Tol Barad sounds pretty exotic, but really, what doesn't in World of WarCraft: Cataclysm? If you're a WoW: Cataclysm player and haven't heard of the Tol Barad zone yet, then what in the hell have you been doing? Letting a bot play your game? Maybe the WoW Glider? Tsk, tsk.

Good skin care begins with knowing what kind of skin your have, what special issues you have, and what products work best for your skin. In this video we show you how to identify your skin type and choose skin care products that best suit you. Skin Care Routine

Marketers from Facebook who design ads for advertisers can ask them to switch over to higher end product in which Facebook would be designing or hosting themes based on their products. This product theme will have a separate scroll area where advertisers (after buying rights from Facebook) can scroll latest development happening in their company or the latest offers with which company is coming out. Through above setup Facebook gets fees for hosting personalized theme as well as providing a s...

First Things First Before you can begin to work on a damaged panel, you must determine what type of material that you are working on. For instance, the panel may be mild steel, high strength steel, aluminum, plastic, sheet molded compound, or a number of other types of material.

The CNA certification exam can be stressful at times, especially on the clinical exam portion. However, despite the exam difficulties, everything has a solution. Qualified nursing assistants are preparing various CNA study techniques and CNA study guides just to reduce any test anxieties and stress.

Never leave the house without doing these 7 things. It doesn't matter how expensive your clothes are if you have issues like bra straps hanging out. Here is a quick checklist for you. Check for for lipstick stains on your teeth.

It seems even Al-Qaeda is not immune to World Cup hysteria. The international terror network issued the following demented statement, early in the pre-season:

Apple just released iOS 12.5.1 (build number 16H22) for iPhone 5S, 6, and 6 Plus, as well as iPod touch 6th generation, in addition to iPadOS 12.5.1 for iPad Air, mini 2, and mini 3. The update fixes an issue in iOS 12.5 where Exposure Notifications could incorrectly display logging profile language.

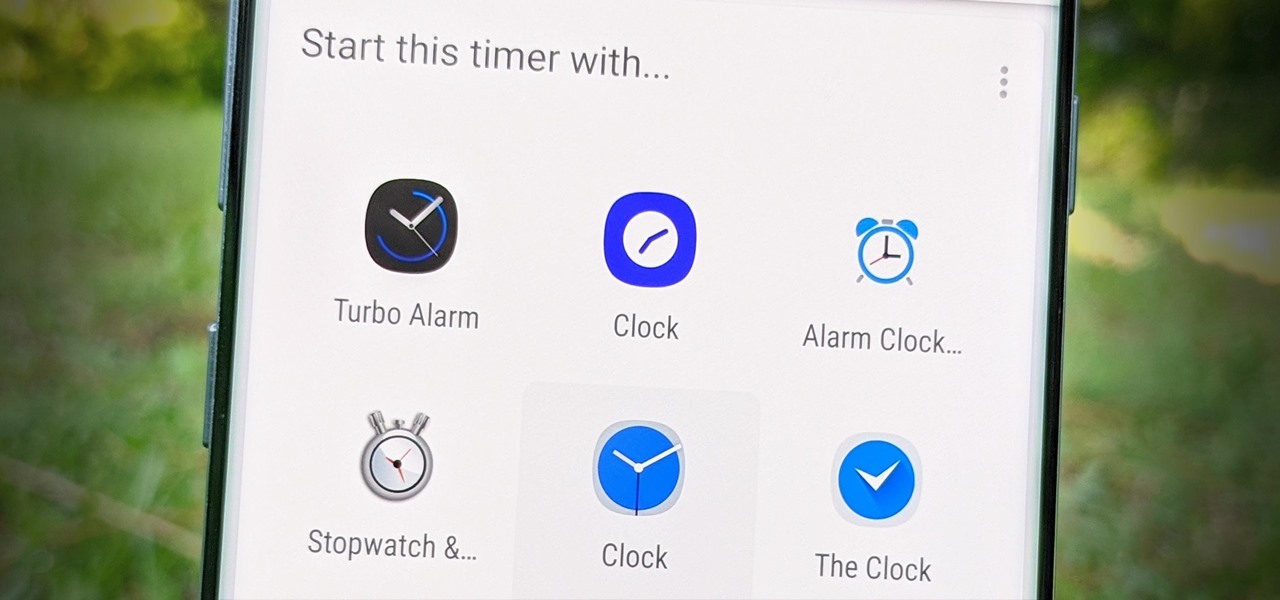
If you don't use the stock clock app, you've probably run into an issue when using Google Assistant on Android. By default, it'll only use the clock app that came with your device to set timers and alarms, effectively ignoring your third-party clock. But there's a way to fix this.
The Power of One is one of those books that I really should have read years ago. I’ve certainly meant to read it for a long time so this was a satisfying title to cross off my list. It’s stunning that this was Bryce Courtenay’s first novel. I look forward to reading his others because if this is where he started, he’s a talented writer.

