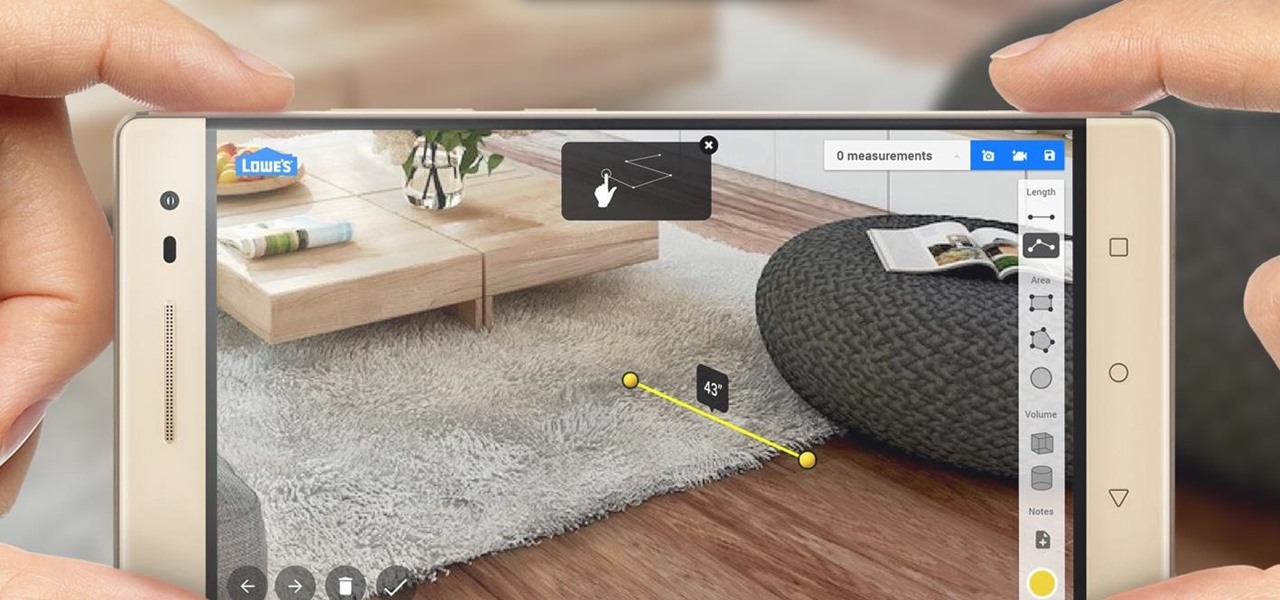
One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.

A fresh batch of developer info has been revealed on Magic Leap's Creator Portal. On Thursday evening, the normally secretive company gave the general public perhaps the closest look yet at Magic Leap One's Lumin operating system.

The shifting sands of immersive computing, currently fluctuating between augmented reality and virtual reality, can be hard to navigate if you're only versed in one of the platforms. But a new series of videos from Leap Motion paints a picture of a near future world in which AR and VR will seamlessly merge together, forcing us to change the way we see both.

As it prepares to ship its first product by the end of the summer, Magic Leap has managed to impress yet another high-profile investor in telecommunications giant AT&T.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

We watched the first piece of public-facing content Magic Leap has released so you don't have to, and, well, you didn't miss much.

If it had come out just a week earlier, around April 1, no one would have believed it. But it's true, Leap Motion has developed its own prototype augmented reality headset, and it looks pretty wild.

This week's Game Developers Conference came at just the right time for Magic Leap, a company that was riding a wave of bad news from legal troubles and rumors regarding Magic Leap One.

Many Samsung fans were excited when the Galaxy S9 kept the 3.5 mm headphone jack. While this is a rare delight in 2018, you also have the option for high quality audio playback over Bluetooth. When used with compatible headphones, the S9's new Bluetooth audio codecs can greatly improve audio quality.

When Google first announced Android Oreo (Go edition), many believed these devices would be focused more on developing countries. However, thanks to ZTE, we'll be getting Android Go stateside, so US customers on even the tightest of budgets can still enjoy the convenience of a smartphone.

In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.

While the public now knows much more about the Magic Leap One: Creator Edition today than it did yesterday, there's still a quite a bit that's unknown. One of the most significant questions — with any mixed reality product — is the field of view. How much of what we see through these glasses will contain the computer's virtual creations?

After spending a good portion of 2017 teasing us with images and bits of news, Lenovo, in a partnership with Disney and Lucasfilm, has finally released its Mirage AR headset along with the Star Wars: Jedi Challenge game collection.

