After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.
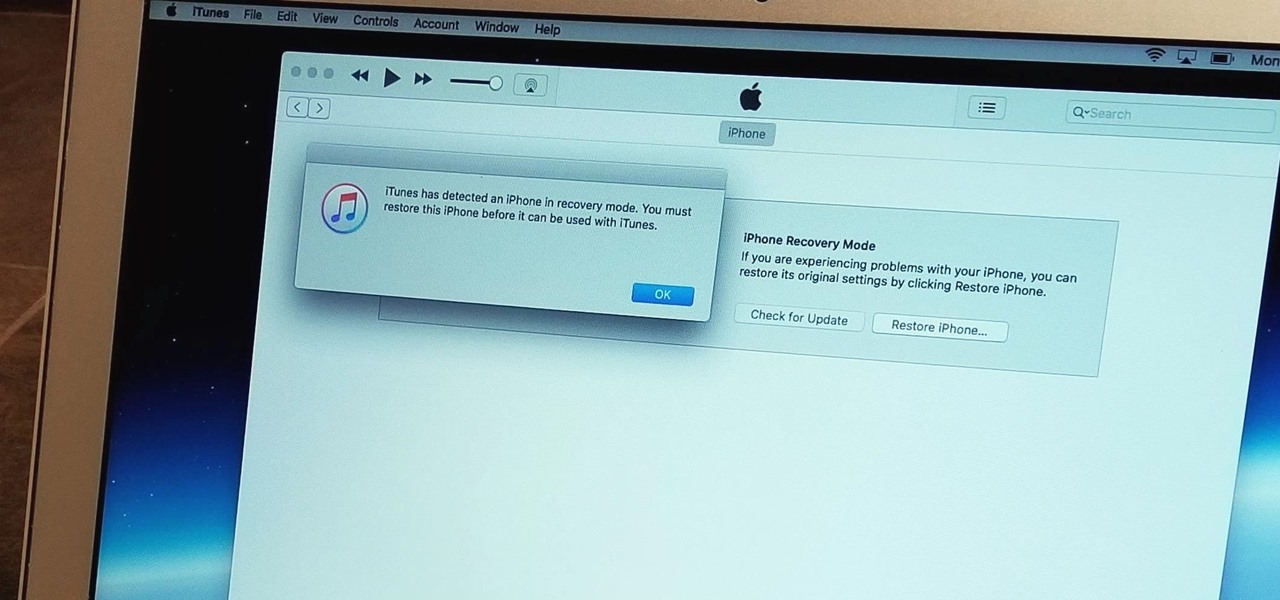
With the iPhone 8, 8 Plus, and the exclusive iPhone X, Apple has come full circle in transitioning its users away from the home button present since the first iPhone a decade ago. This gives us a window into Apple's design philosophy moving forward, but it also presents some new problems, especially when it comes to entering and exiting DFU mode in iTunes.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

For about a million Americans each year, a joint replacement brings relief from pain and restored mobility. But, 5–10% of those people have to endure another surgery within seven years, and most of those are due to an infection in their new joint. If doctors could treat infections more effectively, patients could avoid a second surgery, more pain, and another rehabilitation.

