We hang flags to proclaim our patriotic spirit. This is especially true for retired veterans or those who have loved ones serving in the military. Others hang flags representing the seasons, important events, favorite teams or just a cute and whimsical design as decoration. An American flag can be particularly tricky to wash. Red, white and blue all lying together in one inseparable panel can cause the blue or red dye to bleed onto the white. This is not just a problem with an American flag; ...

Plantar warts are non-cancerous growths that can be found on the heel or ball of the foot, and in some cases, even on your fingers. They most often are very painful and are hard to get rid of. Most removing methods can be very painful and uncomfortable.

I saw this on the Food Network and tried it out. We loved it. It is a great way to use leftovers and with the holidays upon us, I know you'll want to try it. I think it was Jamie Oliver who presented it although I couldn't find it on the website. It was described as a common thing done in the UK as the evening meal after a Sunday lunch. It is great with leftover turkey, dressing, and potatoes and gravy. The name comes from the sounds that it makes when it cooks. When you put the patties in th...
FV Extender for Chrome This is an extension you can download for your the Chrome browser. At this time the extension only accepts and sends back gifts but may do more in the future. See developer's site for more information, and a quick video showing this feature in action.

How to... Remove A Very Tight Lid? Use Items You Have Around The House! Step 1Want to remove a very tight lid? Do you have a weak grip or arthritic pain in your hands? Have you already tried tapping the lid with a spoon? Thumping the bottom of the jar with the palm of your hand, and it still won‘t come off? An easy, quick way to remove a very tight lid is to put on rubber gloves! Yes. Ordinary household rubber gloves. Hold the jar in one hand, then use the other hand to twist the lid off. Thi...
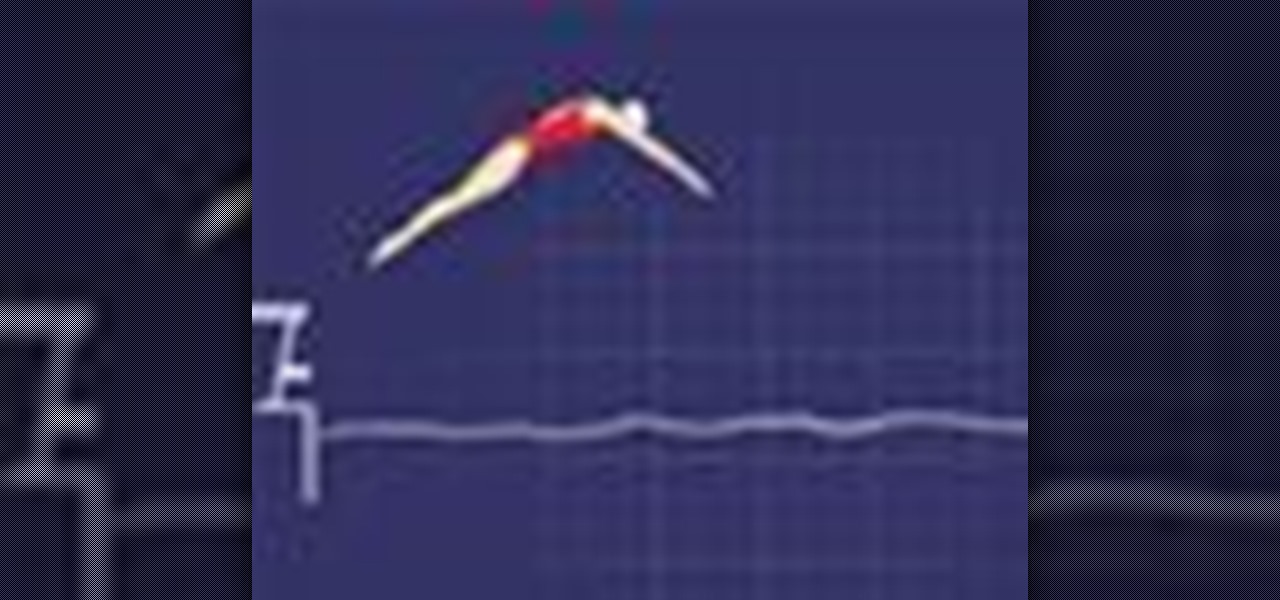
Most top swimmers use the grab start to get their race under way. This gets you moving off the blocks quickly and into the water smoothly. The starter will not begin the race until everybody is ready and still. This is really important because you can be disqualified if you fall in before the start or if you are slow getting ready. Follow along in this how-to animation to learn the best method to power off the blocks in swimming.

This tutorial shows you another method for creating a new dynamic flash page in Flash MX Professional. Create a new dynamic flash page in Flash MX.

Is your toilet full of lime scale and other nasty stains that you just can't get rid of with conventional methods? Don't worry just reach for the fridge, and grab yourself a cola! Clean your toilet with Coke.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

Panasonic announced an interesting concept today that could advance millimeter-wave radar technology for automotive safety uses in detecting pedestrians, bicyclists, and other motorists.

Ink & Paint was originally intended to provide a place for the sharing of graffiti and street art related news and the spreading of the street art culture. However in recent months I have noticed a distinct lack of "lowbrow" art in the WHT community. Don't get me wrong though, I'm a HUGE nerd. I love null byte, I love the Minecraft world, and all the tech posts that are becoming increasingly more common. It's awesome. However the nerd in me and the artist in me both want to see more comics, s...

