
News: 100 Movie Spoilers in 5 Minutes
Movies spoiled


Movies spoiled
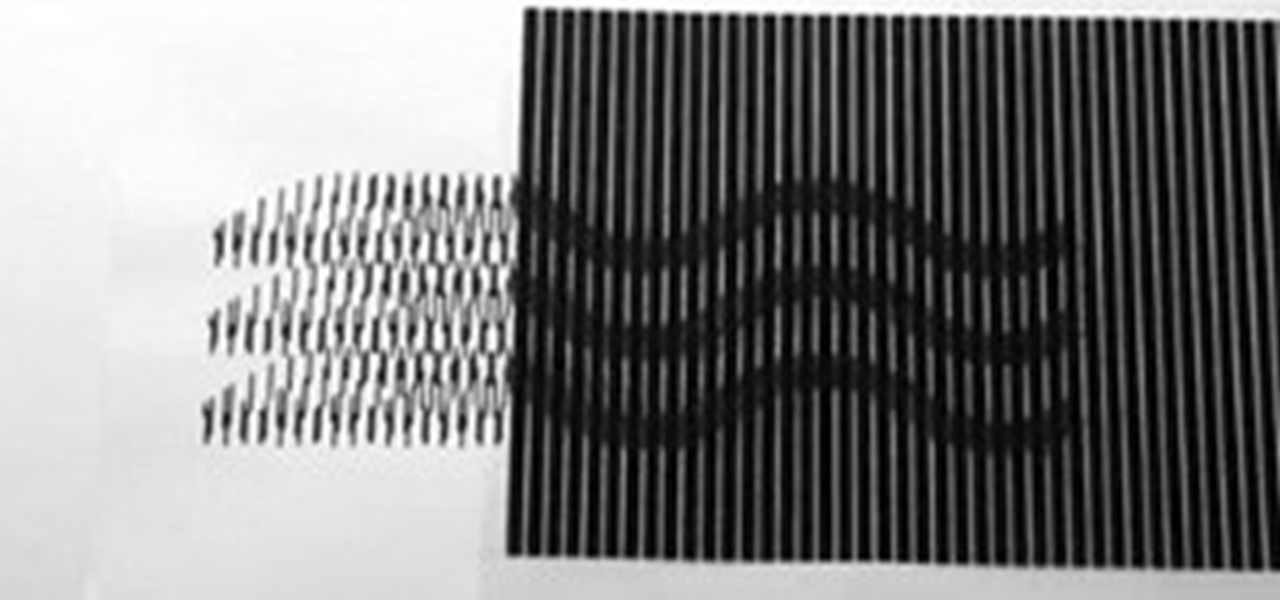
Pioneered by Rufus Butler Seder in his popular children's picture book Gallop!, and ably demonstrated by WonderHowTo favorite brusspup in the video below, "scanimation" refers to a novel (but distinctly old-timey) technique for cramming multi-frame animations onto a single sheet of paper by a process of superimposition and selective interference. Interested in creating your own scanimations? It's easier than you'd think. In the following clip, Paul Overton of Dude Craft presents a complete ov...

The Fog of Will Suki = a chink in the armor, a psychological weakness. Doubt.
There is a wonderful site that just launched with the youth sports community in mind. The site is http://YouthSportTravel.com , a collaboration of youth sports coaches and a major online travel brand. They offer arguably the best prices on hotel and motel rooms anywhere. For proof, I tested a number of locations with www.hotel.com, Expedia and Travelocity in comparison with YouthSportTravel and in each case; YouthSportTravel was equal to or cheaper than the competition. But this is not all th...

Learn how to always win in a game of Tic Tac Toe. Learn the strategies needed to win if you start first or your opponent starts first. Be the guru of Tic Tac Toe and never return to your losing ways again. This is also a good way to bet a little money and make a little extra on the side. Always win in tic tac toe.

Packaged macaroni and cheese dinners can be a quick, guilty pleasure, but making the real thing can be easy, too. This is the perfect recipe for a rainy day (and great for kids on spring break!)

Have the old man and woman come back and start doing it in a chucky cheese or matress store,maybe tryin to get into a night club or falling asleep in a weird spot..STREAKING OR UNDER WEAR WALKING IN A SPORTS STADIUM OR ARENA!!

Fly an rc airplane with a line attached to the beads.

