If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

You know Moana's a rock-solid pick for Halloween this year. The question is, how far will you go to become Moana? Are you going to just slap on a cream skirt and a red bandeau? Or do you want to go all out and end up with the finished product like YouTuber Gladzy Kei did?

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

There's no denying that there are some seriously useful new features in iOS 11 for iPhone. But there's also no denying that Apple got a few things wrong with the latest iOS update, as well as left a few important features out.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

As unappealing as it sounds, transplants with fecal material from healthy donors help treat tough Clostridium difficile gastrointestinal infections. Researchers credit the treatment's success to its ability to restore a healthy bacterial balance to the bowels, and new research has shown that the transplanted bacteria doesn't just do its job and leave. The good fecal bacteria and its benefits can persist for years.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Apple introduced third-party keyboards back in iOS 8, and swipe-input options like Gboard, SwiftKey, and Swype made typing on an iPhone one-handed much easier. Even better, apps like Word Flow moved the keyboard to the side of the iPhone, so there was less thumb-stretching. Well, ever since iOS 11, Apple has had its own option for better one-handed typing in the stock keyboard.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

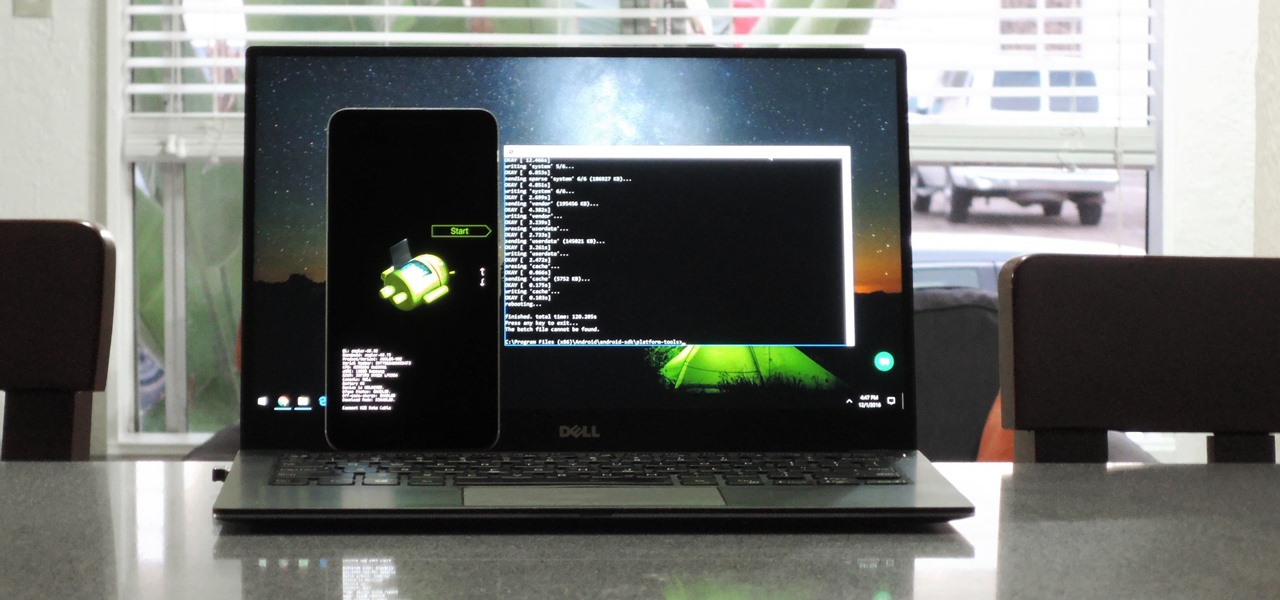
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Even the most seasoned cook is always looking for ways to make cooking easier and cleaning up after meal prep a breeze. There are a million and one tricks and tips out there to simplify your kitchen routines, but some of them are more valuable than others.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.