Geohot's Towelroot exploit made rooting the Galaxy S5 so easy that it was almost unreasonable not to try it out—even for the first-timers out there. This, of course, meant that folks who didn't truly need root for their usage went ahead and got Superuser privileges anyway.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.
There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor.

Welcome back, my greenhorn hackers!

Microwave popcorn promises so much—a tasty, relatively healthy snack that's ready in minutes—yet it rarely delivers. Most of the time you'll end up with a scorched bagful or a bunch of stubborn un-popped kernels, but it doesn't have to be that way. With a few simple tricks, it's easy to get perfectly fluffy, tender-crisp popcorn every time.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

It's no surprise that Costco has great deals, and that's why millions pay annual fees for the privilege to shop in their wholesale outlets. Just take their hotdog and soda combo for $1.50—it's the same price now as it was 27 years ago.

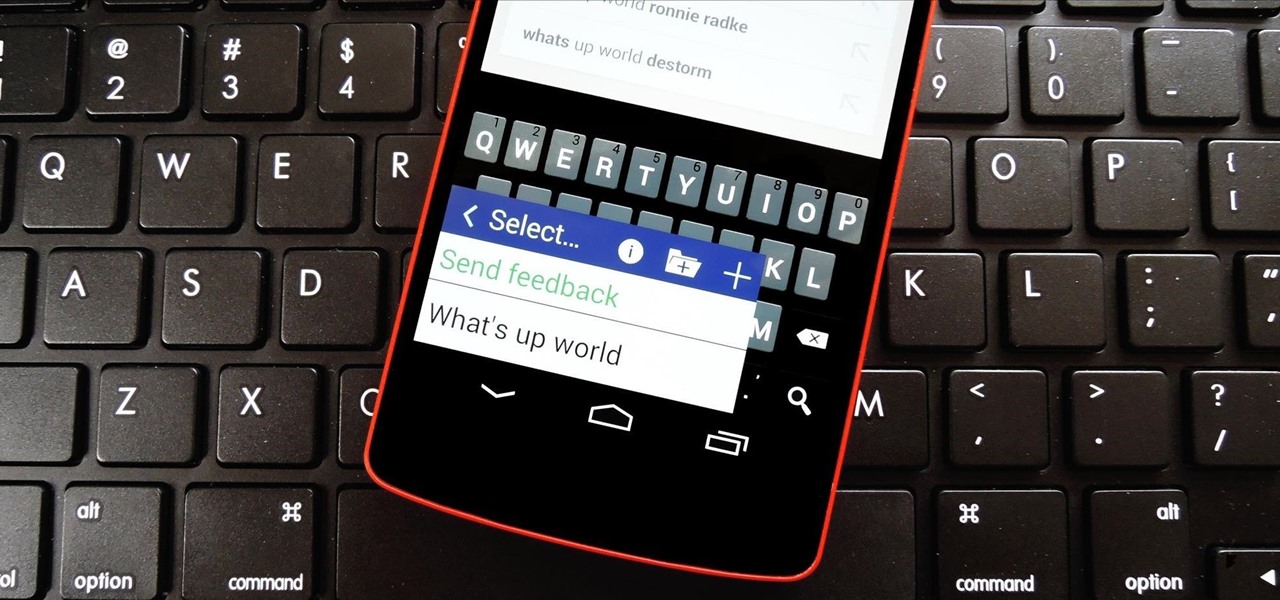
The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

