You want whales? Ok, you'll get whales! That seems to be the unspoken message from Magic Leap via its latest update in the form of several new experiments posted inside its Helio app.

As we predicted earlier this week, the focus has already begun to move from Magic Leap back onto Apple's rumored augmented reality smartglasses. The latest credible whispers come from none other than longtime Apple-focused analyst Ming-Chi Kuo.
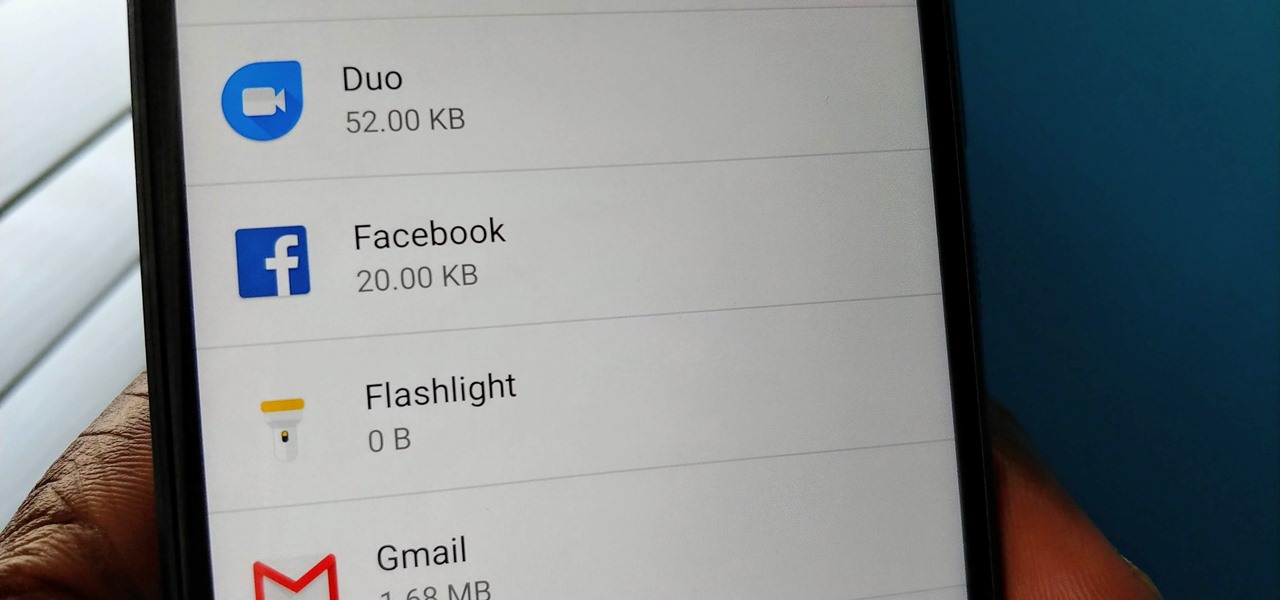
Despite years of user complaints, OEMs are still preinstalling third-party apps on brand new devices. Even in 2019, you'll still find plenty of phones with Facebook preinstalled. What's worse, it's installed as a system app, so it can't normally be uninstalled without root access. However, there are a few workarounds.
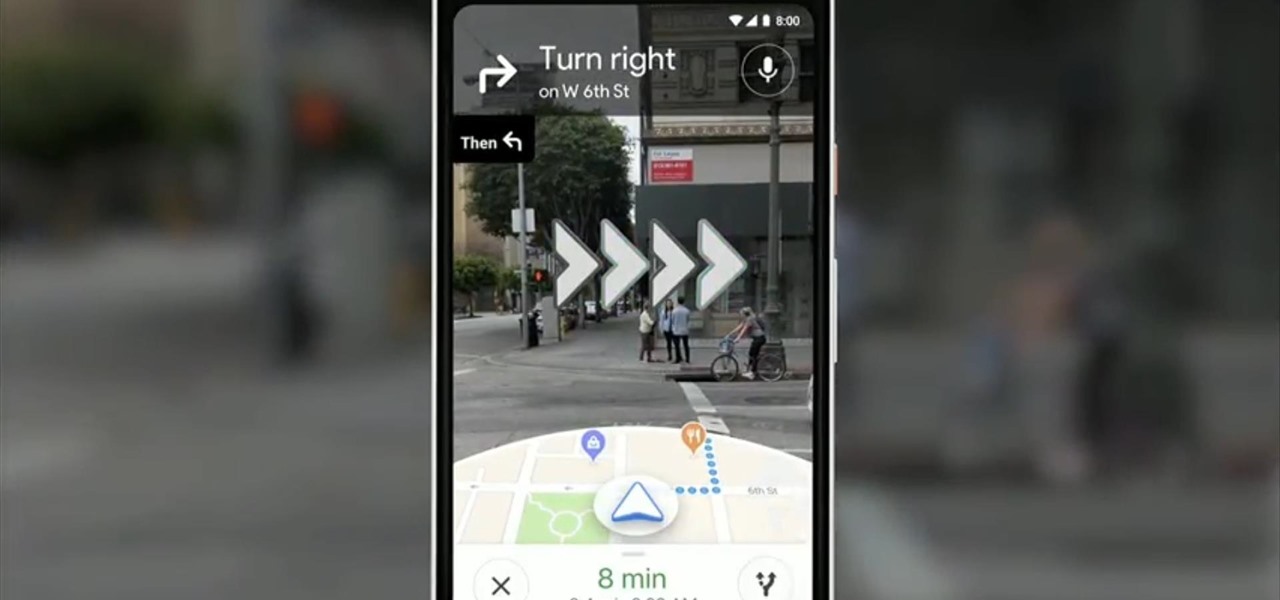
At Google's I/O developer conference keynote on Tuesday, ARCore may have been absent, but Google did preview a potentially trailblazing augmented reality feature for Google Maps.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Sketchfab, one of the leading 3D model aggregators, continues to defend its turf from encroachment by Google. This time, the company has deployed a new API that gives developers even easier access to Sketchfab's extensive library.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

