Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.
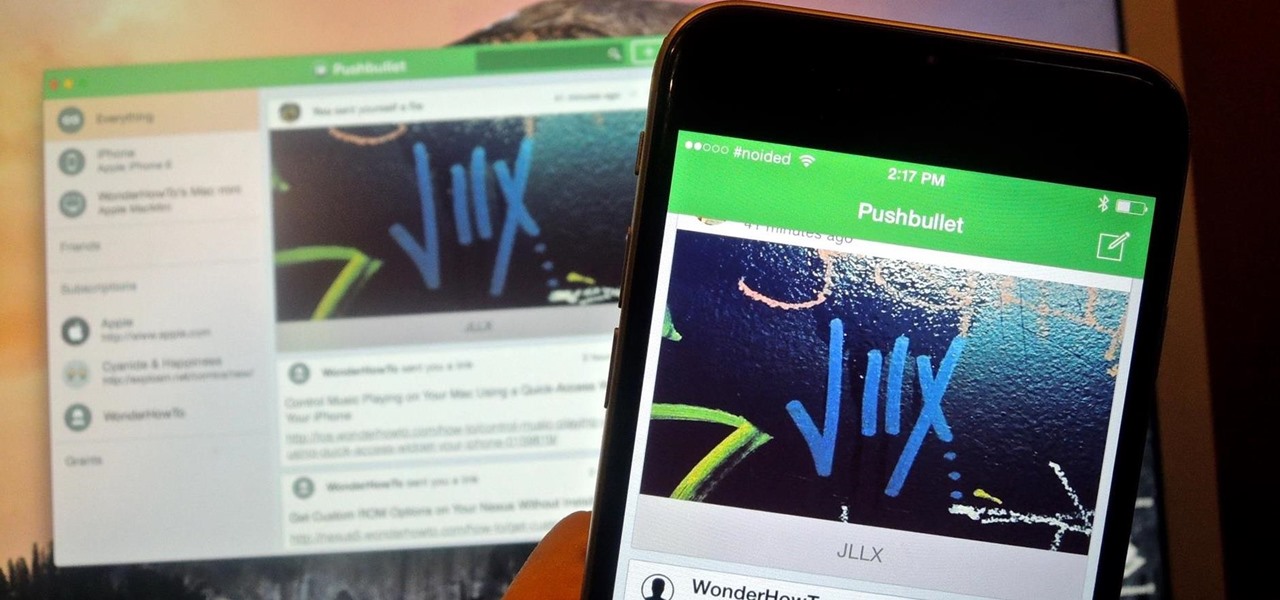
With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other.
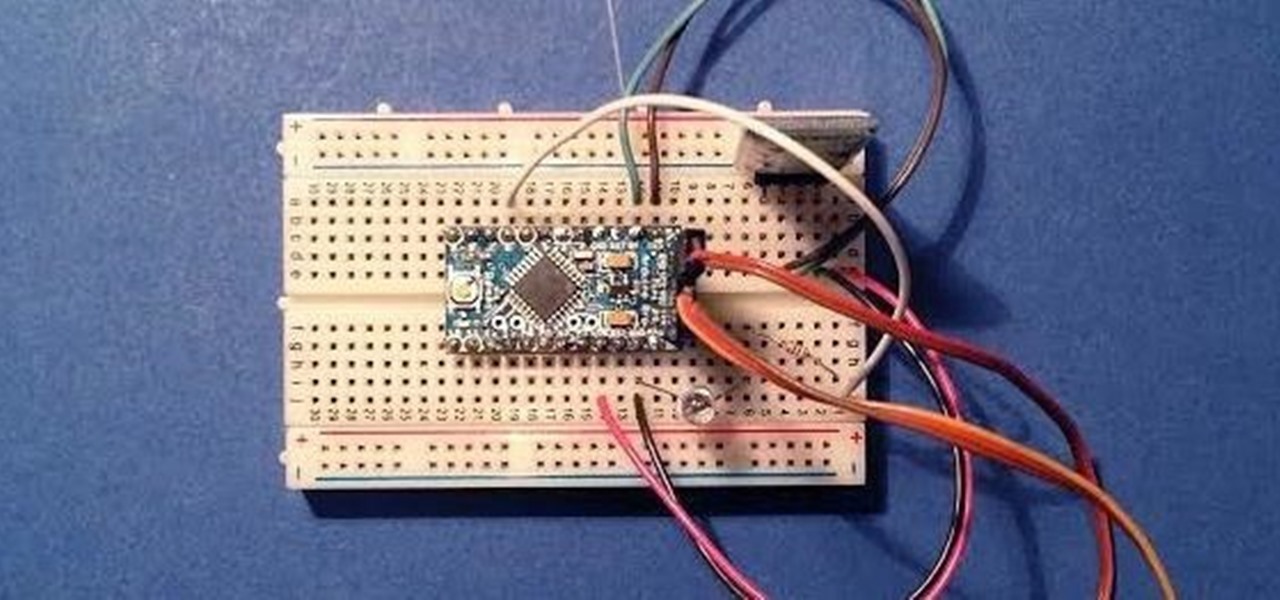
Since its creation, Arduino has been growing exponentially more popular as DIY enthusiasts and Makers alike realize its potential. As new versions of the device are released, many easy-to-use peripherals are showing up on the market also.

