Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

When it comes to give away or sell your iPhone, you can't just power it down, take out the SIM card, and hope everything will be okay. There's valuable data on your iPhone, and you need to get rid of it. Plus, if you don't perform all the necessary steps, chances are whoever ends up with the device won't even be able to use it. If you're selling it, that could ding your seller reputation.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

If you work for a company you are probably entitled to maternity leave. Gather as much info as possible and then have an honest conversation with your employers. With tact and civility should be able to have time to recover with your baby and keep your job too.

If you like 2D side-scrolling video games, then Shank's your man. Shank is full of "beat 'em up" action and combat, perfect for any gamer addicted to the old style of play. Shank is available on both the Xbox Live Arcade (Xbox 360) and PlayStation Network (PS3). But this Mahalo walkthrough for Shank is for the PlayStation 3.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

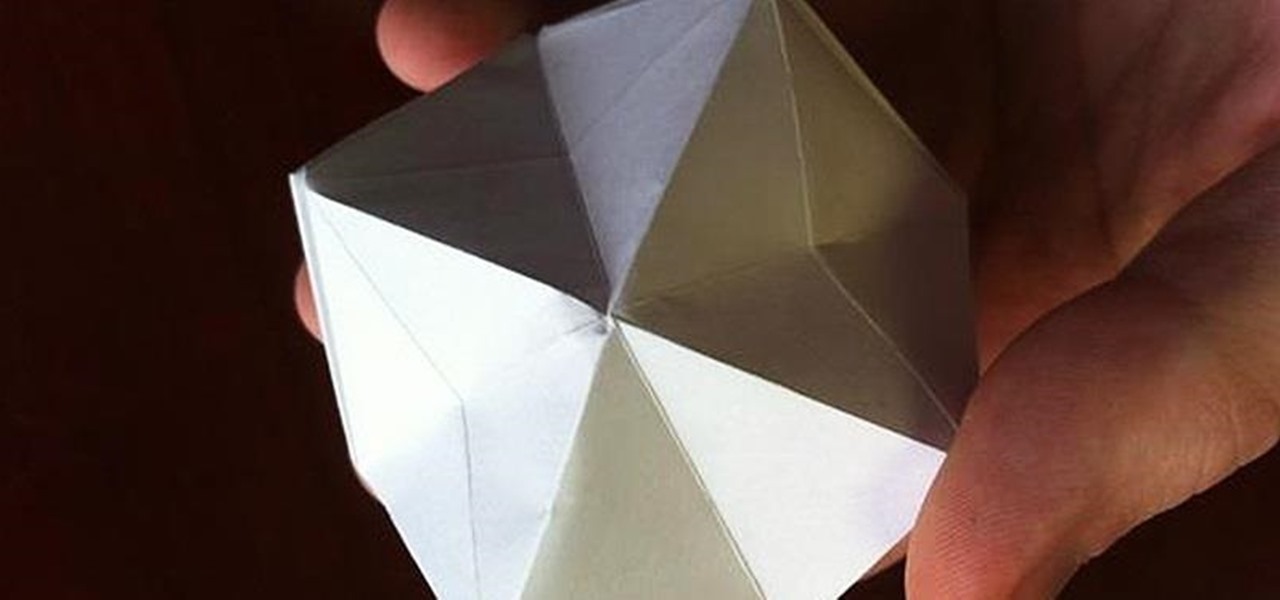
One of the most popular and basic origami geometric shapes is the "water bomb," which is a simple inflated cube. With a few extra folds and only a minor shift in approach, a more complex geometric shape can be achieved.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

IT is a competitive field, and finding success requires more than knowledge of a couple of coding languages or knowing how to google really well. To stand out among your peers and competitors, you should learn everything you can and get as much diverse experience as is available.

Even as we look forward to returning to work in person, the last year has changed how work can be done. That means there will always be a demand for good programmers and coders who can support the digital infrastructure of the online working world. The Backend Developer Bootcamp Bundle can give you the expertise you need to become a highly qualified programmer for only $29.99.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

Niantic recently added a new Field Research task type called AR Mapping that challenges players to capture video footage of PokéStop landmarks and upload them. In return, players receive rewards in the form of in-game items.

Apple always finds a way to sneak in tiny, inconspicuous features that improve the iPhone experience. And with iOS 14, there's a hidden, unannounced gesture that makes it possible to navigate apps and menus faster than ever before.

