Need to change a little décor in your home or apartment? Blinds are the perfect solution for bringing a room to life... or maybe just for blocking out the sun. This video tutorial will show you how to fit roller blinds. Roller blinds can be kind of tricky, but if you have a little help, it's a cinch. Now, go fit a Roller blind!

Need to change a little décor in your home or apartment? Blinds are the perfect solution for bringing a room to life... or maybe just for blocking out the sun. This video tutorial will show you how to fit wooden venetian blinds. Wooden venetian blinds can be kind of tricky, but if you have a little help, it's a cinch. Now, go fit a wooden venetian blind!

Need to change a little décor in your home or apartment? Blinds are the perfect solution for bringing a room to life... or maybe just for blocking out the sun. This video tutorial will show you how to fit vertical blinds. Vertical blinds can be kind of tricky, but if you have a little help, it's a cinch. Now, go fit a vertical blind!

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.
Augmented reality has taken the advertising industry by storm, but the technology has a steep learning curve. Luckily for advertisers, Unity is here to flatten the curve a bit.

To build hype for the HoloLens 2 among developers, Microsoft is borrowing a page out of Magic Leap's playbook.

On Thursday, Magic Leap decided to step up its efforts to foster its developer community by launching the Independent Creator Program.

The display is one of the most critical components in augmented reality hardware, and on Tuesday, one of the companies making that component, Avegant Corp., closed a funding round of $12 million to support development of next-generation AR displays.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

Magic Leap has reached a major milestone in the lead-up to the launch of its Magic Leap One: Creator Edition by opening access to its developer portal and software development kit (SDK) to all developers.

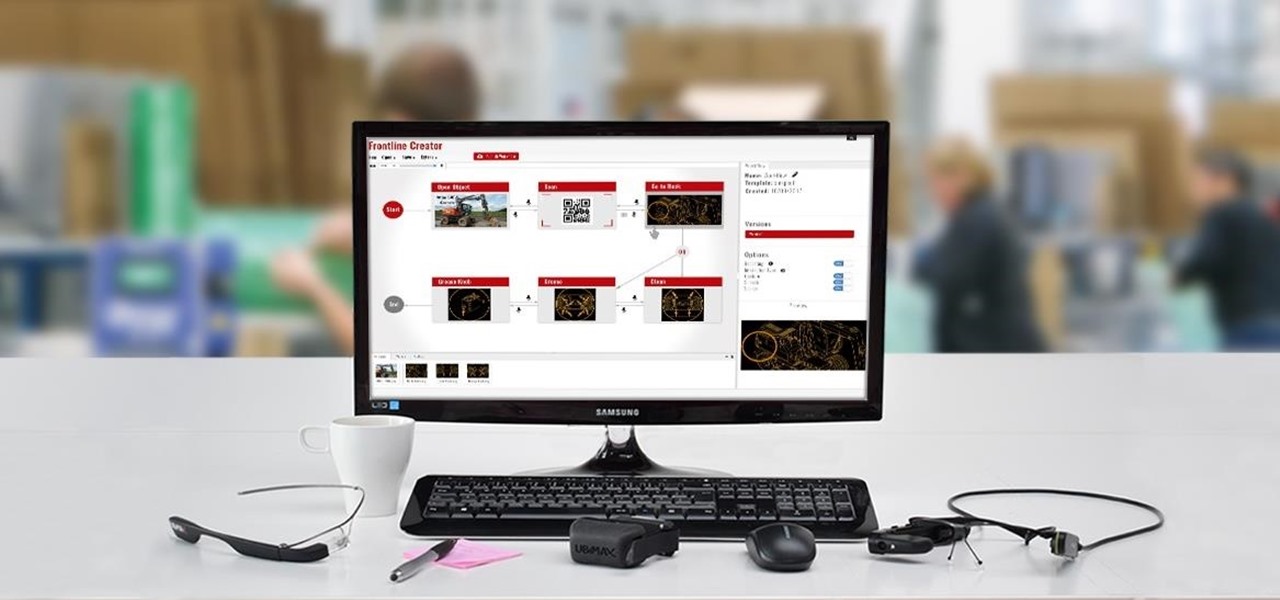
Augmented reality software provider Ubimax unveiled their graphical authoring and publishing tool for their Frontline enterprise platform to attendees at Augmented World Expo Europe today.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Matte and flat colors have became quite popular. I was surprised to see how many cars used these colors at SEMA 2011.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Do you love music and need a little extra cash? Do you think you have a knack for entertaining others with your rockin' playlists? Check out this video and learn how to turn that musical mind into a career as a wedding DJ. The most memorable part of the wedding reception is the music and dancing and you could be a part of it! Follow these steps and have people complimenting you on your awesome tunes as they leave the reception.

