
How To: Build a Man-in-the-Middle Tool with Scapy and Python
Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.


Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Contrary to popular belief, taking someone's mind off their sadness and telling them to "cheer up" doesn't do much good. Misery loves company, and while it may be a tiresome cliché, there's actually some science behind it.

This is evil and it destroys people. Let's just get that out of the way. Nonetheless, suppose you need to make someone distrust their own memory and perception of reality. Suppose you want someone to believe in you more than they believe in themselves.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

As most of you already know, the White House is the seat of the Executive branch of government in the United States. Constructed in 1792, it is one of the oldest buildings in the U.S. During the War of 1812, it was burned down and later rebuilt. The White House was inspired by a few foreign government buildings and is somewhat Greek in appearance.

There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking about. You're addicted to finding out what's going on with your friends and addicted to telling those friends everything you're doing. You can't stop, even when you're at work.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.
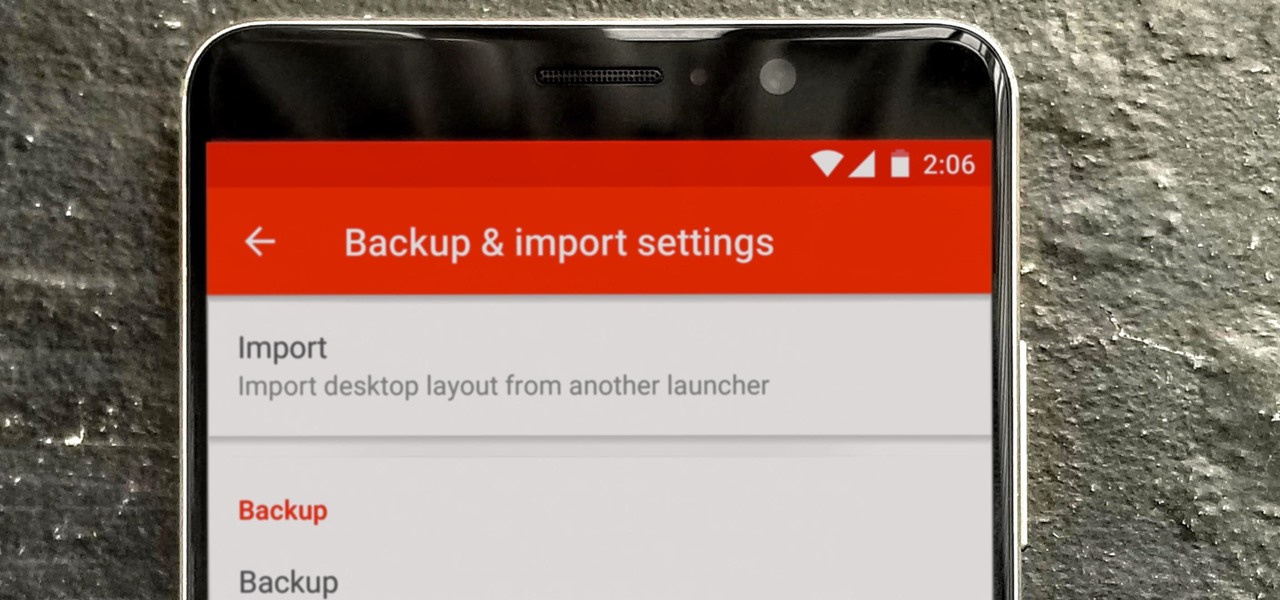
So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

The director of 100 Musicians and Nurse/Fighter/Boy talked with us about old school filmmaking Charles Officer has directed shorts, music videos for K’naan, and the features Nurse/Fighter/Boy and Mighty Jerome, a documentary about Canadian track star Harry Jerome. His new short 100 Musicians, which screens Monday as part of Short Cuts Canada, is a small ode to civic optimism, concerning itself with a lovers’ argument over who exactly misheard a radio DJ reporting the plans of Toronto’s much m...

Shorts, learning from your audience and the fundamental plausibility of being hustled in the desert Mike Clattenburg, creator of Trailer Park Boys and Afghan Luke, was kind enough to talk to us from Nova Scotia, where he was hard at work in preproduction, about Crackin’ Down Hard, his short that screens Monday and Tuesday as part of TIFF’s Short Cuts Canada Programme. We picked his brain about realism versus surrealism in comedy, the virtue of shorts, and the virtue of turning negative skinny...

