Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.
Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

Hello there Nullbyte users! This will be my first article here.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

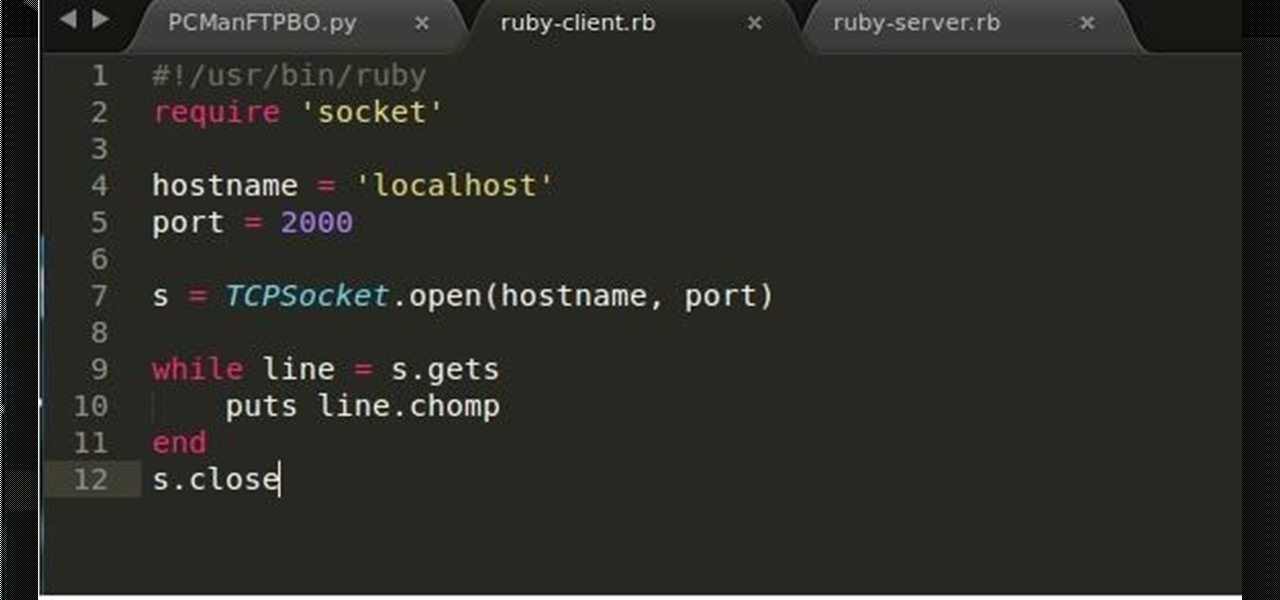
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

You can find hundreds, if not thousands, of complaints about Wi-Fi performance issues with iOS 8 across all Apple devices. Even I had the issue on my iPhone 5S. The Wi-Fi connection on my router was strong, but I was getting extremely slow speeds. So slow, that I would resort to using LTE instead of Wi-Fi, which in turn led to going over my monthly data allotment.

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

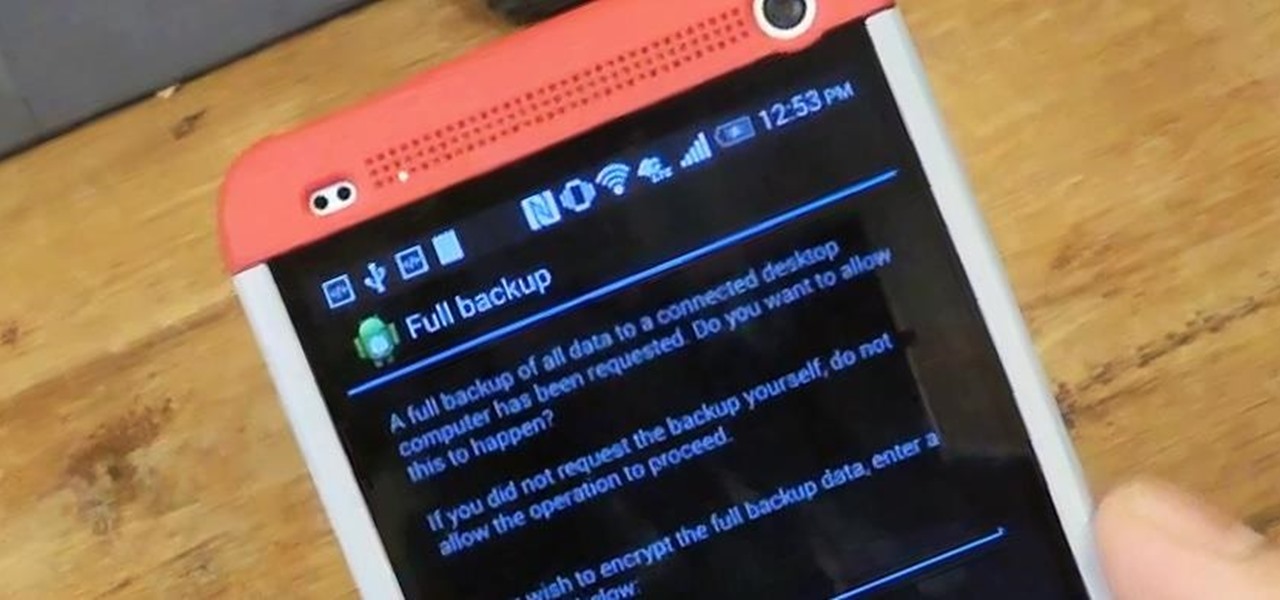
Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

