Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?
Below are the official rules and guidelines for submitting content to WonderHowTo. Please look over them before publishing any articles. Ignoring the rules could result in deletion of your article or being flagged as a spammer. Most of these rules apply to comments as well.

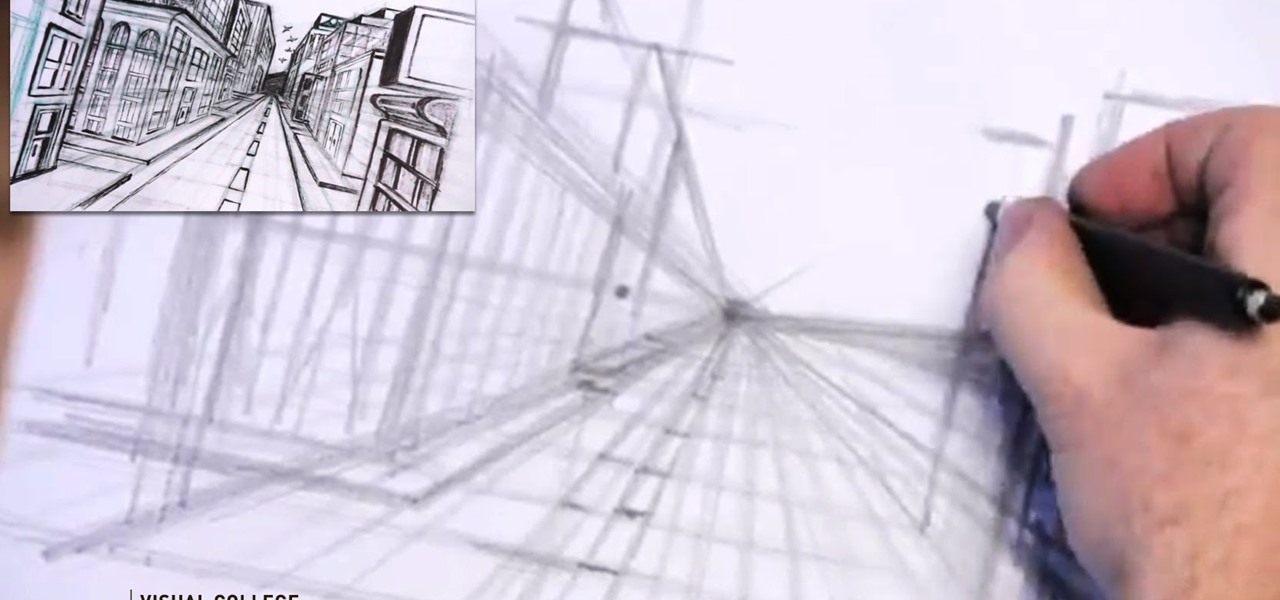
Video: . Step 1: Today We Are Going to Draw a City in One Point Perspective -- Buildings in the City Going into One Point Perspective. Let's Start Our Drawing with the Vanishing Point and Horizon Line. In Order to Get the Feel of the Drawing We Need to Determine Where Vanishing Point Will Be. Feel Free to Improvise and Change It Depending on What You Want to Achieve. Start Mapping Lines in.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches, savory pies, and flaky, crispy turnovers, too. We've already told you how to get perfect, firm fruit pie fillings, so now, let's learn about crust.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Ever since high school, I've been preparing my own taxes. Each year it gets more and more complicated, which results in me filing later and later, avoiding it until I have the time or just can't wait any longer. I even resorted to using TurboTax online to help do some of the grunt work for me these past couple years, but that hasn't stopped me from being lazy about it. I have yet to file my 2010 taxes, but I will very soon. Tomorrow, in fact—before TurboTax raises their prices.
Proposition 22 Prohibits the state from borrowing or taking funds used for transportation, redevelopment, or local, government projects and services. Initiative constitution amendment.
Anyone who follows the TSA blog, run by “Bob”, will know that from time to time the agency attempts to offset the ballooning negative public opinion directed towards it, and the openly criminal behaviour of its employees, by bragging about “dangerous” items that it has discovered and confiscated from the luggage and persons of those traveling through the nation’s airports.
Well another great way to burn up our taxpayer money. From Cold Warriors to targeting trafficking: US military shifts focus in Europe - World News.

After getting slammed with a crazy-big earthquake/tsunami, the Japanese nuclear plant Fukushima Daiichi might be on the brink of meltdown. Not as bad as Chernobyl, but maybe as bad as Three Mile Island. Nobody wishes such a disaster on anyone...anywhere in the world. In the US, there are about 100 nuclear facilities, about 8 of which are located near hot beds of seismic activity.

This video shows how to attract a man like a magnet! There are three powerful principles involved. Men are very attracted by confidence. It is not a question of acting confident, but of being confident. You need to practise thinking about what you like and appreciate about yourself. You should not try to impress a man because he can sense that you are auditioning for him. Principle number one is to stop trying to impress him. Men love to pursue a woman. Think about yourself as a flower and th...

In this tutorial, you will learn how to model a Ducati rear tire using Cinema 4D. We're sure the same principles will apply to any motorcycle tire you decide to model. The guy gives VERY detailed information about tires which should be helpful. Model a Ducati rear tire in Cinema 4D.

The Interactive Lab Primer (ILP) has been developed as part of the Royal Society of Chemistry Teacher Fellowship Scheme, one of the themes of the Chemistry for Our Future program, and initiative which aims to secure a strong and sustainable future for the chemical sciences in higher education. The aim of the ILP is to address the diverse range of experience and skills students bring with them to a university by offering a resource to support their transition from school to the university chem...

Having a website people can easily navigate is common sense. It can save taxpayer dollars & help your agency achieve its mission. Here's how to dramatically improve your website by focusing on your customers' needs & adopting some basic usability techniques.

Double click an edge, select a loop. That's the main principle behind edge loop modeling in modo. Modo has an entire suite of edge tools available for modeling - this tutorial shows you the basics of edge loop selection and getting started with this method of modeling in modo. Edge loop model in modo.

This how-to shows a great muscle combo workout: legs and abs. Men's Health, the preeminent source for fitness videos, breaks it down for you.

This is really cool. He goes pretty deep into the principles of magnetism before actually showing how his generator comes together and works. Great information.

there is no explanation, but this video does visually illustrate the basic principles of VAWT design and construction.

Do you love the internet? Me too. That's why you should learn about Net Neutrality. Though this video was made a few years ago, the basic principles have stayed the same, and Net Neutrality laws are currently on the tables of governments all over the world. Get informed and save the internet!