Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.
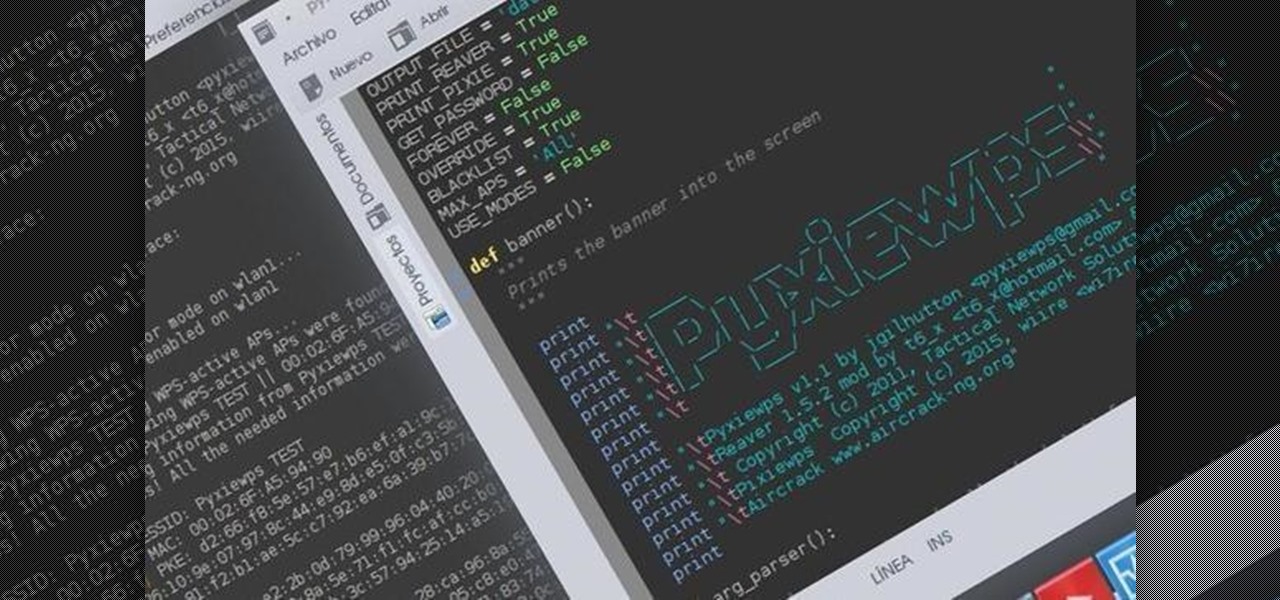
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.
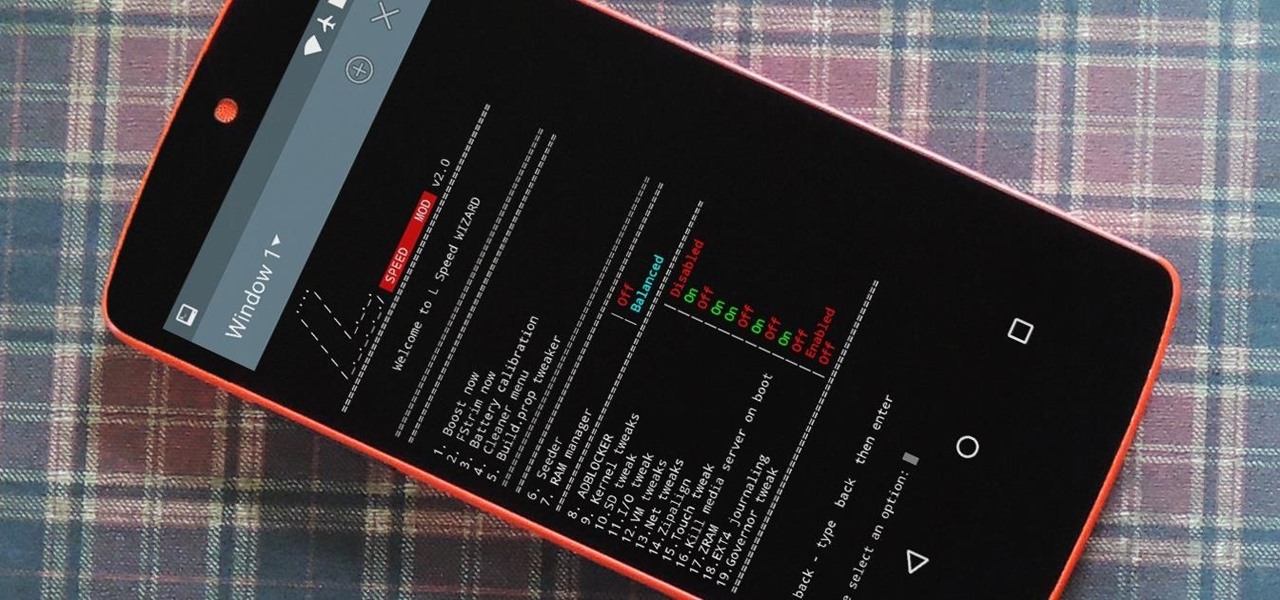
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management and other system-level functions, he created a flashable ZIP that will apply many fixes in one fell swoop.