For most people, the battery life on a DSLR is more than sufficient, but if you want to do a really long exposure or time-lapse, one charge might not last long enough to get the shot you want. You can always connect it to an extension cord to charge while you shoot, but that can be really annoying to work around.

I love my Mac to pieces, but there have been times, so many times, that I wanted to silence that classic Apple start-up chime. I mean, the only thing the sound does is notify everyone around you that you have a Mac, and that you have turned said Mac on, right? Well it's not so vain.

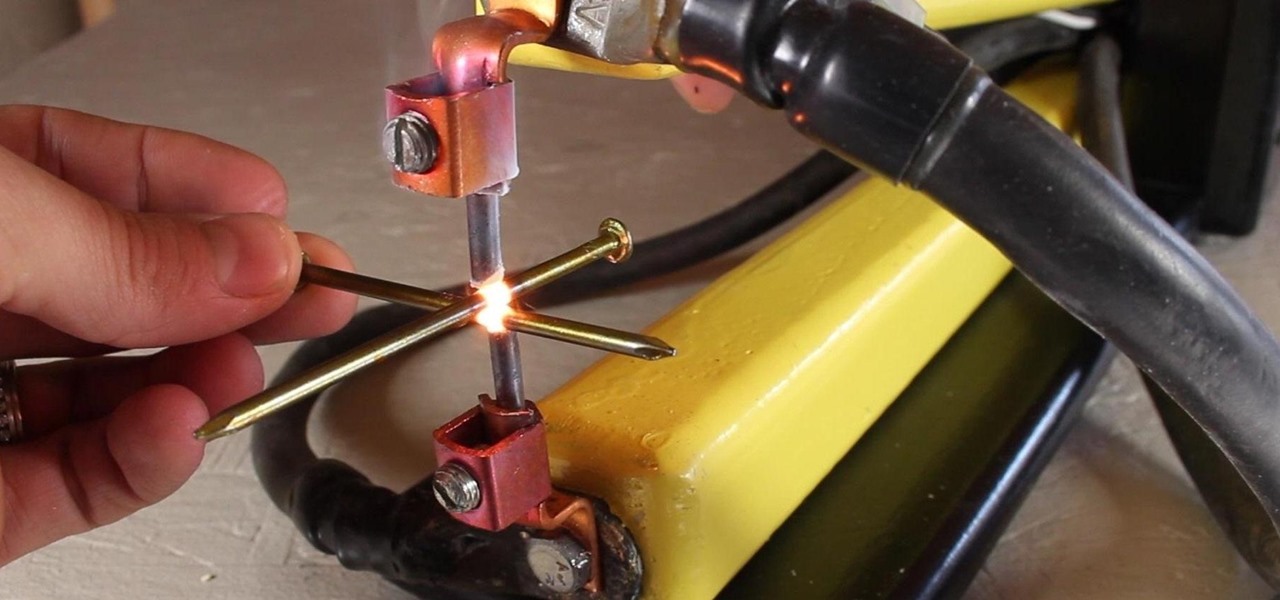
A typical resistance spot welder can range in price from about $200-$800, but with a little resourcefulness and a bit of free time, you can make one like this for about $10 or less.

The Samsung Galaxy Tab 2 (7.0) 4G LTE on Verizon has only been released for a couple months now with good reviews. It comes with dual cameras, memory expansion, and very quick 4G LTE speeds, without needing a contract. While most users are satisfied with the tablet as is, there are others that prefer rooting the tablet in order to install their own custom ROM. Now you can do it with the Samsung Galaxy Tab 2.

Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent version.

Ryu from Street Fighter is the face of fighting games, and as such could not be omitted from Marvel vs. Capcom 3. This video will show you the basics of fighting as him in this new game, including all his supers, specials, combos, and launchers you can use to confuse and annihilate your opponent. HADOUKEN!