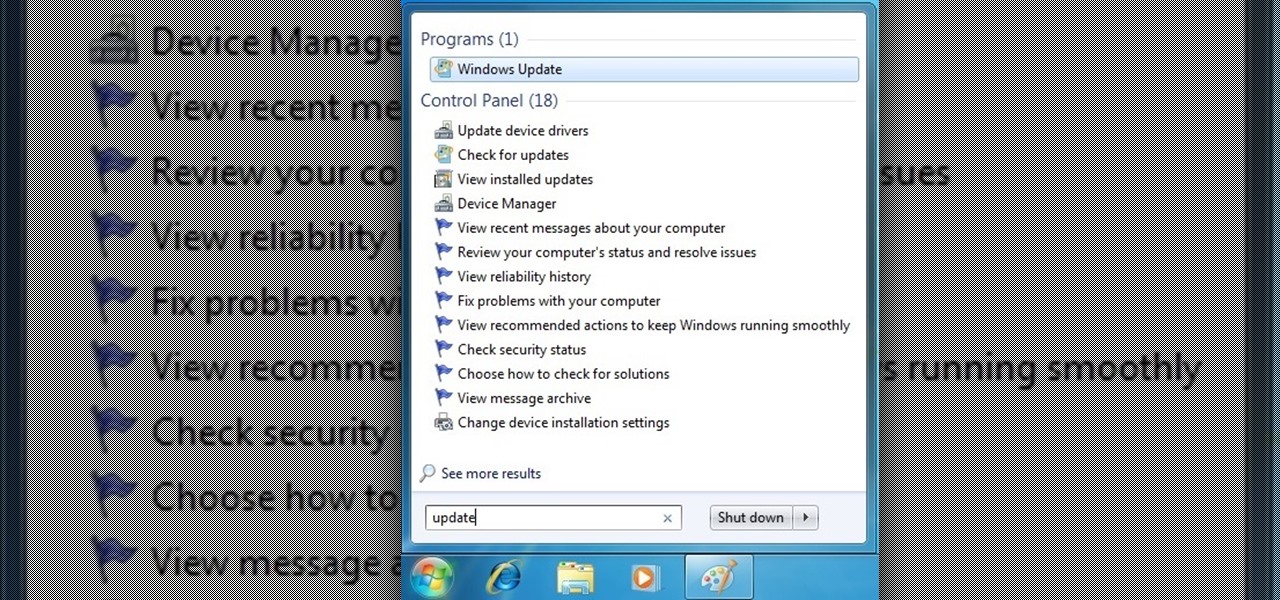
From a fresh home install of Windows 7 (not factory install) this will guide you step by step to updating your Windows 7 and getting it up and running.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

One of the things I hate most about Android's alarm clock is that you get the alarm icon in your status bar way ahead of time. Regardless of whether the alarm is in five minutes, five hours, or five days, that icon just sits in your status bar.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

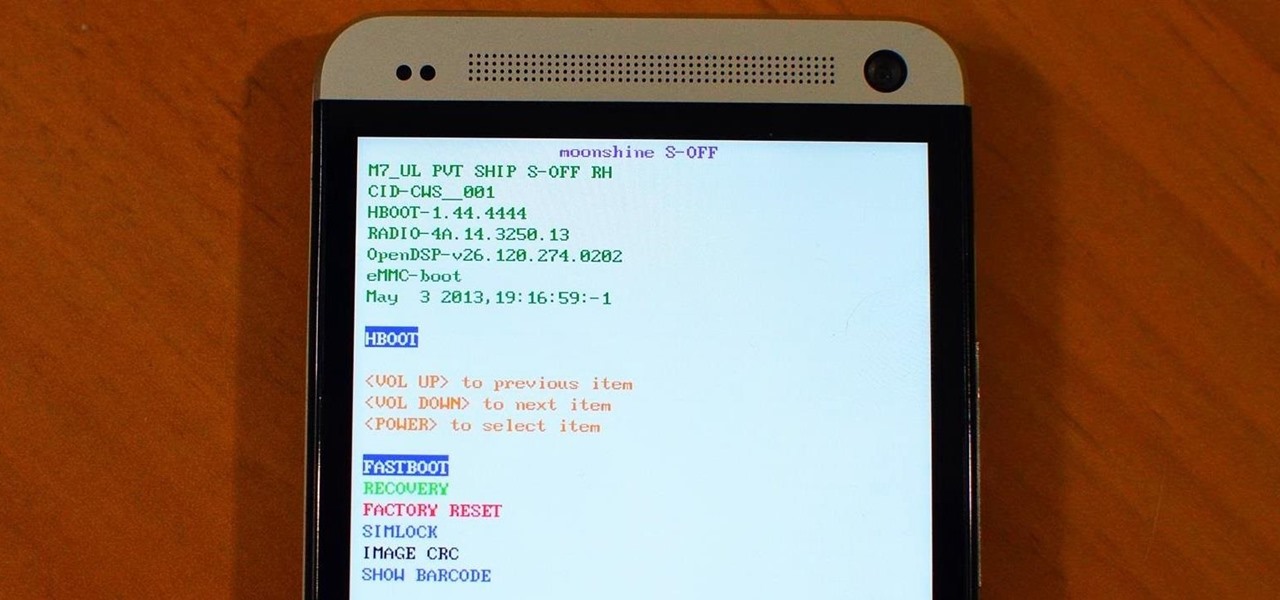
If you still have time left on your warranty, taking your HTC One in for repairs can be a serious pain if you've modified it in any way. To avoid the chance that they'll reject your phone because it's been tampered with, you'll have to return it to stock condition.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

