This is the #1 Self Defense Technique for Women's Self Defense or for anyone for that matter. Even with over 20 years of martial arts training I myself would use this technique because it is by far the most effective and delivers the outcome we want ,which is to be released or to provide means to escape. Think about it, could someone attack you and defend their own eyes while not obscuring their own eye site? Also in the event of a confrontation the eyes will most likely come available at one...

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

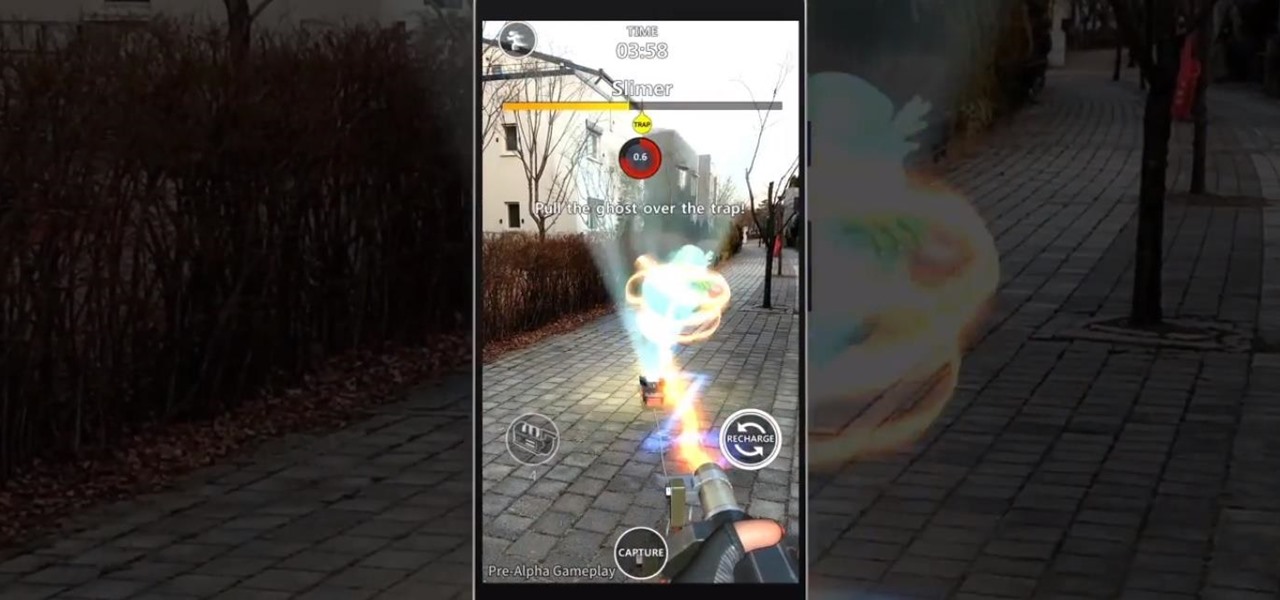
Sony's Ghost Corps, the caretaker of the Ghostbusters franchise, just released some pre-alpha gameplay footage from the upcoming Ghostbusters World location-based AR game to whet the appetites of would-be hunters of the paranormal.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