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

Last week, we told you about one of the first pairs of augmented reality smartglasses to get Amazon Alexa functionality, and now we're finally getting a look at how it works.

From all the demos we've seen, we know for sure that the marketing world is going to change drastically thanks to Apple's ARKit.

With augmented reality comes an infinite realm of possibilities for storytelling. We have seen it through wineries telling their history with interactive AR experiences and through authors that use augmented reality to bring portions of their books to life. However, filmmaker Peter Jackson might take the cake on creating an incredible new way of storytelling.
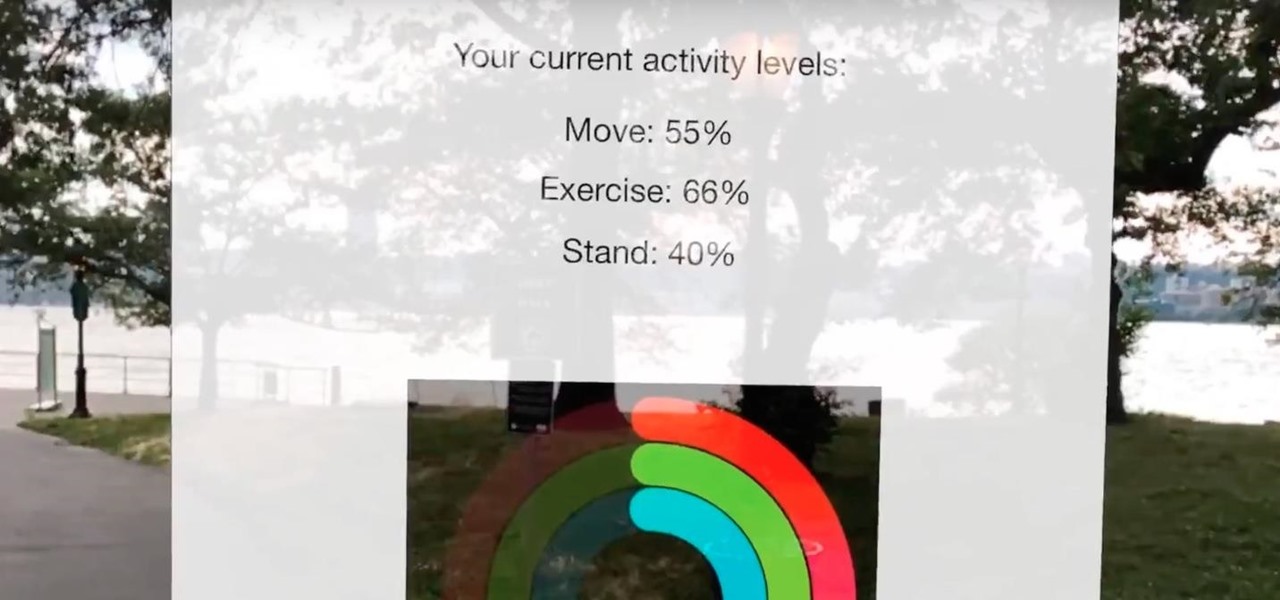
When people work out, they want to get the absolute most out of their routine. Going on a run is great exercise, but finding an optimal route that works best for you can be difficult. Luckily, Apple's ARKit has the capability to make it much easier to get the most out of your workout.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