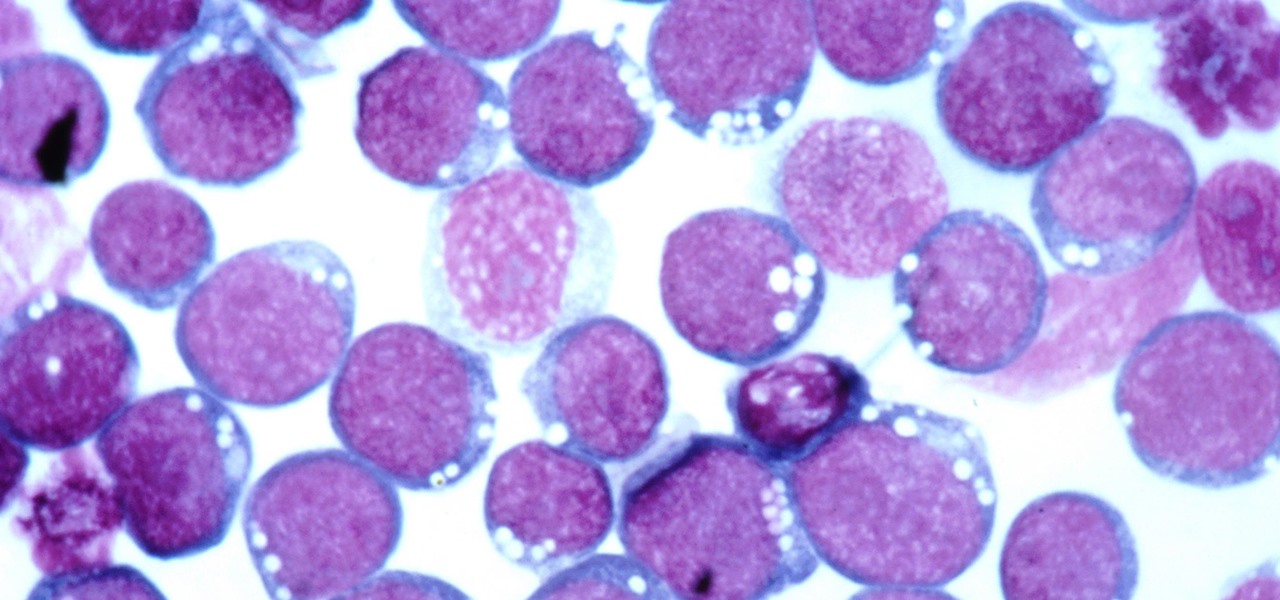
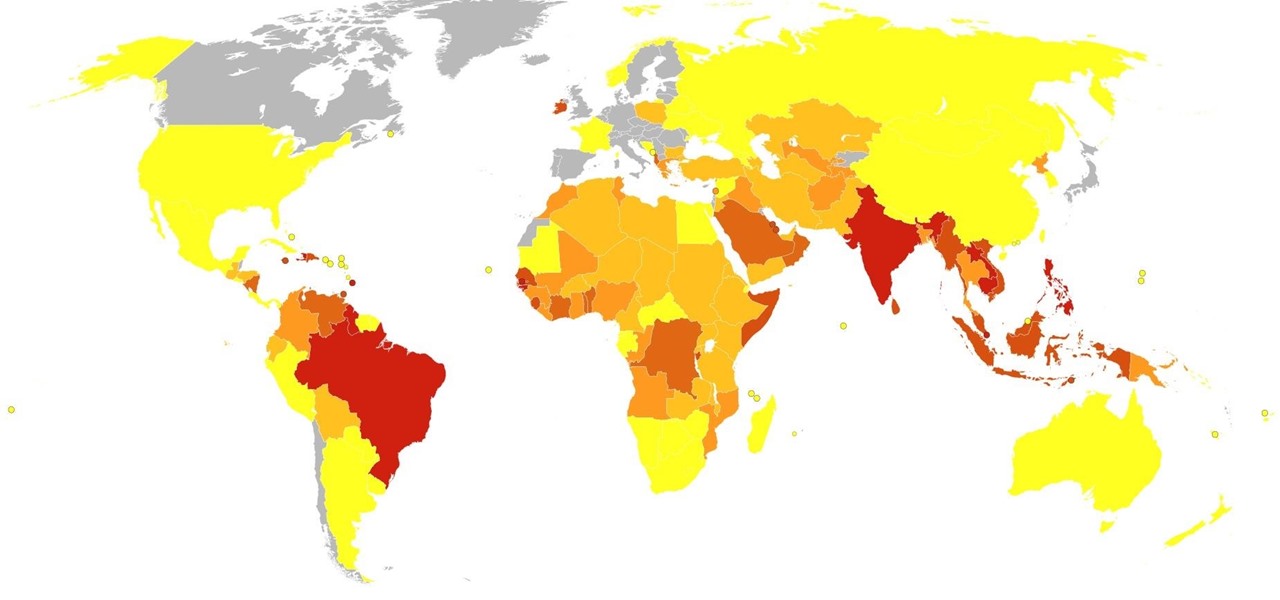
Malaria is a massive worldwide health problem. The Centers for Disease Control and Prevention estimate that 212 million cases of malaria occurred worldwide in 2015 and 429,000 of the infected people died.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

Who would have thought that musical.ly would be the first social media app with a highly successful original show?