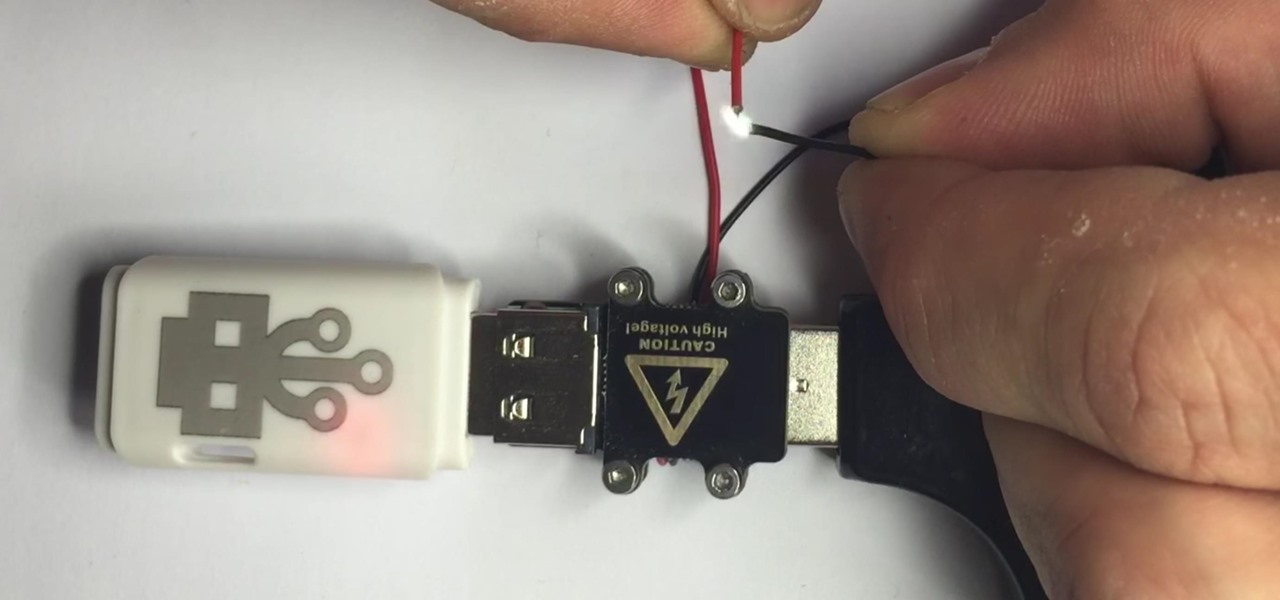
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

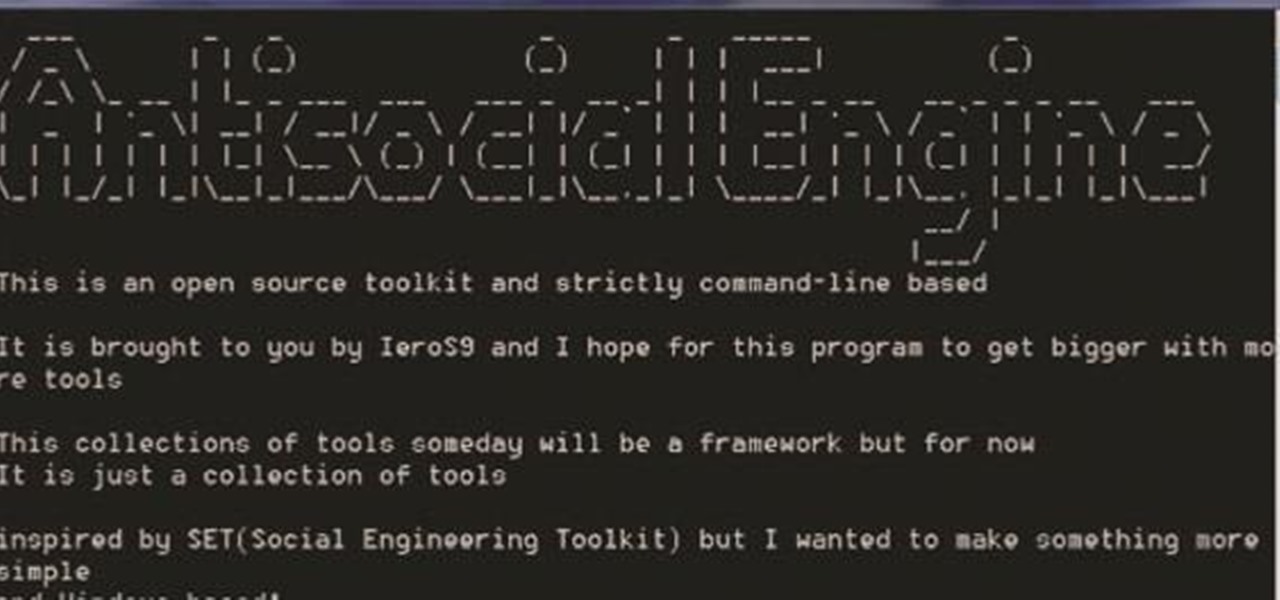
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