The trick in the video is that the magnets are made of a conducting material and they connect the battery terminals to the copper wire, so the battery, magnets and copper wire make a circuit that generates a magnet field just in the vicinity of the battery. The geometry means the two magnets are automatically at the ends of the generated magnetic field, where the field is divergent, so a force is exerted on the magnets.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

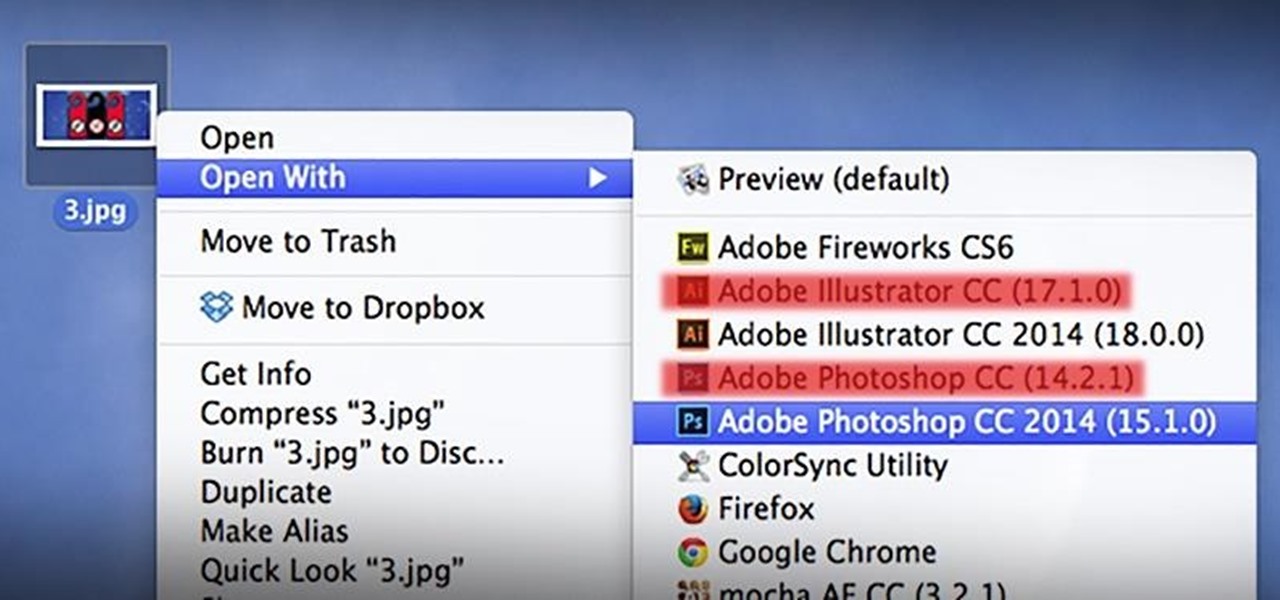
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

