After spending a good portion of 2017 teasing us with images and bits of news, Lenovo, in a partnership with Disney and Lucasfilm, has finally released its Mirage AR headset along with the Star Wars: Jedi Challenge game collection.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

As you know, it's impossible to be a Steampunk without a pair of goggles. In fact, there are entire communities dedicated to judging other Steampunks based solely on their goggles. A Steampunk without goggles is like Samson without his hair, or a duck without a beak—totally powerless. As I'm sure you also know, the right pair of goggles can instantly render any outfit Steampunk, no matter what it looks like.

Director, M dot Strange, explains how formulating ideas is the most important part of film making, no technical skills.

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

Despite the cancellation of Mobile World Congress and several high-profile companies pulling out of the upcoming Game Developers Conference, Magic Leap is pushing forward with hosting its own developer conference.

We've been predicting the rush of augmented reality wearable makers from China for a couple of years, and now it looks like it's in full swing, with one of the most promising entrants coming from startup Pacific Future.

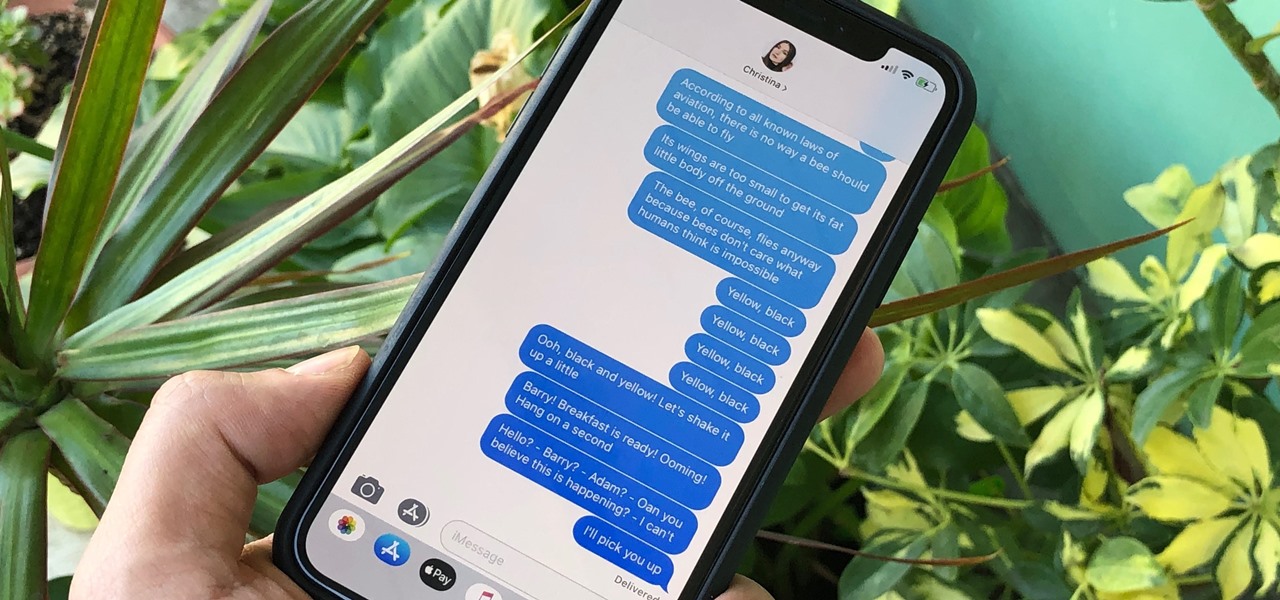
Back in its infancy, the App Store was filled with text bomb apps that allowed users to send a barrage of text messages to friends, family, and foes. It was a fun way to annoy people, but Apple quickly scrubbed the apps because of technical issues. Although text bombs are still banished, you can now use a Siri Shortcut to send text bombs through iMessage on your iPhone.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

