DRUM! Magazine — the leading magazine for drummers and percussionists worldwide — has announced the biggest drumming event ever to take place in Northern California. On Friday, August 13, drummers will descend on the San Jose Repertory Theatre in the heart of Silicon Valley to witness three of the world’s most exciting drummers — extreme drumming sensation Marco Minnemann, Tower Of Power funk master David Garibaldi, and former Mars Volta wunderkind Thomas Pridgen — for an evening of mind-blow...

“On this day he had lived with that feeling, with death breathing right in his face like the hot wind from a grenade across the street, for moment after moment after moment, for three hours or more. The only thing he could compare it to was the feeling he found sometimes when he surfed, when he was inside the tube of a big wave and everything around him was energy and motion and he was being carried along by some terrific force and all he could do was focus intently on holding his balance, ri...

Hallelujah, a miracle tool has been released to the world. This Windows/Mac tool is called Spirit and it enables you to jailbreak any iPhone, iPod Touch or iPad quite easily. And Gizmodo is all over it, with an in-depth guide on exactly how to do it.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Another media player bites the dust. First, we saw the extinction of the phonograph and gramophone. Then came the fall of eight-track tapes. Even modern record players became more and more obsolete, with DJs switching over to the world of digital music. And today— the end of cassette players! What's next? Compact discs?

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Advances in technology continue to make our lives easier and more convenient. If you want to send fax, for instance, you no longer need to own a fax machine. You can easily and quickly send fax directly from your computer in one of several methods, including via an Internet fax service provider or using Windows built-in Fax and Scan tools. Read on how to use an Internet fax service, one of the faster faxing methods, to send fax messages from your PC.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.
Sergio Peralta Advisor: Jessica Davis

Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this is both altruistic and an unsubtle attempt to boost followers).

Google's much anticipated eBook Store has finally opened. As of today, the digital bookselling enterprise is awaiting your needs, with over 3 million eBooks to read directly on the web or on other platforms, like Android, iPhone, iPad, Sony and Nook devices.

If you've run out of time for all of our more time-consuming Halloween costume ideas, here are some places on the web for free, downloadable paper masks. There must be at least 100 options among these links to satisfy your last-minute costume needs! Just download, print, and cut 'em out to the appropriate size, then either glue a stick/handle on or tie some elastic string on.

Now that Vision Pro, Apple's mixed reality headset, has been announced, Apple can free up some R&D resources to commit to its upcoming foldable iPhone, which has been rumored for just as long as Vision Pro has. Will it be a flip-style or a larger foldable? Let's see what all the industry experts and Apple leakers have to say.

Facebook's earnings calls are generally focused on numbers—revenue and user growth. But this week the company's founder and CEO, Mark Zuckerberg, carved out a significant portion of the call to elaborate on Facebook's plans for immersive computing.

On Friday, the Tokyo Olympics finally kicked off after massive delays and complications due to the pandemic.

Now that Snapchat has extended its virtual try-on powers from the face and feet to the wrist, Samsung is leveraging the new capability, along with an interactive twist, to sell its smartwatches.

For awhile now, Google has offered the ability to translate text through smartphone cameras via Google Translate and Google Lens, with Apple bringing similar technology to iPhones via Live Text.

Just when everything seemed settled over at Magic Leap, it turns out that the internal tumult is still in play.

When we got our first look at US Army soldiers testing Microsoft's modified HoloLens 2 last year, it still looked very much like the commercial edition, with some additional sensors attached.

The story of the HoloLens has been a mix of work and play. But while many developers have devoted time to creating gaming and entertainment apps for the HoloLens 1, with the HoloLens 2, Microsoft has been encouraging everyone to focus more on the enterprise side of things.

