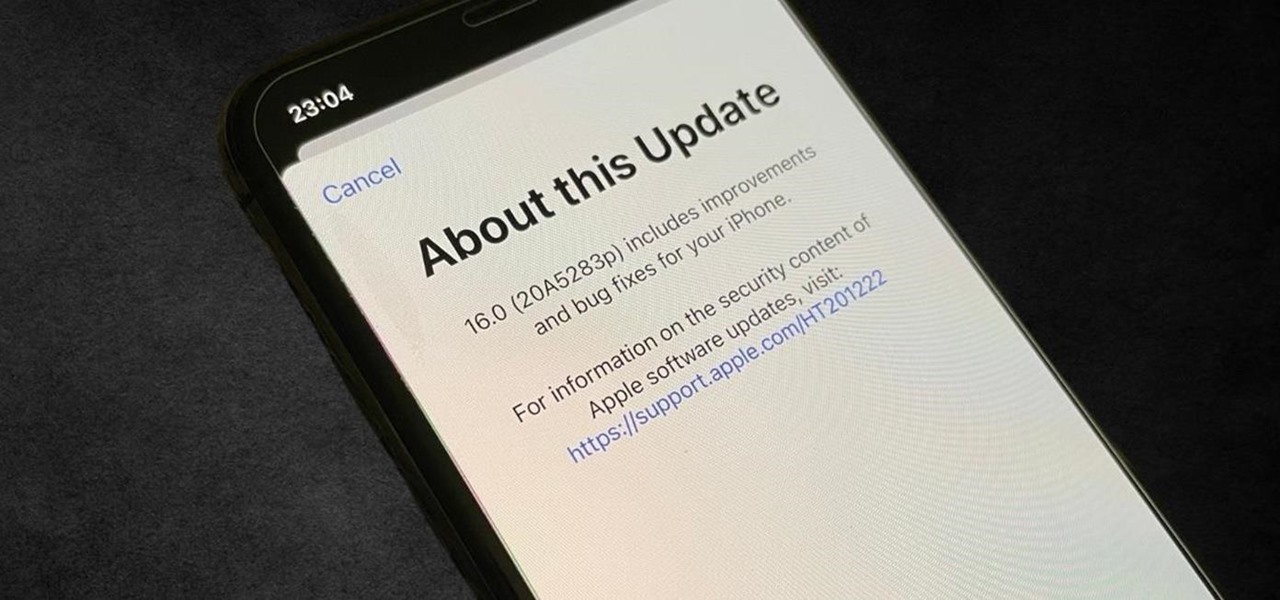
Apple just released iOS 14.1 for iPhone today, Tuesday, Oct. 20. This update first hit iPhones one week ago, but not for long — Apple pulled the release almost immediately, later seeding it to iOS developers only as a GM (golden master) release.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.
Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all over again, as Apple just released the fifth developer beta for iOS 13.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

If you're someone who frequently awakes in the middle of the night trembling in terror, you might want to consider swapping sides. According to research done at Yüzüncü Yil University, those who sleep on their left side experience more nightmares than those who sleep on their right.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

You may be tempted to install the iOS 16 developer beta on your iPhone to try all the exciting new features it has to offer, but it may be a good idea to wait if you only have your personal iPhone that you use every day.

Apple just released the second public beta for iOS 14.5 today, Wednesday, Feb 17. The update comes just one day after the company seeded developers the second 14.5 beta. Because of that, we've had 24 hours to sink our teeth in beta 2's new features, like 217 new emoji, Apple Music lyric sharing, Apple Music UI updates, and new Shortcuts options.

Apple released the second developer beta for iOS 14.5 on Tuesday, Feb. 16. The update comes 15 days after Apple seeded developers the first 14.5 beta, which included a slew of new features such as default music app support, compatibility with PS5 and Xbox Series X controllers, and more.

We've wanted them for years, and Apple has finally made widgets accessible on the home screen in iOS 14. These are not the same widgets found in past versions of iOS. They're more data-rich, more colorful, and more versatile. And best of all, both the home screen and Today View get access to them.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

Autism affects 1 in 68 children in the US, and that means it affects at least 1 in every 68 families. More boys than girls are diagnosed as being on the autism spectrum, and it's estimated that almost 60,000 12-year-olds in the US have autism. That is a 37-fold increase from the 1 in 2,500 children diagnosed just 30 years ago.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Apple's latest iPhone software update — iOS 17.5 — is finally ready for prime time. Released on May 13, it includes at least 32 new features and changes you need to know about, from a new game and offline news access to new wallpapers and anti-stalking capabilities.

When you don't feel like talking, let your iPhone do all the work. Yes, your iPhone can speak for you, and it works over phone calls and FaceTime calls. It will even work its magic over your iPhone's speaker for in-person conversations. While Apple created this feature to support people who are unable to speak and people who have lost or are losing their speech abilities, anyone can use it.

There are plenty of tools that'll help you type faster and more efficiently on your iPhone or iPad, such as Slide to Type, Dictation, and even a case with a physical keyboard. But one of the best tricks will help you type frequently used words, phrases, sentences, email addresses, and more faster, and you can sync your settings with your Mac so you can type more with less effort on all your Apple devices.

One of the most useful new features Apple included on iOS 16 lets you instantly lift the subject out of a photo, separating it from the background. Once extracted, you can paste, save, or drop the cutout wherever you want as a new image, and you can even make it a sticker in messaging apps.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

You can view and hide iCloud contact groups on your iPhone, but Apple won't let you create or delete groups or add or delete contacts from any groups unless you're on a tablet or computer. Why Apple refuses to add a group management tool to Contacts on iOS is anybody's guess, but there is a workaround you can use instead.

If you have a PlayStation 5 and an Android phone running Android 12, you can stream and play your PS5 games right from your mobile device using PS Remote Play. While simply pairing your PS5's DualSense wireless controller with your phone will give you the basic controls to play third-party games, Remote Play takes a little bit more work to set up.

Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.