The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try to squeeze every last bit of speed and performance out of it.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...
Just because your Samsung Galaxy Note 2 is on silent doesn't mean that the world stops spinning. Emergencies can pop up at any time, even when your phone is put away during a lecture in class, in the library, or at an important business meeting.

We all know about partying like it's 1999, but what about gaming like it's 1999? The folks over at Irrational Games, the studio behind the new BioShock: Infinite, which was just released today, decided to go a little retro and include a hidden game mode for the most hardcore gamers. By default, the game starts out with the normal Easy, Medium, and Hard difficulties, with "1999 Mode" made available only after you beat the game. But if you enter in one these secret Konami codes provided below, ...
How to draw Lelouch from Code Geass. Follow step by step tutorial of Lelouch from Code Geass. Lelouch's trademarks are his ebony hair, and violet eyes, which he inherited from his mother, and father respectively. Hope you enjoy watching this tutorial! For the full tutorial with step by step & speed control visit: how to draw.
Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

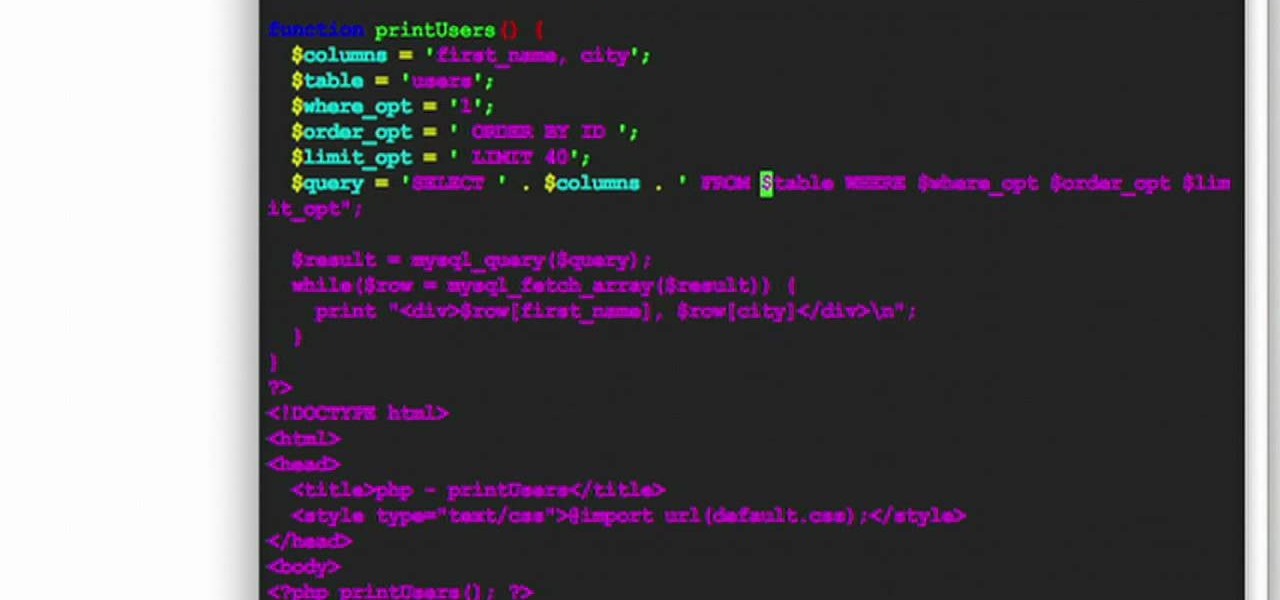
HipHop for PHP is a source code transformer that allows you to optimize your PHP code easily, which will allow you website to run faster on less server space. This video is a record of a seminar on using HipHop done by a Facebook employee who had a hand in it's development. If you make websites using PHP, this will be very good stuff for you to learn.

Need to make an newsletter for your company or business? It's really not that hard to do, if you know a little bit about HTML coding. Ryan Quintal and the Email Dance House sits you down and shows you how easy it is to make a custom HTML email from design to Constant Contact.

This lesson in boffer sword fighting with the Knights of Gray is the most important of them all! This video tutorial for all you LARPers out there focuses on the rules and the code of foam boffer weapon fighting.

In this video from MegaByteTV we learn how to block ads on a web page using the Google Chrome browser. If you see an ad on a website, click the icon which is actually a shortcut to a JavaScript code. It will then block the flash on a JavaScript website. Automatically all of the flash on a page will be blocked. You can do this by using the link provided in the box underneath the video. Copy and paste the JavaScript code into a new bookmark on your browser. Right click the bookmark bar and hit ...

