Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

We last saw China-based augmented and virtual reality headset maker Shadow Technologies at last year's Augmented World Expo, where they had the Action One, one of the wildest augmented reality headsets we've seen, on display.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Many new, emerging technologies are coming to our faces. Some are already here, and it's hard to tell what's what. We've taken a deep dive into the three main types (virtual, augmented, and mixed reality), but if you need a quick primer, this infographic will do the trick.

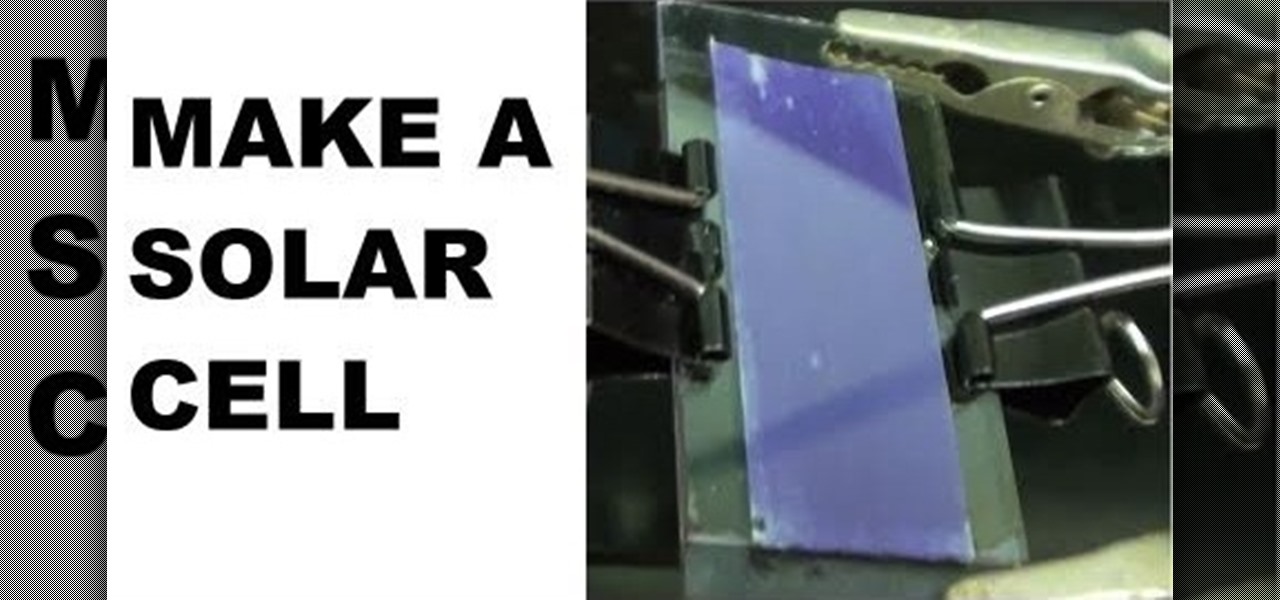
Discover the power of raspberries! Literally. In this NurdRage science video, learn how some crushed raspberries and some titanium dioxide (TiO2) can create a powered dye-sensitized solar cell. Inside a raspberry is something called anthocyanin, which is a flavonoid pigment. Commercially purchased solar cells are way more powerful than this DIY solar cell, but with a little improvement, who knows. Nurd Rage also lets you know how this works.

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.