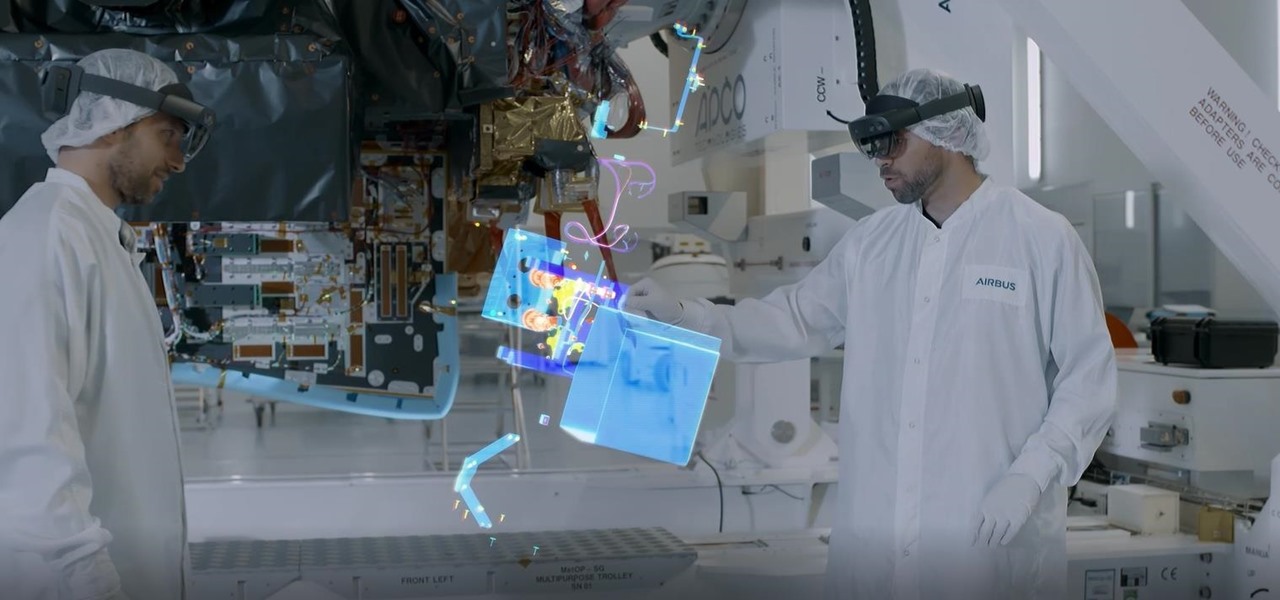
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

The annual Augmented World Expo (AWE) typically packs the front page of Next Reality with new products and services from companies in the augmented reality industry.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

As the opening act to the grand unveiling of the long-awaited HoloLens 2 at Mobile World Congress Barcelona on Sunday, Microsoft showed off the standalone Azure Kinect time of flight sensor, which also happens to supply the improved human and environmental understanding capabilities of the next-generation augmented reality headset.

After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens.

Location-based gaming pioneer Niantic has been preparing its flavor of AR cloud, the Niantic Real World Platform, to bring more realistic and interactive augmented reality experiences to mobile apps. And now the company is looking for a few good developers to help execute its vision on the platform.

Despite funding difficulties that forced Meta to place employees on temporary leave in September, the augmented reality headset maker is reminding enterprise companies that it remains a viable option for visualizing and working with 3D design models.

Augmented reality developers who have exhausted their treasure trove of video tutorials and panels from the recent Magic Leap developer conference can now shift their continuing education attention to Unity.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

Rumors are swirling today that NASA's Jet Propulsion Laboratory (JPL) may have shown us the first public glimpse of the next-generation HoloLens. Are they real? Or just a prototype? We've been digging in all day to find the answers.

While they don't do augmented reality just yet, the latest styles of Snapchat's Spectacles 2 camera glasses serve as a peek into the future of how mainstream AR wearables may look.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.

A fresh batch of developer info has been revealed on Magic Leap's Creator Portal. On Thursday evening, the normally secretive company gave the general public perhaps the closest look yet at Magic Leap One's Lumin operating system.

The shifting sands of immersive computing, currently fluctuating between augmented reality and virtual reality, can be hard to navigate if you're only versed in one of the platforms. But a new series of videos from Leap Motion paints a picture of a near future world in which AR and VR will seamlessly merge together, forcing us to change the way we see both.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

We watched the first piece of public-facing content Magic Leap has released so you don't have to, and, well, you didn't miss much.

If it had come out just a week earlier, around April 1, no one would have believed it. But it's true, Leap Motion has developed its own prototype augmented reality headset, and it looks pretty wild.

This week's Game Developers Conference came at just the right time for Magic Leap, a company that was riding a wave of bad news from legal troubles and rumors regarding Magic Leap One.

Many Samsung fans were excited when the Galaxy S9 kept the 3.5 mm headphone jack. While this is a rare delight in 2018, you also have the option for high quality audio playback over Bluetooth. When used with compatible headphones, the S9's new Bluetooth audio codecs can greatly improve audio quality.

When Google first announced Android Oreo (Go edition), many believed these devices would be focused more on developing countries. However, thanks to ZTE, we'll be getting Android Go stateside, so US customers on even the tightest of budgets can still enjoy the convenience of a smartphone.

In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.

While the public now knows much more about the Magic Leap One: Creator Edition today than it did yesterday, there's still a quite a bit that's unknown. One of the most significant questions — with any mixed reality product — is the field of view. How much of what we see through these glasses will contain the computer's virtual creations?