You can add banner ads in thesis header. To do this, first go to your word press admin and click on custom file editor in thesis option. Now select custom_function.php in edit selected file option and click edit selected file. You will get a warning so to do this you need to use FTP. Go to the path in FTP which is showing in the video and then click on Launch.php and now copy the code which is showing in the video and paste it in the launch.php. But you have to change your header image path i...

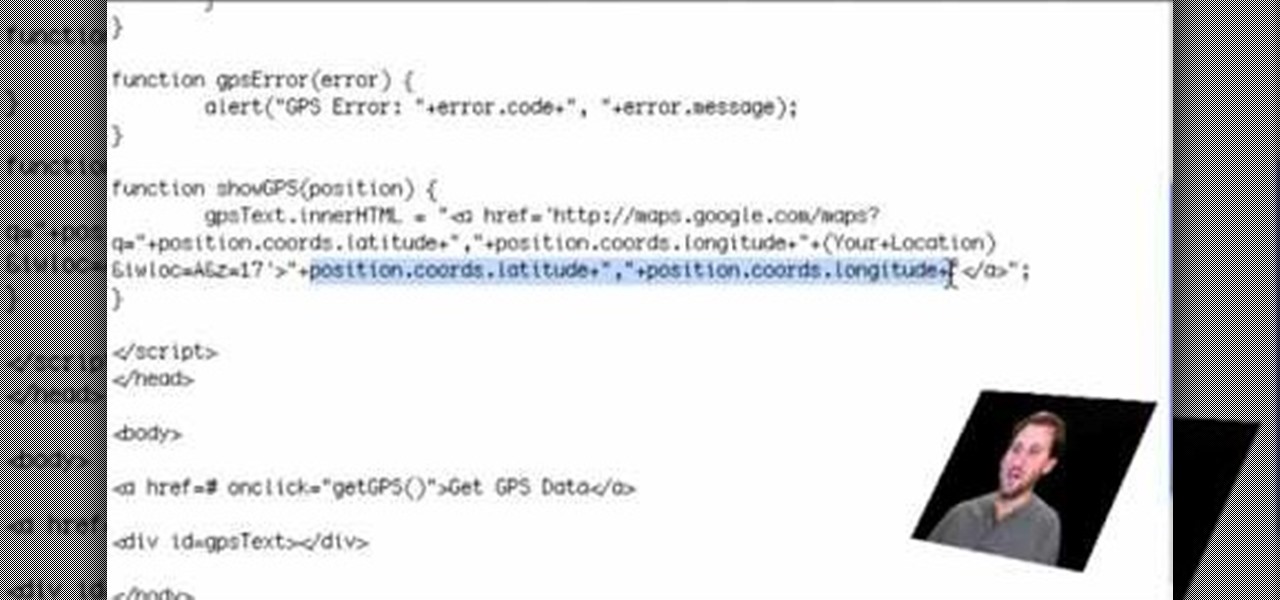
If you are a web developer, you can check your iPhone location in a webpage by using these simple java script codes.

In order to build Google Chrome extensions, you will need to familiar with scripting and codes. These are small programs that add additional functions for programmers. It is a compressed directory. These files must have a particular name: i.e. "manifest" (manifest.json). An extension will have at least one of the following: browser actions, page actions, content scripts, and utility web files.

John Roy demonstrates the tutorial to view or retrieve layouts that ens with .swf. SWF files can be viewed by pasting the url in the address box.