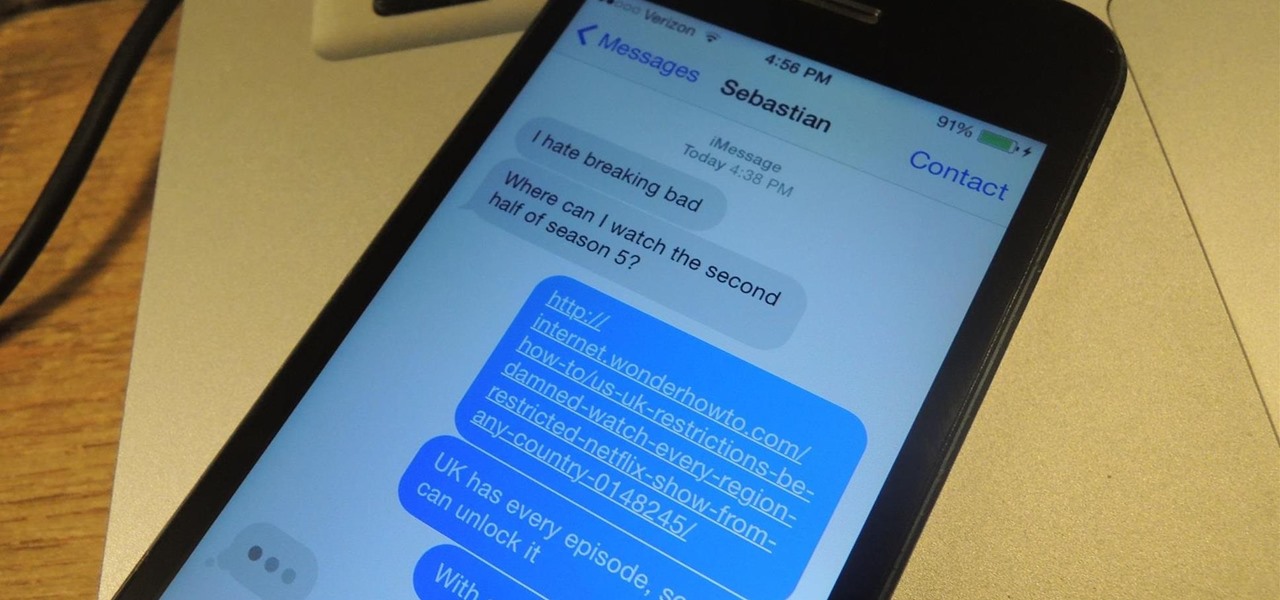
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

Ever wonder how to make an engine out of soda cans? Not even sure if it's possible? These videos will show you how to build a working Stirling engine out of cans and other general materials. Here it is in action:

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

The longest-running children's television show in the United States, Sesame Street, hasn't survived 50 years without leveraging new technology along the way.

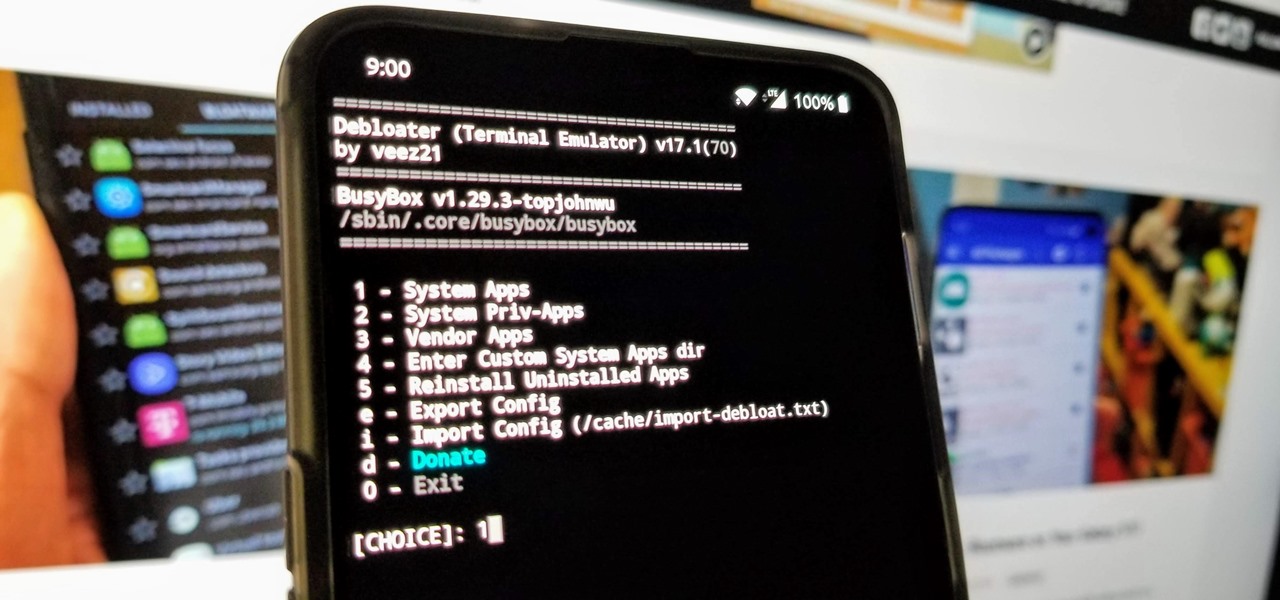
When you get a new phone, the last thing you want to deal with is a ton of preinstalled programs staring back at you. They not only clutter your home screen with apps you'll probably never use, but they're also wasting space on your internal storage and potentially draining battery. To truly uninstall them, you'll need root — but even then, it can be hard to pin down all the apps that should be removed.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Full disclosure — I have almost zero Street Fighter experience. The first time I played the game was at Barcade, way back in ... 2017. Yes, to the shame of gamers everywhere, this reviewer is a Street Fighter noob.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

