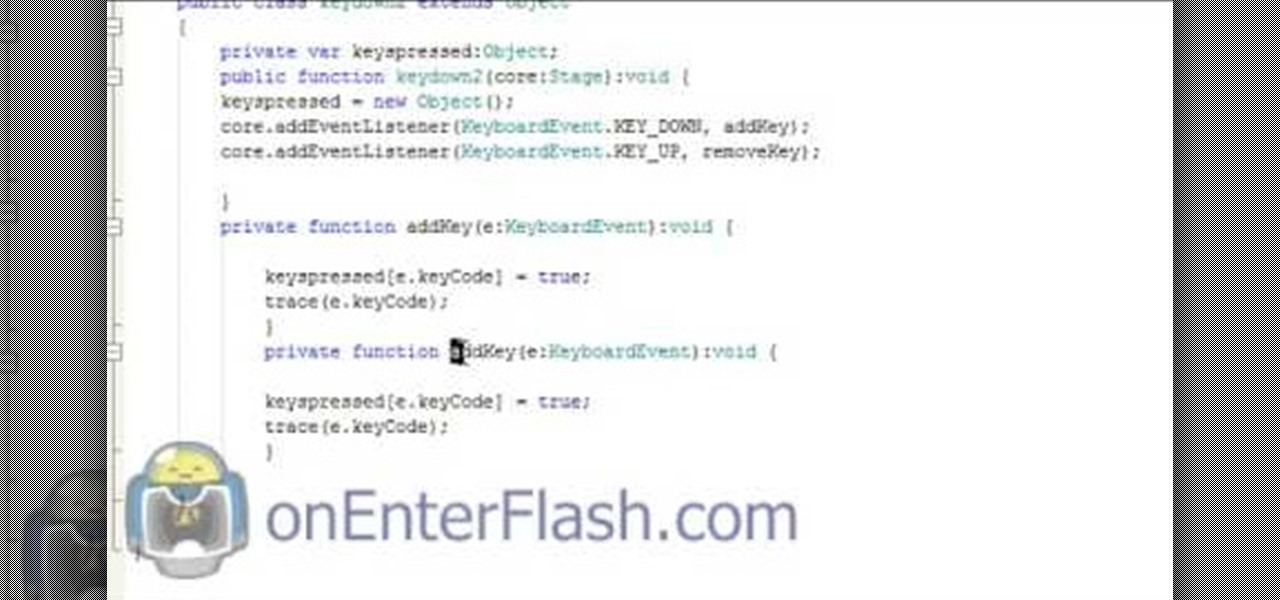
Flash Actionscript 3 is a wonderfully powerful, but somewhat obtuse, tool for creating websites. This video will teach you how to use one particular function in the language, creating a class that has multiple key detection enabled. This will allow you to create a website where users can key in multiple inputs and the website will respond appropriately.

Whether you're new to the Adobe graphic design suite or a seasoned graphic arts professional after a general overview of CS5's most vital new features, you're sure to be well served by this official video tutorial from the folks at Adobe TV. In it, you'll learn how to take Illustrator CS5 designs into Flash Catalyst and create interactive experiences without writing code. Refine your vector art in Illustrator while preserving the structure and interactivity you added in Flash Catalyst.

Learning different coding languages can be difficult. You spend so much time mastering one and getting used to thinking along the channels you need for it that learning something new can sometimes be more difficult than starting from scratch. Starting from scratch, notably, is also difficult.

Learning to code is difficult, particularly if you're doing it alone. While coding may be among the most valued job skills in many markets, the education is sometimes inaccessible.

Learning to code is difficult, but the potential of a little expertise in a few programming languages grants you is worth the effort. Learning to code won't just put you on one career path; many fields, from game design to data science, use coding languages. The All-in-One Coding Skills Bundle can be your start toward mastery of some of the most useful coding languages around for $29.99.

QR codes are so handy. Nowadays, all you have to do to scan one is open your phone's camera app and tap a button. But creating one is a different story — online QR code generators aren't always trustworthy, and most phones don't have a built-in feature for it. Thankfully, Google Chrome now does.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!

One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched this weakness with its iOS 11.3.1 update.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Three variants of the Pixel 2 have appeared in Google's Android Open Source Project (AOSP) code, confirming various suspicions about which processor will power the Pixel 2.

Google has added some fun Easter eggs to Hangouts that'll give you a few more ways to procrastinate throughout your day. All of them (except for one) work on the web browser version, the Chrome app, and the mobile apps for Android and iOS, and are activated by sending a specific message.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

If you just purchased an Android enable mobile device with Bluetooth, then one of the main objectives you'll have on your to-do list is to set it up in your vehicle for hands-free dialing and phone calls. Activating Bluetooth inside your car is easy, and all you need to remember is a little number called zero. Actually, you need to remember it 4 times — Best Buy has answers. The Best Buy Mobile team explains how simple it is to activate Bluetooth settings on an Android cell phone.

This is the 12th puzzle, entitled "Titans of Industry", in Assassin's Creed 2. Code wheel puzzle 1: The key here is in the “4=1” on the blueprint at the left of the screen. Line up the red 4 over the gray 1 and input the following code: 917240. Image 1: This one’s the opposite of the light-bulb “puzzle” from before – just move the dollar sign over the bulbs to extinguish them. Image 2: Highlight the glowing ball at the center of the image. Code wheel puzzle 2: Your hints here are the “2” on t...

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to hack Bejeweled Blitz with cheat codes (07/21/09).

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.