Advanced crip walking takes lots of control and practice. This shows you moves like 'The V', 'quick step' and 'shuffle spin'. He breaks down this form of hip hop that is popular on the street. It involves a lot of feet shuffling and is often accompanied by rap or hiphop music.

Here are 6 king tutting movez. King tut is a popping dance move. Popping is a combination of funk and street dancing. Follow along with this visual demonstration to learn how to king tut. This king tutting tutorial is for beginners.

This an advanced king tutting tutorial, not for beginners. Hint: keep practicing the direction of your wrists and hands. The last song is from Slick Dogg - Follow Me Through The Battle. Follow along as you practice the king tut poppin dance move. Popping is a combination of funk and street dance.

Breakdance, or breaking is a street dance style that evolved as part of the hip hop movement in Manhattan and the South Bronx of New York City during the early 1970s. In this breakdancing tutorial, you will learn how to do the "swipe" move. You have to practice these a lot in order to get good at this move. Watch this how to video and you will be breaking the swipe in no time.

Breakdance, or breaking is a street dance style that evolved as part of the hip hop movement in Manhattan and the South Bronx of New York City during the early 1970s. In this breakdancing tutorial, you will learn how to do the "Kip-up" move. This move takes a lot of upper arm strength, so you have to practice these a lot. Watch this how to video and you will be breaking a "kip-up" in no time.

Learn how to ride a motorcycle safely. The bike in the video is a 2008 Triumph Street Triple.

How to say, "Excuse me!" when you are trying to move through a crowded street in Beijing.

A classic dessert at any Churrascaria, Cream of Papaya is not only delicious but also aids digestion as Papaya contains enzymes which soften and break down red meat. Cucaâ??s Tip: Supermarkets are the worse place to buy ripe fruit. Try your local street market or Indian grocery.

This video shows you how to do the match back trick with wooden matches. The Street Magician shows you how to do this trick.

Flooding occurs in a low water area and often appears to be safe. Motorists who drive through flooded areas risk losing control of their cars. People have extreme confidence in the size and weight of their vehicles. Flooding kills more people than any other natural disasters. Don't drive quickly through flooded streets because it increases the chance you will hydroplane and lose control of your car.

In this tutorial, we learn how to draw a neighborhood using an imaginary box. First, draw a straight line and then the boxes should go around it. Continue to draw additional boxes around the line, then fill them in with the outline and further details. Draw in the roof, walls, windows, and doors. When you finish with the details, start to shade them in and then add in the street details. Make sure to give the ground some rough edges and also add in lights on the street. Add as many details as...

Miandza teaches us how to sketch a street. You start with a horizontal line and two diagonal lines, all intersecting in the middle. You then start to add parts of buildings, in perspective. You continue to use the lines as reference and add more buildings. Then start doing trees and people. Also add pavements and start doing details on all objects. You finish by drawing the sky and the birds. The final scene is still a sketch, but has lots of details and uses the perspective to look natural.

Miandza teaches you how to sketch a busy street. You start by drawing a horizontal line and add 2 diagonal lines, for all 3 lines to meet in the middle. Using those diagonal lines, draw vertical lines, at the same distance from each other. These will act as buildings. Also start creating the road in the middle. Add details to the buildings like doors, windows or pieces of decoration. Create trees and two large towers in the far end. The road will have a truck and the pavement should be filled...

Scott Brown teaches us how to make a wind turbine using a ceiling fan in this video. First, place steel banding around the middle of the ceiling fan base. Now, cross all the combinations of the wires and keep them close together so you don't confuse them. Hook these up to DC terminals so you get around 50 volts on both of them. Hook them parallel so you keep the voltage down to around 50 volts together. Then place the wires into a connector that has a pipe connected to the bottom. This will c...

This video shows us the method to make a universal motion alarm to protect your home. You will need a reed switch with an alternating contact, a 9V battery with a battery clip, a switch, a buzzer, a small plastic box and a magnet. When a magnet is brought near the reed switch, it switches to the other contact and the switch is open. If the magnet is removed, the switch is closed and the buzzer starts ringing. Make the circuit with correct polarity for battery and the buzzer. Make a hole in th...

Watch this science video tutorial from Nurd Rage on how to make silver different colors by electrochemical anodizing. Without using paint, you can give a silver surface various colors by anodizing it.

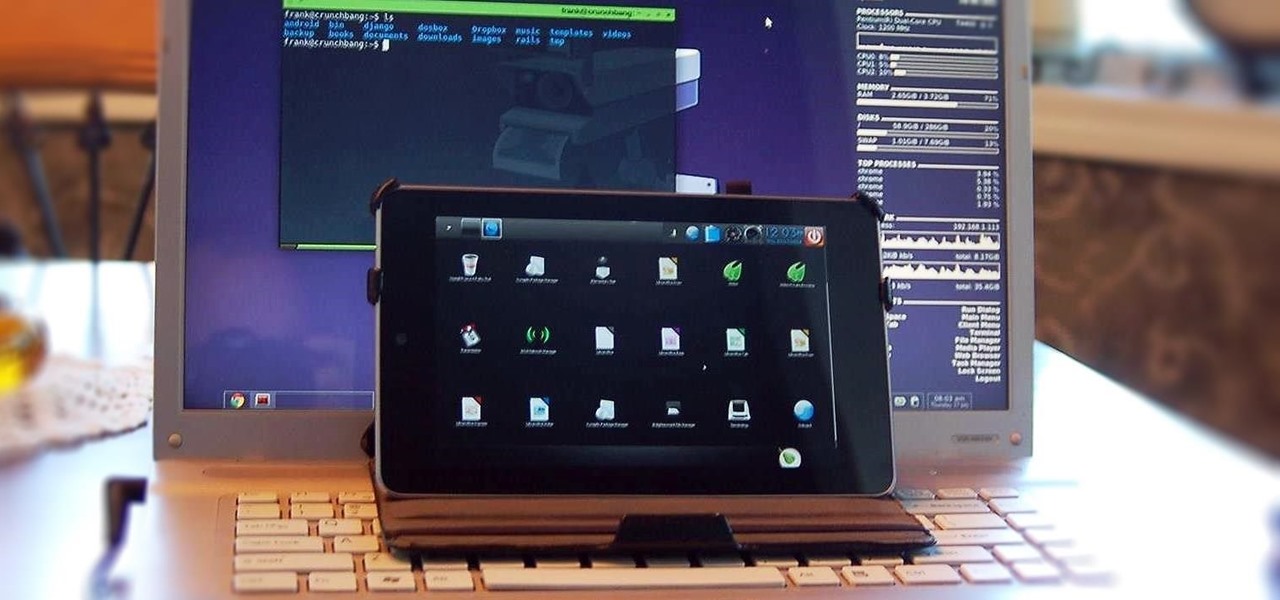
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

There's no doubt you've heard the old saying, "When life gives you lemons, make lemonade." The phrase was penned in an obituary to a dwarf actor in 1915 by an anarchist named Elbert Hubbard, who lost his life five months later aboard the RMS Lusitania when it was torpedoed by a German submarine.

Greetings my fellow hackers.

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

There are many ways to take a screenshot in macOS (previously Mac OS X), but all of the well-known options give you a drop shadow in the picture when snapping application windows.

When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.