Gastronomes who import the consumption of food - rather than its making - often think more about the palatable impact of a morsel of chocolate or a bite of cake than how the chocolate or cake came to be. But if you're interested in putting on a chef's hat to go full circle with your love of food - i.e. cooking/baking and eating - then you will be pleasantly surprised, even with the hard work involved.

Here is a video on making Pastrami flavored snack sticks. Part 1 is mostly the first day's work (preparation) with a little into the second day's set-up and stuffing. Part 2 is the balance of the production (stuffing and cooking with the recipe at the end). Alternate methods of cooking are to cook 1 hour and dehydrate until ready. No details are given on packaging.
For all kinds of 3D material channels, it sometimes benefits the project to have a small, tileable image that will fill the surface of the object without an obvious seam. Of course, a tileable image will show the duplication if the instance shows up enough times. The trick is to avoid any hard lines where the image might change dramatically as it tiles across the face of the 3D object. Here's one method to avoid those nasty straight seams. (In two parts).

In this first clip, Chef John shows the basic restaurant technique for poaching eggs. Due to the high-volume of a brunch service, it is almost impossible to poach eggs “to order.” They are poached ahead of time and held in cold water until final plating, when they are re-heated in simmering water for a few minutes. This method also works great at home for smaller batches as you’ll see. Once you’ve poached your eggs and have them in cold water you are free to set up the rest of the plate
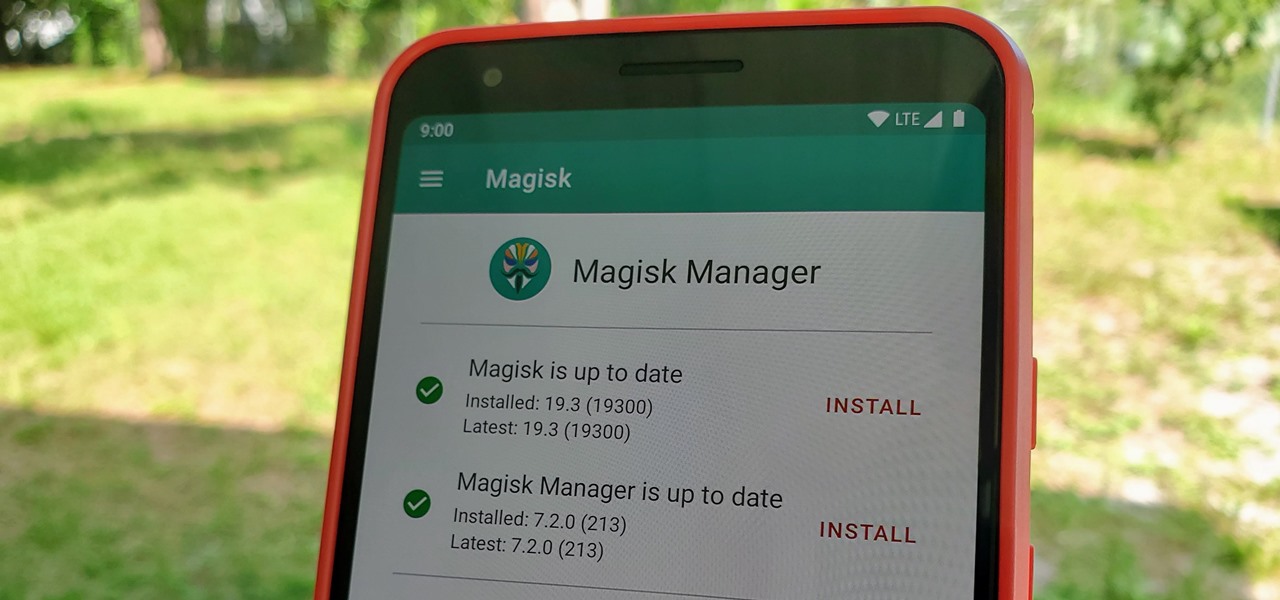
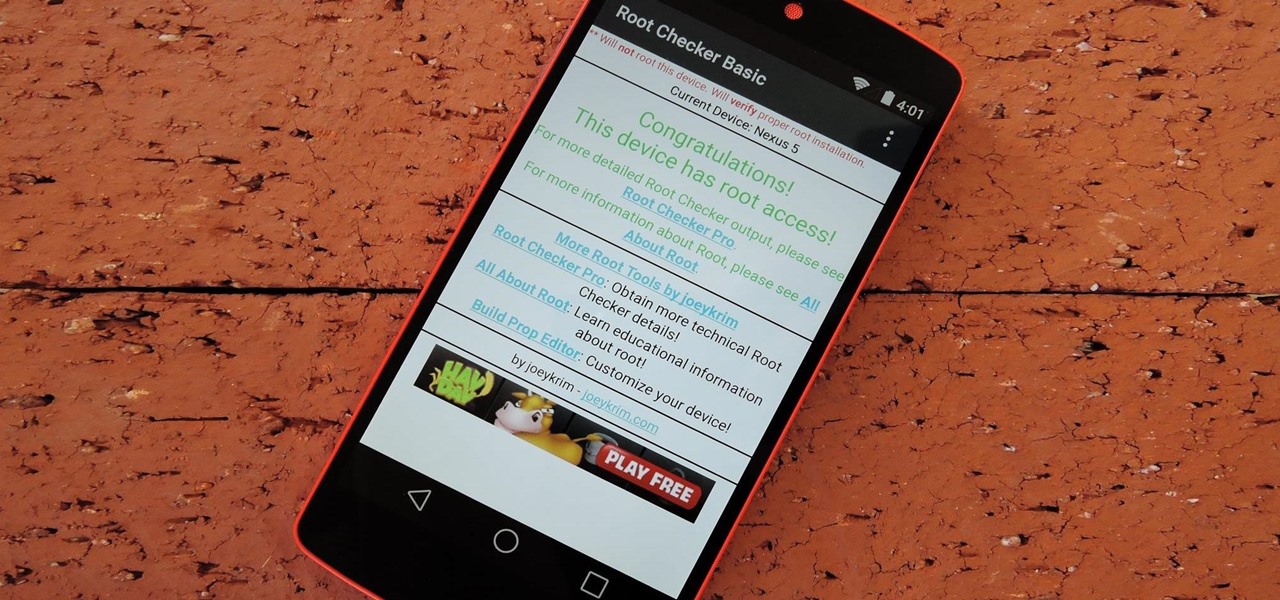
The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

