A guy walks into a bank with a shotgun and tries to shoot his way into the vault. It's not a joke, it's the kind of crime that you're standing up against when you play L.A. Noire for PS3 or Xbox 360. Watch this walkthrough video to learn how to beat the Bank Job Street Crime mission.

It's tough for a cop in L.A. Noire- you've got all sorts of bandits all over the place. For a little help dealing with the Shoo-Shoo Bandits, check out this walkthrough of the Shoo-Shoo Bandits Street Crime mission for PS3 or Xbox 360.

You can't just fight in L.A. Noire, you've got to be better than that. Watch this walkthrough video to learn how to beat the Boxing Clever Street Crime level. Whether you play on PS3 or Xbox 360 this video will show you how to solve the case.

Some things never change. Even in the 1940s L.A. had her share of gang fights, and if you want to beat all of the Street Crime missions in L.A. Noire on PS3 or Xbox 360, you'll have to take part. Check out this walkthrough video.

Every good cop knows when to ask for backup. To beat all of the Street Crime missions in L.A. Noire for PS3 or Xbox 360, you're gonna need a little help. To get past the Hung out to Dry mission watch this walkthrough video.

In L.A. Noire, death is everywhere. Sometimes, it even comes down from above. If you are trying to get past the rooftop shootout Street Crime mission Death From Above in L.A. Noire for PS3 or Xbox 360 check out this walkthrough video.

In this tutorial, we learn how to meet a woman on the street. There are several ways you can meet a woman on the street. The first way is to drop something near her and see if she brings it to you. If she does, you can start to strike up a conversation with her. Another way is to go up and ask for directions or recommendations around town. Make sure to have a lot of confidence and don't try too hard when you are approaching a woman. If you show too much confidence, this will scare her away an...

In this video, we learn how to attract women with the instant street pick-up. When you are approaching women on the street and having a conversation with them, they will most likely close you first. Tell her that you want to see her again and make sure you get her number! Don't let her leave or walk away without asking her number. She's not going to talk and have a long conversation with you and not want your number. Pay attention to her body language and make her feel important, which will h...

It's not a complete Freddy Krueger costume without his famous glove! Learn how to make the famous glove from Nightmare on Elm Street to terrify your friends at the next Halloween party.

Freddy's Alive! No, it's not the next part of the Nightmare On Elm Street series, it's the new remake coming out in a theater near you. And in celebration of the return of "A Nightmare On Elm Street", starring Jackie Earle Haley as Freddy Krueger, Indy Mogul's BFX made this great how-to video on making a cheap, but super-realistic, highly detailed replication of Freddy's iconic killer clawed glove. If you're a fan of the horror series and Freddy, this is the ultimate fan reproduction to make ...

Learning French on the web is brought to life by walking the streets of France though a YouTube video. Here a French man brings you to a large advertising poster on a Paris Street to show the use of verbs. While the content of the billboard/poster itself grabs your attention, the on the street instructor provides vital information so that you will better understand the imperfect combined with conditional tense. This novel approach of learning French grammar though the use of real life example...

There are good magic tricks, and there are bad magic tricks. The host of this video tutorial might not be the most skilled magician around, but he's a pretty good judge of card tricks. Check out how to street hustle with the three-card monte card trick. With just a little sleight of hand and a little magic, your spectators will be astonished. See the reveal and explanation.

Live in a shady neighborhood? Learn how you can keep your car from getting ripped off? Protect your vehicle by parking it in smart areas like well lit streets or in front of an angry dog. Also, don't drive the nicest car on the street. It's too flashy and will incite interest.

This acoustic guitar video tutorial explains how to play the song "Grey Street" by Dave Matthews Band on the acoustic guitar. There are only two parts, so it's not too tough to figure out. This is a great instructional video for hardcore DMB fans and acoustic guitar enthusiasts. Practice your guitar skills by learning each chord to the song with this step by step video.

This how-to video shows how to drift in NFS Pro Street. The care used is called a Silvia, and it is a great car for beginners.

This is a tutorial on NFS Pro Street. This how-to video shows how to drift on the car Silvia Ryo.

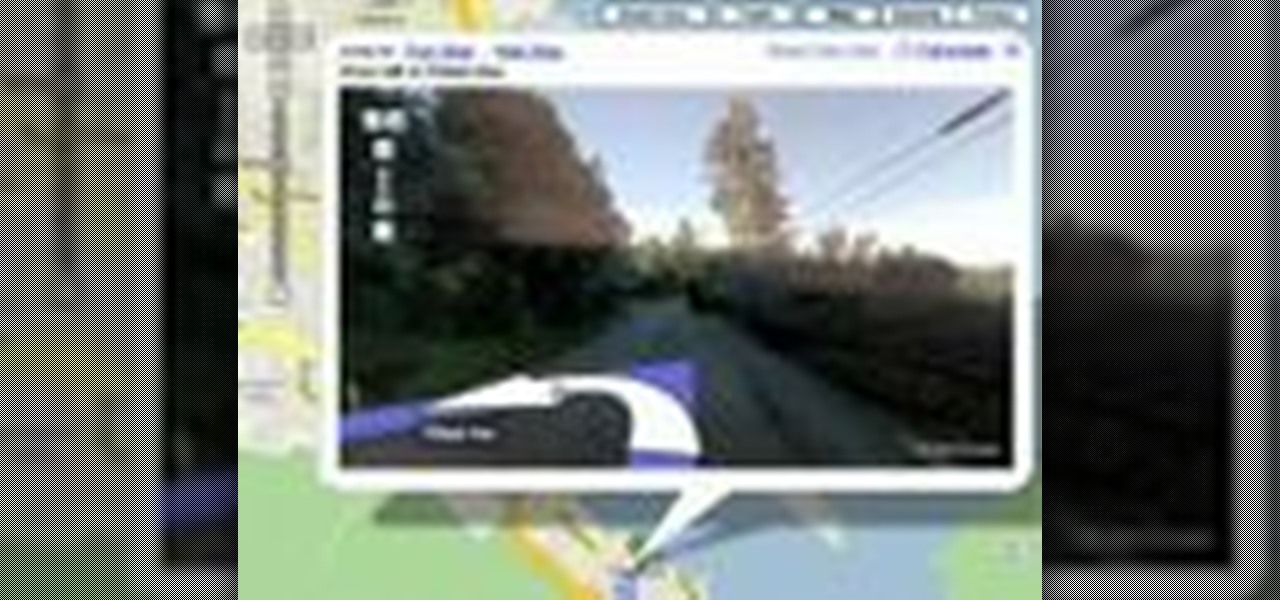
Now you can use street view when getting driving directions on Google Maps. Check out this video to get tips on how to use this feature.

