
How To: Create an Adobe Flash slide show
Let's face it: Most people, even our friends and family, find it pretty boring to open emails with huge photo files attached to them. They're bulky and take forever to load.


Let's face it: Most people, even our friends and family, find it pretty boring to open emails with huge photo files attached to them. They're bulky and take forever to load.

Step 1 Launch the Adobe Flash program and select “Flash File (Actionscript 3.0)” under the “Create New” menu. Change the workspace layout to “Essentials” by clicking on the drop-down menu in the upper left of the top menu bar.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install UbuntuOne on Ubuntu Linux.
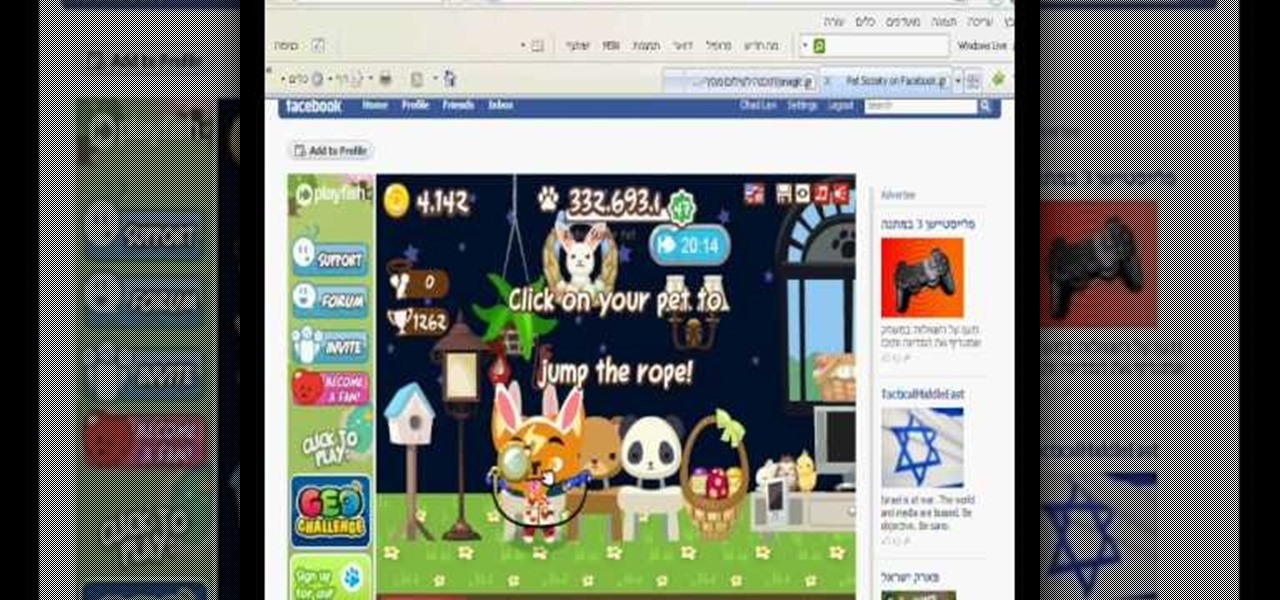
How to get pet society money cheat in a easy way. auto clicker: http://rapidshare.com/files/40560577/Autoclicker_V3.exe.html
Adding subtitles to a movie is super handy. That's because whether or not you speak English it can be hard to hear exactly what a movie star is saying. He could have a thick accent, or maybe the volume on your computer just sucks and everything comes out muffled. For times like these, subtitles help combat the confusion.