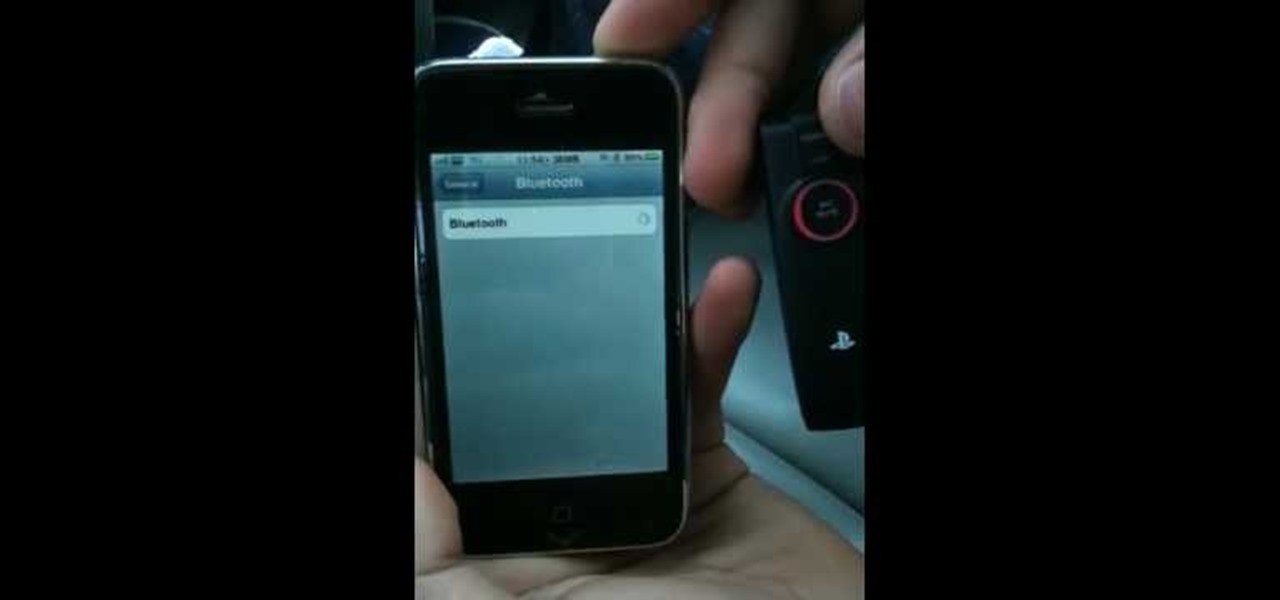
Look around you. Chances are (if you haven't been living under a rock for the last few months), you have at least several snazzy electronics gadgets lying around. From your PS3 to iPhone, iPad to laptop, your ADD will find a source of diversion no matter which way you look.

You want the best quality photos you can get, and the Canon EOS 7D digital SLR camera makes perfecting your pictures easy. There is a range of technologies to enhance image quality. This video shows you the many options you can use.

