
How To: SQL Injection! -- Detailed Introduction.
Hello NullByte! This will be my first How To series.


Hello NullByte! This will be my first How To series.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

Hello, multicolored-hat hackers!

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.
Fifty-four percent of Americans 18 and older drink coffee every day, and why not? With 100 milligrams of caffeine per six ounces of drip coffee, it's just the morning beverage to wake you up and kickstart your day. You can feel the caffeine surge through your body like the Holy Ghost, making you aware, focused, and ready for action.
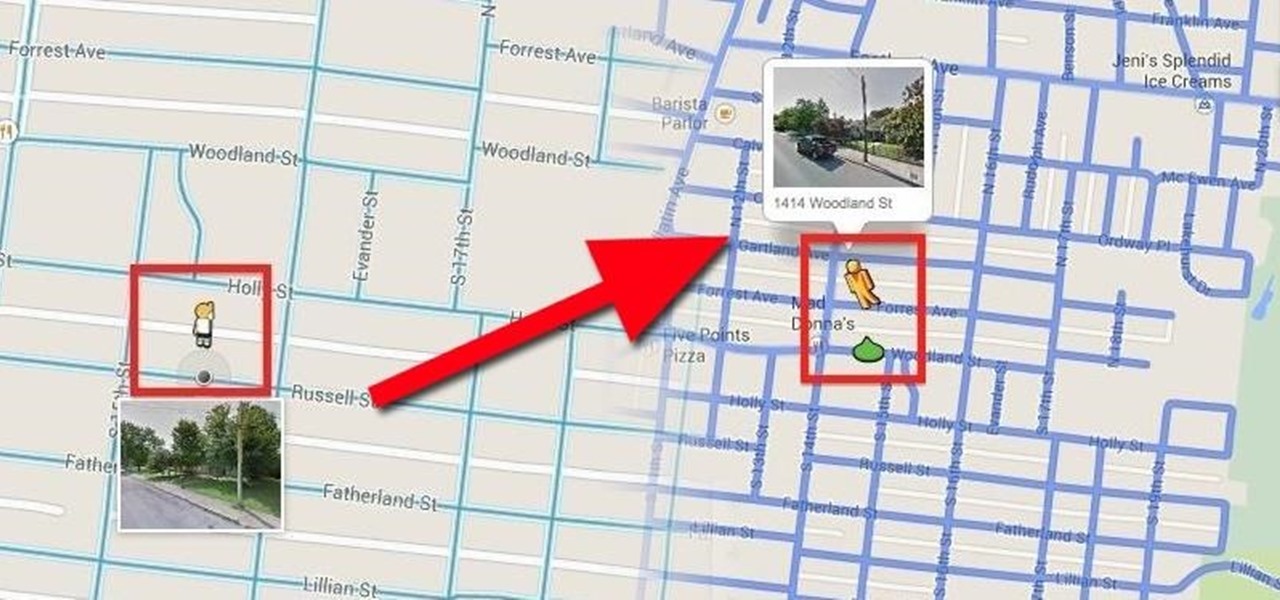