With each update, Chromebooks are slowly becoming the Android tablet we always wanted. They already run your favorite Android apps and recently added a multitasking feature introduced to Android smartphones a few years ago: picture-in-picture mode.

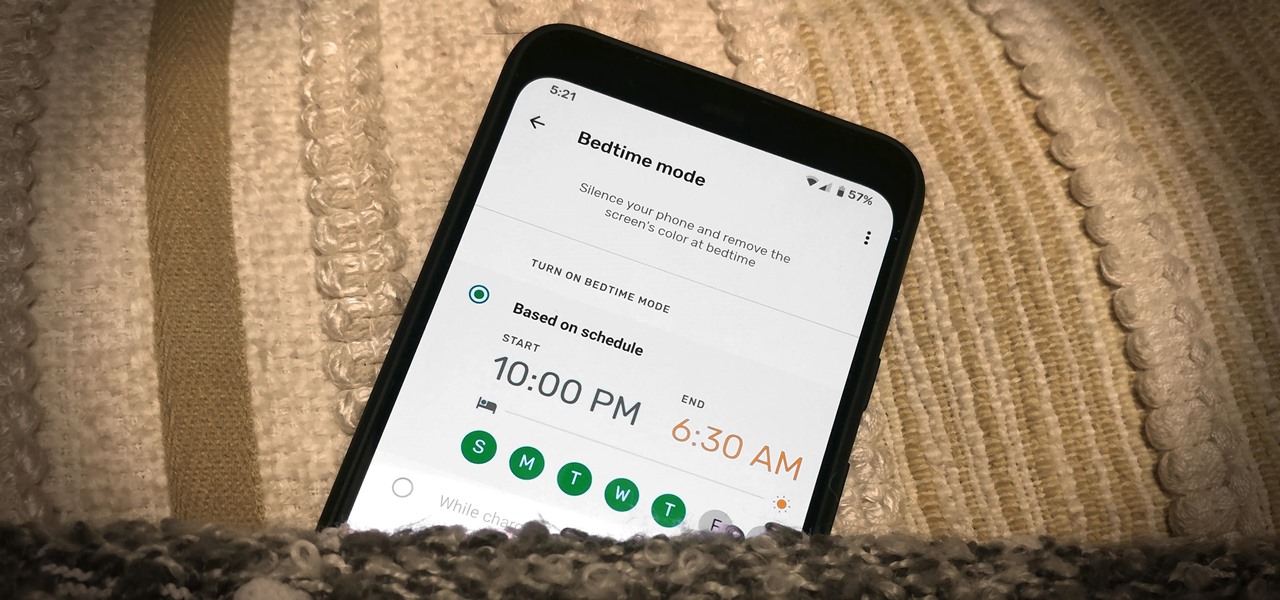
Apple added a Bedtime Mode to its Screen Time tool for curbing smartphone distractions. Google's version of Screen Time, called Digital Wellbeing, actually predates Apple's, but a recent update is finally bringing in Bedtime Mode.