If there's one thing I know, it's that people hate buying mobile games. I'm the same way — no matter how good a game looks, if I have to pay for it, I have to fight the urge to immediately walk away. That's why it's such a big deal when a great game goes on sale. Right now, that game is 'Reigns.'
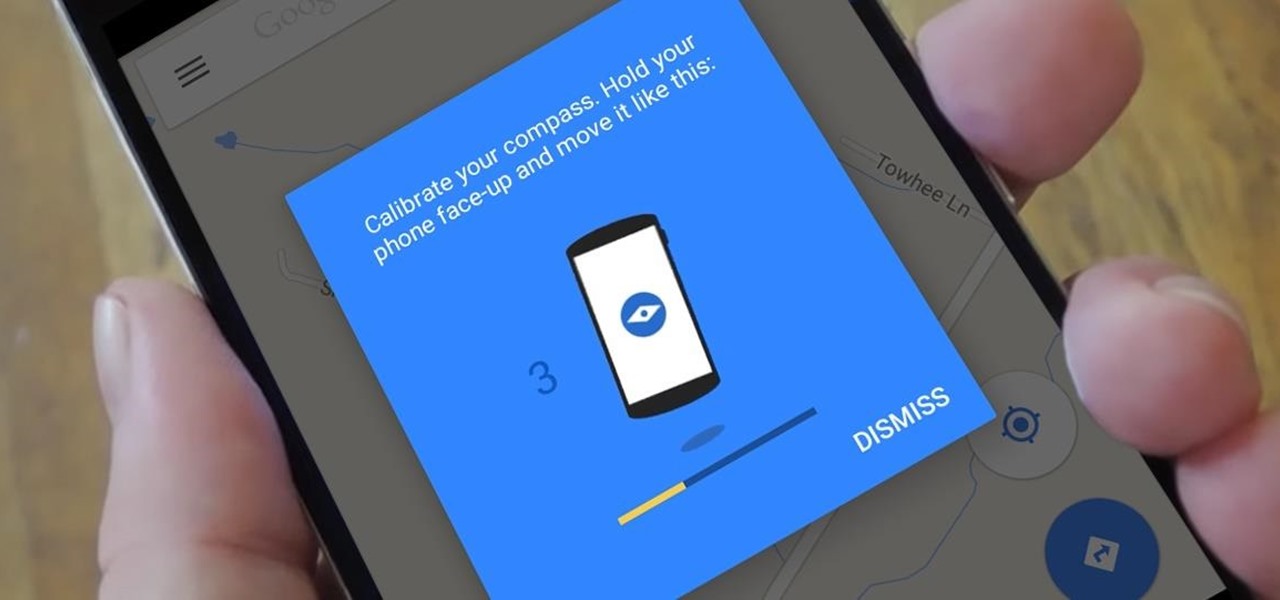
A lot of users with newer Android devices, particularly the Nexus 6P, have been complaining about issues with their device's compass. I've experienced the issue a few times myself—when you open Google Maps and try to get directions somewhere, you're prompted to calibrate your compass before you can proceed.

Navigation app Waze occasionally gives you the option to have a celebrity voice provide directions for your trip, like this famous European with a funny voice, or this decidedly less-famous European with a funny voice.