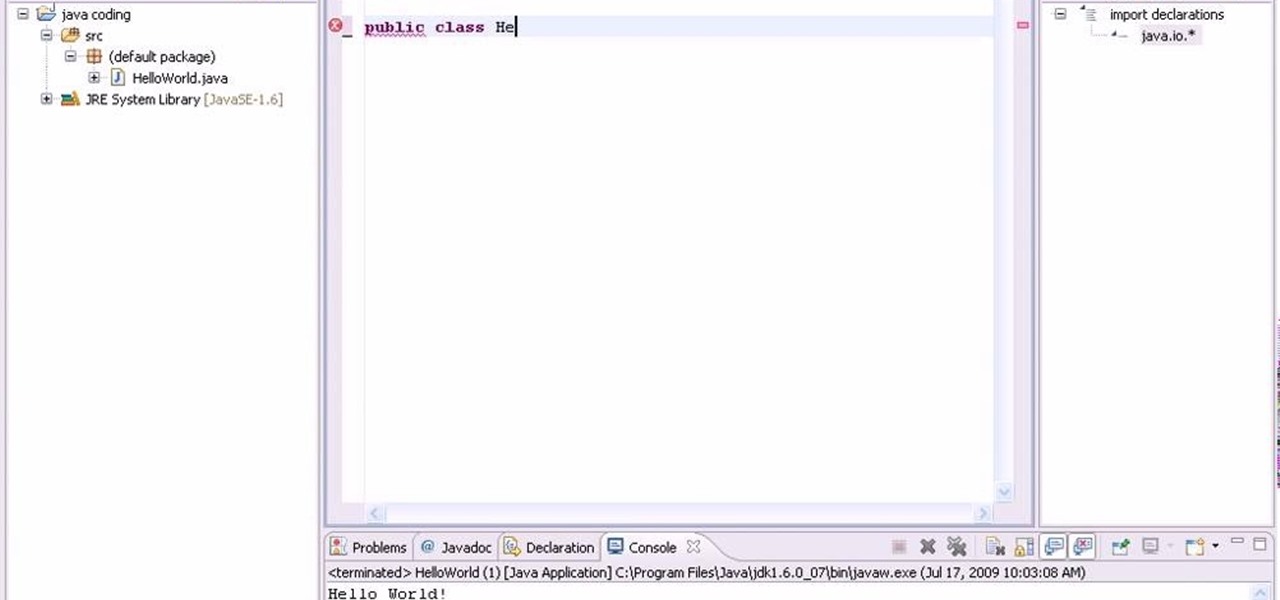
Java is a wonderful programming language which is widely used all over the world. To do programming in Java you will need a Java Development Kit which is also called as JDK in short. This can be downloaded from the Java Website for free. To improve and assist in your developmental activities you will also need an IDE, which is an Integrated Development Environment where you can develop, compile and test you code at once place. Though Java code can be written in a normal text pad and compiled ...

In order to create a custom caption box in WordPress you'll need to go to your dashboard. Here click on appearances, then on editor. Now over on the right select the sidebar option. Here you'll see some code, what you need to do is find the word that you want to replace on the main page, you can use ctrl+F to find the word. When you've found it within the code just replace it with whatever you want and then press the 'apply' button. You'll see that the main page will now be displaying the wor...

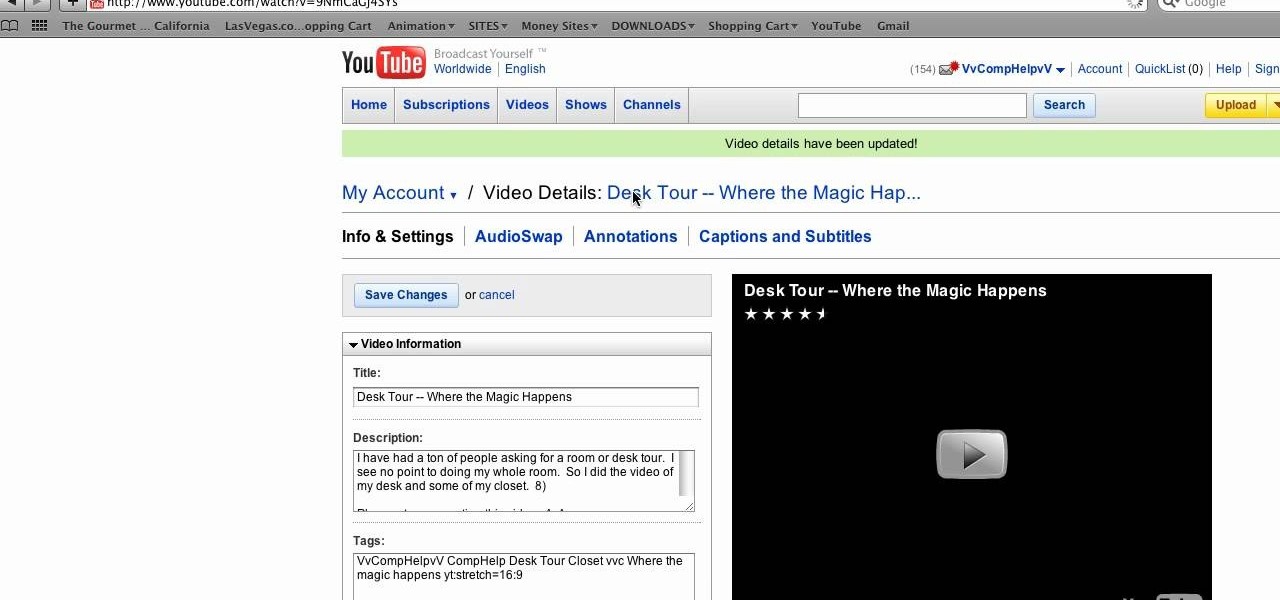
CompHelp uses his Mac to show us a new feature that the website has recently introduced. This feature allows people to use a simple code to crop, change, stretch, and even increase the quality of YouTube videos before they are uploaded. He starts out by showing viewers the memo where this information was released, then goes step by step to show interested parties how to use the special codes.He uses one of his own videos as an example, demonstrating what was wrong with it, then using the new ...