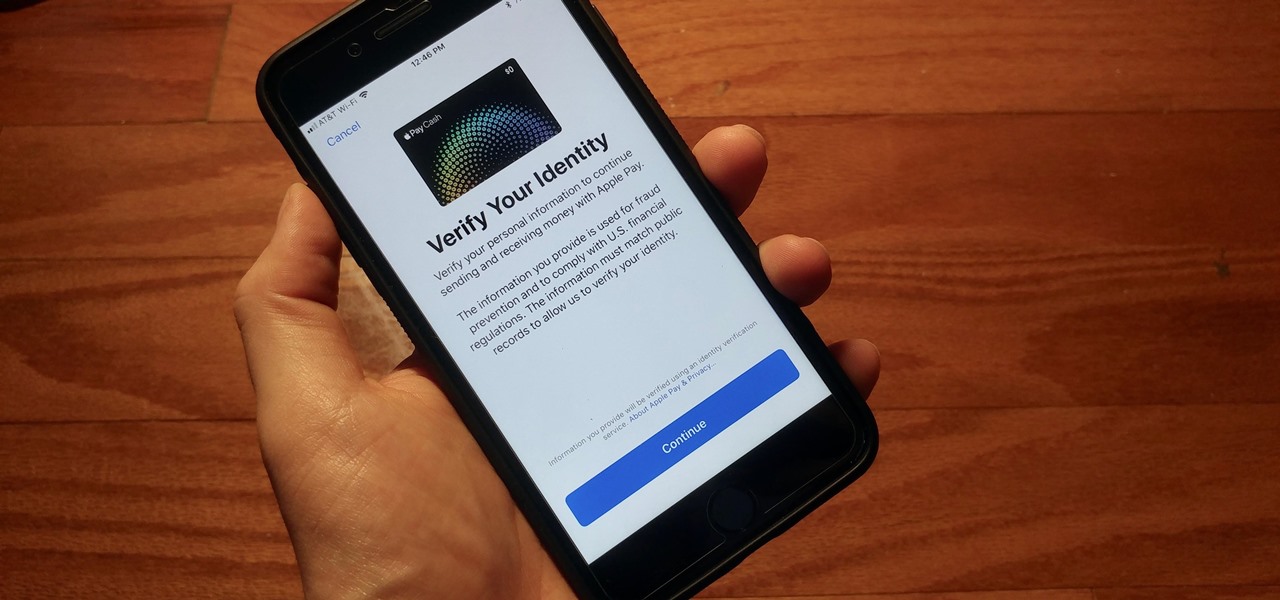
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