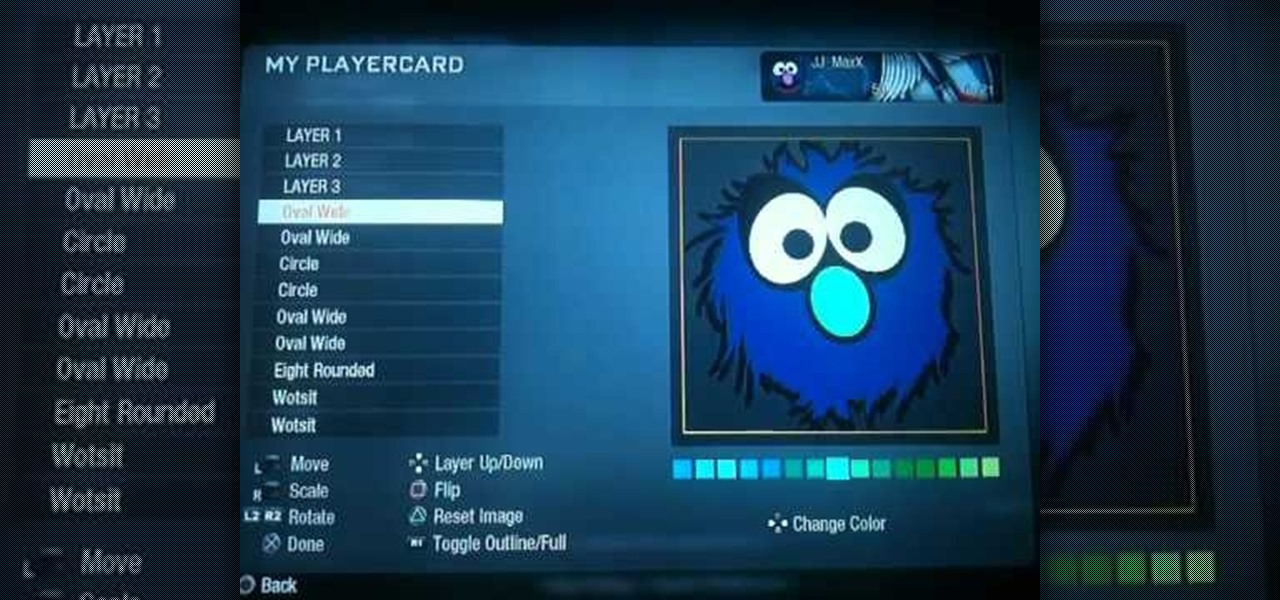
Sesame Street Muppets are beloved by the majority of American television-watching children, but Grover doesn't get as much love as some of the other Muppets like Big Bird and Elmo. Show him some love by making a Grover player card / emblem in Call of Duty Black Ops.

One of the reasons we love Halloween is because the spooktacular holiday lets us go all out and get crazy with our makeup without getting condescending, awkward looks on the street.

Sliding gloves are a great tool to help you add a new surface to your longboard sliding. Sort of like the combination of longboarding and street luge, this adrenaline junkie sport is fast. Check out this video to learn how to make the gloves.

A steadicam can mean the difference between a professional and steady wide shot of Victorian era London or a wobbly, user-generated content-esque portrayal of some old lamps and streets. Having control over how your camera moves is so vital to good film production.

In this video, we learn how to do the invisible board & super jump glitches in THAW. First, turn low gravity on then get onto the roof of a building. From here, jump onto the ramp then jump into the grass down on the bottom. After this, find the invisible wall and jump up it. After this, climb to the top of the mountain right next to it. Then, run down the street and slap the wall while jumping up it until you reach the top of the hill. Then, run down and jump to the bottom on the street. Now...

This might be the single best combo that Guile can do in Street Fighter 4, and you're gonna learn how to do it. It's a Flash Kick - Focus Attack Dash - Sonic Hurricane combo that is devastating and can be done quite fast with practice. Which is what you should be doing as soon as this video is over and you can get to the arcade. Unless you're watching this on your phone AT an arcade, you 21st century digital person.

The video describes an easy way to survive an attack from someone in the street. When the assailant grabs your, your first reaction should be to guard against their initial blow. Then, punch them in the groin, grab them around there neck in a sleeper hold type move using your arm to wrap around the back of their head and/or neck. Proceed to knee them hard either in the stomach or groin, and then simply push them off of you presumably giving you enough time to run and escape.

Have you ever found something in your suitcase that wasn't yours? Maybe it was, but you're almost certain it wasn't. Maybe a friend slipped something in your baggage before your departure flight? Maybe the TSA was playing a joke on you, since they have all the master keys for your approved travel locks?

Tutting is basically the human body's way of trying to become a square. Or a triangle. Or a rectangle. That's because tutting is a type of street dancing that involves moving the body to create geometric positions, usually with right angles.

Have you always secretly harbored a love for urban design or architecture but your parents made it clear to you that they would only financially support you through school if you studied pharmacy? We know your situation sucks, but just because you can't get a degree in urban planning doesn't mean you can't sketch out designs of beautiful cities.

What do you get when you comebine graffiti, a spray can, and a lean and mean street urchin? Well, according to graffiti artist Wizard, you get a very gangsta looking spray can with an arrow-shaped goatee.