While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

See how to increase the mW of a 5 mW Green Laser Pointer!
Brian Sredd gives tips and pointers on how to make loops in mixmeister.
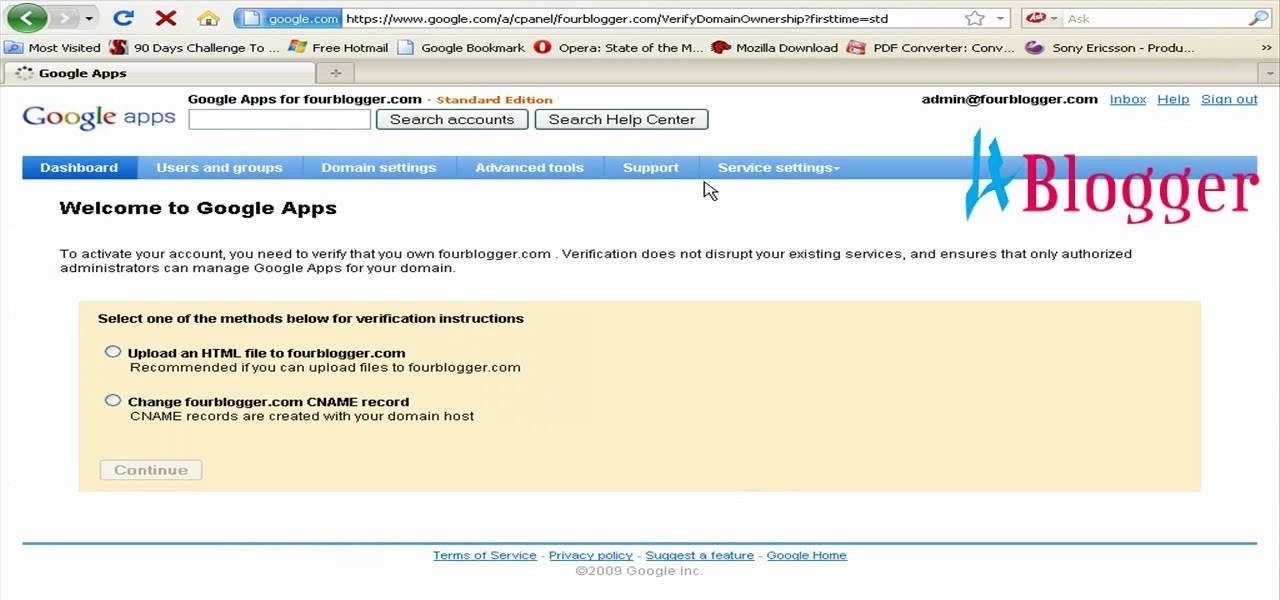
You can create the Google apps email like Gmail for your domain. So to do this first you need to go to the google.com/a and click on the standard in "other Google apps editions". Now click on "get started". Now select "administrator: I own..." and enter your domain name and click get started. Now on next page create your account by filling all the fields and click continue and now fill the info of your administrator account and click I accept button. Now next step is for the verification of y...

This tutorial teaches you how to create a blue and gold cut crease makeup look. Use MAC's uppity fluid base on the lid and inner corner. For the lid, use Shock Tart and put it all over. For the inner corners use Obsessive Compulsive Cosmetics called Oric. Blend it into the lid color. Now take MAC's technical color in Auto Day Blue from the outer corner going through the crease. With a small smudge brush, use a dark blue color to cut the crease. Blend the blue out towards the eyebrow making it...