Ant-Man isn't one of the most famous Marvel superheroes. In fact, with the news of his individual movie came great doubt that the comic book legends could succeed in telling the tiny story of an oddball hero on the big screen. Yet with its humor and unique story, Ant-Man has become a hit movie in its own right—and the hero will most certainly make a hit Halloween costume.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...
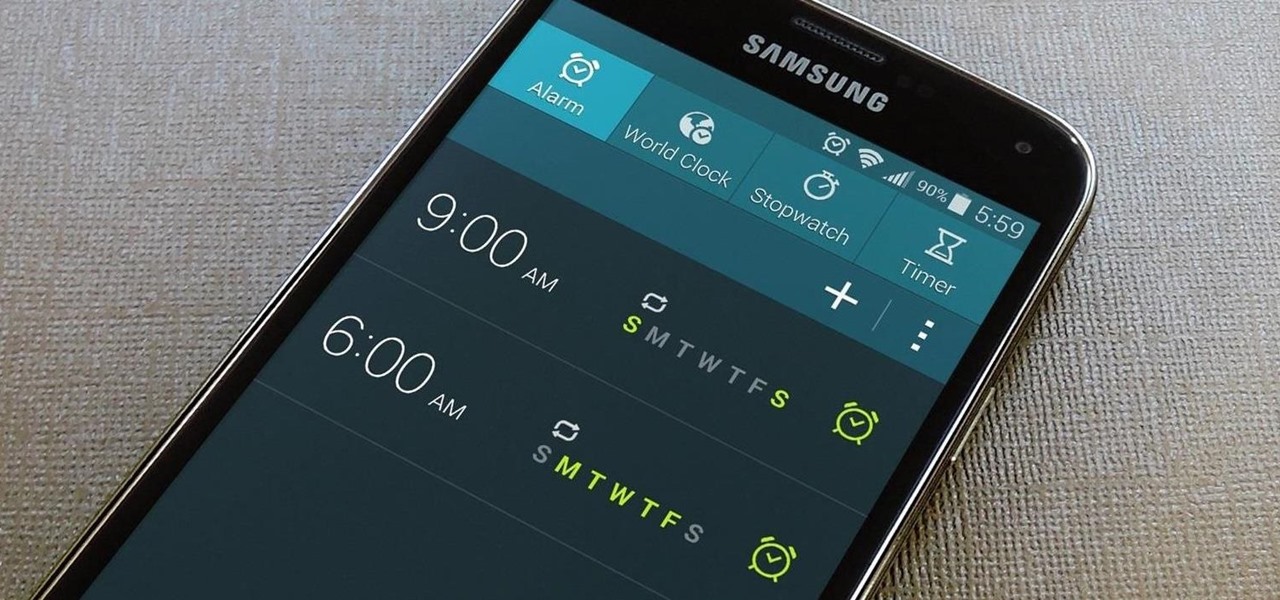
The basic clock app on Android devices is functional and has a few nice features. One of these is a "World Clock" view, which lets you see the current time in different cities across the world, and shows the time in your location at the top.