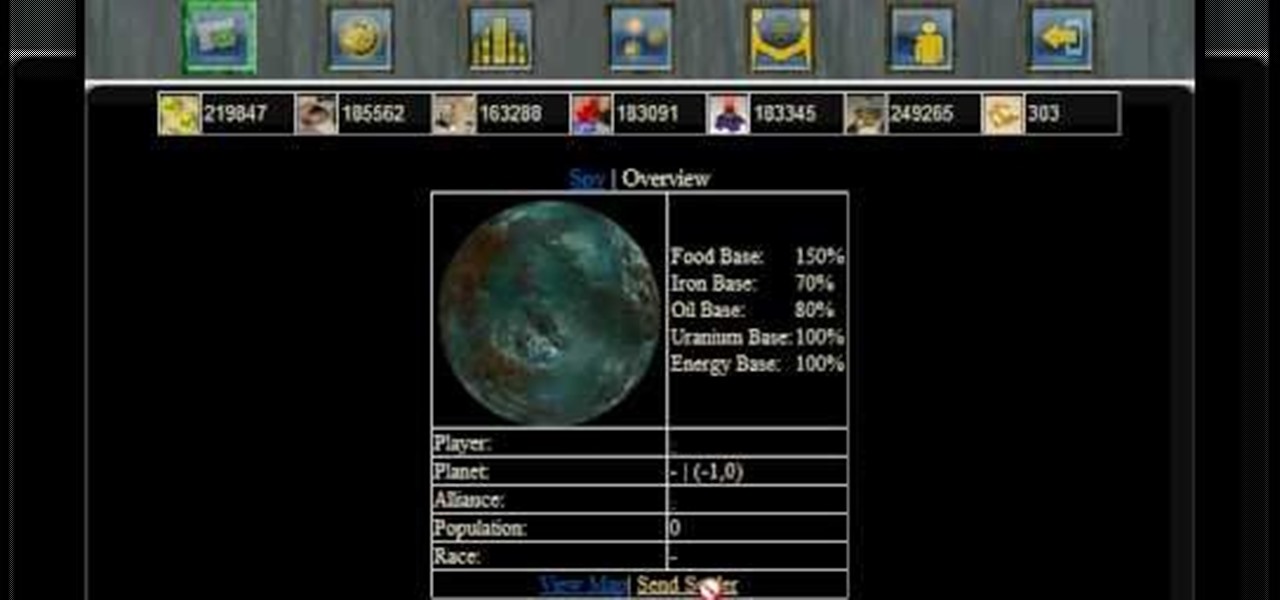
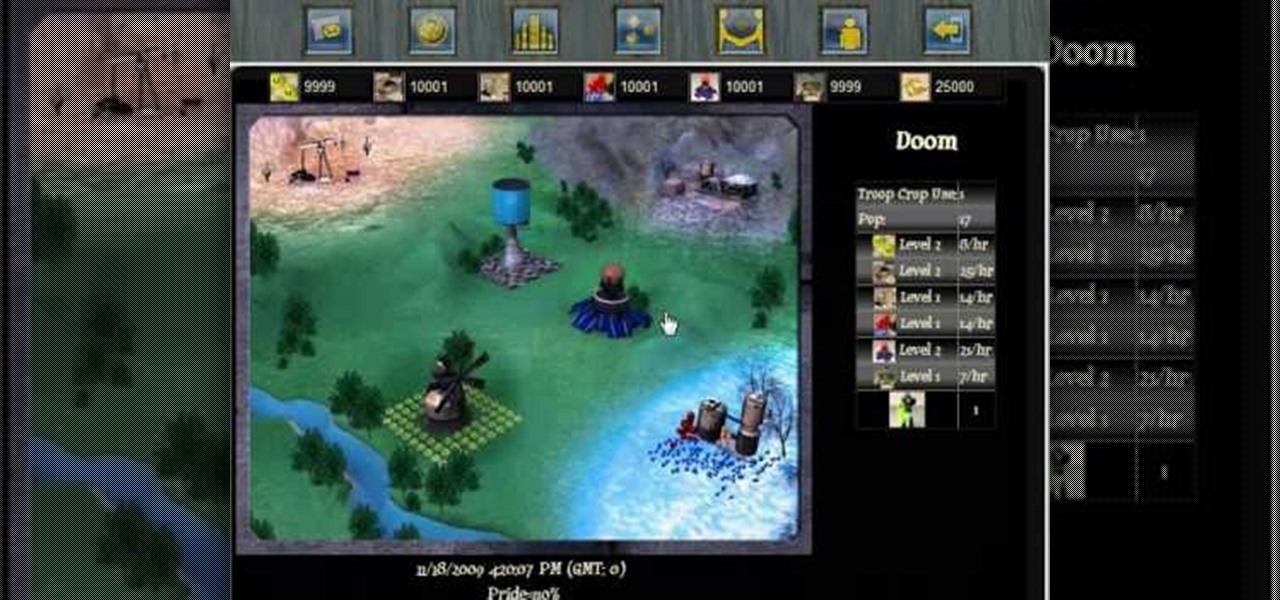
Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...

In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

One of the new technologies rolled into Adobe Illustrator CS3 is Kuler. Kuler first appeared on Adobe Labs and has become its own community where people are posting color groups left and right. Now you can not only take advantage of these color groups on the web and download them, but you can also get to them directly in Illustrator CS3.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

The bleach bypass effect is a classic, and is large part of what gave Saving Private Ryan it's distinctive look. This video will teach you how to apply bleach bypass yourself using Adobe Premiere Pro. Give your video that old-school look using the most modern of technologies.