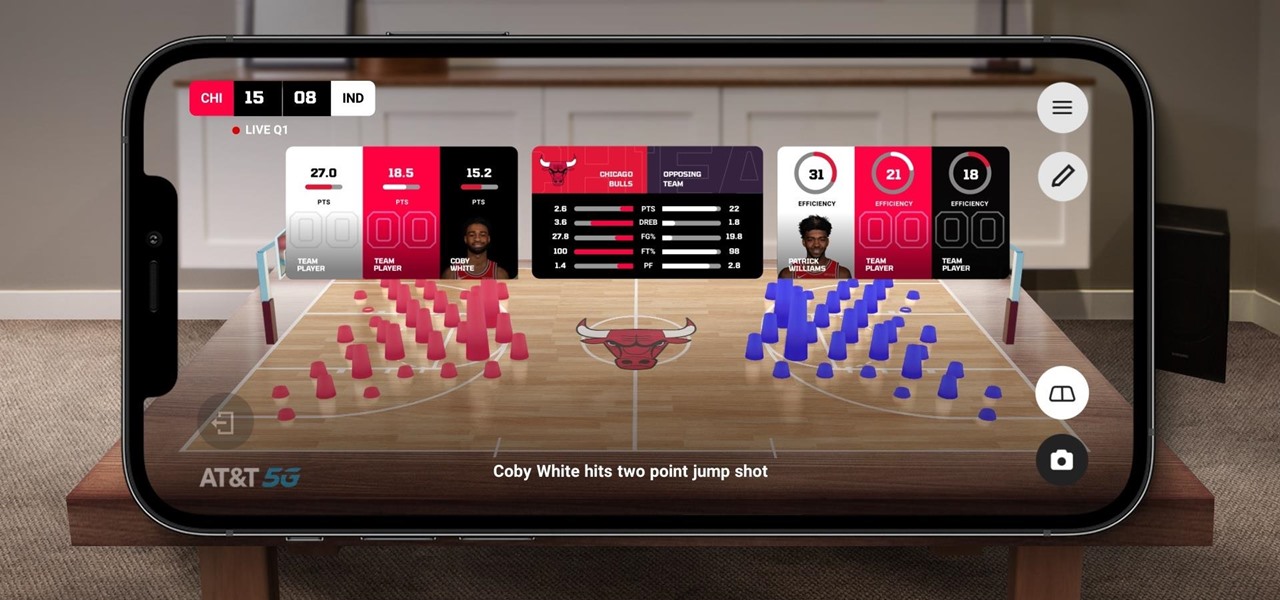
The Chicago Bulls may not be very relevant in the current NBA standings, but they do lead the league in one other area.

Over the past three years, Epic Games has raised billions of dollars in funding on the success of Fortnite as well as Unreal Engine, one of the top 3D engines available for developing games and AR experiences.

While Apple has been rather secretive about its work on AR wearables (despite the abundance of leaks revealing details about their unannounced devices), Facebook has been rather chatty about its plans for smartglasses.

What is old is new again. In this case, a classic arcade game gets the augmented reality treatment. In a new promotion playing off its ad campaign featuring actor Craig Robinson (The Office, Hot Tub Time Machine), Pizza Hut has turned its pizza boxes into a virtual Pac-Man game via web-based AR technology.

The moment many of the crypto savvy insiders in augmented reality and VR have been waiting for is here: we're finally getting our first big auction of NFT art that exists purely as a hologram.

Based on recent reports, we've got a pretty clear picture of what to expect from Apple's rumored augmented reality headset expected to arrive next year, but the outlook is more opaque concerning its consumer-grade AR smartglasses.

Apparently, we learned nothing from Jurassic Park, as scientists are still working on bringing extinct species back to life. Until that day comes, you can interact with long-lost animals through augmented reality...if you have a newer model iPhone.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.

After the mobile augmented reality platforms of ARKit and ARCore moved Google's previously groundbreaking Project Tango (the AR platform that gave us the first smartphones with depth sensors) into obsolescence in 2018, we've seen a bit of a resurgence of what was then a niche component for flagship devices.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

The company augmented reality that Rony Abovitz was trying to build at Magic Leap apparently wasn't working out the way he hoped it would. That company, built on dreams, music, and future-looking entertainment, rather than truly new technology, came with a $2,300 price tag for a device using dynamics most mainstream consumers have never even tried.

Over the past two product cycles, Apple has been rumored to be preparing to reveal its Apple AirTags tracking devices that can help iPhone owners find their possessions with augmented reality.