As softModders, the first thing we do after updating to the newest version of Android is to root, install a custom recovery, and install a superuser app. By doing this you open up your HTC One to a vast quantity of new apps and tweaks you can use to truly make your phone One of a kind.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

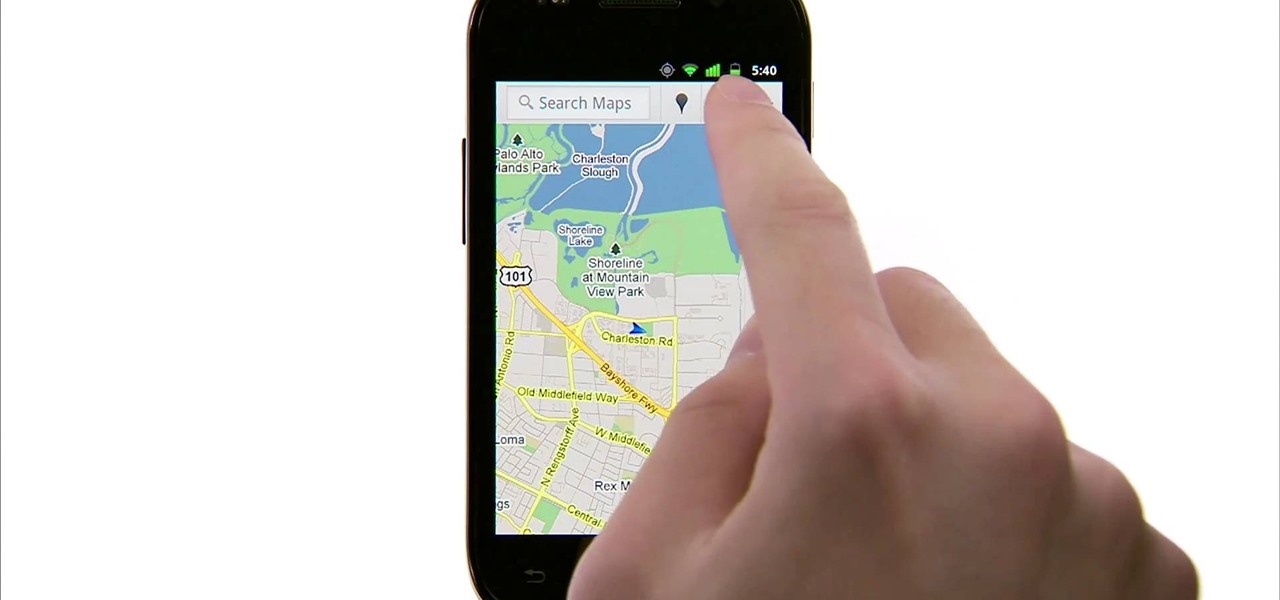
Google Maps is much improved in Android 2.3 (Gingerbread). And even better on the Nexus S. This smartphone can do many things, but the best feature is still Google Maps, which will appear shortly on all Android devices when Gingerbread is officially released.

Contrary to popular belief, graffiti doesn't have to be all tough names, tough tags, and tough gansters. In fact, you can draw just about any subject you want using the graffiti style in order to make it look cooler and more street beautiful. But don't take our word for it.