Two companies behind a number of augmented reality devices have joined forces to develop a 3D depth-sensing camera system that will facilitate computer vision capabilities for augmented/virtual reality experiences and more.

A new survey shows that the majority of companies have an interest in using augmented reality, though adoption remains low. Meanwhile, two companies with support roles in the augmented reality industry are seeing positive financial results.

The Nintendo DS is one of the most technologically advanced handheld gaming devices out there. Not only does it have dual screens, but a touch screen as well. Some of the more recent DS' even have a built in camera. But with all great technologies, problems are sure to rise. In this tutorial find out how to repair the Nintendo DS Lite top screen. Remember, opening the device can possibly result in a voided warranty, so know what you're doing and good luck!

In order to play SWF files, you need to download SA Flash Player. You can find this program on a website called Mega Upload. For FLV files you need to download the applian FLV player. You can find this program at a website called applian technologies at the address http://applian.com. Once you have downloaded and installed these programs, you will be able to do such things like watch videos you couldn't previously access and play games on your computer that, again, were not available before. ...

This video teaches Korean Food cooking just like a Food Channel TV show. In this video we learn how to make SoGoGi JangJoRim or boiled beef and quail eggs. Unlike western technologies, this recipes shows how to first soak hand cut beef in water to remove blood and then to boil the meat with spicy vegetables like hot peppers, green onion, ginger and garlic. After cooking, the meat is removed and shredded while the cooking broth is saved and the veggies are discarded. The shredded meat is added...

There are dozens of light bulbs on your vehicle, illuminating everything to the road in front to the license plate in the rear, and for all of the modern technologies given us, most automotive bulbs are essentially the same as on out grandfather's car. So, it's no wonder why burnt out auto light bulbs are the number one cause of lighting failure.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

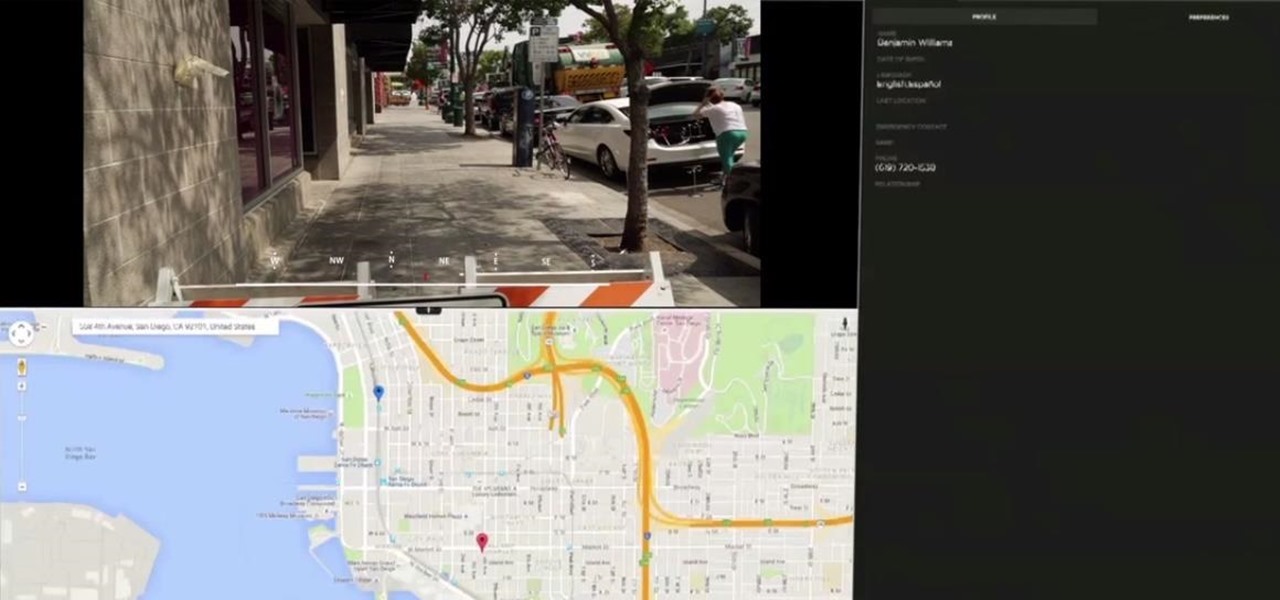
Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

The reality of tomorrow will not be static. We're here to bring you a daily look into the cutting edge innovations poised to merge the impossible worlds of our imagination with real life. We're NextReality.