When the Google Maps web app got a massive redesign earlier this year, I was pretty excited to try it out, but it was a fairly disappointing update for me. The slower load times, confusing street view, and bicyclist neglect are just a few of the reasons I don't enjoy it over the old classic Google Maps. The brand new drag-and-drop measuring tool released this week is actually pretty useful, but not enough to change my mind.
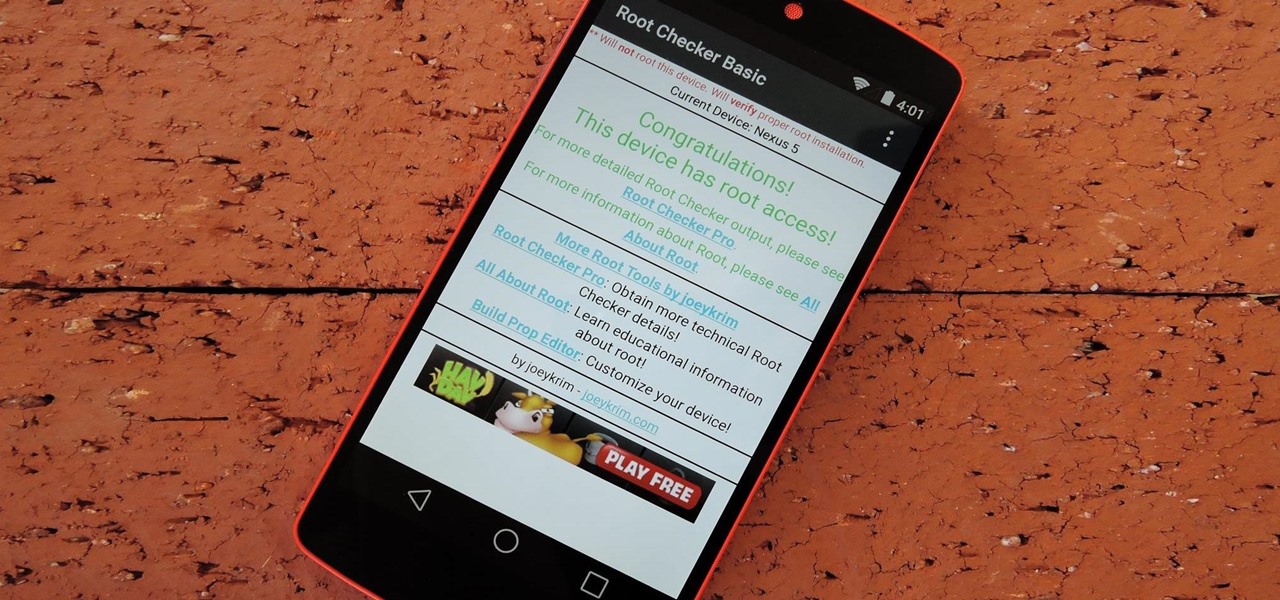
While the preview images for Android's upcoming "L" release just came out yesterday, the new firmware has already been rooted, as is standard with its openness. So if you were feeling reluctant to try Android L because it didn't support existing root methods, then you might want to reconsider.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