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Most of us have already had an encounter with the Epstein-Barr virus, or EBV, for short. As part of the herpes family, it's one of the most common disease-causing viruses in humans. We get the disease with (or without) some nasty symptoms, then we recover. However, EBV stays in our body after the illness has ended, and it's one of the few viruses known to cause cancer.

Dengue fever is a danger to anyone living or visiting tropical or subtropical regions. It can be hard to detect the infection in its earliest and most treatable phase, especially in children. Luckily, new research highlights better techniques for triaging the disease in infected children with more severe symptoms, potentially saving lives.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.

The evolution of our infection-fighting systems may have something to teach modern scientists. That's what a group from the University of Granada in Spain found when they studied a protein that's been around for over four billion years. Their work, by senior author José Sánchez-Ruiz and colleagues in the Department of Physical Chemistry, was published in the journal Cell Reports.

Deep down inside, Kindle Fires are actually Android tablets — the only trouble is, Amazon has layered so much of a skin on top of it all that you can't normally use Android's main app store, the Google Play Store. The Amazon Appstore, which comes bundled with Kindle Fire devices, only has about 600,000 apps, so it would be great if you could access Google Play's library, which boasts 2.8 million.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

One of the biggest features to come out with Android O was the addition of a new System UI Tuner submenu that lets you customize the navigation bar at the bottom of your phone's screen. But as it turns out, this same feature can be enabled on devices running Android Nougat, even without root access.

It has become hard to decipher where your digital imprint ends and your true self begins in today's tech-dominated world. Scrolling through news feeds and endless updates is not conducive to a good night's sleep, nor does it help you lead a well-balanced life.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

Cholera is rapidly spreading in Mozambique, with over 1,200 people infected. Since the outset of 2017, cholera has spread from the capital city of Maputo (pictured above) to three of its ten provinces. Health officials report other areas in the country are seeing case counts rise, and two deaths have been logged so far.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

A tiny louse is responsible for decimating the citrus industry. Diaphorina citri, the louse in question, better known as the Asian citrus psyllid, harbors and spreads the "Candidatus Liberibacter asiaticus" bacteria that causes citrus greening disease.

If you have a mobility impairment that affects your hands, arms, or manual dexterity, a smartphone's touch-based interface can almost be a barrier between you and the mobile internet. Eye-tracking software requires too much computing power for today's smartphones to handle, so it might seem as though there's no good way to interact with an Android device.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

There are two types of Halloween lovers: Those who like culturally-relevant costumes and serving precious ghost cupcakes, and those who live to freak their friends the hell out in the most disgusting way possible.

We're wild for whipped cream in our coffee, atop our brownies, and in-between wafer cookies, so we always have some in our fridge. To be specific, we always have homemade whipped cream in our fridge, because the taste is just so much better than the pre-made stuff.

A strange thing is happening: there are people, groups of people even, walking the streets day and night staring wide-eyed at their mobile phones and laughing like manic children. What are these people doing? Are they taking pictures? Are they participating in some new social media craze? Is their activity an omen that the zombie apocalypse is upon us?

Pie crusts are pretty intimidating if you're an at-home baker with little experience, since there's a lot of science behind making them. A perfectly flaky crust that's golden brown—not charred and black along the edges—requires careful attention, a foolproof recipe, and some decent baking skills.

Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world.

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

There are countless recipes for mug cakes (and breads) on the internet, but not all of them are good. Mug cakes promise a warm, moist, and fluffy cake after a few minutes and with minimal work... but sometimes, all you end up with is a chewy, rubbery mess.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Plastic wrap is, arguably, man's greatest invention—or at least, the 2000 Year Old Man thought so. Its primary use is to protect food from getting dried out in the fridge or on the counter; but if that's all you're only using it for, you're missing out.

There's no doubt you've heard the old saying, "When life gives you lemons, make lemonade." The phrase was penned in an obituary to a dwarf actor in 1915 by an anarchist named Elbert Hubbard, who lost his life five months later aboard the RMS Lusitania when it was torpedoed by a German submarine.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.