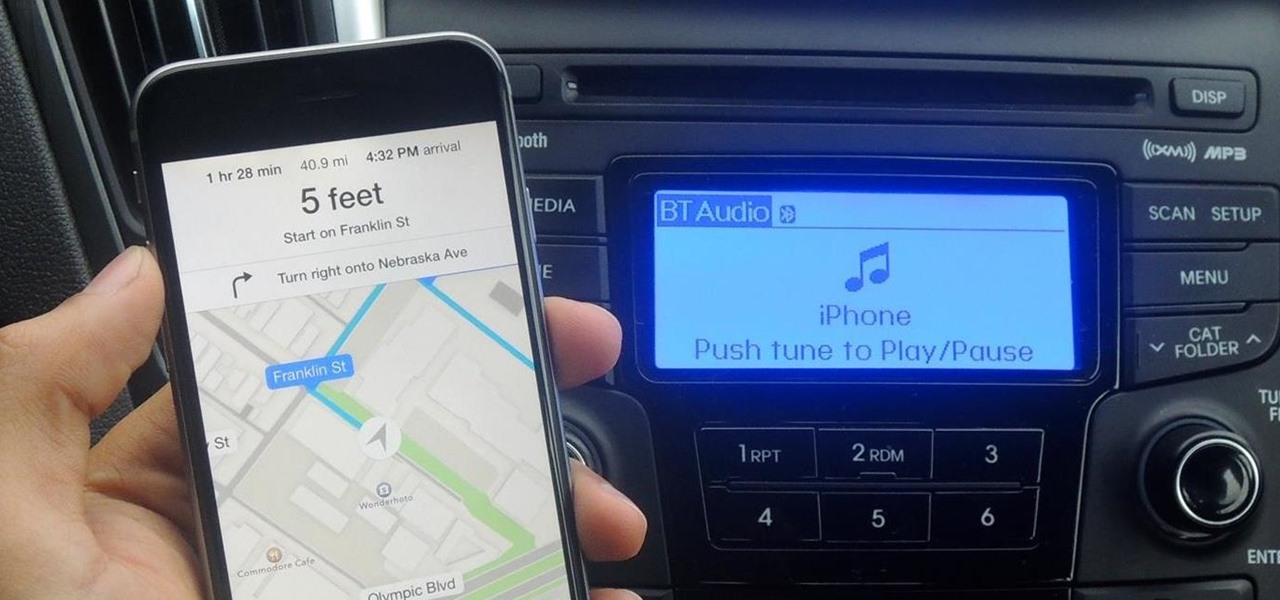
Maps is great for getting turn-by-turn directions in unfamiliar territory, but how many times does your favorite song have to be rudely interrupted by that navigation voice telling you to turn left or right? Yes, you need those spoken directions to get to where you're going, but you also need to hear every part of your song, right?
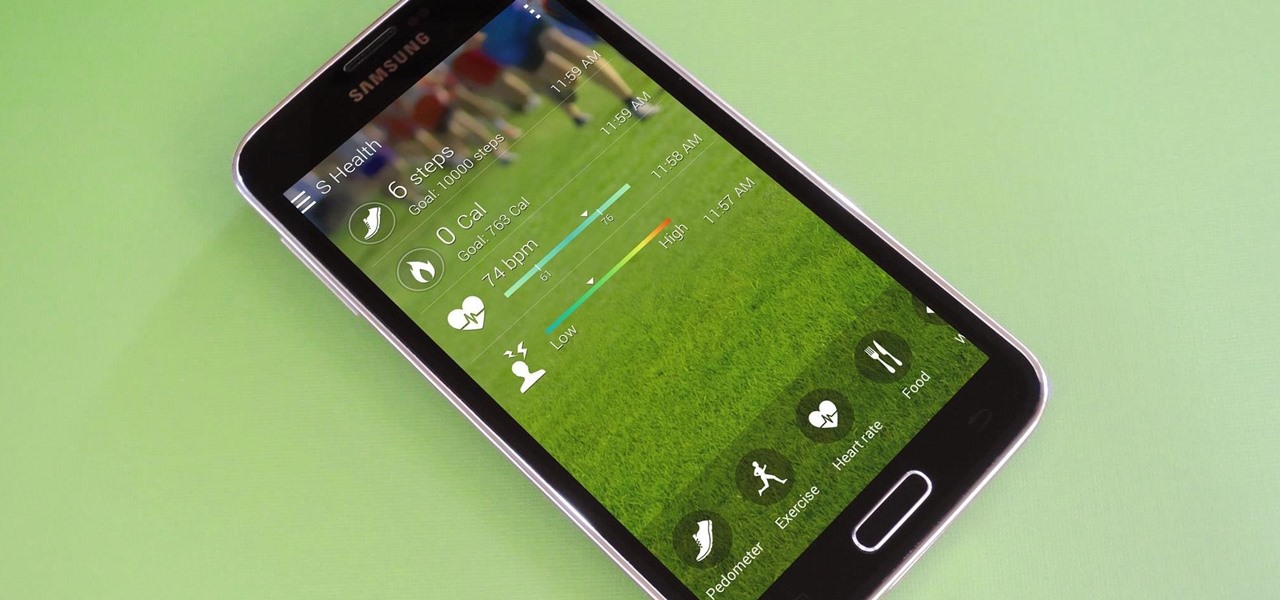
S Health is one of the biggest selling points for newer Samsung Galaxy devices. It offers a centralized place to view and manage data collected by all of the various sensors like the heart rate monitor.