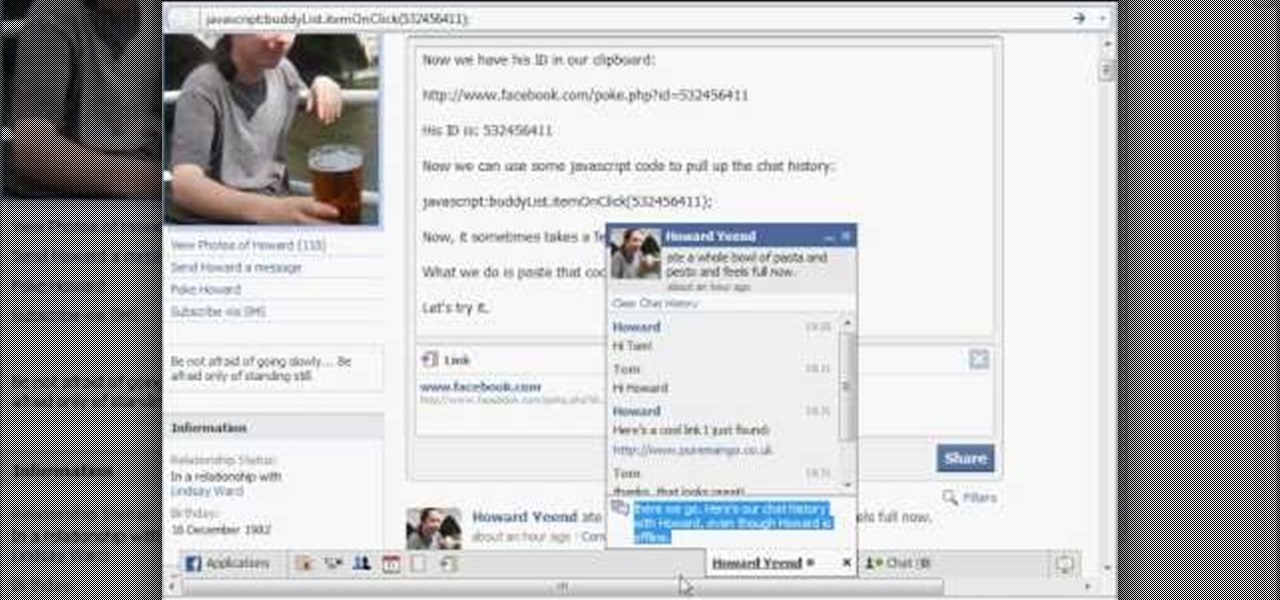
A Facebook profile page shows up explaining the steps on how to get chat history of a friend on Facebook. It explains that you need to go to the profile of the person you would like to find chat history with. It then explains steps on how you can copy there Facebook ID. Once you have accessed that he provides you with a JavaScript code to use to pull up chat history. He gives you step by step examples explaining how to set up the ID and apply it to the JavaScript coding. Once that has been es...

Learnasyouwatch shows viewers how to automatically play YouTube videos. First, you need to open your web browser and go to YouTube. Find the video you want to automatically play or upload your own video to YouTube. On the ride bar there is a section that says 'Embed'. Click on the pin wheel icon next to it that is 'customize' and you can set various parameters. Now, you need to copy the embed code and right click and copy this code. Paste this code into a word document. You will need to add '...

Cool tips and tricks on Facebook give you some extra edge on others. This trick will demonstrate that how to talk to your special loved ones that no one else can understand.

Going to be a nurse? Then one important part of your nursing responsibilities involves doing a daily check of the code blue cart or crash cart. The crash cart is checked every shift for emergency items and function. In this how-to video we review the nurse’s responsibility to test the defibrillator oxygen tank, most hospitals change tanks at 500 or 1000 psi. Follow along an see how simple it is to do a daily check of the code blue cart.

Looking to install a physics engine for Flex or Papervision? In this video lesson, Mike Lively of Northern Kentucky University demonstrates how to install the Wow Physics Engine into Flex 3 for use with Papervision3D. For more, and to get started installing the WOW-Engine on your own machine, take a look!

In this video tutorial, Chris Pels will show how to make standard HTML elements in an .aspx page accessible from server side code so they can be used in page processing like a standard ASP.NET server control. First, see how the addition of a runat=”server” attribute to a standard HTML control like a div allows it to be referenced in server side code with full Intellisense. Next, see several examples of how you might manipulate HTML elements on a page with this technique. Lastly, see how this ...

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.