For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.
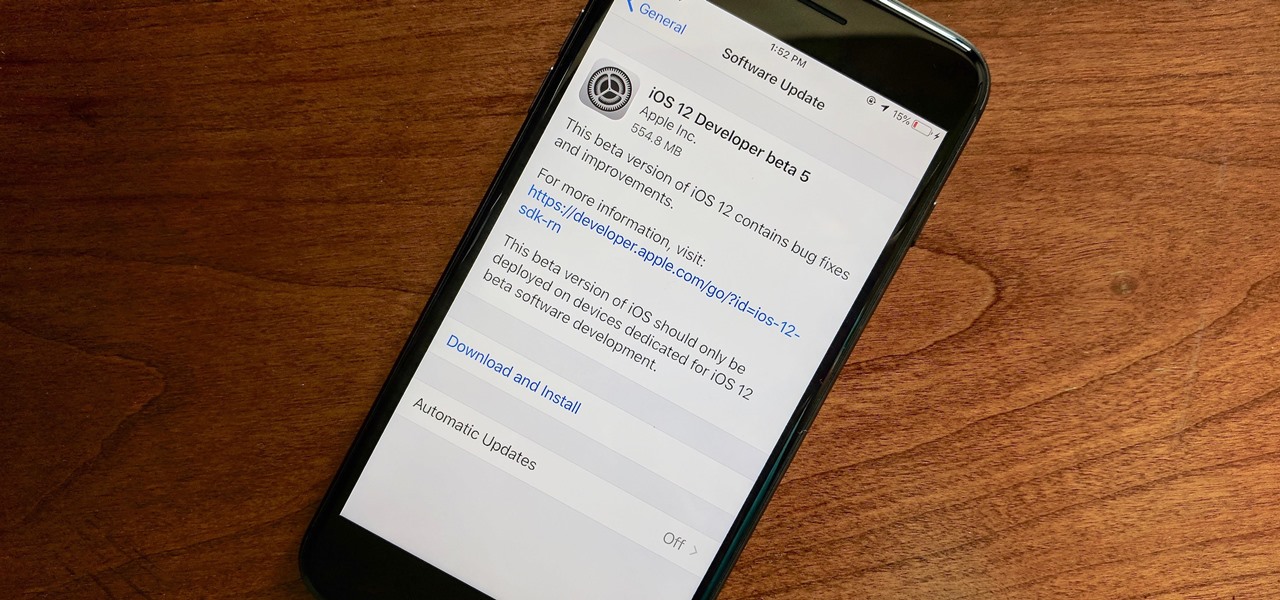
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see this one drop one day early.
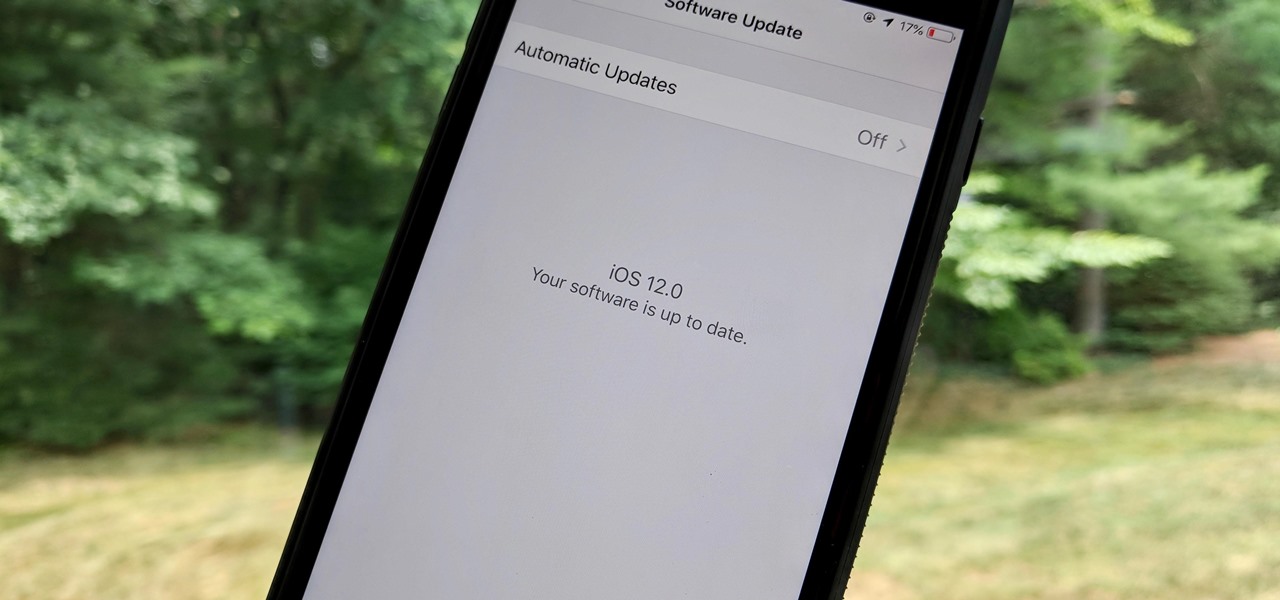
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

In July 2017, LG announced a new smartphone lineup, the Q series. These devices focus on providing some flagship features at a more affordable cost — features such as an 18:9 1080p display. LG's goal here seems to be adding value for the more budget-conscious users, and in 2018, they've continued the series with the Q7.

Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, there are a few things you can do about it.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

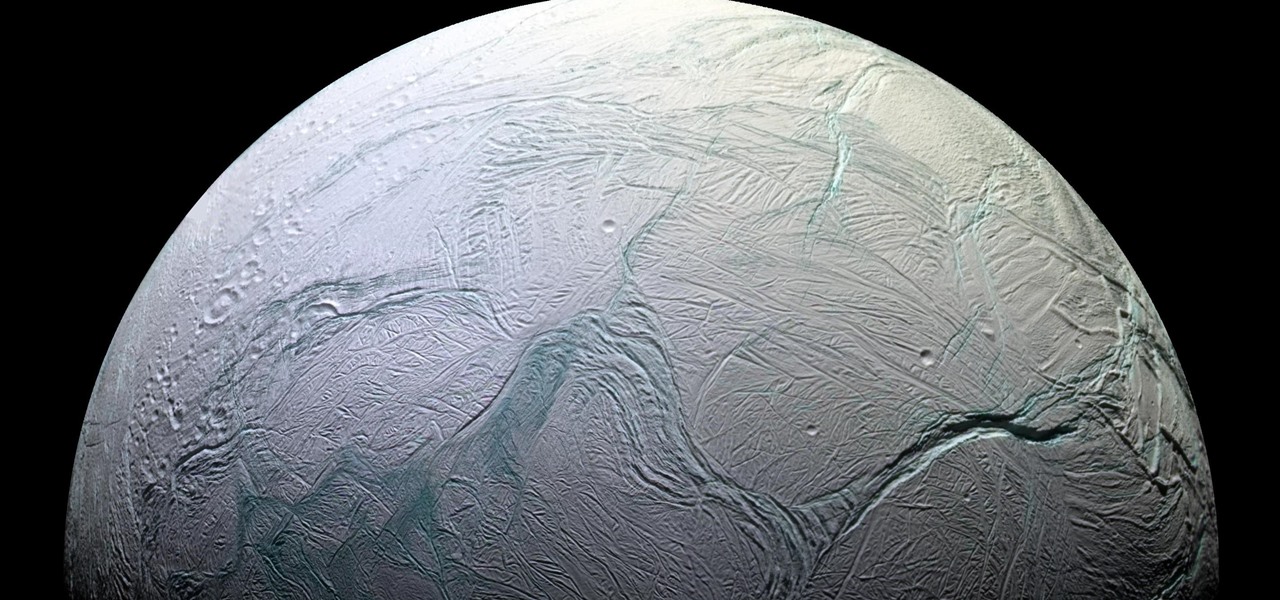
Earlier this year, NASA reported on findings that might point to water, and microbial life, on moons orbiting Jupiter and Saturn. Named Europa and Enceladus, those moons contain large oceans under their icy surfaces, which many speculate could hold microbial life.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

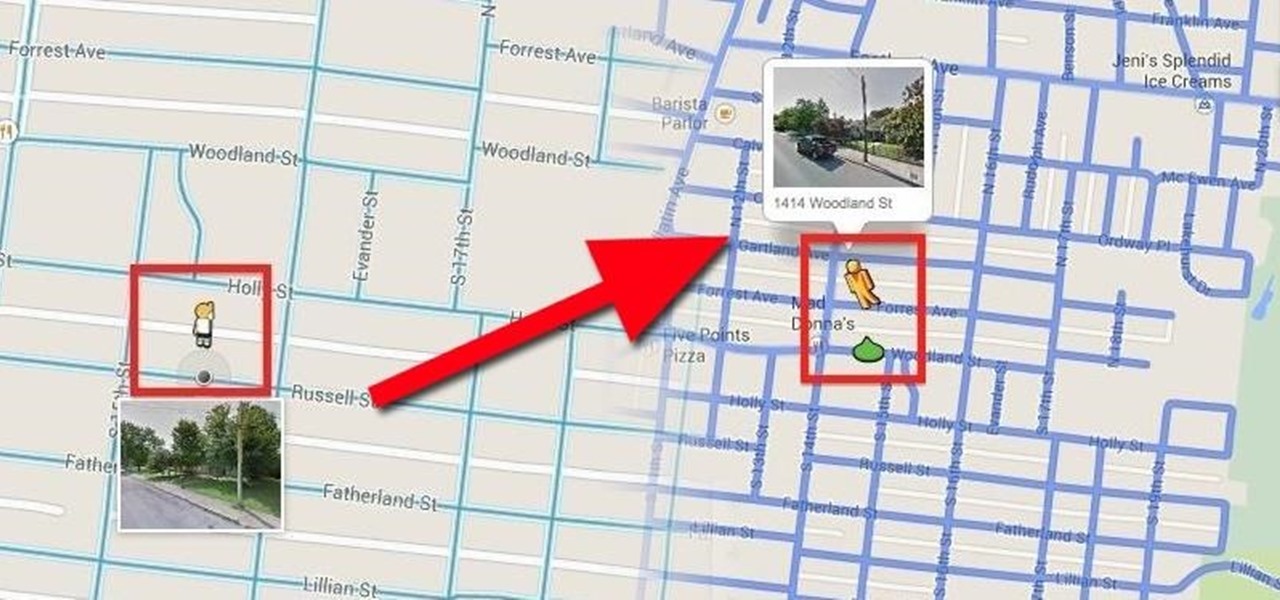
When the Google Maps web app got a massive redesign earlier this year, I was pretty excited to try it out, but it was a fairly disappointing update for me. The slower load times, confusing street view, and bicyclist neglect are just a few of the reasons I don't enjoy it over the old classic Google Maps. The brand new drag-and-drop measuring tool released this week is actually pretty useful, but not enough to change my mind.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