Are you a Minecraft cake fanatic, but have a hard time gathering enough eggs together to satisfy your addiction? Have you ever wondered if there was an easier solution to getting those "hard to get" chicken eggs? Well, today we will be going over a method of chicken egg farming.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.

Jeb just announced a great new feature that will be added in the 1.2 update. This map format, titled "Anvil," will open Minecraft to so many more possibilities with the new update to mod compatibility.

It's no secret that water and electronics don't mix well, but somehow, people always manage to combine the two. I've had my fair share of water-damaged electronics, everything from cheap headphones to a desktop computer. My devices are getting dunked in water so much, it's like doughnuts in coffee. And I know I'm not the only one. That jam session with your favorite song will end really quick when your iTouch is chilling in the toilet bowl.

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.
Sergio Peralta Advisor: Jessica Davis

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

I've come across a few very stubborn Xbox consoles in my day. A previous Null Byte demonstrated how to fix the Xbox with just eight pennies and some electrical tape. But if you've got one of those hell-born boxes that just refuses to be fixed in any way, shape, or form, there is always one last ditch approach. I'm talking about the infamous "towel trick". It works over 90% of the time, from my personal experience. Though, please note: This is only a temporary fix.

I can't believe it, but I've actually read about dozens of people getting their iTouch, iPhone, or iPad stuck in a bricked recovery loop and then going out to buy a new one. This is overly unnecessary. When it gets stuck in the recovery loop, some people mistake themselves by thinking that it is impossible to get the device back into DFU (Device Firmware Upgrade) mode. Getting the device back into DFU mode would at least allow us to jailbreak the device, essentially bringing it back from its ...

What happens when a struggling writer cannot finish the screenplay to her second film? She writes a book.

Last post, we looked at fractal cookies based off of the recipe by Evil Mad Scientist Laboratories. In this post, we'll follow their recipe for fractal cupcakes based off of the Koch Snowflake, which we used previously to decorate pumpkins for Halloween.

Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

The clock is ticking! Pick up some bokeh tips or buy an app—whichever method you choose, you have until Monday, November 7th, 11:59pm PST to participate in this week's Giveaway Tuesdays Photo Challenge. Below, 50 beautiful bokeh photographs to inspire your entry.

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

Welcome to WonderHowTo's first Weekly Community Roundup! Each week we will be featuring the best projects from the community, as well as ongoing challenges and activities you can partake in. WonderHowTo is made up niche communities called Worlds, so if you've yet to join one, get a taste of what's been happening this week in the highlighted Worlds below...

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

Earlier last month, I wrote on how to subscribe to Google+ users using PlusFeed. I used it, and then I realized that I wasn't getting my own feed anymore. I discovered that the free service had been disabled due to cost issues, as detailed by the creator +Russell Beattie. The code is open source, and you can roll your own service, if you have the know-how and the time. If you don't, but still want to create RSS feeds for your own public posts, or just to track your favorite Google+ users, the...

You're never going to see a project from me that involves straight pipe. You would have when I was a kid, but after too many years in the construction industry, I need to see a good finish. If the project doesn't look slick, I don't want to say I did it.
Oh, yeah. I was a skeptic, too. A few things are worth noting, though. 1) This stuff is cheap. You can get started on a project for very little money. Even advanced fabrication tools are reasonably priced.

For as much money as they've made from North American video game audiences over the years, Japanese game developers don't seem to have very much faith in them. Dozens of great titles from their 40 years in the industry have appeared in Japan and across Europe, oftentimes even in English. But they never make it over to America, like Mother 3, Last Window: Midnight Promise, Dragon Force 2, and Tobal No. 2 (that one didn't even hit Europe).

A couple months ago, the world was supposed to end. It didn't. But that didn't stop the Centers for Disease Control and Prevention (CDC) from warning citizens of one global possibility besides complete destruction—ZOMBIES. They used the farcical flesh-eating living dead as an excuse to teach you about the necessity of real-life emergency planning.

Ball Pythons have become big business in the pet trade industry over the years, due to them being one of the most docile snakes in the constrictor family usually preferring to roll into a tight ball hiding it's head than to striking out with the intent to bite. These snakes come in a vast assortment of colors and patterns many of which are highly sought after and can get to be rather pricey. If you are considering adding a ball python to your home please put serious consideration into the nee...

They've been at it for a few years now, but the crazy group of amateur rocket scientists who call themselves Copenhagen Suborbitals have triumphed over adversity, successfully launching their DIY rocket nearly 2 miles into the sky last Friday. The privately funded, non-profit aims to one day send human beings into suborbital space on the cheap, without the need of government budgets and administration.

The Free Art and Technology Lab (F.A.T.) has provided three different energetic and passionate methods for voicing support for Ai Weiwei, the famous Chinese artist and activist who has been detained without known reason by the Chinese government since March 31st.

For most street artists, it takes a considerable amount of time to paint large art installments on the walls of urban structures. The more time it takes, the better chance there is of getting caught, since nearly all of the rogue artwork is slapped on the sides of city and privately owned buildings.

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.