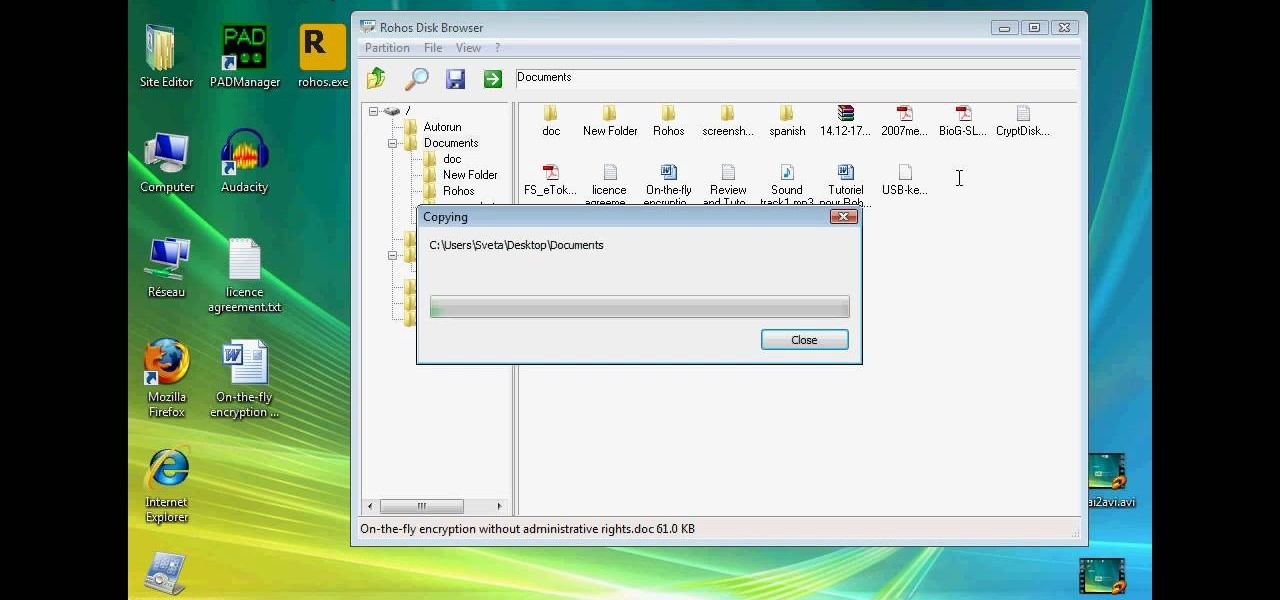
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).

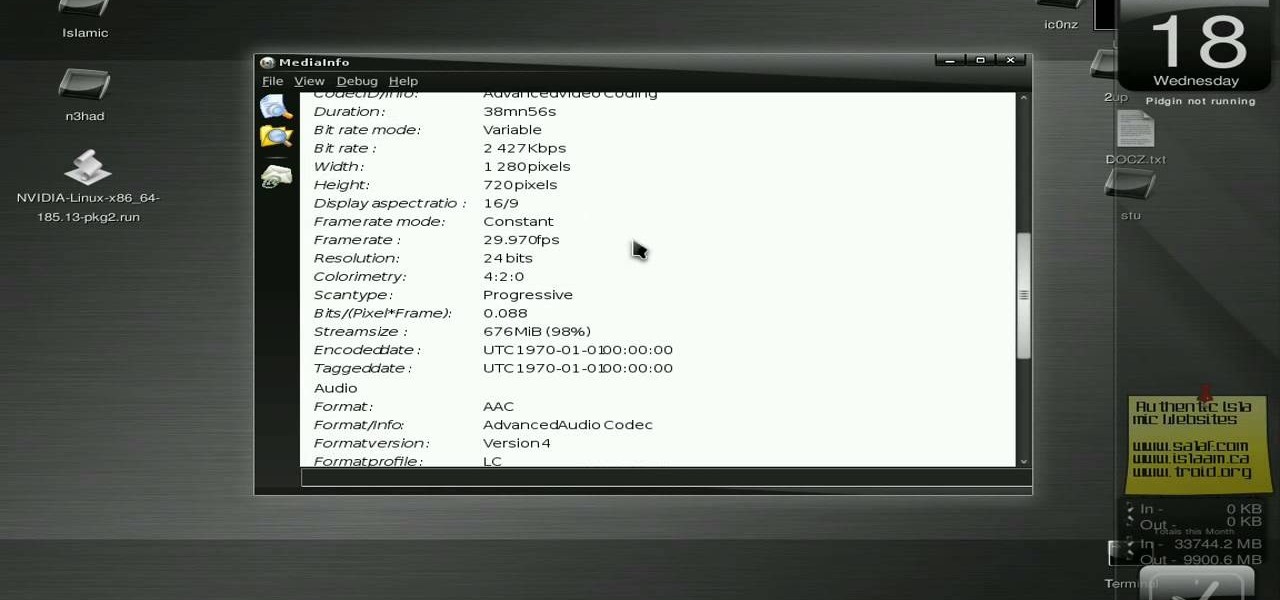
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the MediaInfo GUI on Ubuntu Linux.

Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze.

Last week's Augmented World Expo felt like a distant memory by this Monday, as Apple unveiled ARKit 2.0 at its annual Worldwide Developers Conference. Certainly, this news would overshadow anything augmented reality this week as it nearly eclipsed AWE when early reports leaked of the toolkit's new superpowers.

On Wednesday, June 6, the people at Magic Leap finally (FINALLY) decided to give the public a dedicated, slow, feature-by-feature walkthrough of the Magic Leap One: Creator Edition. How was it? About as good as it gets without actually getting to see what images look like through the device when wearing it.

Using the ARKit 2.0 announcement as its springboard, software maker Adobe is looking leap up to the level of Unity Technologies and Epic Games, the companies making the go-to tools for creating augmented reality experiences.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

If you ever want to go beyond the basics on your Android phone, unlocking the hidden "Developer options" menu is the first thing you should try out. With it unlocked, you can change the way parts of stock Android looks, enable ADB connectivity with your computer, add visual reactions to taps, and more.

Developers in the augmented reality space are sitting on the bleeding edge of a hot technology. With the intense interest, especially in the tech circles, there are a large number of people working on potential solutions and uses for the technology. There is also a lot of time, money and effort being put in the tools and infrastructure for the technology. For better of for worse this also means constant changes.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

If you've ever used the YouTube mobile app for Android or iOS, you've probably noticed a cool little multitasking feature it has. While watching any video, you can simply swipe down on your screen to shrink the video down to a thumbnail view, which then allows you to browse the rest of YouTube while the original video keeps playing.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

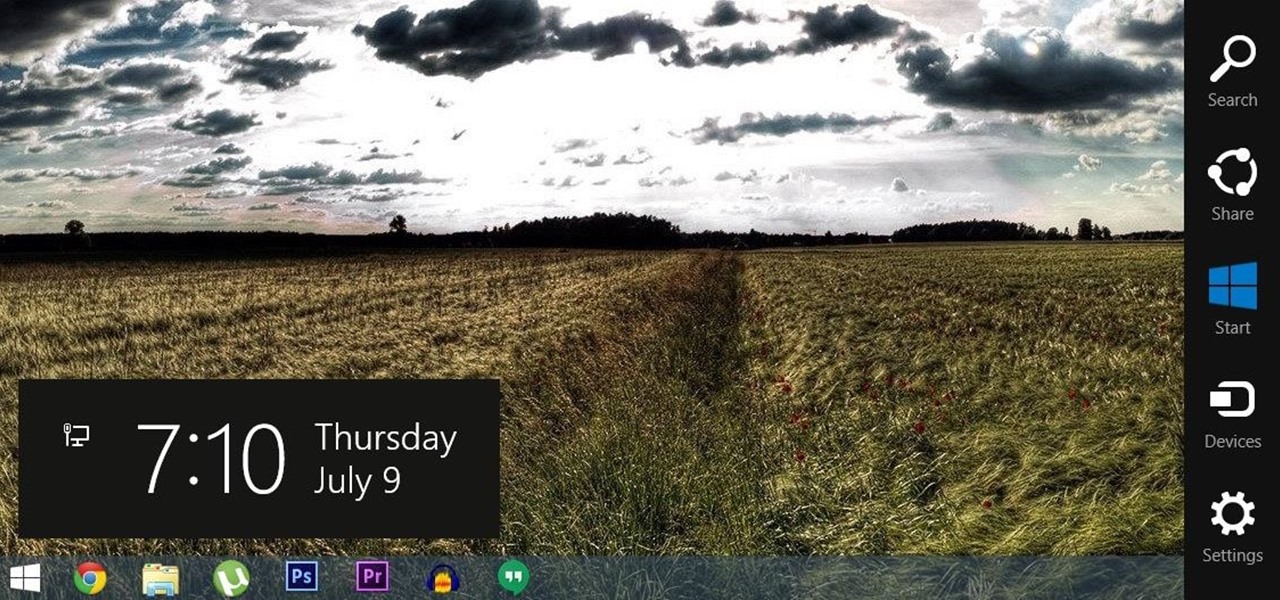
For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

When streaming services like Spotify or Pandora compete for customers, the main differentiating factor is the size of their libraries. While these and comparable services usually run somewhere around $10 per month, a completely free alternative may actually have the most expansive library out there.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Winter is coming... and if you don't get that Game of Thrones reference, it's okay, you're still cool in my book.