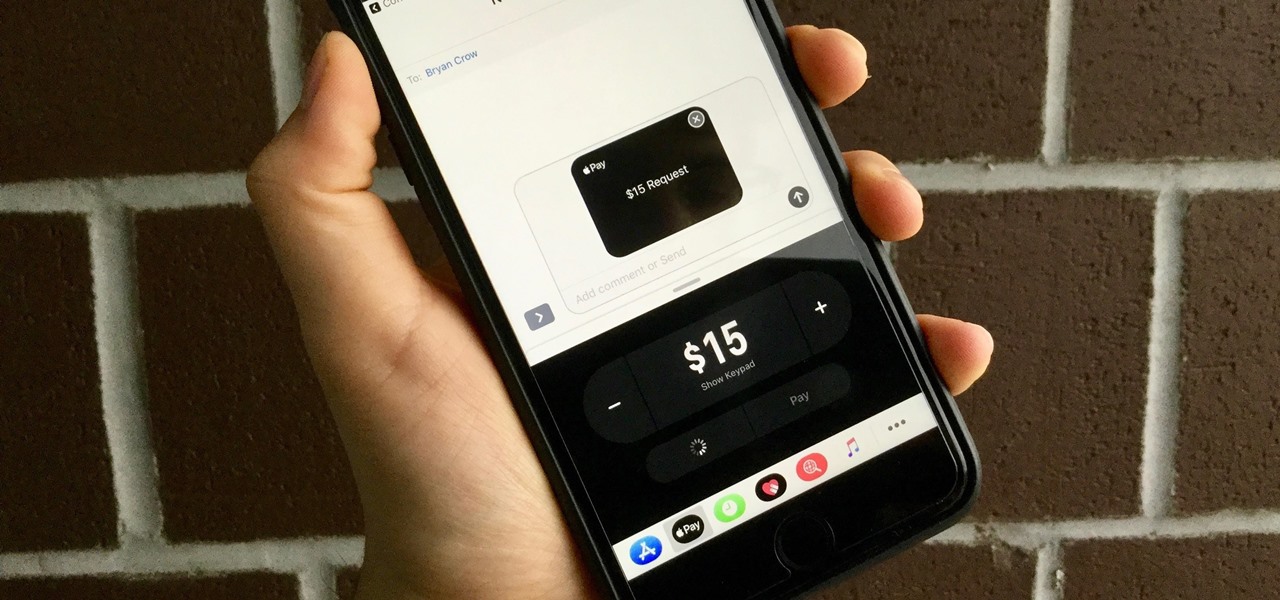
With the release of iOS 11, Apple promised to give us person-to-person transactions by way of iMessages. In the iOS 11.2 update, the new Apple Pay Cash system is now ready for you to send money to family and friends right from your iPhone — and there are multiple ways to get it done.

