We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.
The new Google Now Launcher has hotword detection and one-swipe access to Google Now, but personally, it's not enough to convert me away from other launchers like Apex or Nova. Just because it's Google's official launcher for stock Android doesn't make it better than all the rest.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Those of us who lived our childhood through the '90s remember the rapid advancement of console gaming. From the Nintendo to Game Boy to Dreamcast to PlayStation, we were consistently greeted with newer and better technology on a year to year basis.

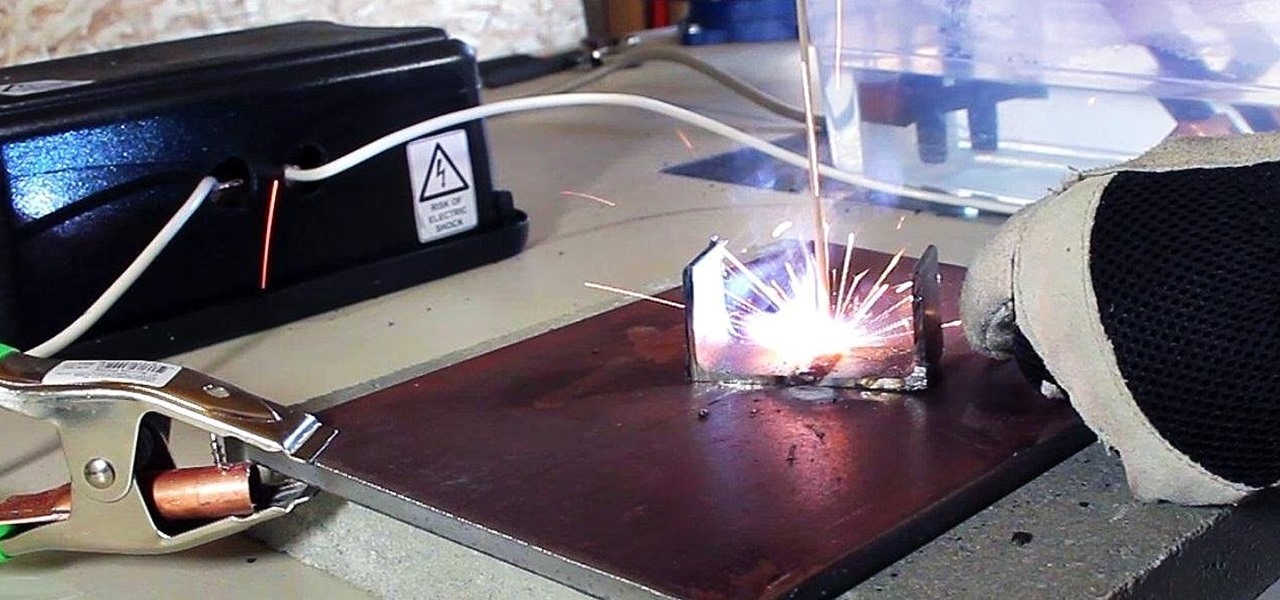
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: .

If you're an avid PC gamer, then you're probably well familiar with the term overclocking, which is basically just tweaking your computer hardware to run faster than it was originally intended.

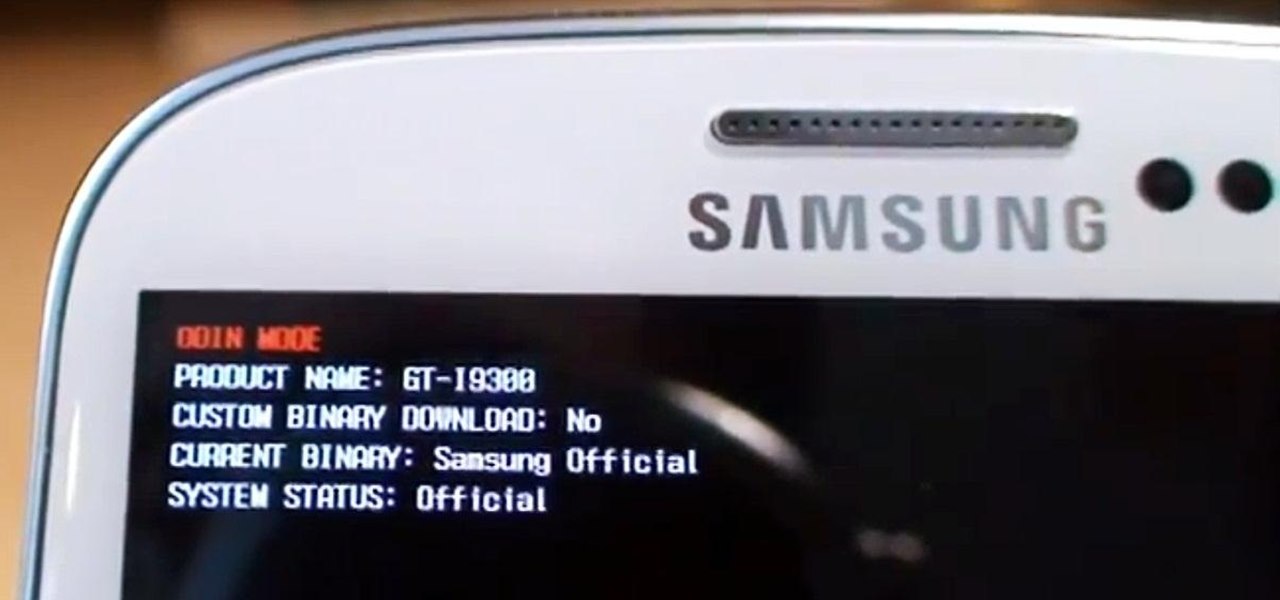
Need root on your Samsung Galaxy S3? Phone not getting the Jelly Bean update? Stuck on the Samsung screen? Phone bricked? Need to restore back to stock? Odin can help!