Elon Musk's SpaceX is launching the world's most powerful rocket. The Tesla founder and CEO says the company is about to go through "manufacturing hell" to make delivery schedules for its new Tesla 3. Somehow, Musk says Tesla will offer Level 5 driving (so you can take a nap while your car drives you to and from work) within two years.

Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.

China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Over 90% of ride-or-die iPhone users will upgrade to the latest Apple smartphone, according to a recent survey. Really, though? Well, Morgan Stanley certainly seems to think so.

The Google Pixel was just knocked off its pedestal as DxOMark Mobile's best smartphone camera, courtesy of the HTC U11. Ouch ...

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

Stratford may soon become Canada's answer to Silicon Valley as the driverless car industry arrives. Potentially changing the character of the Ontario town known for hosting the Stratford Festival, a celebration of all things Shakespearean and stage-related.

Updated 5/2/17: CultofMac reports analysts at Deutsche Bank are confirming the delays. The analysts believe the delays are due to "component shortages and technical challenges." This would corroborate the rumors listed below. We here at Gadget Hacks will bring you more on this story as it develops.

The rumors surrounding the next iPhone and Apple's ambitions toward augmented reality have been going on for months, and a fresh development brings back the idea of Apple's Smart Connector bringing the two together. The Verifier, an Israeli news site, claims the next suite of iPhones (iPhone 8, iPhone 7s, and 7s Plus) will all sport Smart Connectors for both AR and wireless charging.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

The US Department of Education has put together a competition called the EdSim Challenge with a $680,000 purse to facilitate next-gen education. The event calls upon augmented and virtual reality, as well as video game developers, to bring immersive simulation concepts to prepare the workforce of the future.

Things are definitely starting to shape up with iOS 10. After three developer betas of the upcoming operating system, Apple has begun rolling out the developer beta 4 release for iPhone, iPad, and iPod touch, which focuses mostly on refining some of the cool new features.

Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

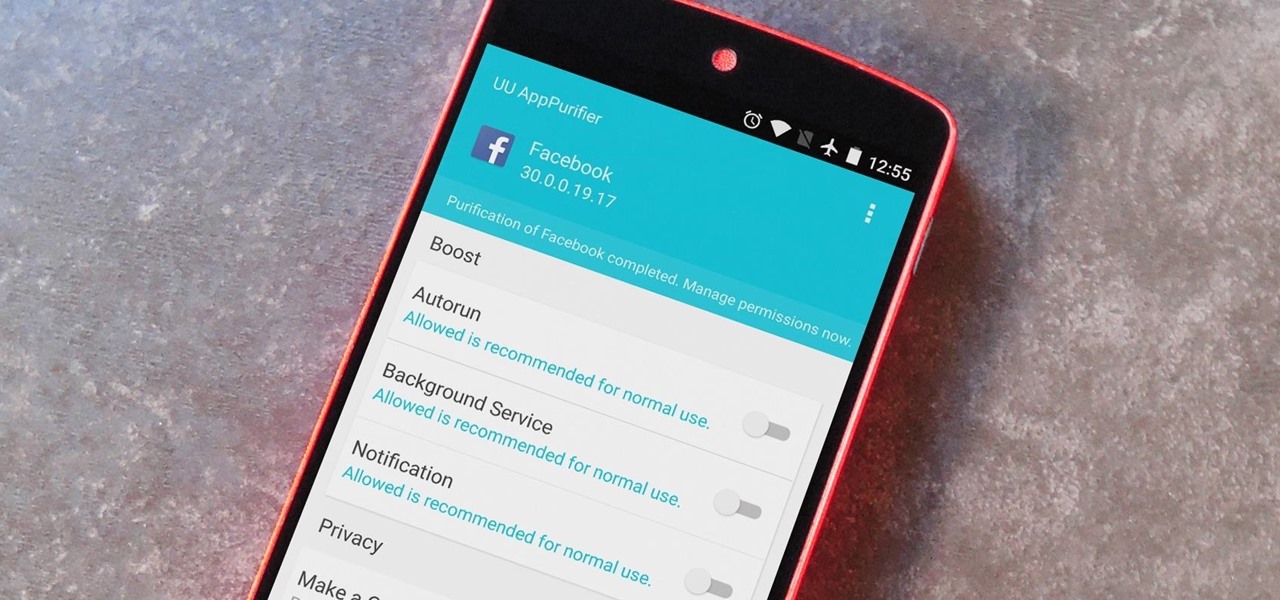
When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first place.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Like many others, I like a good cocktail every now and then, and I've always been impressed when my cocktail enthusiast friends would come up with a new drink or even just remember how to concoct a Clover Club (FYI, it's made with gin, raspberry syrup, lemon, and egg white). There's a secret bartenders and craft cocktail aficionados know, though: It's all about math, the simplest and most intoxicating math. Pythagoras would be so proud.