There really isn't any custom manufacturer skin, like Sense, that can match the clean look and fluidity that comes with stock Android. HTC knows this, and they, just like Samsung, include a Google Play Edition version in their flagship lineup.

HTC thought it best to cover their own ass by placing a red warning whenever you start your device if you've unlocked your bootloader. While it may help them identify a tampered phone, it does not help you in any way. Luckily, XDA member santod040 created a modified HBOOT that removes the "This build is for development purposes only..." text for you. While this will modify HBOOT, it will not change your unlocked or S-Off status.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

I want my Halloween costume to take as little effort as possible and be cheap—extremely cheap. That means I don't want to pay 50 bucks for some costume online or spend all day playing with liquid latex, and I most definitely do not want to visit a super crowded costume store in Hollywood.

You've gotten used to your brand spankin' new Nexus 7 and finally have a feel for Android, but now you want more features. Well, user Juan Mercator was in that predicament, and asked how to install the ever popular CyanogenMod ROM on his Nexus 7 over on our Nexus 7 SoftModder forum.

Zombies. That's the first thing that comes to mind when I see footage of a once heavily populated area turned completely desolate. Either that or you stumbled across a Ke$ha concert...BURN.

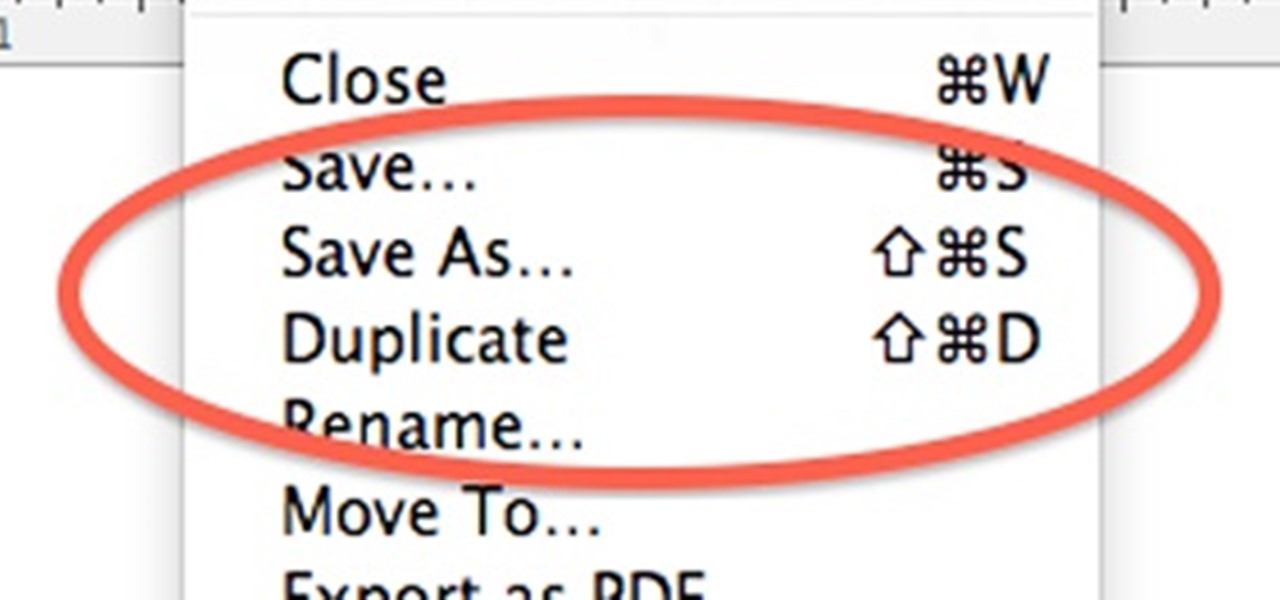
When OS X Lion (10.7) debuted last year, a lot of Apple users were dismayed that the "Save As" option had disappeared, replaced by the "Duplicate" function. Most felt that it just wasn't the same, so when Mountain Lion was released, the "Save As" option was brought back… sort of.