Welcome back my fellow hackerians, Today i'm going to tell a bit more about the famous DDOS thing. And on top of that we're going to DDOS a website.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

This is why you're fat. Coincidentally, this is also why you're happy when you nom on artery clogging junk fare. We don't recommend you whip up this recipe on a regular basis unless you're hopin' and wishin' for a heart attack this Christmas, but this would make a sweet treat every once in a while.

Of course, in a Star Wars story, one cannot hope to board a major ship and take it any major distance without being attacked by Rebel or Imperial forces, depending on your side. Star Wars: The Force Unleashed 2 is no exception, and in this video you'll learn how to deal by beating level 7: The Battle for the Salvation.

In this video, we learn how to install brakes, shifters, and grips. You will need: Allen keys, grease, a knife, and a grip to do this. First, attack the brakes onto the handles, then the shifter and the bolts. Make sure to grease the bolts before you place them onto the handles. Do this on both sides of the bike. Make sure you have everything on the correct sides, then slide the grip in. Customize the grip so it's the right length and cut it with the knife to do this. Once finished, connect a...

In Minecraft, the key to survival is building proper shelter for yourself to survive the nightly attacks by the creatures that roam the land. But whose to say that you can't spruce the place up a little bit? Notch has included a feature in the game that allows you create paintings using a few sticks and a piece of wool. In this video you will learn how to craft the paintings and also how to put them up and some of the random paintings that you can get.

During Halloween, party planning can get really hectic. Between baking and cooking party food to picking up plates and utensils at the store to putting up black and orange streamers, there's more than enough stuff to do to give you a panic attack.

We once read a Twitter profile that said, "Love food. Hate exercise. Will die of heart attack." While that's funny and all, we doubt any of you guys and gals would want to drop dead on your 40th birthday. While we're totally for the occasional splurge, it's definitely a good idea to begin eating healthy now.

A big part of pizza's allure is its perfectly crispy crust and oodles of heart attack-inducing oil sitting on the cheese. Personally, we can't even consume a pizza we get from Pizza Hut or Domino's without taking a napkin and blotting off the oil.

Bed bug management requires many levels of attack. Prevention is very important. You should never pick up discarded items on the street. Don't buy used or refurbished mattresses or furniture. Toss out vacuum bags.

Kameron Kay teaches us how to make a floating flower crystal toe ring in this tutorial. You will need: stretch cord, large crimp bead, flat nosed pliers, flat backed crystal flower, glue, and small scissors to make this. First, cut out your chord to the exact size that you need. After this, use glue to attack the ring into the middle of the string. Place a crimp bead on the bottom to help the bead stay in place, then glue these together as well. Next, tie this together and attach an end to th...

In this tutorial, we learn how to work a spinner bait. This has a head as the weight, then the hook underneath the head and skirt. On the other side of the safety pin, there is who flat blades for murky waters. These help with sun reflection. This is a very versatile type of bait that helps you fish in murky waters. Bass will attack it as soon as they see it, helping you catch more fish. There is a lot of equipment on this, so it takes the bass a little while to get a hold of it. To ensure yo...

Are you having a hard time defeating the character Tiamat? Well, this tutorial is just what you need! In this video, you'll find out how to defeat this ugly, Predator looking beast.

if you're looking for a little bit more of a challenge in the game Darksiders, then check out this tutorial. In the video, you'll be finding out how to find all ten pieces to the Abyssal Armor. This armor is much different than War's original armor and is much stronger and gives life on all attacks. It doesn't need to be collected to win the game, but it helps make your character stronger.

Achievement hunters, listen up! It's time to head into the Transformers' world with Transformers: War for Cybertron. This game takes place on the planet to both the Autobots and Decepticons and it gives you a first hand experience of what happened on that planet.