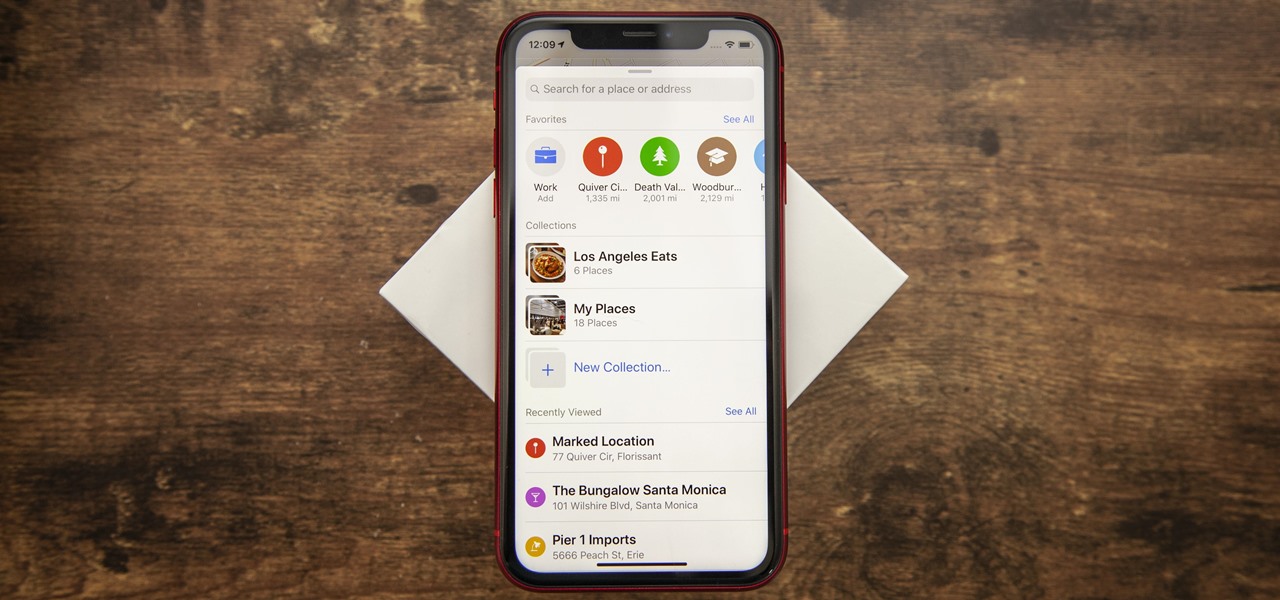
It's no secret that most people who got an iPhone 5 (or upgraded their old iPhone to iOS 6) have been sorely disappointed with Apple Maps. We may all miss Google Maps, but the Google says they aren't even working on an app for iOS 6 yet. Even worse, Google exec Eric Schmidt says they're waiting on an invitation from Apple, and if we know Apple, that could be a while. Users who didn't get an iPhone 5 have had an even worse time of things—Apple disabled 3D maps and turn-by-turn directions on ol...

In this motorcycle repair video series, learn from motorcycle mechanic Mario Rossi how to change the sprocket and chain on a street bike.

This video is a tutorial for Windows computer users in order to write very simple java programs very quickly. The first thing that you do is open a brand new text edit window. Then you should write in html code your java program, by using html you will need to include all of your brackets and all of your commands. Do so in this text edit window. Then you should save your file somewhere that you will be able to find it. Save it as test java.java you need to write your file name with .java at t...

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Already among the first game makers to add augmented reality content to an existing game upon the launch of ARKit, Zynga is breaking new ground with mobile AR once again.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Although Niantic is already an augmented reality startup unicorn thanks to the success of Pokémon GO, the company has reportedly captured yet another round of funding.

Two companies armed with web-based augmented reality tools, Vertebrae and Shopify, are ready to help online retailers boost their sales.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

The Asphalt series has been a staple in the racing genre since its first incarnation all the way back in 2004 — I still remember buying it for my newly-obtained Nintendo DS. It warms my heart to see that, after all this time, Gameloft continues to produce mobile Asphalt games, releasing the latest for Android today. Unfortunately, that's about all Gameloft has taken from its previous efforts. To be frank, this game ain't good.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

It’s late at night and your remote control runs out of batteries. When you go to replace them you realize you only have one batter left. Now you’ll have the quick fix knowledge to power your remote with just one battery until you can find another.

For pre-schoolers this is a lesson tune about crossing the street. It teaches children to be safe when crossing a street by holding an adults hand and looking both ways. Preschool video lesson tunes are short songs or chants with an educational message done to a familiar tune.

When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piece of identifying information. While not obvious, you can delete or even change this attribute.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Congradulations, you've reached the point in Dragon Age 2 where you can start your first sidequest! Simply look on Gamlen's desk for the 'Bait and Switch' letter to start it. Thisvideo series will give you a full walkthrough of this important early quest that may even net you a new companion...

If you're looking to make some unique footwear from paper mache, this video will teach you how. The term for these shoes is hooves, and they will definitely turn heads as you wear them down the street.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use GPS maps and the compass on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

This is a gameplay video of all the Ultra Combos for each fighter in the highly anticipated video game Street Fighter IV for the Xbox 360.

Learn how to make this tasty dish by watching a street vendor. While the video doesn't mention any specific amounts, you can experiment until you get the recipe just right. Yummy!

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.