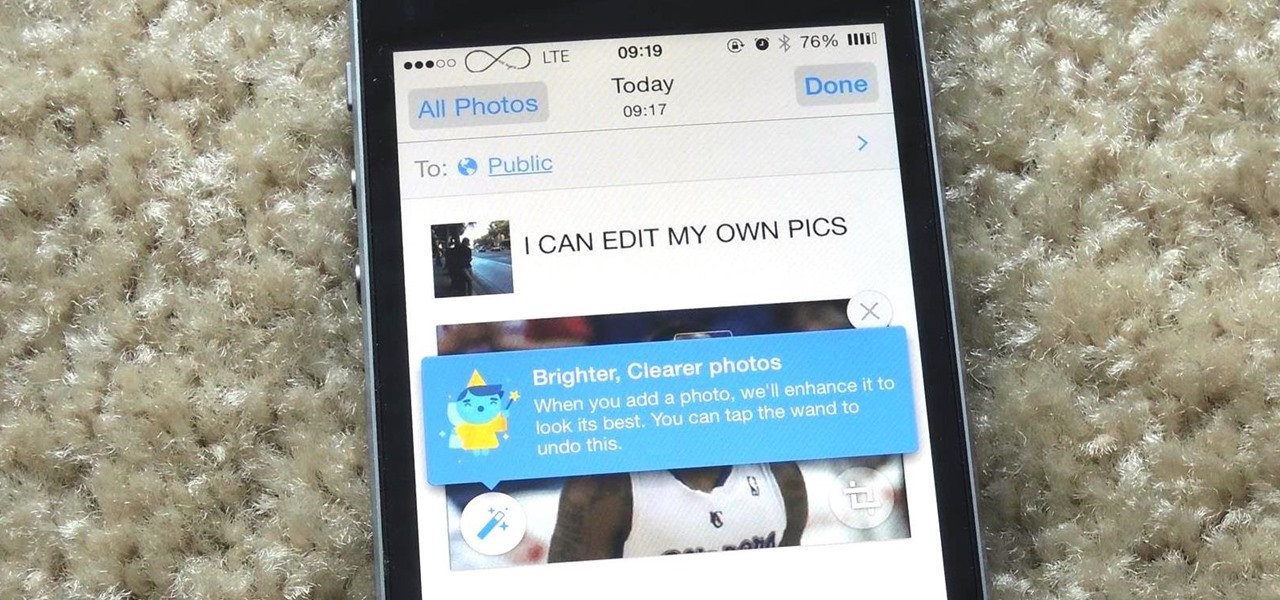
Facebook is really good at two things: connecting people all over the world and force-feeding changes to its users (ahem...Facebook Messenger).
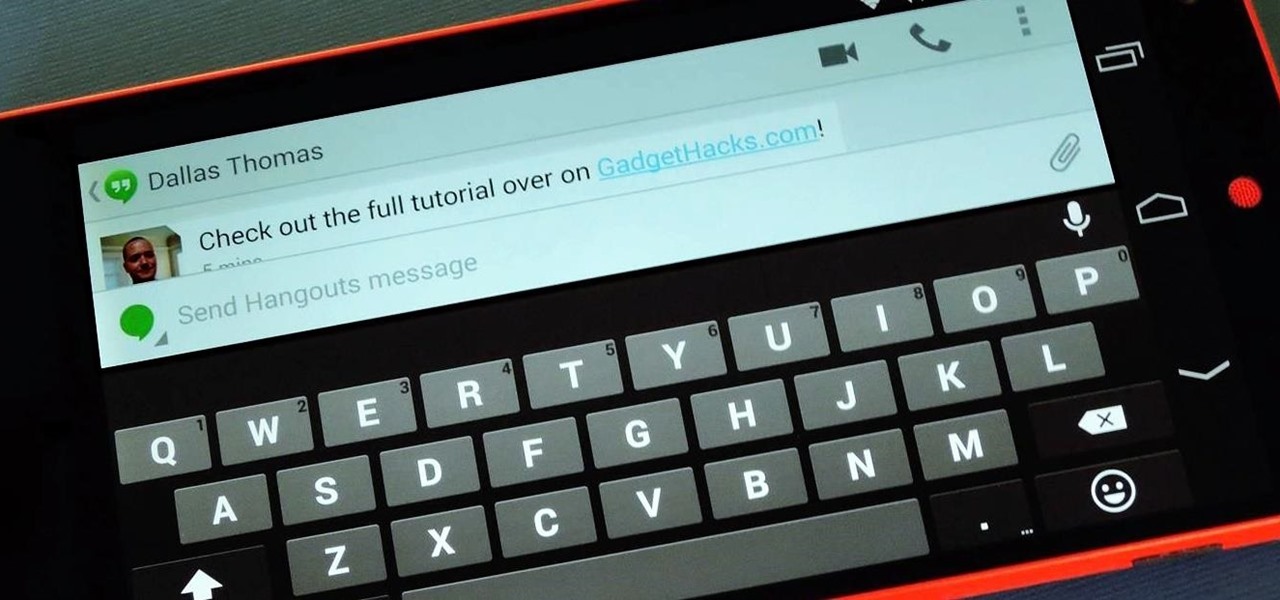
For some reason, when you're typing in landscape mode, Android extends the text input field to cover every bit of the screen that the keyboard's not occupying. This gets pretty annoying sometimes, especially with messaging apps where you might need to reference what the other person just said in order to properly form your response.