The reverse dives are a special group of dives that entail both technical and graceful maneuvering. Learn to perform these amazing dives with tips from a professional diving instructor in this free video series.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

Last week's Augmented World Expo felt like a distant memory by this Monday, as Apple unveiled ARKit 2.0 at its annual Worldwide Developers Conference. Certainly, this news would overshadow anything augmented reality this week as it nearly eclipsed AWE when early reports leaked of the toolkit's new superpowers.

On Wednesday, June 6, the people at Magic Leap finally (FINALLY) decided to give the public a dedicated, slow, feature-by-feature walkthrough of the Magic Leap One: Creator Edition. How was it? About as good as it gets without actually getting to see what images look like through the device when wearing it.

Using the ARKit 2.0 announcement as its springboard, software maker Adobe is looking leap up to the level of Unity Technologies and Epic Games, the companies making the go-to tools for creating augmented reality experiences.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

In a LinkedIn post published on Tuesday, Microsoft's leading advocate for the HoloLens made a prediction that the mixing of immersive technologies will define augmented reality in 2018.

A group of researchers from Stanford University and Princeton University has put together the largest RGB-D video dataset to date with over 1,500 scans of over 700 different locations across the world, for a total of 2.5 million views.

This is a Q&A video with the question asking if glaze putty can be applied over primer or not. In this short Q&A video I am going to answer this question.

Contemporary dance moves are more technical and definitely more serious than your average club dance. You won't be seeing the Booty Dance in any contemporary dance classes, that's for sure.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

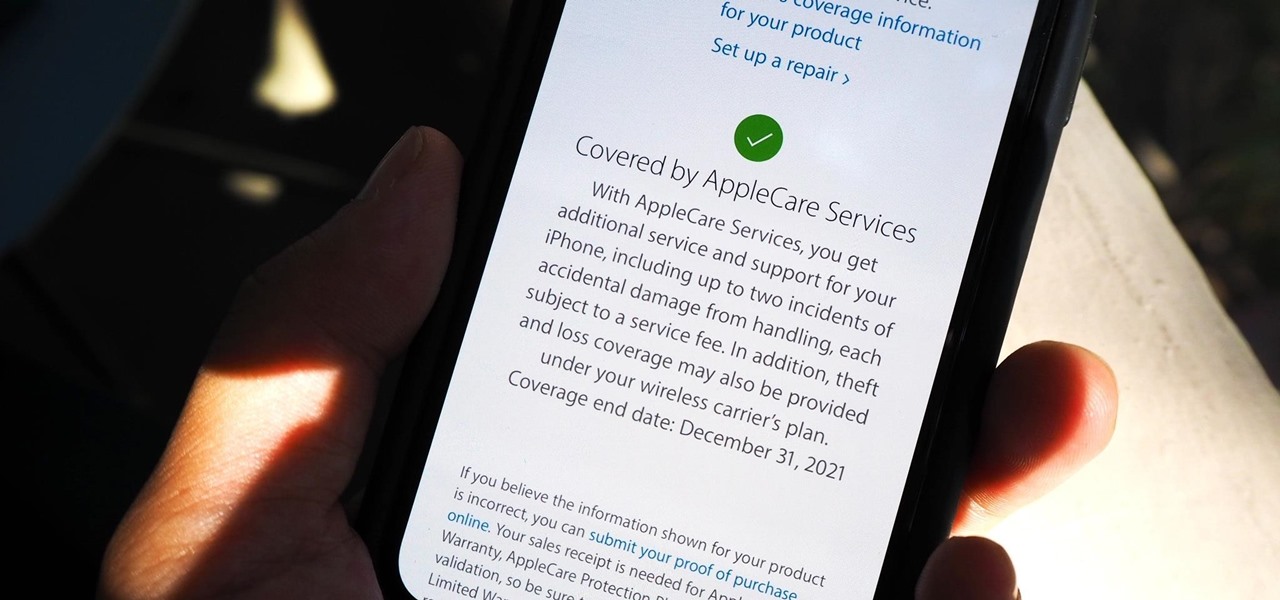
Let's say that the screen on your iPhone is showing signs of discoloration, which makes the display annoying to use. You'll need a replacement display or a new iPhone as soon as possible. If you have one of the newer iPhone models, the cost to fix it might be more than your wallet can handle, but a warranty may still cover it, and there are ways to check quickly.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.