Make a maze out of invisible dog fence. Have a bunch of people wear many collars on their bodies and tell them they need to navigate their way to the end of the maze. They can see the end of the maze, but if they take the wrong path, they will get shocked. Also either have them wear the barking dog shock collars so that if they leave the boundary they will scream and keep getting shocked until they return to the maze path, or have another method to get them to return inside the boundaries. Bu...

Jackass guysI have been laughing my ass off watching you since episode 1. I have many prank ideas for you but the best one is to have vallet parking for bam and return his car to him in horrible condition, possibly a different car, only to find out he was set up. Im sure we can adjust this idea to perfection.I'm a college student in michigan and I turn 21 in 2 weeks on october 6, but can't afford to go to vegas as planned, and spending my 21st birthday with all you guys would be an experience...

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.

How To Sing Without Lifting Your Larynx

This article will show you to replace the brakes of your Porsche 944 S2 vehicle. First watch the video below. The video has a German soundtrack, but English subtitles are added to YouTube. If you don't see them by default, just press the "CC" button below the video in the controls.
Technology: The Less You Know the Better?

Ok, this prank is an idea I have for part of a comedy film I am writing a treatment for, and it is dedicated to pranks and pranksters!This idea is based on women always, ALWAYS, going nuts over their butts and how big they are! Women are always so self-conscious about their weight and their butts, and always putting guys on the spot asking how they look in clothes and if something makes their butts look big, so this is dedicated to all those women out there!We would need a guy, maybe a cast o...
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

It's currently 2011, but when you fire up your game console, put your hands on the controller and play the new Dead Space 2 video game, you're warped into the future— into the year 2511— just 3 years after the events that took place in the first Dead Space. And it's sure to be a beautiful, frightening, futuristic experience.

The 68th Annual Golden Globe Awards take place this Sunday, January 16th, 2011 between the hours of 5 and 8 PM PST — that's 8 & 11 PM for those of you on the East Coast (and Somewhere in the Middle for those of you Somewhere in the Middle).

Parental involvement is a crucial ingredient in the success of many children. Teachers know the saying all too well that it takes more than a village to raise a child, for one - it takes parental involvement. Thus, it is important for teachers to reach out to parents in that first week of school. Teachers should write a formal letter that is welcoming and easily comprehensible to the parent and the student. This letter should be able to communicate that the teacher values the child’s educatio...

There is no fan experience in professional sports quite like watching an NBA game live. Partly, this can be attributed to the combination of fluid teamwork and jaw-dropping athleticism the players exude in the form of size, speed, jumping ability, grace, and strength. What truly differentiates the NBA from the spectators' perspective, though, is the figurative nakedness of the players. While the NFL buries its athletes beneath pads and masks, the NBA presents its talent in shorts and a tank top.

Since its launch in 2001, Wikipedia has become the number one reference site on the web, used by anyone and everyone, written by anyone and everyone. With over 18 million collaboratively written articles, there's backgrounds and descriptions on practically everything—if it exists, there's probably a Wikipedia page for it.

According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the Wi-Fi version or the 3G model.

Zynga games has released their ZLotto feature that you can use to get exclusive prizes for FarmVille, Mafia Wars, YoVille, PetVille, and FrontierVille!

Ever typed out a long message on your phone only to find several errors after you hit send? Proofreading would fix this, but anyone who's spent time trying to edit on a smartphone knows how difficult it is. Thankfully, Gboard makes this task easier.

It's soon going to be time for the elections and everyone is prepping up for it. The Republicans are waiting to elect Romney, who in my and many others view will not keep his promises. The Democrats are trying their best (its working) to make Obama as strong as possible against Mitt, who, in their minds, will be easy to defeat. Obama's acceptance polls have been steadily rising in the past few months.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

Having bills to pay is one of the worst parts of life, especially around the holidays. And if you're extremely unlucky, you might also have to pay some hefty medical bills. This can put a heavy damper on plans, wants and needs. What's worse? The people that you owe money to are pushy and always bother you to pay in a more timely fashion, or worse, pay bigger premiums.

Earlier we've looked at starting off in Survival mode, plus simple combat. Now we look at a more refreshing aspect of Minecraft: Food!

THE ODYSSEY is an epic adventure, a world first, a race against time, an entire year of living dangerously.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

When it comes to social engineering, Null Byte is here to show you how it's done. Social engineering is the key fundamental to unlocking tons of possibilities and opportunities in your everyday life. So, what is social engineering? Social engineering can be called many things. It's taking nothing and turning it into something. It's taking the bad and making it good. Above everything else, it's the art of manipulating the world and people around you—coercing that salesman into giving you a low...

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.