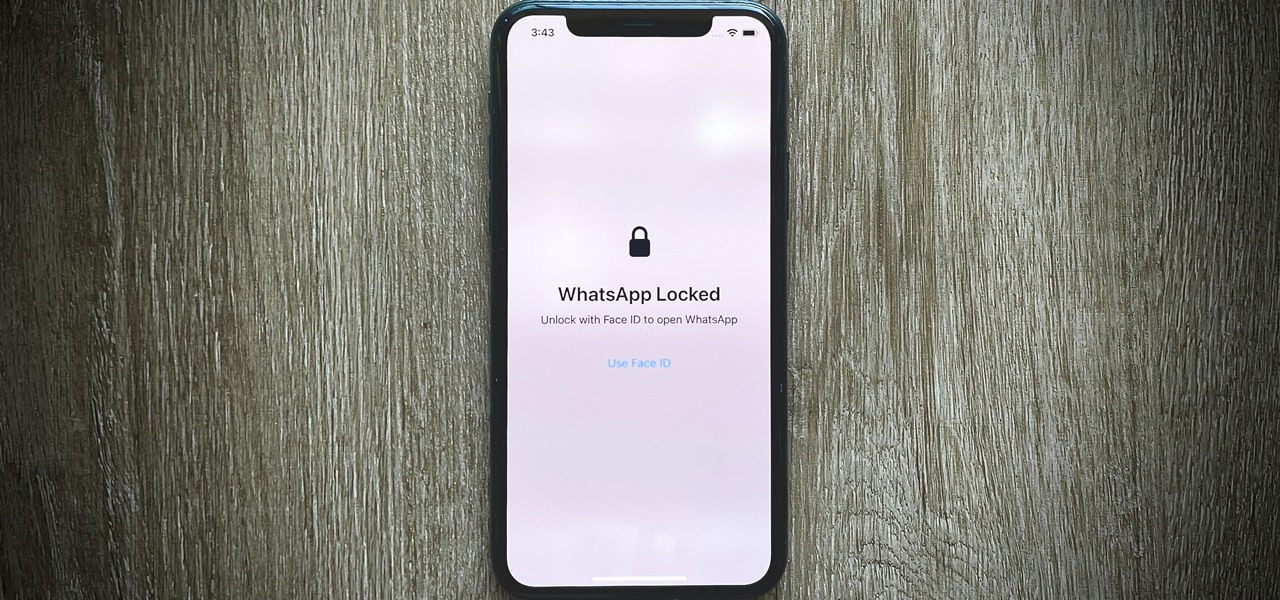
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

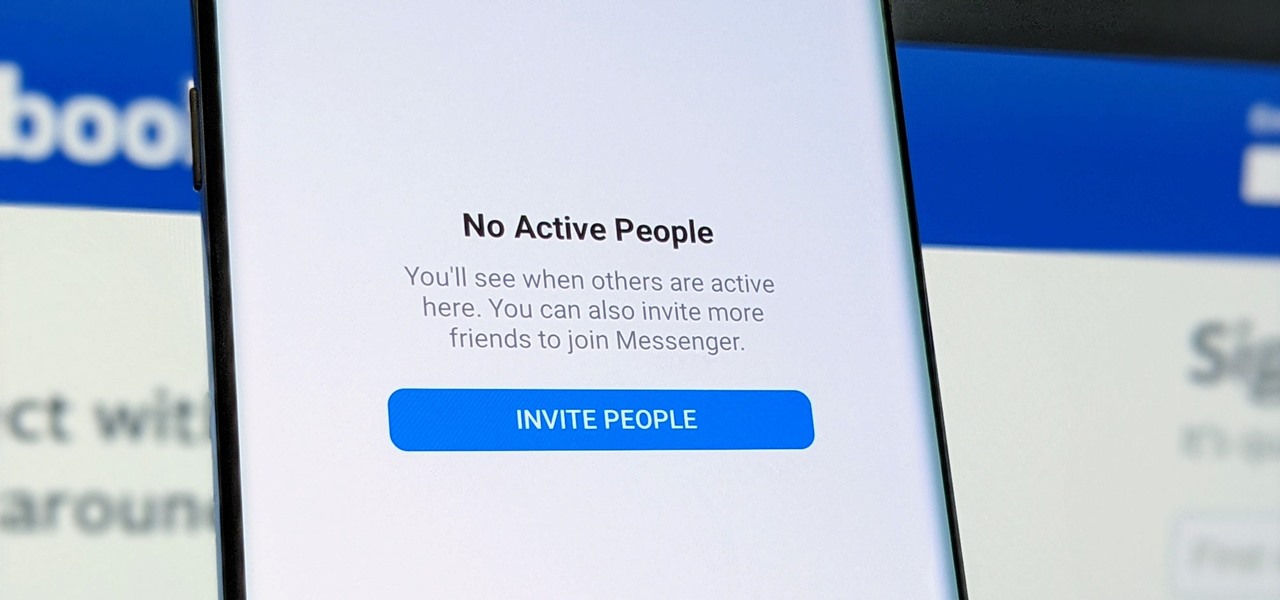
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

Apple just released iOS 13.6, and while there aren't a ton of new features here, there are some pretty amazing ones to be on the lookout for.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.