You may or may not have heard of alt-rock band Panic! at the Disco, but a year and a half ago they released a single called "The Ballad of Mona Lisa", which had an accompanying music video that was Steampunk-themed. In fact, here's the video:

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

On Monday, the social media giant Facebook suffered a massive outage that, as of this writing, is still in effect.

The initiative known as Project Aria has been the focus of curiosity around Facebook's augmented reality plans ever since Mark Zuckerberg revealed the device around this time last year.

Facebook Reality Labs chief Andrew "Boz" Bosworth does a lot of hinting and teasing of what's coming next at Oculus, often with only a vague timeline on the horizon.
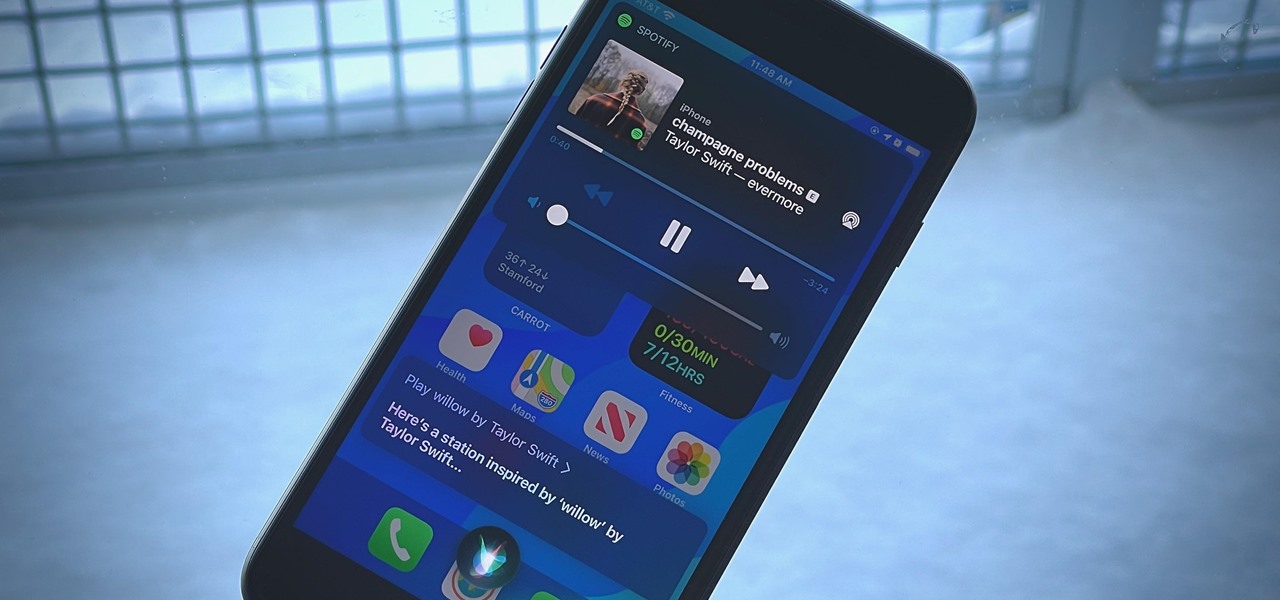
It's no secret that Apple and Spotify haven't exactly gotten along in the past, but things are looking better than ever in iOS 14.5.
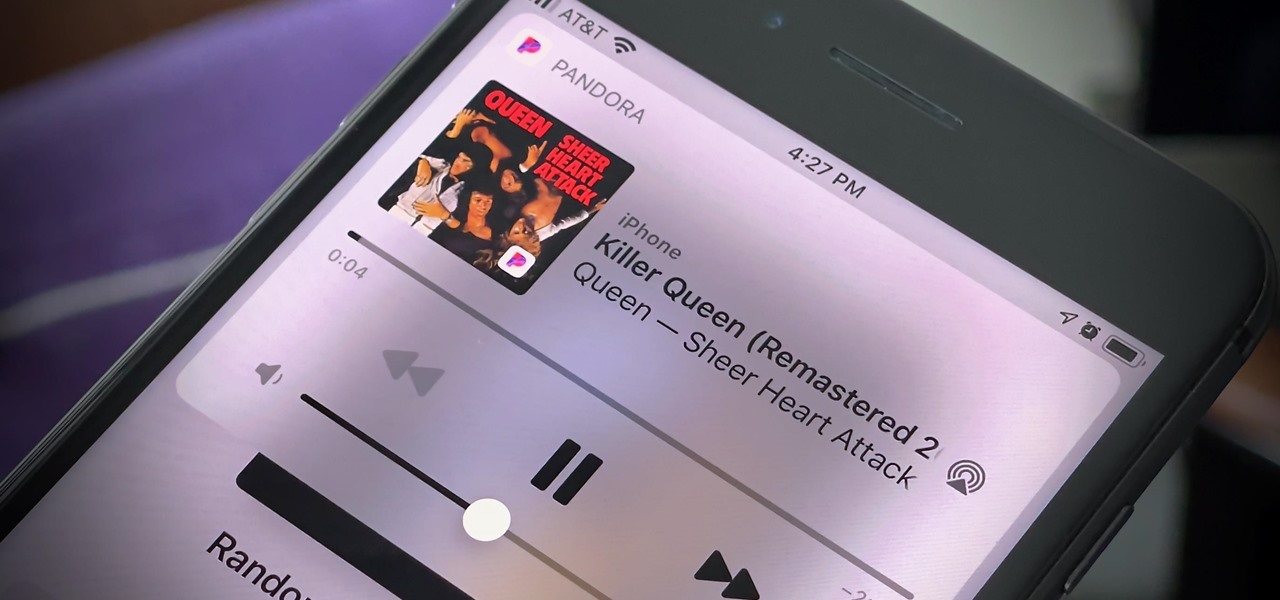
If Pandora is your primary music app on your iPhone, you know it can be frustrating to use with Siri. The digital assistant always wants to use Apple Music instead, so you need to specify that you want to play through Pandora with almost every request. That's now a thing of the past because iOS 14.5 allows you to set Pandora as your Siri's preferred music player.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.