The guitar is a double-edged sword. I've played all my life, and though I love the act of guitar playing, there are quite a few people I could live with never hearing play again—ever.

This video tutorial from izbyfl shows how install Google Chrome and enable its plugins in Ubuntu. First download application from here: http://www.google.com/chrome/intl/en/eula_dev.html?dl=unstable_i386_deb.

Now that you've got your Nikon SB-900 professional-grade speedlight, make sure that you get the most out of it with this free photographer's guide, which will walk you through the flash unit's basic features and functionalities.

Cityslipper shows you how he uses the cleft grafting method to make a less appealing green apple tree produce better tasting red apples. 10-12 inches long scion wood is collected from the good apple tree while it is dormant. Care is taken not to let the twigs dry out. Selected scions should not have spurs rather they should have leaf buds that lay flat against the twig. A good host twig on a healthy-looking branch should be selected. A clean cut should be made with the fine teeth of a grafing...

Ever hear of SmillaEnlarger? It's a small graphical tool (based on QT) to resize, especially magnify bitmaps in high quality. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

This video tutorial demonstrates an easy way to activate MMS on iPhone 3G or 3Gs Firmware 3.1 o. First download the File here.

So, your children have the same old boring Fisher-Price Power Wheels that all the other kids on the block have. Do you really want your child to be like all of the rest? No, I didn't think so. Turn those miniature Power Wheels, Dumar or Peg Perego vehicles into a little bit of realism, if you can handle it. All it takes is a little modification and you'll be wishing you were five again. With a few simple hacks, your son and daughter will be burning rubber, jumping curbs and burying those othe...

So, your children have the same old boring Fisher-Price Power Wheels that all the other kids on the block have. Do you really want your child to be like all of the rest? No, I didn't think so. Turn those miniature Power Wheels, Dumar or Peg Perego vehicles into a little bit of realism, if you can handle it. All it takes is a little modification and you'll be wishing you were five again. With a few simple hacks, your son and daughter will be burning rubber, jumping curbs and burying those othe...

Need a few cool moves to show off the next time you're trying to impress the ladies at a club? Then check out this helpful video to learn a sequence of tutting moves (a type of street dance that emphasizes right angles) and popping.

Normal leopard print nails can be a little too jarring for those who enjoy the print but prefer it in a more wearable, less hooker-like shade.

This video drawing tutorial shows a technique for sketching out people in a style reminiscent of graffiti. This video lesson will provide inspiration from street art into your own artwork. Follow along with the demonstrator, experiment with the new ideas, and learn how to draw graffiti style people in a way you like.

This tutorial video will teach you how to identify various types of Chinese treats that you can find on the street. It covers silk worms, starfish, snails, scorpions, and various other foods! Bon appetit!