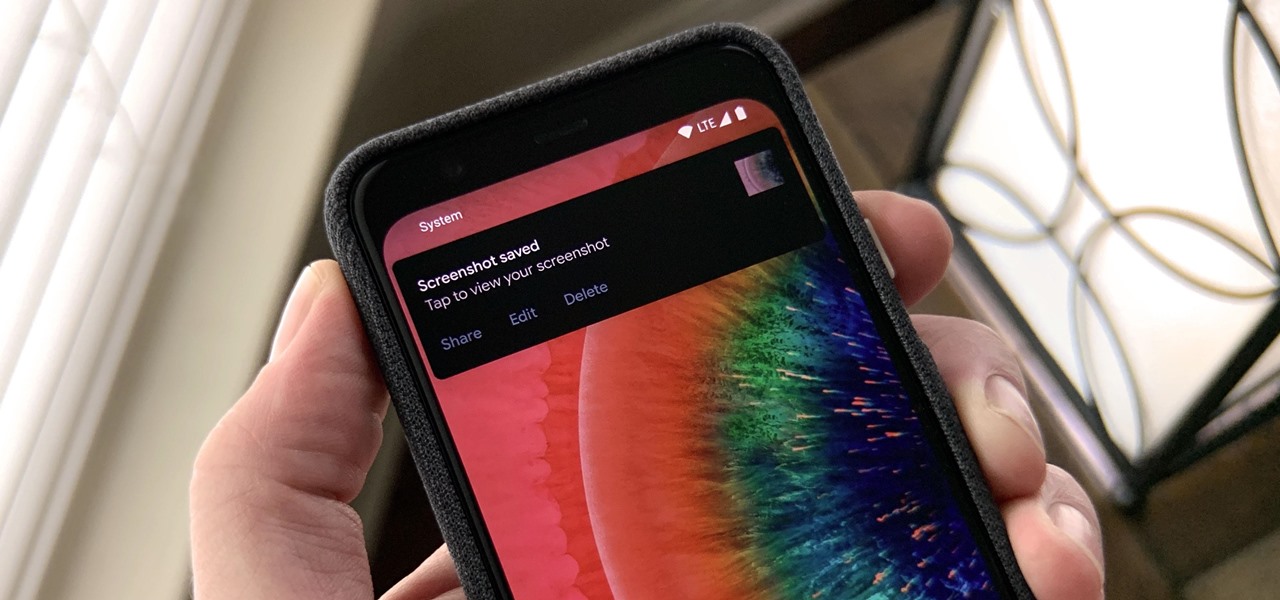
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

It wasn't too long ago that the power menu for stock Android didn't offer much beyond turning the device off, but Google has steadily added more functions, like capturing screenshots and provisioning access to emergency information.

LineageOS is great and all, but custom ROMs were at their peak when CyanogenMod reigned supreme. It had all sorts of innovative features that have since been copied by Google and Samsung and the like. But one thing that still hasn't been adopted into stock Android or One UI is CM13's easy way to adjust screen brightness.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.

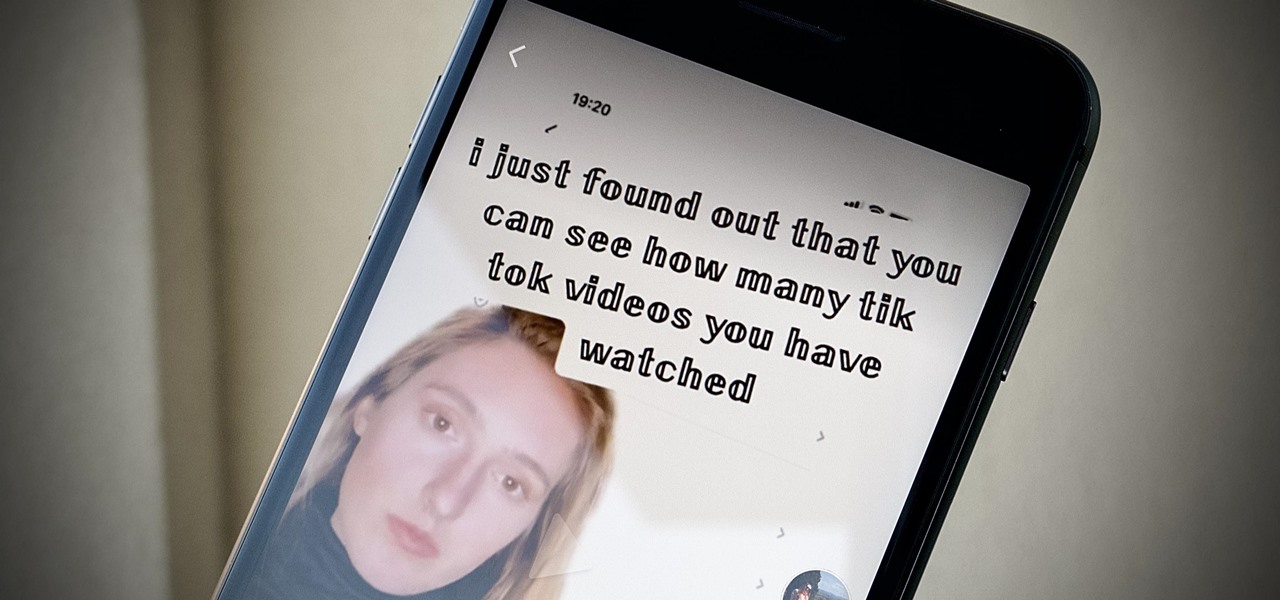
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

After closing its office last year, enterprise AR company Daqri has moved on to the final stage of its lifecycle with the liquidation of its assets.