As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commercial industries. According to them, Steampunk has been on the rise for the last few years, and they predict that it will explode into peak popularity within the next two years. But what does that mean and how will it impac...

It might be time to move those Instagram photos to another service. It seems that Instagram has never heard of the phrase, "If it ain't broke, don't fix it." In a very big WTF moment, the extremely popular photo sharing and editing app decided that it has the right to sell its users photos to third parties without pay or notice. Yep, you heard that right. That photo you took of your girlfriend laying out on the beach could be in the next stupid Corona commercial without your consent and witho...

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

In this video tutorial, Jessica teaches us how to make pork chile verde. The ingredients you will need are: 10 tomatillos, 5 garlic cloves, 2 jalapenos, 1 cilantro bunch, 1 pinch of oregano, 4 lbs of pork shoulder, olive oil, 1 yellow onion, 1- 1/2 cup chicken broth. First, remove the husks from the tomatillos and rinse, then cut them in half and place then on a baking sheet along with 3 garlic cloves. Next, broil in the over for 5-7 minutes and let them cool off. Now, cut your jalapenos and ...

Thermal cooking saves energy costs and preparation time, so why not try out this delicious recipe using a thermal cooker? You'll learn how to make a fruit cake inside a thermal portable cooker, which could get you addicted. Give it a try, see if you're a thermal cooker.

The egg is an incredible compact, nutrition, protein and fat all in one prepackaged unit. This video will show you how to boil an egg using a strainer basket in your boiling water to heat steam your eggs as an alternative to regular boiling.

Every few months I get together with a friend and we have a ‘masala making session’! We spilt the cost of the materials, the work load and then, split the masala. It takes a few hours but once it’s done, cooking is just so easy and so fast. All you have to do is add in the veggies or the meats and cook. Watch this how to video to learn how to make large quantities of masala sauce for all your Indian recipes.

This series starts by introducing you to the song itself and its parts. Then it will branch off explain each note, step by step and show you how to play every facet of the song. The bridge is a bit tricky but our expert will breeze you through it like a hot knife through butter. So pick up your axe and turn on your PC! It's time to jam!

Are you looking to mix up your guitar playing style? This is the video series for you. Our expert knows the ropes, has played in some top bands, and is ready to sit down and show you some inside information on how to play country guitar. Watch as our expert shows you what he knows about the trade. Learn the different rhythms and picking styles that will have you sounding like a country superstar. Also check out the many different guitar licks that will give you that authentic country and west...

This heart healthy meal is a great treat for those hot summer nights when you don't want to cook. Watch as Chef Jane Murphy shows you how to prepare spicy cold soba noodles, a great Japanese dish.

So take a few moments and watch this instructional video series designed to help teach the basics of Hip Hop dance for beginners—or those of you who are already dancing fiends but perhaps unfamiliar with the variety of styles and moves under the umbrella term “Hip Hop.”

Vampires and bad dreams aren't the only enemies of the unwary sleeper. Teeth grinding while asleep is an annoying and possibly painful problem afflicting may people. There are a variety of reasons you may grind your teeth but, luckily, there are also a number of solutions to this nocturnal problem.

In this series of car restoration videos, our body shop owner and hot rod designer shows you how to restore the exterior of that old classic car back into like-new condition. He demonstrates ways to expose rust, grind it away and then repair the body section which rusted.

In this series of car restoration videos, our body shop owner and hot rod designer shows you how to restore the exterior of that old classic car back into like-new condition.

In this Cajun cooking class on video, learn how to make boudin sausage. Our expert chef and caterer, Karl James, will walk you through the process step-by-step, including what ingredients and equipment you will need. Although this is a complicated recipe that takes some practice to perfect, Karl makes it easy as he shows you how to chop and cook vegetables, season and prepare the meat, how to cook rice, how to assemble your meat grinder and sausage stuffer, how to soak the casings and fit the...

Whoa! Talk about an artery clogger! As if this super huge hot dog wasn't enough to induce a full-fledged heart attack, the deep fried bacon screams "heart failure" to the nth degree. If you're daring enough to eat this XL bacon-wrapped hot dog (and even more daring to serve it), then this video recipe will show you all the gory details.

Salsa dancing, like salsa the food, is spicy hot and full of Latin American sizzle. During salsa dancing, there is a double-handed move called the in-n-out in which the girl gets spun out to her left and gets resisted by the guy on her right shoulder so she doesn't spin out too far.

The hot dog is an American snack now popular the world over. This easy hot dog recipe will show you how to make this traditional summer treat! Make Chicago hot dogs.

In this tutorial, Jackie Silver shows us how to create a hot compress for acne. Acne can affect everyone, no matter what age they are. Using a hot compress can help treat the irritation of the pimple and speed the healing process. To make a hot compress, soak a soft wash cloth in hot water, making sure not to burn yourself. Place this on your face until it cools off, for 10 minute periods. Do not squeeze the blemishes with your fingers, this can cause damage to your skin. To close your pores ...

Julia Child and her guest demonstrate how to make a dirty steak with hot fanny sauce. 'Dirty Steak,' a three pound rib-eye roast cooked directly upon hot coals, is both unique and delicious. Make dirty steak with hot fanny sauce.

Julieg713 is a nail art expert. Check out her nail art tutorials on WonderHowTo (Search Julieg713). Her nail art looks are fun & pretty, not to mention well demonstrated. This nail polish video demonstrate how to create a red hot lips nail polish design. Watch this video to learn how to recreate this nail art look.

Sometimes easy is the answer, as you'll see in this video on how I finally made a hot knife for cutting plastic. Make a hot knife for cutting plastic.