Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Cited by many listed on this year's NR30 list as the most important event in the last 12 months, last year's release of ARKit catapulted Apple CEO Tim Cook to the top of Next Reality's rankings. This week, we dug deeper by explaining why he's at the top of the list of NR30 Mobile AR leaders.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

This week, we're beginning to see the wide ranging impacts of some of the early iterations of augmented reality hardware and software.

Now that ARCore is out of its developer preview, it's time to get cracking on building augmented reality apps for the supported selection of Android phones available. Since Google's ARCore 1.0 is fairly new, there's not a lot of information out there for developers yet — but we're about to alleviate that.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

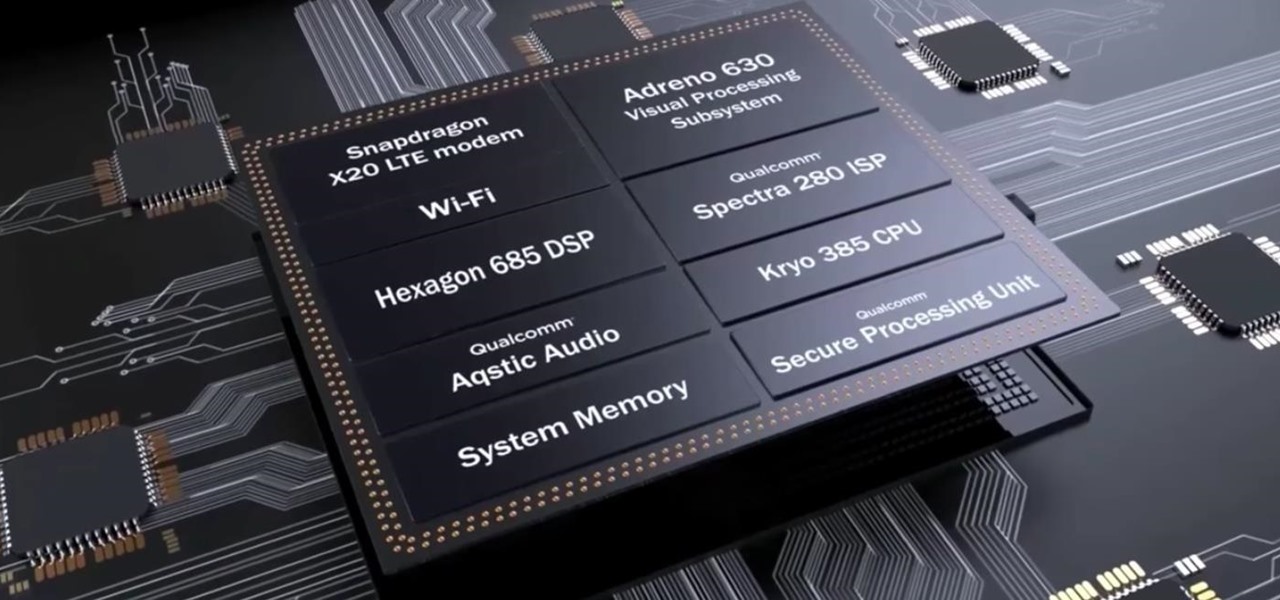
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

The latest and greatest in Qualcomm's long line of mobile processors, the Snapdragon 845, is now set to touch down along with the Galaxy S9 and S9+. And as gorgeous as Samsung's newest flagships are, the processor that powers them under the hood is just as highly anticipated.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

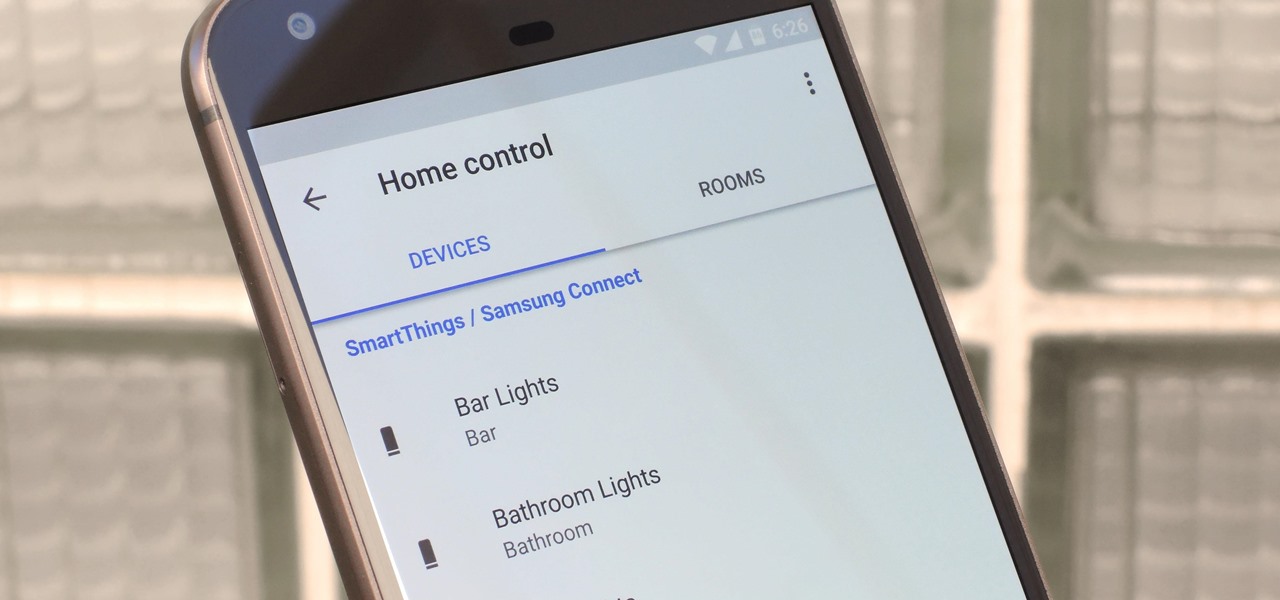
The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to happen when these two technologies intersect.

Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.

Dengue fever is a danger to anyone living or visiting tropical or subtropical regions. It can be hard to detect the infection in its earliest and most treatable phase, especially in children. Luckily, new research highlights better techniques for triaging the disease in infected children with more severe symptoms, potentially saving lives.

Our quest to find new antibiotics has taken a turn — a turn down the road, that is. A team of scientists from the University of Oklahoma is scooping up roadkill and searching for bacteria on them that might yield the world's next antibiotic.

Using extreme time-lapse microscopy, scientists watched a virus take over a bacteria to create a cell that looked and functioned more like a plant or animal cell. True story.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

While visiting the Made by Google pop-up shop in New York City this morning, I had a chance to try out the new Daydream View virtual reality headset. First impressions are important, and Google's new mobile VR product makes a good one. The headset is made of a soft fabric that most evokes a beloved old college sweater that's well worn but properly cared for. The demo only featured the Slate (darker gray) model, though customers will ultimately be able to choose from either Slate, Snow, and Cr...

Before the iPhone 7 was launched and all the unrealized reports about the phone's features were tucked back into their annual rumor mill, there was some speculation about wireless charging. Specifically, whether or not the iPhone 7 and 7 Plus would support it. We now know they don't, and here's why.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

Even as the world continues to grapple with the pandemic, the tech industry continues to chug along, with some looking for ways to present new products, and in some cases continue major conferences that reveal the latest in augmented reality developments.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.