Make khanom krok from the streets of Thailand. They are delicious little morsels of coconut pudding. You can sell them too . . .They cost about 5 bahl.

In a two-part lesson on a drone-blues riff from the streets of Harlem. Also, news about the FIRST extended Satan and Adam recording made on the street back in 1989. (Gussow is using an A harp.)

Ubuntu and Windows may have trouble syncing time because when they are dual booted, they both assume that your hardware clock is set to a different time setting. Ubuntu assumes that your clock is set to UTC and Windows assumes that your clock is set to local time. Answers Launchpad has solutions to fix the syncing issues. To correct the issue, configure Ubuntu to be set to local time. Launch your terminal window and click on the description box. In the code string change the UTC default value...

Change your Snow Leopard dock on Mac OS X with this video tutorial. Go to Leopard Hard drive -> System folder -> Library folder -> CoreServices folder -> Dock App (right click) -> Show package contents -> Contents folder -> Resources folder -> Scroll down until you get to Scurve-1.png, Scruve-m.png, Scurve-sm.png, Scurve-xl.png -> Highlight them all and delete them -> Select the dock you want to change it to -> Paste the files into the place that you deleted the others -> Search for "Terminal...

This video will show you how to enable MMS on your iPhone 3G and 3GS on 3.1 firmware. First, copy and paste the terminal code. Hit enter. Go back to the description and click the link to the file. Connect your iPhone and go into iTunes. Hit options, check for updates. Go to where you have downloaded the program.

Chair massage is all over now, even airport terminals. A chair massage is wonderful when we don't have a table and we're in an office or in front of a computer at home. Learn the art of giving a chair massage in this health how-to video.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

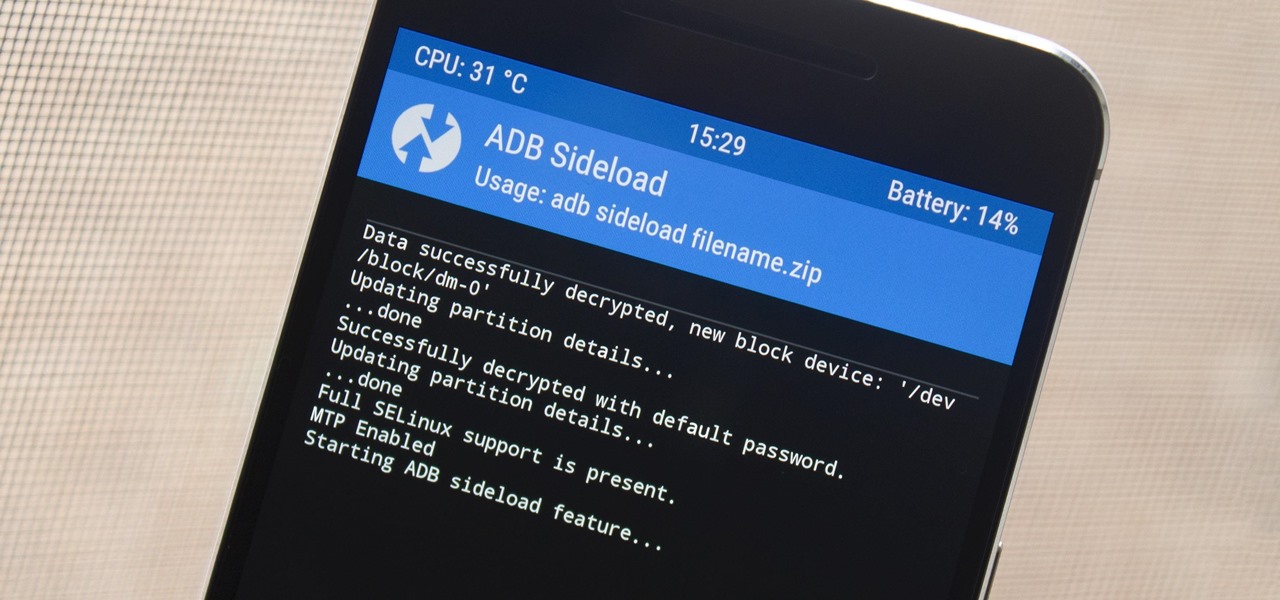
The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.