We don't generally think of medicine as being very relevant to Steampunk, but it was a big part of Victorian science fiction. Notable examples that you may be familiar with would be Frankenstein and The Strange Case of Dr. Jekyll and Mr. Hyde.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most other smartphones, if the users turns the phone on silent or vibrate, the shutter sound is killed. If that doesn't do the trick, usually muting the shutter sound itself in the settings will do the trick. But for some of y...

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

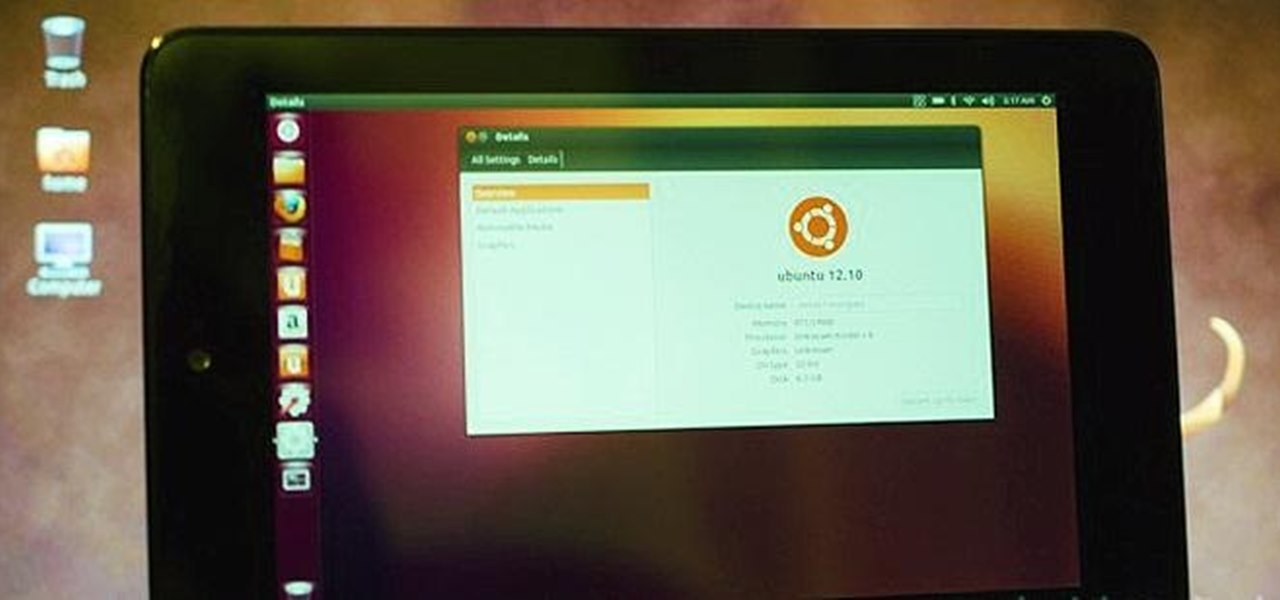
There's over 20 million people out there who use Ubuntu as their main operating system, and the number is steadily increasing due to its thriving community. While it's easy enough to download Ubuntu on your PC, the process to get it on your mobile devices can be fairly more difficult. Thankfully, it's not the hard to get Ubuntu onto your Nexus 7 tablet, but first you'll need to unlock it.

Tripwires are a new mechanic released in Minecraft 1.3, and people are still trying to figure out how best to use them. Minecart returns are a great idea, but what about traps?

There is something special about a secret knock. It gets you into secret super villain meetings and is a surefire way to test for rotating bookcase passages. Secret knocks usually work with an intimidating drug lord and for policeman listening at the door for the correct pattern of raps.

A math story problem in which you seem to come up a dollar short in the solution...but not really. Here's the trick with an explanation.