What could Apple be planning here? Are we going to see some revolutionary new features for the iPhone? Will we see mostly bug fixes and security patches? It's time to find out, as Apple just released the first developer beta for iOS 13.4.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

OnePlus has always pushed the boundaries with specs. They give their phones the premium treatment, which, yes, includes the camera nowadays as well. But even though they have become pretty solid in the photography department, it could always be better.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

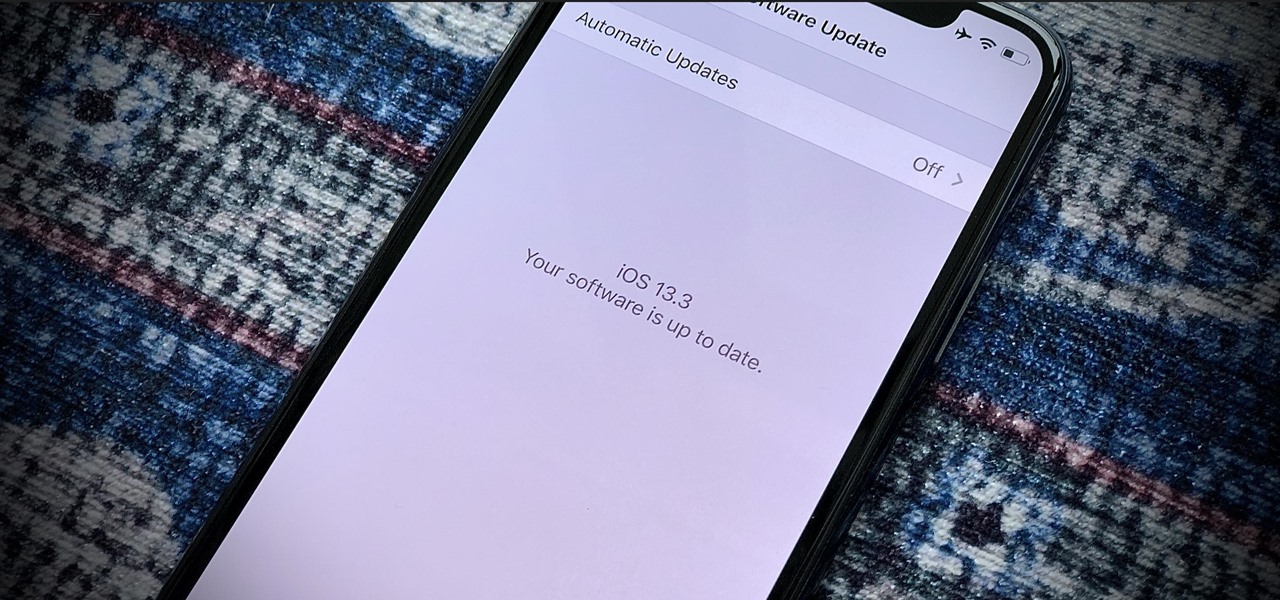
Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.

One of our favorite email apps, Edison Mail, just got even better. In versions 1.17.0 (iOS) and 1.12.0 (Android), the app introduced a new Assistant, a powerful tool that makes organizing travel, packages, entertainment, bills, calendar, and more a breeze over email. The best part? You can customize it to your liking, so the Assistant works precisely as you need it to.

Since the release of iOS 13.3 beta 3 on Nov. 20, Apple has remained silent on new beta updates. That's likely because there was a holiday the following week, and then all of the major shopping events after that. But now, it's back in the game, and on Thursday, Dec. 5, Apple pushed out iOS 13.3 developer beta 4 and public beta 4.

Who's ready for another beta season? We beta testers have had quite the break: Apple released the fourth public beta for 13.2 on Oct. 23, and since then, two full weeks have gone by without a shred of beta news. It seems this Wednesday, Nov. 6 is our lucky day, as Apple just released the first public beta for iOS 13.3.

The latest official update for iPhone, iOS 13.2, introduced 22 new features and changes to the iOS 13 era, building off the improvements brought by iOS 13.1 and iOS 13 proper before it. It's time to take our first peek into what's next for iPhone and iOS, as Apple releases iOS 13.3 developer beta 1 today, Tuesday, Nov. 5.