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

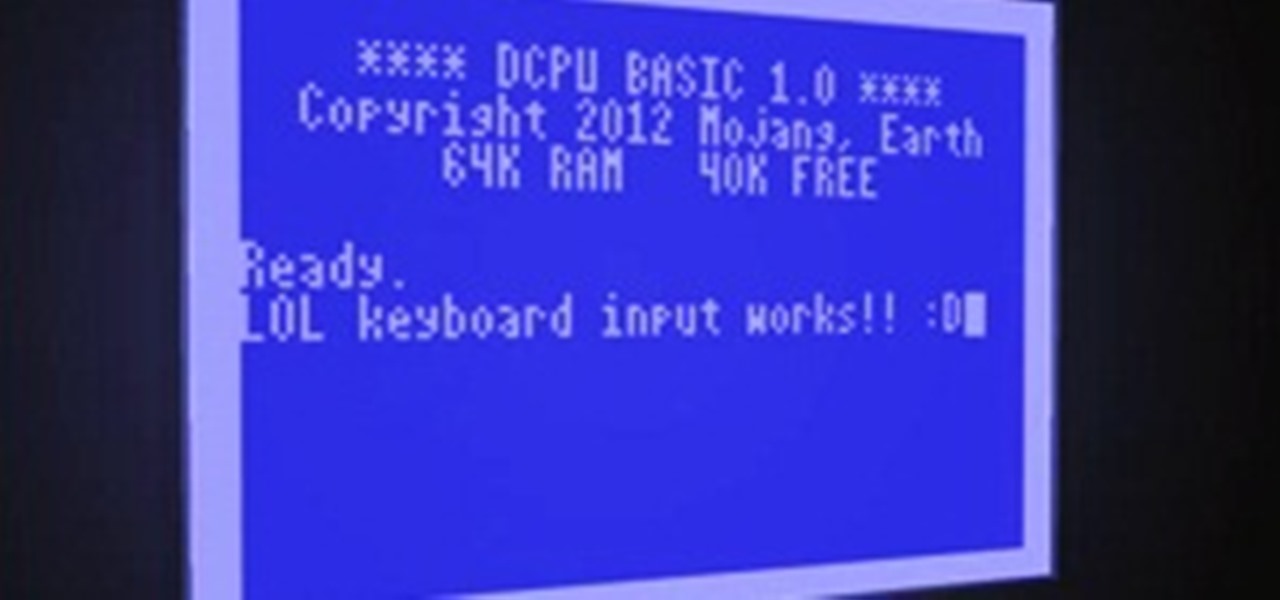
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered with spending enormous amounts of time writing anything much more complicated than a "hello world" application in assembly. What's on the top of everybody's mind is creating a compiler for a more widely used language.

I'm back with the third part to my laser weapon series (see part one and two), and I'll be explaining the function, application, and potential of semiconductor lasers, aka laser diodes.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

I'm sure everyone has heard about Google's changing privacy policy on March 1. It's scattered everywhere, with notification bubbles on Google Search, YouTube, and the rest of their products. Click here to see the new privacy policy that will take effect on March 1, 2012.

This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Content is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

Snapshot: 12w08a brings us a few nice things a few things I'm not so sure about and a few things I just hope Mojang doesn't incorporate into the next official update.

Continued from Organize Yo'sef Part One!

The Stun-Gun In this article, I'll show you how to make a small, weaponized highlighter. Before I get into how to built this device, let me warn you. This device is harmful! When used, it can cause burns and/or serious muscle spasms. The voltage is potentially deadly! DO NOT attempt to build this device unless you are experienced with safety, electronics, soldering, and understand circuit schematics.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Since the launch of Edit on a Dime several weeks ago, I’ve been putting a variety of automatic video editing apps though their paces. One of the first tested was Magisto, a web-based app that’s directly accessed through YouTube, which I enjoyed, but found some obvious problems with. Since then, I’ve been in contact with Oren Boiman, CEO and founder of Magisto, who was kind enough to address my concerns.