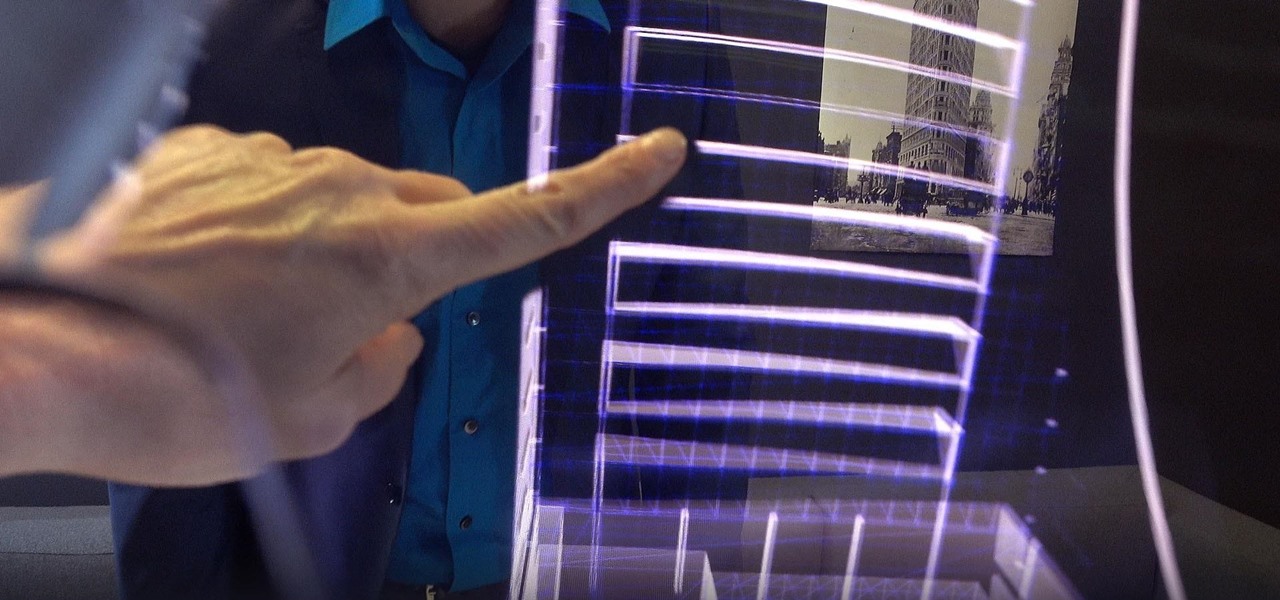
The interactive displays of the future as visualized in Steven Spielberg's science fiction classic Minority Report, as well as the augmented reality interfaces used by millionaire playboy Tony Stark in the Marvel Cinematic Universe, are now closer to becoming reality in the military realm.

Augmented reality might not be able to cure cancer (yet), but when combined with a machine learning algorithm, it can help doctors diagnose the disease.

Smartglasses maker Vuzix has emerged with the first hardware powered by the Snapdragon XR1 chip, roughly nine months after Qualcomm introduced the chipset designed to drive augmented reality wearables at the Augmented World Expo in Santa Clara.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.

Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

The long and somewhat tumultuous journey of Leap Motion has come to an end, thanks to another startup.

It may sound like deja vu, but neural interface startup CTRL-labs has closed a $28 million funding round led by GV, Google's funding arm, for technology that reads user's nerve signals to interpret hand gestures.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Influenced by the growth of augmented and virtual reality technology as well as 3D computer vision, Ericcson Ventures invested in Matterport, whose hardware and software help companies create AR/VR experiences.

While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.