Do you love music and need a little extra cash? Do you think you have a knack for entertaining others with your rockin' playlists? Check out this video and learn how to turn that musical mind into a career as a wedding DJ. The most memorable part of the wedding reception is the music and dancing and you could be a part of it! Follow these steps and have people complimenting you on your awesome tunes as they leave the reception.

The reverse dives are a special group of dives that entail both technical and graceful maneuvering. Learn to perform these amazing dives with tips from a professional diving instructor in this free video series.

Null Byte readers are no strangers to the powers and benefits that come from learning how to code. By knowing only a handful of programming languages and platforms, an intrepid developer can create everything from best-selling apps to spyware in the comfort of his or her own home.

The Halloween season is the perfect time for telling scary stories, but augmented reality is here to bring the tradition of frightening children to the modern age.

Arthur van Hoff, former CTO and co-founder of Jaunt, is taking his immersive content talents to Cupertino.

If there was a version of the Doomsday Clock for counting down the release of Microsoft's HoloLens 2, then the caretakers of that imaginary clock would move the minute hand to "one minute to midnight."

The mystery surrounding the release of the next version of the HoloLens has been swirling for months, but at least some of that mystery may removed in the coming weeks.

Epic Games released Unreal Engine 4.21, bringing a number of new features, bug fixes, and improvements for augmented reality development, including deeper support for Magic Leap One and the addition of support for the Windows Mixed Reality platform and headsets.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

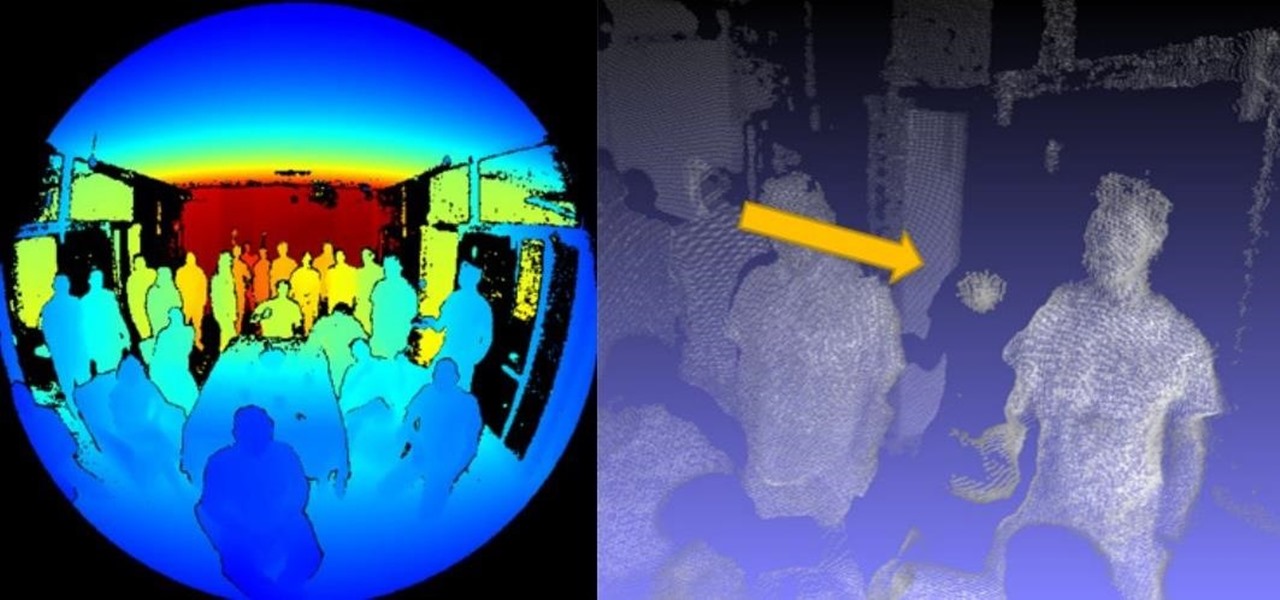
Images captured by Microsoft's next generation Kinect depth-sensing camera that will facilitate augmented reality experiences in the next version of the HoloLens and give computer vision to untold multitudes of connected devices in enterprise facilities, have made their way into the wild.