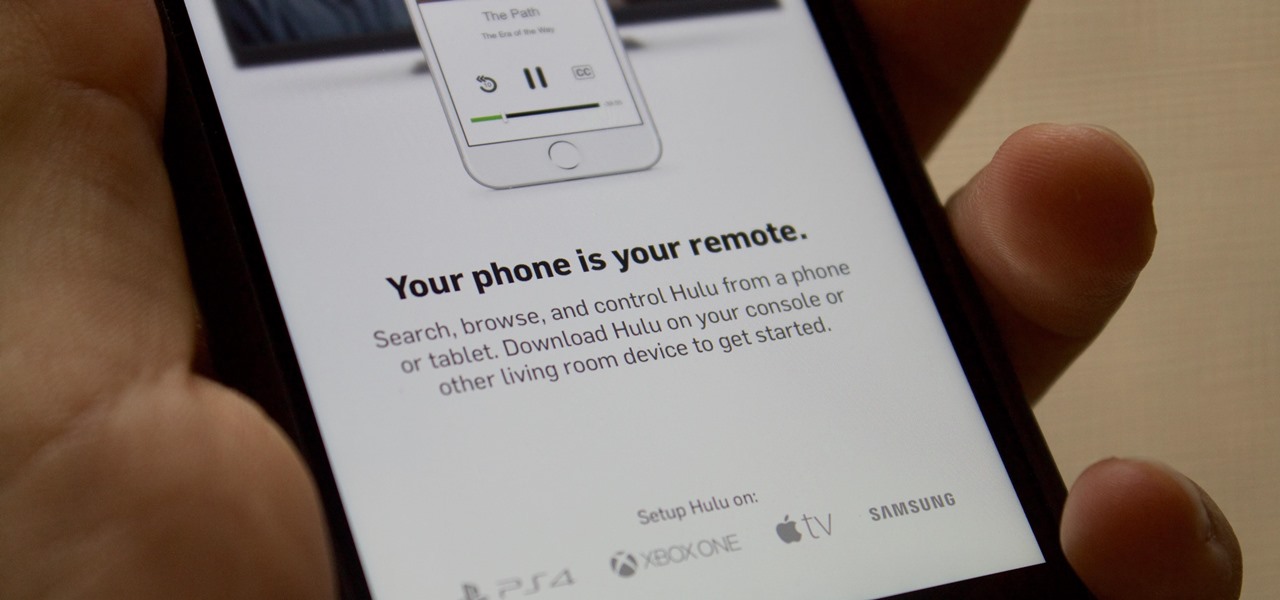
Your smartphone is the perfect place to watch Hulu on the go. Whether you're looking to catch up on your shows in a hotel, or your phone is the only screen available, mobile streaming can be a lifesaver. But what about when you have access to a TV? Wouldn't you rather watch your favorite Hulu Original on the big screen than on your comparatively tiny smartphone?

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

The international, Exynos-powered Galaxy S7 and S7 edge have had a working root method ever since a few days after release. But the North American variants—those using Qualcomm's Snapdragon 820 processor—have locked bootloaders, and have proven to be almost unrootable up until now.

If you think that "pawpaw" is just an affectionate name for your grandfather or a cute way of talking about your cat's feet, you're missing out on one of the most interesting fruits out there.

This cardmaking tutorial is part 3 of a mini series all about the Creative Expressions Gemini Die called Corvus. I have made this pretty pink & white card using a different method for using the die and it is inset rather then used with edges. Step 1: Items Used

All papercrafters and cardmakers and scrapbookers use metallic paper and card but what happens when you run out? and what is an easy why of making some? well here is the answer.

Golden Secrets for super glossy hair - by superwowstyle! Do this about 3-4 times a week. You will start seeing a difference in about a week if you follow all the steps!

The best kept Indian hair growth secret shared! Learn how to grow hair long and fast & naturally!

Learn how to remove blackheads from nose and face, naturally at home! Video: .

This Video will show you how I Blow dry my hair Lightly. Doing this make my Hair so much easier to care for on a

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Video: . This Video will Show you how to Season and Clean

How to Get Your Edges Back w/ Cayenne Pepper & Tropical Isle Black Jamican Castro Oil.

While the preview images for Android's upcoming "L" release just came out yesterday, the new firmware has already been rooted, as is standard with its openness. So if you were feeling reluctant to try Android L because it didn't support existing root methods, then you might want to reconsider.

Here's a great video that shows how make make a hand drill fire from scratch using Stone Age tools...

Here's my latest armor tutorial...what I call the "Demon Hand". The method used in this tutorial can be used to create pretty much any armor. This one is is 18 gauge brass, but if you use stainless steel I suggest 20 or 22 gauge. This is the easiest of all of my gauntlets to create, and it takes a lot less metal. Less than an 8.5" x 11" piece (per hand). Would make cool motorcycle riding gloves!