This is the first 3D game from the Castlevania series, and it's solely for the Nintendo 64! This 18-part walkthrough series will cover everything involved in beaten Castlevania 64 using the Carrie Fernandez character. She's a young orphan gifted with dangerous magic powers on a vampire hunting mission to stop Count Dracula's impeding return to power. Watch and learn! Then try out defeating the game using Reinhardt Schneider.

In the Xbox 360 game Darksiders, you'll eventually have to play the Iron Canopy level, which consists of The Seesaw, Webbed Floor, Two Lifts 1 Bomb, Loom Wardens, Broodmother, Silitha and Return Silitha's Heart. War will be ambushed and captured as he enters the Iron Canopy. When he comes to, you'll find him hanging from a spider web. Tap the Action button to break free. Make your way around to the left to discover a Soul Chest in hidden nook behind your starting location. Now cross the webbe...

Who could forget the spectacular conclusion to the "Back to the Future" trilogy? The scene where Marty and Doc Brown use a train to push the DeLorean to 88 miles an hour so Marty can return to the 1980s has become iconic. With this tutorial, you can recreate the scene in miniature using fairly inexpensive props.

You don't need flying broomsticks or magic balls to play this version of the game – it's tailor-made for muggles like us.

With a little time, you can turn a pair of rabbits into lifetime bunny buddies. Step 1

Learn how to do full situps with dumbbells and alternate cross punches. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do a low single cable squat power cross punch. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do knee tuck floor crunches. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do single-dumbbell front lunge and power row at bottom. Presented by Real Jock Gay Fitness Health & Life.

Learn how to play a classic vocal warm-up rising through the keys playing a major scale up to note 5 and returning to the root before rising by a semitone

This video shows you how to create a LEGO Star Wars imperial scout trooper from Episode 6...The Return of the Jedi.

In this video, Curtis Smith from Southwest Yard & Garden is joined by Bernadillo County Home Economist Patricia Aaron to talk to us about cooking with pumpkins. There's probably no vegetable that anounces the arrival of fall like a pumpkin. When you're using a pumpkin to make piesm cakes, and so forth, you want to choose a medium-sized one. Smaller pumpkins can make good side dishes. Bear in mind, it takes a bought a half pound of cooked pumpkin to make one serving. Here, we're using a nice m...

Here's how to make this Middle Eastern delicacy. You Will Need:

iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

In this video tutorial, Mad Cow Moo shows you how to do blurs on footage in Sony Vegas. Looking on the time line for a break in the audio, place the cursor at this point and hit s on the keyboard to split the video into segments Go to the time line to the final frame you want and point the cursor here, creating a highlight, and hit the s key again. Right click on the audio, select group from the drop down and choose, "Remove From". Right click the video track on the left top corresponding to ...

To make Italian meringue butter cream cake icing you need some basic ingredients. The things that you need are 2 Cup Light Corn, Syrup, 2 Cup Egg Whites, 2 Teaspoon Cream of Tartar, 1/2 Cup Granulated Sugar, 2lbs Butter, 1 Tablespoon of extract. Start out by placing the corn syrup into a heavy bottom pot onto medium heat. Onto the egg whites. Start beating the egg whites (medium speed)till a bit frothy and then add the cream of tartar. Increase speed to high and while beating add the sugar. B...

Kare-kare is a Filipino oxtail stew with bok choy and peanut butter. This stew is full of flavorful ingredients that create depth and interest to the marrow rich oxtail. This hearty dish will fill you up while delighting your taste buds with rich flavors. Watch this video to learn how to make a traditional Filipino oxtail stew called kare kare. This will comfort you on cold days. Ingredients: 3 tbsp oil, 2.5 kg/5 lb oxtail or 2 kg/4 lb shin of beef, 3 tsp salt, 2 tbsp annatto seeds, 2 large o...