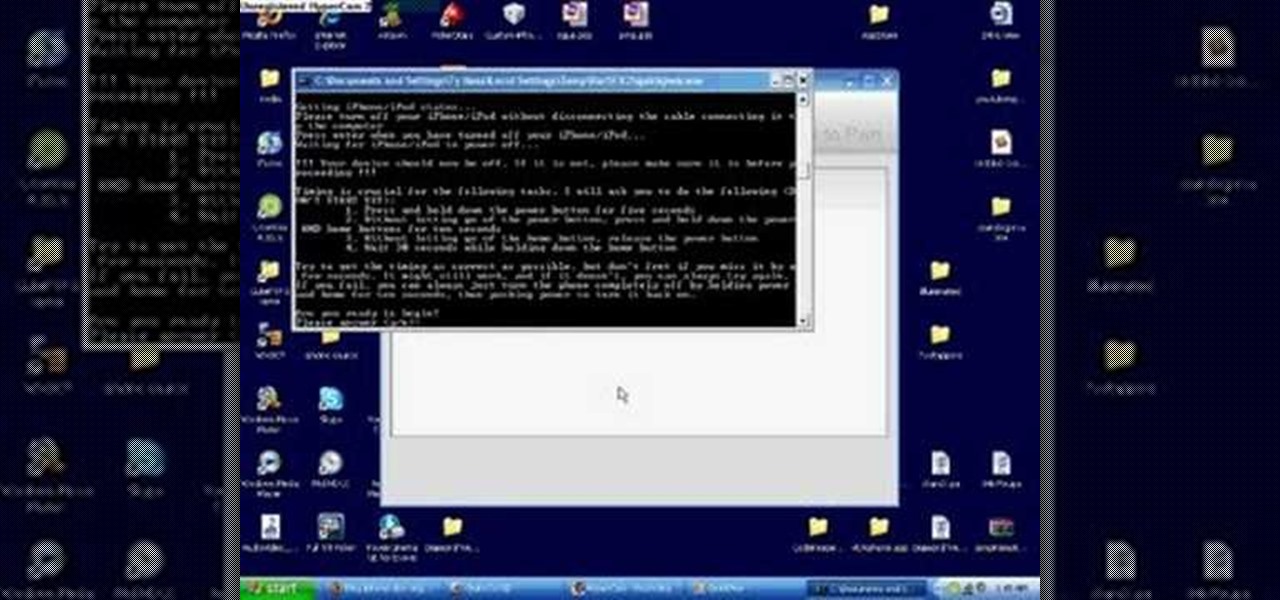
Get out your iPhone or iPod and get ready for some jailbreaking! Watch this video to see how to QuickPwn Jailbreak your Apple iPhone 3G and iPod Touch. This jailbreak will work with the 2.0, 2.0.1 and 2.0.2 Apple firmware.

In this video tutorial, Chris Pels will show how to extend the standard set of ASP.NET configuration settings with your own XML configuration elements. First, see how to create a configuration section handler which is required to interpret and process the information in custom XML configuration elements. During this learn how to use declarative model for defining the behavior of a configuration section handler. Next, see how to add a custom section handler and custom elements to an ASP.NET co...
This video is to get you started with the initial setup of the Doom 3 to Maya workflow. Topics covered (in order) are set up, export your first character ingame, texturing, animations on character cycles, load game models into Maya. Part 4 is a WMP video.

Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding community for Kindle a bunch of time to flourish, with tons of great code, hacks and homebrew. Today's Null Byte is going to show you how you can root, and then remove the crappy original screensavers that come installed on th...

To convert your MP3s to ringtones using iTunes follow the instructions below. First download and install iTunes and then agree to the terms of use and open the program. Then, click "File" and then "Add to Library." Locate the MP3 file you want to convert and open it in iTunes. Now click "iTunes" at the top of your toolbar and select "Preferences", then click the "Import Settings" icon bar and select "MP3 Encoder" in the "Import Using" bar Click "OK" twice to exit to your iTunes library. Now r...

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.