Windows 8 Beta (Developer Preview) It wasn't that long ago Windows 7 was released - now Windows 8 Beta is here. I did do a Google search to see when the stable version will be out but wasn't able to find an official statement from Microsoft. However - I saw several articles on Google hinting that the final release might be in August or there about.

Having bills to pay is one of the worst parts of life, especially around the holidays. And if you're extremely unlucky, you might also have to pay some hefty medical bills. This can put a heavy damper on plans, wants and needs. What's worse? The people that you owe money to are pushy and always bother you to pay in a more timely fashion, or worse, pay bigger premiums.

Have you ever wondered how credit card numbers work? I mean, how they really work? How do they come up with the numbers? Credit cards actually follow a very specific pattern. Let's take a look at how they're set up.

Google+ is taking over more and more of Google's core properties. This week, we've seen several announcements from Google blogs about new products, new features, new looks, new integrations. If you're like me, you actually want to know where to go for all the latest information on Google products.

If you have made the switch from Windows to Linux, I want to congratulate you in advance. I'm sure you have noticed a huge performance increase when using Linux over other operating systems. This is only half the battle, though! Most users who are new to Linux end up using Ubuntu. I have no gripes with Ubuntu, but I do not agree with their philosophy. It almost mimics Windows. Ubuntu favors ease of use, and despite valiant efforts by the development team thus far (Ubuntu is crazy fast), all o...

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

In these weekly Scrabble Challenges, so far we've covered two-letter words, double bingos, high scoring moves, triple-triples, last moves, parallel plays, phoneys and opening moves. For this week's puzzle, we're revisiting the strategy for opening moves.

Social network fatigue sets in when it starts to feel impossible to keep up with all that new content from your friends, followers, and acquaintances on a daily basis. You lose track of stuff you wanted to read more about, and you miss important news from your friends, but are bombarded with inconsequential details from people you don't actually care about. What's the solution? Filter your streams so that you only see the content you do care about, and get rid of the rest.

Game design is sedentary work. Generally its practitioners do their work with their butts planted securely in front of a computer in an office (be it home or away) as their muscles and verbal skills atrophy. Even game journalists are prone to this condition. Not so with Colin and Sarah Northway (pictured below), the husband and wife team behind NORTHWAY Games. Not only do they make really cool indie games, but they do it with just a laptop while traveling the world meeting indie developers of...

The Netherlands are a hotbed of indie game development, which seems appropriate for such a brilliant and eccentric little nation. Two man Dutch indie developer Vlambeer have found themselves in the news more often than most companies of their size, thanks to two great games and a third on the way.

+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

In this Null Byte, we are going to be installing Packet Injection capable drivers in Linux. These are the open-source drivers required to sniff wireless traffic, inject packets to crack a wireless access point, and go into "monitor-mode". These drivers are superior because they are the fastest available drivers.

For more than a decade, Interplay was arguably the best video game publisher in America. Their list of games is a who's-who of the most creative and forward thinking games of the '90s, including everything fromOut of This World to Alone in the Dark to Earthworm Jim to Descent. They've been around since 1983, but have fallen on hard times since 1997, when they became a public company. They were acquired by a French publisher who then went bankrupt. They were forced to close their internal deve...

You'll see a lot of Linux action going down here at Null Byte. We use Linux for hacking-related stuff because it provides a more relaxed programming environment, making it easy to write exploits and tools. Linux has many features Windows is lacking, such as full control over the OS right down to the Kernel and massive availability of mature, open source (read: free & tweakable) tools & projects.

For this week's review round-up, we bring you two games from opposite sides of the indie world. One is a free online hybrid shooter/platformer combining elements of Team Fortress 2 and Minecraft. The other involves driving jeeps around and shooting things as fast as possible. Both are great.

Four years ago Mind Candy was a pretty small game company. They were best known for their revolutionary but short lived ARG Perplex City, and had no other successful franchises to fall back on when that ended. Their plan to save it? Start a free online social game for children ages 7-12 called Moshi Monsters, where kids can create monster pets, raise them, and socialize with one another in a controlled, safe environment.

Since PDF files are so popular in both our daily life and work, we see them everywhere. And sometimes we find there are terrfic images or text in the PDF files and we want to save them as seperate files for future use, such as in a presentation or post. Here's the question: how can we save those elements from the non-editable file formats?

Every year at the big video game trade shows around the world, like E3 and gamescon, the big three console makers each do a hot-ticket exclusive press conference to let the media know what's coming for their system. Computer games have no such press conference. Who would give it if they did?