In this tutorial, learn all about how to make the most of your iPhone camera when on the street. Sometimes on vacations or trips, it is difficult (and dangerous depending where you are) to carry around a big, heavy camera all day. Did you know that you can take great photos with a pocket-sized iPhone? In this clip, Lisa will show you where to aim and how to set up your shots with an iPhone to get the best pictures possible. The best part about mobile picture taking? You can upload your images...

Windows 7 has hit the streets. If you've got Windows Vista or XP, and you are preparing to do the switchover to WIndows 7, check out this video!

The one card trick that every street magician or street hustler needs to know is 3 Card Monte. With the help of this video tutorial, you'll see exactly how to perform the three-card monte throw. There is no real magic here, it's all just a sleight of hand, which is needed for any magic card trick.

This tutorial segment is from the old "Basics" video by Transworld RIDEbmx. From bunnyhops to 180s to feeble grinds to basic grinds on the bike, the Gonz and Butcher guide you along to learning the building blocks of street riding. Learn how to ride a BMX bicycle with the basics! You'll even learn how to do the bar spin trick on your bicycle. These are the basics to street bike riding my friends.

Feeling inspired? Looking for a place to express yourself creatively through art? Why not take to the streets, and use the city walls as your canvas. This video shows you how to make a stencil, just like the ones the international star Banksy uses.

In order to color complex street drawings with markers, you will need the following: markers in assorted colors and a street sketch.

Have you ever had the urge to throw a ball at someone, but knew you could never do it? Regardless if for merely a gag or out of frustration, we all have that someone we would love to use as target practice, but know fully well we can't purposely try to hurt another person. Well, we have the solution here...

Watch this video and learn how to teach your children to cross a street when they are standing between parked cars.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

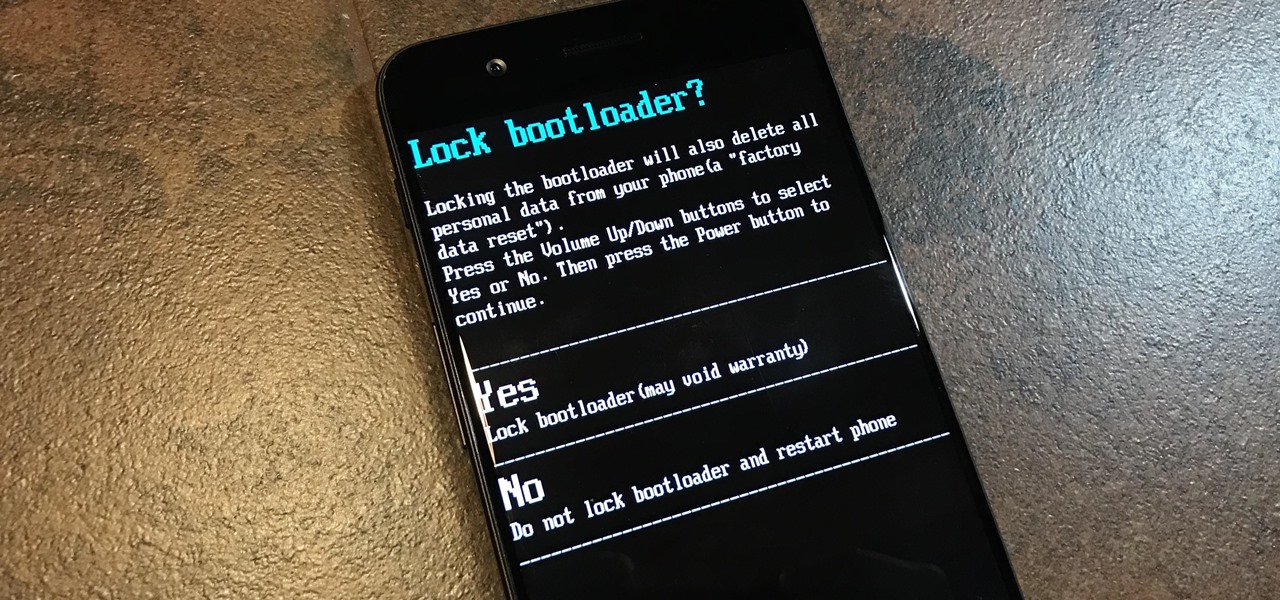
Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.