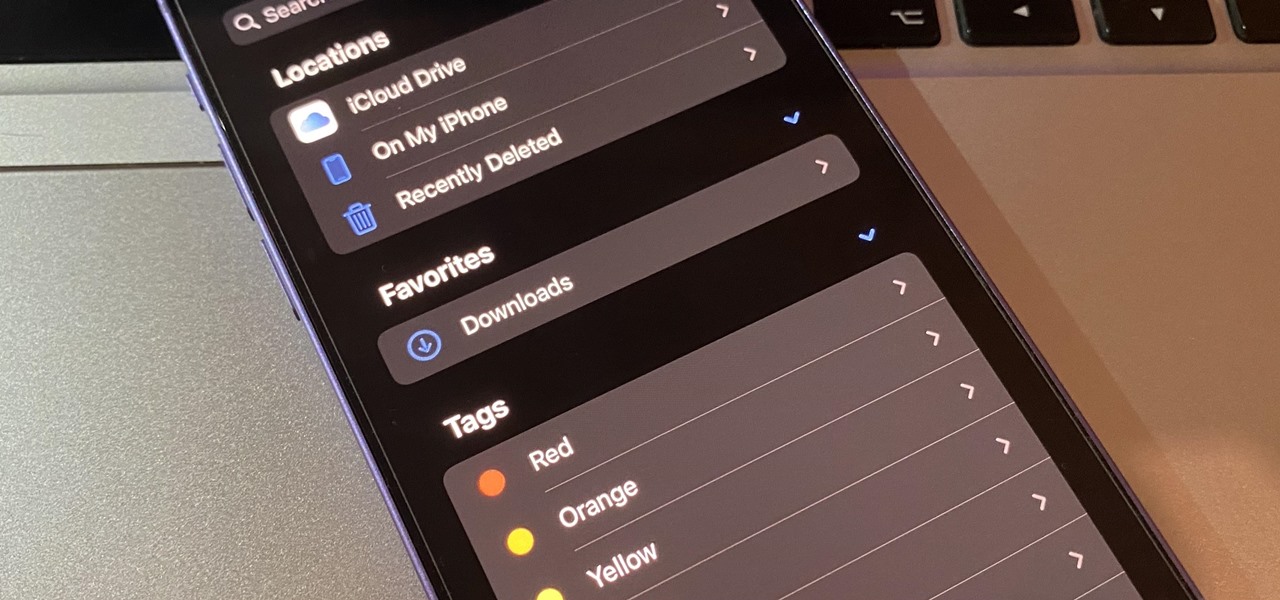
If you're not using your iPhone's Files app yet to manage images, documents, and other files on iCloud, third-party cloud services, or your local storage, it's time to start. Apple's built-in file manager is finally a powerhouse with many tricks up its sleeve in the latest software update.
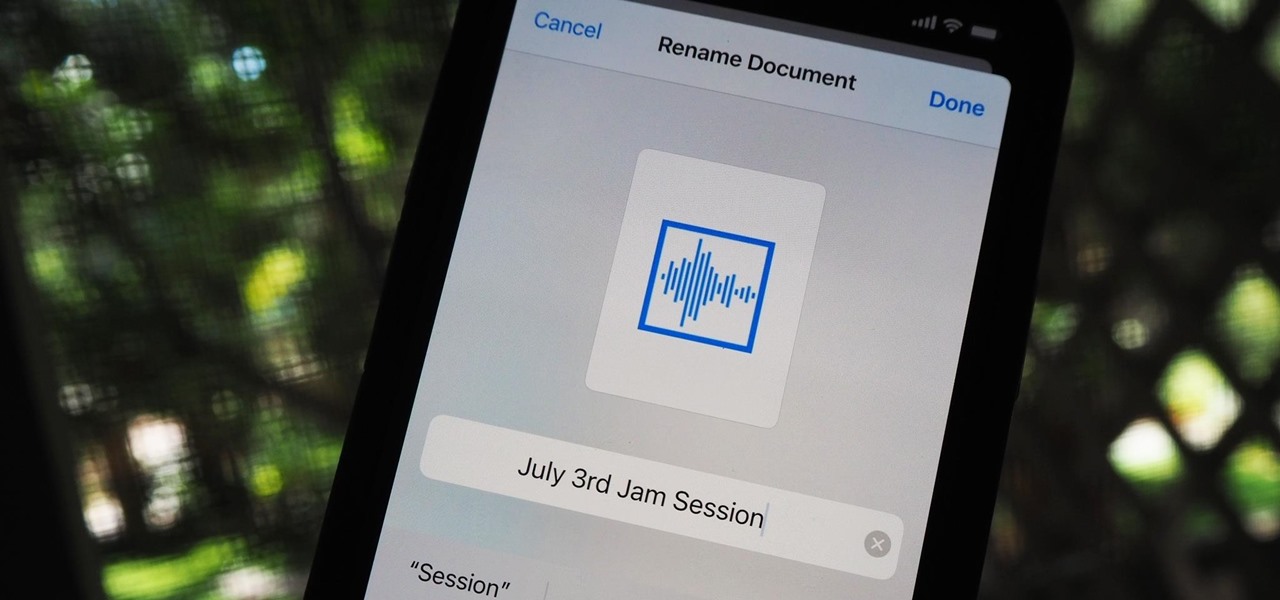
You can easily remove audio from videos in the Photos app on your iPhone, but the same cannot be said about removing video and just keeping the audio track. However, another stock Apple app can help extract the sound clip, and it barely takes any work to set it up.