Unlike the normal cars, the racing cars are more powerful, more maneuverable and less error forgiving. That's why you always have to move them from one track to another with a tow, and not on their own. In this tutorial, I will show you how to lift a racing car on a tow.

With the Samsung Galaxy S5 all but assured to be showcased in a just a few weeks, we've got our hands on some fresh details of the upcoming flagship device.

If you want to raise your children in a Christian way, it is very significant to make them understand what Jesus' sacrifice did for them.
A new leak from GSM Israel on March 6th shows some telling screenshots of the U.S. variant of the upcoming Samsung Galaxy S4, some of which confirm features seen in the leaked 4.2.1 ROM for the Galaxy S3.

So, you've got your new iPhone 5 from Apple, but wait—where do you get a case for it? Since its launch, Apple Stores across the country have been carrying absolutely zero iPhone 5 cases. In fact, the only thing they seem to be carrying right now as far as iPhone 5 accessories goes is the new Lightning cable. So, when will they be getting cases? Rumors state October sometime, but there's no telling if it's now or at the end of the month.

Tons of iPhone 5 users with Verizon Wireless hit the message boards last week complaining about their phones sucking down massive amounts of cellular data when they were actually using a Wi-Fi connection. Of course, that means Verizon customers could have been getting charged for cellular data they weren't actually using.

What can you do with a hair dryer besides dry your hair? Lots. You can remove stickers from clothing, clean up crayon marks, and mold your plastic eyeglasses for a better fit. But how about something a little more fun? Well, you can levitate things. Ping pong balls, to be exact.
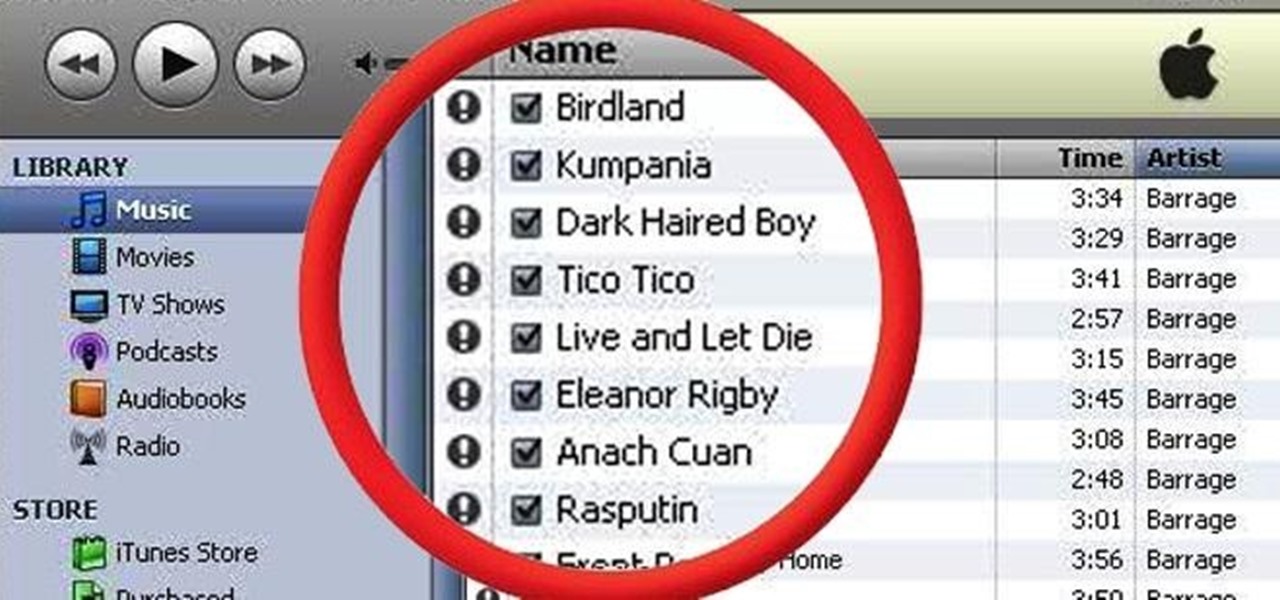
If you've ever mistakenly moved your music files around without relinking them in iTunes, you might now be noticing that you have a long list of tracks asking you to relink them. You could go through them one by one, redirect them to the new file location, then delete any copies. Or you could try to track them all down and delete the old references. But come on, who wants to spend that much time when you can clean up your library using this clever method using only Notepad on your Windows com...

Welcome to Minecraft World! Check out our tutorials, post to the Inspiration board, and come play on our free server! HELLO, FELLOW MINECRAFTERS. Pmaguire here, bringing you my favorite idea for a competition so far! I hope that you will come to love it as much as I do! Well, starting off, as the title states, this week's Redstone Competition will be PvP Arenas! Except, not just ones where you physically fight. You have to have traps, things that make it hard to fight, and various ideas using...

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.