Prince of Persia: The Sands of Time has just come out in theaters, with Jake Gyllenhaal starring, but don't think for a second that the new Prince of Persia: The Forgotten Sands video game out now is because of the movie. The Prince of Persia video game series has been around since 1989, and The Forgotten Sands is just the newest addition. The movie is actually based on the game of the same title from 2003.

This fitness how to video demonstrates beginners level cobra poses. Standing poses along with cobra poses are great for opening the muscles in the lower body. Boost your energy level in the morning with a sun salutation that incorporates the cobra pose.

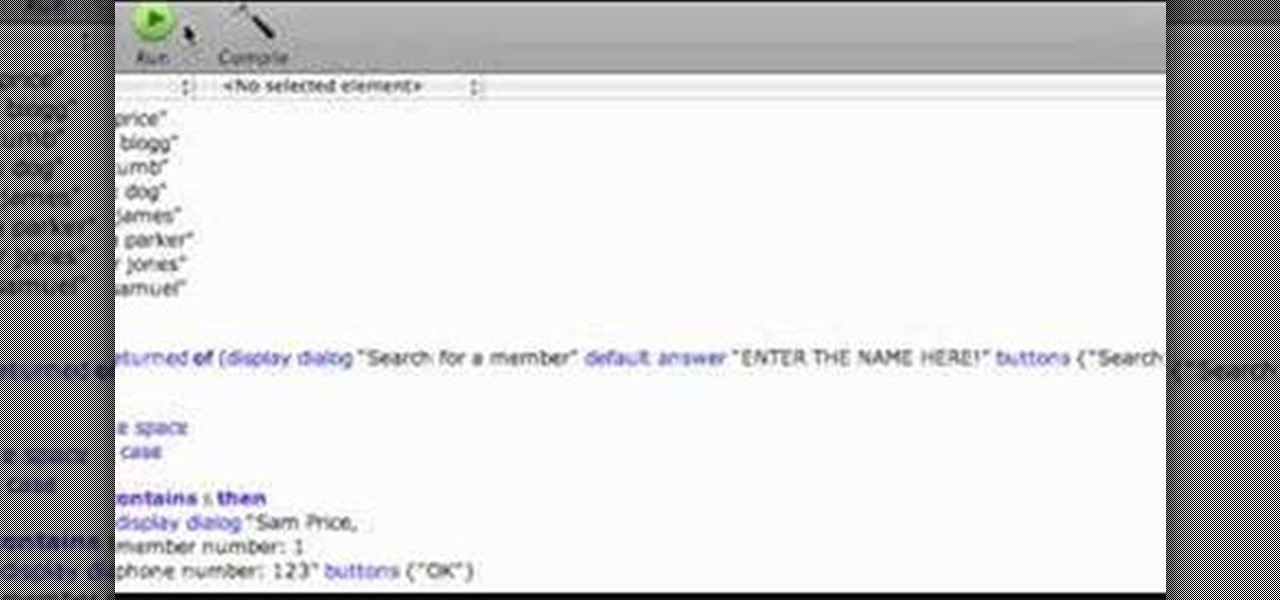
This video tutorial shows you how you can build a database in AppleScript! You don't know what AppleScript is? Well, it's a programming language for Mac computers only. You can build and design your own little applications if you are good enough.

Head shrinking is not only a thing of legends. Make your own cute, shrunken apple heads to add to the spirit of the season. Gather the family and get creative, carving whatever kind of face you would like on a legion of little apple heads.

JB skating combines roller-skating with a variety of dance styles. If you’re board of your normal Friday nights or looking for a fun and funky way to exercise, grab a pair of skates, watch a few videos and then try it for yourself.

You can learn to deal with the thing we all dread, a computer crash. Hopefully you diligently back up work but even if that's not case, stay calm. There is still hope and even if you're not a wiz at computers there are people out there who can help.

Crossword puzzles can help build your mind and improve self-control, language skills, and confidence. Watch this video to learn how to solve crossword puzzles.

The iPhone 15, iPhone 15 Plus, iPhone 15 Pro, and iPhone 15 Pro Max are Apple's most powerful iPhones to date with features like USB-C connectivity, improved camera capabilities, and faster CPUs. But no matter how impressive these phones are, they can still freeze, become unresponsive, or get stuck when powering on — and a force restart is how you get things working again.

Your iPhone has a powerful feature that can keep your secrets hidden from other people, and you'll never have to worry about sharing or showing someone something embarrassing or incriminating ever again.