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Netflix has offered its beta program officially through the Play Store for some time now. Still, the issue most of us face — the beta availability is always scarce. Without getting lucky and landing a beta spot early on when the gates were open, there wasn't much you could do about it. However, there's now a brand new method you can use to sideload the Netflix beta app and join in on the fun.
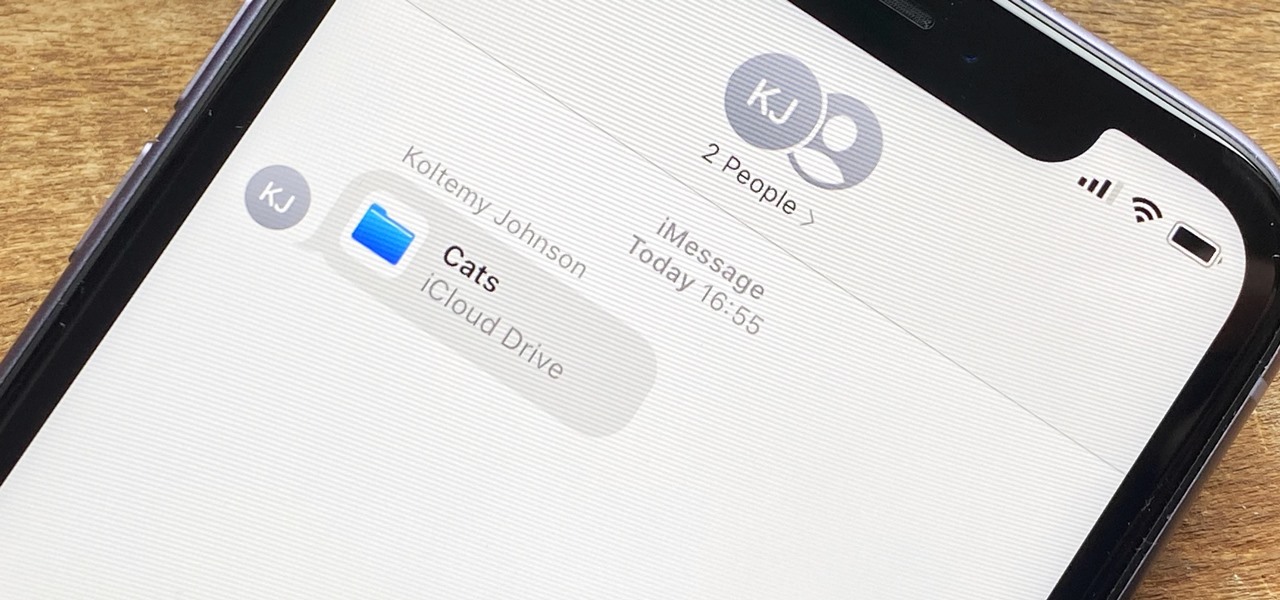
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.
Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.