Video: . If you master only one cocktail, it should be the martini. It’s a legend in a glass, and every hostess worthy of her shaker should know how to make a martini.

Despite its deliciousness, the pomegranate is one of the hardest fruits to eat. Once you cut it open, the seeds are stuck behind a bitter-tasting white membrane, and trying to pull them out with your fingers just results in a huge mess.

Video: . How to Stop Shrinkage with Shea Butter & the Banding Method!

Unless you're a pretty avid home cook, you probably don't know a lot about sous vide. Sous vide is a low-temperature cooking method where food is cooked in vacuum-sealed plastic bags in a water bath for a prolonged period of time.

Fluorescein is a commonly used fluorescent dye that is quite hard to come by in a concentrated form. Fortunately, it's used in relatively large quantities in highlighter markers and can be extracted by a fairly simple process. Fluorescein makes spectacular explosions of color as it dissolves into water and can be used for many different purposes that are addressed in the video below.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

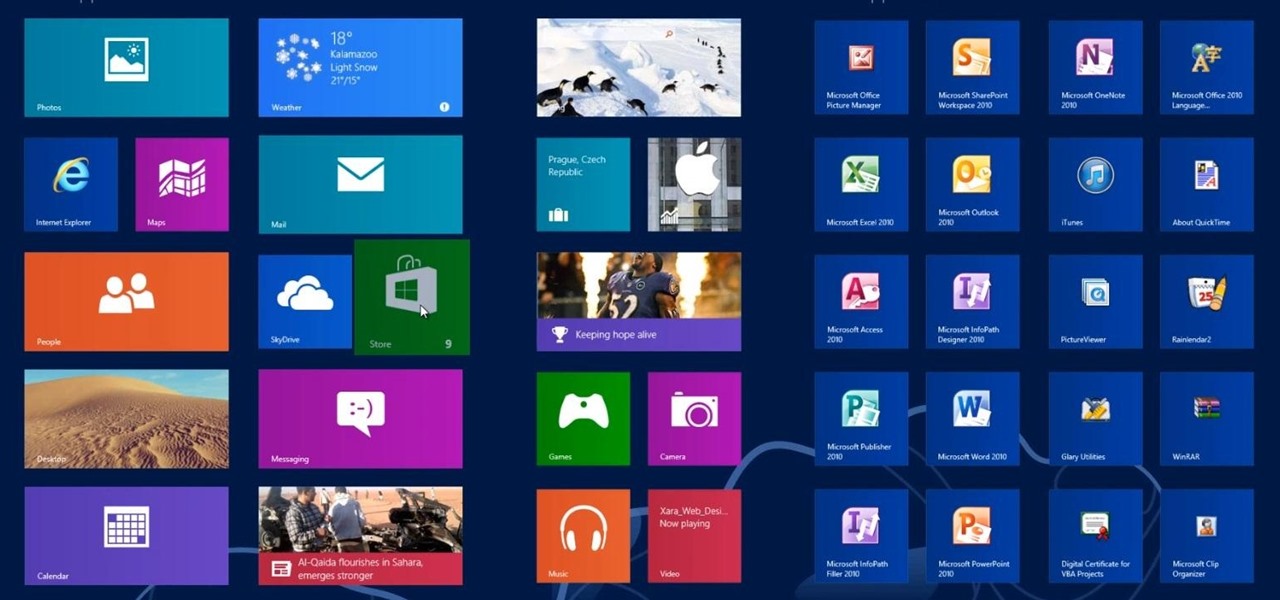
This Windows 8 tutorial, I will show you how to change the name of groups, and rearrange groups and applications in the Windows 8 start menu metro interface.

Windows 8 and its new Windows Store have simplified the process for uninstalling and cleanly deleting applications from your computer. Removing applications in older versions of Windows required a few more steps: My Computer -> Control Panel -> Add or Remove Programs -> Find the Program -> Click Uninstall.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Apparently it is possible to reduce 64,000 possible Master Lock padlock combinations down to just 100. The entire process is clearly illustrated in the below how-to from Mark Edward Campos. For an enlarged version, click here. Looking for something a little more interactive? We have loads of lock-picking tutorial videos. Here's one that demonstrates the same method (math as opposed to shim) outlined in the above illustration.

This is a lengthy, detailed series on iPhone development, for which you'll need an Intel-based Mac computer, running Mac OS X 10.5 (Leopard) or higher. Then, before you actually get started developing for the iPhone, you'll need to register as a developer with Apple. Then, you'll need to download Xcode and the iPhone SDK. Once you have all this, you can start developing iPhone applications!

If you've wanted to solve the Rubik's Cube, there's no better tutorial than this. In this video, you'll learn how to solve the Rubik's Cube with the Fridrich Method.