With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

Many people don't realize much better audio can sound on their phones. While it's solid to begin with, Samsung has included several options in the Galaxy Note 10+ that will upgrade your listening experience to profound status.

It's a strange time for us iOS beta testers. While Apple prepares for the general release of iOS 13 on Thursday, it's also beta testing that software's successor, iOS 13.1. An iPhone updated to iOS 13 on Sept. 19 will only have 11 days before seeing 13.1 in its Software Update page on Sept. 30. To prepare for this release, Apple released the fourth iOS 13.1 public beta, just about the same time as its developer counterpart.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.

OnePlus, whose phones always challenge for the title of best spec-to-price ratio, releases two main devices every year. There's the primary flagship in late spring, then an iterative update with the "T" suffix in fall. Typically, there's not much difference between the two, but this year, OnePlus is mixing up the formula a bit.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

What if, back in 2013, Google Glass had launched not as a Star Trek Borg-like eyepiece, but as a pair of seemingly normal shades, with the augmented reality lens and camera hidden within the frame?

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

Need a unique gift idea for the techy person in your life? Look no further than that phone they always have in their hand. There are plenty of great accessories, apps, subscriptions, and other smartphone-related goodies that will improve their quality of life, and thoughtful gifts like that are always the best-received.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

There are more than a few subscription-based movie streaming apps available for Android and iPhone, each with different benefits and varying pricing plans. Needless to say, it can get expensive fast if you sign up for multiple services because you can't decide on what's best. Hopefully, we can help you out with choosing the right video-on-demand app to spend your hard-earned dollars on.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

With all the controversy around the Pixel 3 XL, the regular-sized Pixel 3 might be the phone of choice for most users. Thanks to the huge boost in screen size, the little brother is now an easier pickup for those who like a bigger screen. And once more, the internals are the same, giving you the same experience as the 3 XL without the display notch.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Autism affects 1 in 68 children in the US, and that means it affects at least 1 in every 68 families. More boys than girls are diagnosed as being on the autism spectrum, and it's estimated that almost 60,000 12-year-olds in the US have autism. That is a 37-fold increase from the 1 in 2,500 children diagnosed just 30 years ago.

Don't believe what you read on the internet, especially today, when web giants like Amazon, Google, and the like showcase their otherworldly products and services. If they seem too good to be true, they probably are—but that doesn't make them any less fun.

Being able to sleep deeply and fully is one of the foundations for real health. When you go without it, you feel subhuman and incapable of dealing with the world—just ask a student who's had to pull an all-nighter or the parents of a newborn. In fact, many studies have shown that lack of sleep or irregular sleep is linked to acne, weight gain, and depression.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

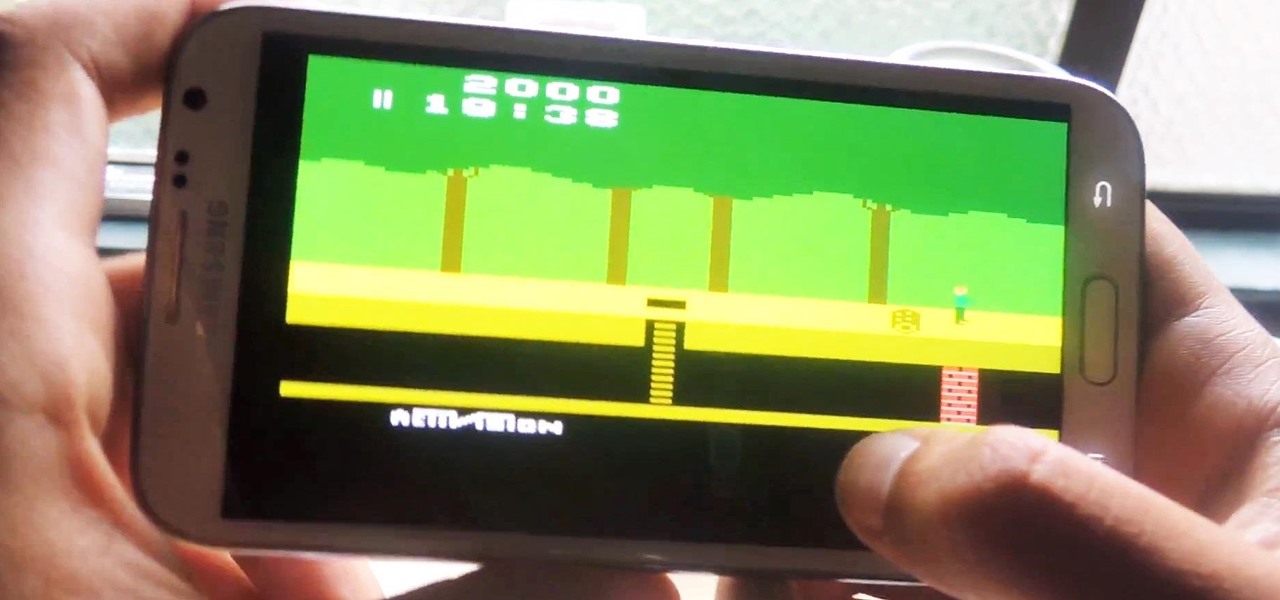
Atari—it's the home gaming console officially responsible for starting the trend of sleepless nights and malnutrition amongst kids and adults alike. If you think Call of Duty is addicting, try playing Space Invaders in the '80s on the old Atari 2600 (voted the second greatest console of all time by IGN).

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive.

Are you having problems because the game was released a long time ago and the more experienced players are better than you? Then you should be very excited to find out that I will be giving you some general tips & tricks about the different classes that I have learned the hard way.

Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But what's worse than your electronics just giving up on you?

While many of the features in the iPhone 16 and 16 Pro series build on what we've seen in previous iPhone models, Apple has packed the 2024 lineup with iOS 18 and plenty of fresh upgrades worth considering.

The new iPhone 16, 16 Plus, 16 Pro, and 16 Pro Max are worth upgrading to, but if you want more advanced features, especially for the camera, you may want to take a closer look at the iPhone 16 Pro and iPhone 16 Pro Max.

The app with the most significant update on iOS 17.5 is, by far, Apple News. While there are a few changes in Books and Settings, as well as minor changes in apps like Podcasts, Apple News has at least 11 new features and changes you should know, some of which are worth getting excited about.