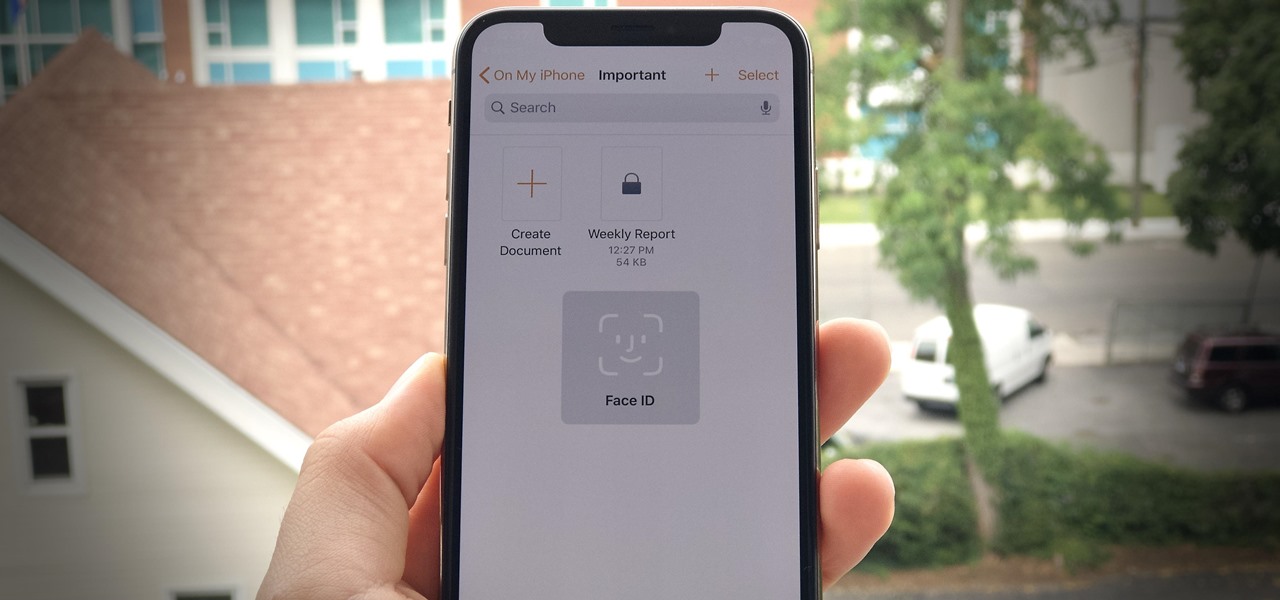
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.
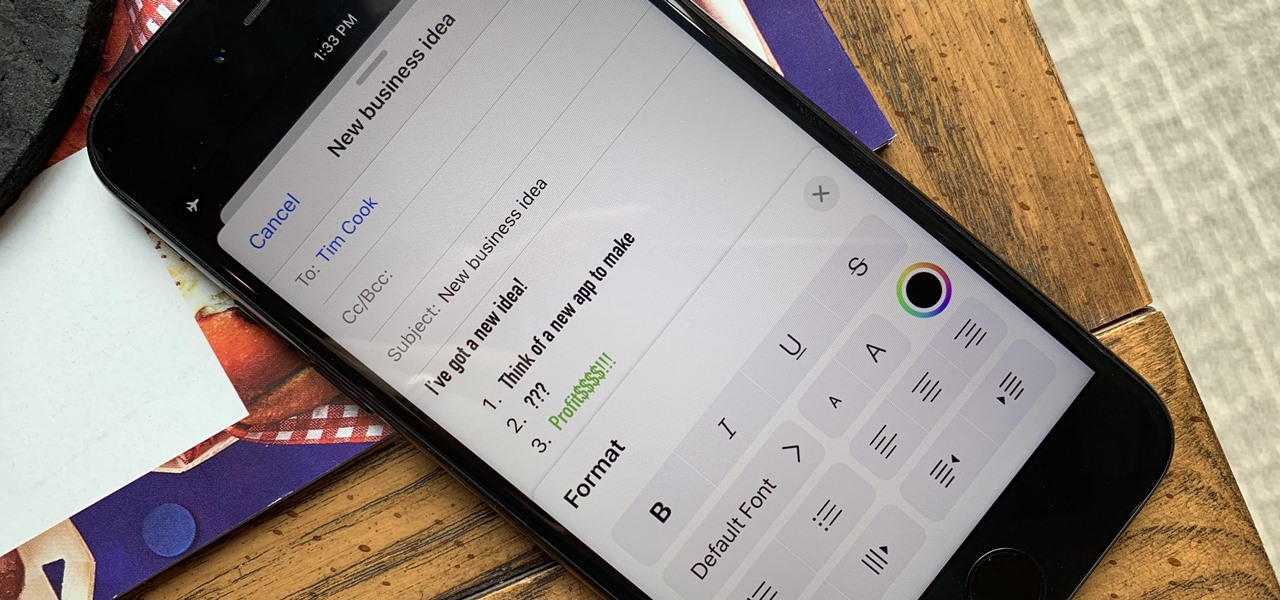
Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone to turn a physical document into a PDF and attach it to your message — all from within the Mail app directly.
When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a system level for some devices, but luckily, the developers are already on top of things.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.
Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.
So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.
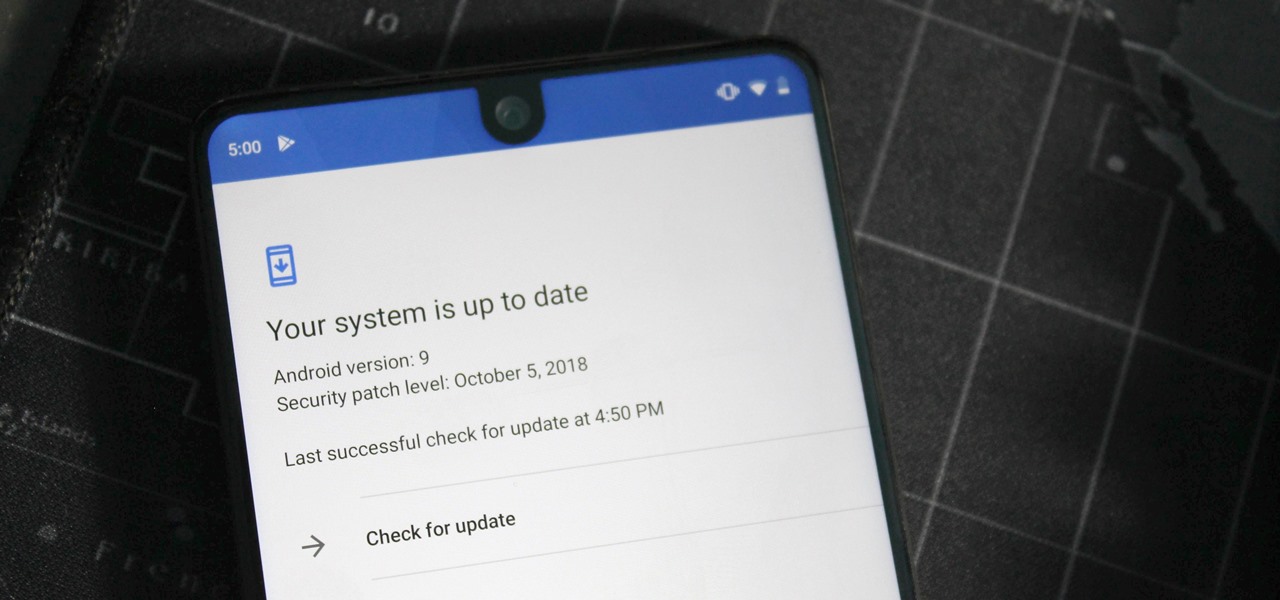
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

Patent holder Genedics, LLC has filed a legal complaint alleging that hand-tracking startup Leap Motion is infringing on its intellectual property.
While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.