During a Laneway Revitalization project some gang graffiti was encountered and replaced with vibrant art work. The event organizer is a Toronto Police Officer who volunteers for the not for profit organization-The Ontario Gang Investigators Association. In this video an explanation of gang graffiti is offered. The organization Notogangs.org is comprised of sworn members of all areas of law enforcement who network regularly in the mandate of the prevention, intervention and suppression of crim...

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock firmware that came with the device.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

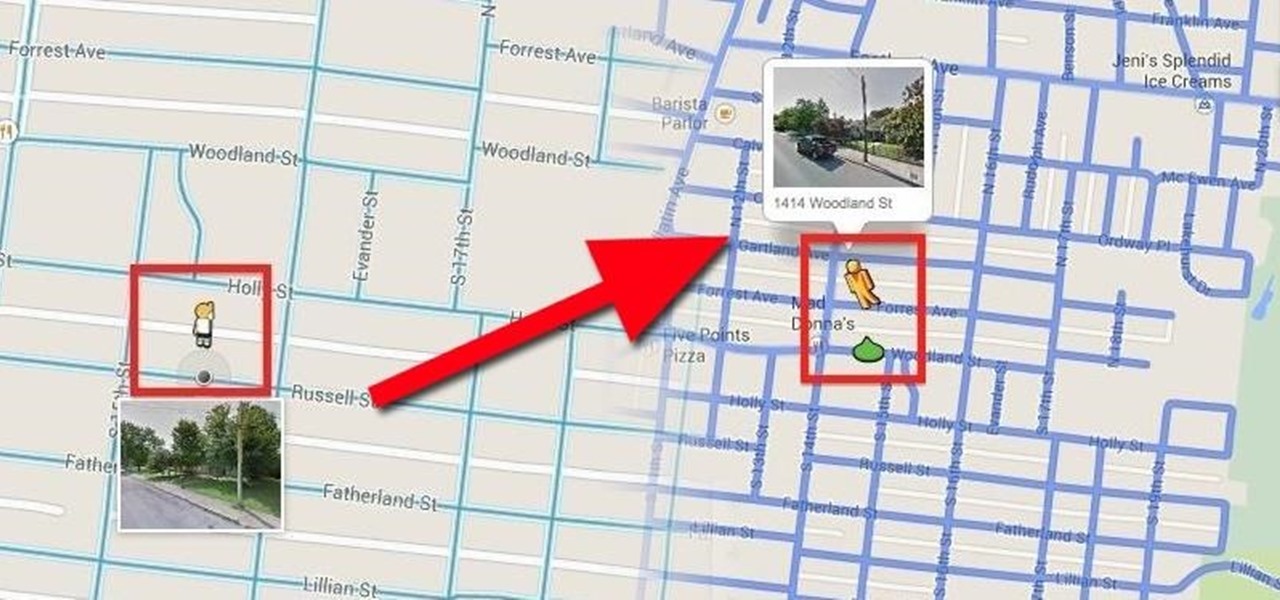
When the Google Maps web app got a massive redesign earlier this year, I was pretty excited to try it out, but it was a fairly disappointing update for me. The slower load times, confusing street view, and bicyclist neglect are just a few of the reasons I don't enjoy it over the old classic Google Maps. The brand new drag-and-drop measuring tool released this week is actually pretty useful, but not enough to change my mind.

Video: . This video gives you a glimpse on what Parisians like to do and go during their free time.

In this tutorial, we will teach you how to defend yourself against an attacker with a knife. It's the best MMA for self-defense, especially for teenagers.

This simple how to will show you the steps to transform your face from a lovable person on the street to a spooky, scary or downright creepy wolf. Awhoooo werewolf in London! How about a werewolf, or just your regular wolf, right in your own backyard? You'll want a white base makeup, some blacks, grays, and eye liner. You can choose to add teeth if you want to get extra scary. So check it out and get wolfy!! Woof woof!

Awhoooo werewolf in London! How about a werewolf, or just your regular wolf, right in your own backyard? This simple how to will show you the steps to transform your face from a lovable person on the street to a spooky, scary or downright creepy wolf. You'll want a white base makeup, some blacks, grays, and eye liner. You can choose to add teeth if you want to get extra scary. So check it out and get wolfy!! Woof woof!