Ever since the planet went crazy trying to find augmented reality creatures in Pokémon GO, we've been waiting for the next virtual object game capable of delivering a similar hit. And now, we might finally have one coming, direct from the magical world of Harry Potter.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Newly appointed Ford Motor CEO Jim Hackett admitted yesterday that demand for driverless transportation could take many different forms and that Ford was rethinking how it would tailor its cars and mobility services for self-drive modes of transportation in the future.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

Ex-Uber CEO and founder Travis Kalanick's bad and likely illegal behavior aside, his vision of not wanting to pay "the other dude in the car" has lead to a ground-breaking driverless test fleet.

The ride-sharing firm Lyft and Faraday Future, a troubled electric carmaker and potential Tesla competitor, have quietly appointed new top executives, but like the rest of the industry, they struggle to find talent for their driverless programs.

The AFL-CIO's Transportation Trades Division, which represents 32 unions in the US, has successfully lobbied for the removal of 10,000-lb. and heavier commercial trucks from provisions in bills expected to pass that could allow for millions of driverless vehicles on public roads and streets, Bloomberg News reported.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

Driverless transportation is definitely coming closer to the mainstream, but most companies developing the technology have said it will be another couple of years before we see autonomous vehicles being used as an alternative for typical transportation.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Millions of dollars continue to pour into the Chinese driverless market. Now, according to research firm CB Insights, $929 million have been invested in the first quarter of this year.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

General Motors (GM) has begun production of 130 Chevrolet Bolt EV driverless test vehicles at its Orion Township, Mich. plant as it expands its fleet to total 180 models deployed in San Francisco; Scottsdale, Arizona; and Detroit.

Okay, I have a confession to make. I'm not a real New Yorker. I'm from the land of southern hospitality and steaks bigger than your newborn: Texas. I don't know how to hail a taxi yet, and I still smile at strangers on the street. I'm slowly learning how to fit in, but one thing I still haven't mastered is the New York City subway system. Every day, I struggle to determine where to find my train and how to stand on it without falling over. Fortunately, Google Maps appears to be making some of...

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

While Live Photos has been a fun addition to iOS ever since the iPhone 6S and 6S Plus, there hasn't been much practical use for Apple's moving images so far. That was, until iOS 11 added advanced features such as long exposure effects that make a DSLR less and less impressive these days.

Waymo's transfer of its driverless car know-how to commercial trucks will likely pose few challenges for the self-driving unit of Alphabet, which owns Google.

Tim Cook claimed 85% of new iPhone buyers are switchers from Android back in 2015. Now, after financial analysts noted a drop in the company's stock prices, Apple has unleashed a series of ad campaigns directly targeting the users it needs to win over. That's you, Android lovers.

UPDATE 5/12: According to Bloomberg, it looks like the merger is on. Anonymous sources claim discussions have already begun about consolidation. Looks like there might be a new 5G powerhouse after all.

Last week, T-Mobile CEO John Legere got salty. He announced ever so cheerily T-Mobile's intentions to release the first true 5G network in coming years, all while gaily smacking AT&T around for their bogus "5G Evolution" reveal. But could Legere be wrong to say T-Mobile will be the nation's first 5G carrier? It looks as though that title may have to be shared with Sprint ...

Oftentimes, seemingly insignificant, nondescript features have the most impact on enhancing our Android's usability. A great example is Nougat's inclusion of customizable Quick Settings tiles, which adds greatly to the user experience by letting individuals tailor their expandable status bars to suit their unique needs.