
How To: Disable User Account Control (UAC) in Windows Vista
In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.


In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

This achievement is sure to make you "fly like an eagle." In the game Assassin's Creed II, you're introduced to a bunch of new weapons and skills that you can use to take down your victims. One of the coolest new additions is that of a flying machine or glider. This can be used to travel from once place to another and can even be used to attack nearby archers. Doing that can actually result in the achievement, Fly Swatter. So check out this tutorial on how they did it and how you can do it. E...

In this brief video tutorial, the host 'Uncle Todd' demonstrates how to 'attack a beat'. This video is intended for beginners. Watch as he shows you how to keep your tempo up as you time your drum strokes in a beat. You should practice my trying just your right foot and your right hand, and then alternating to to your left foot and your left hand. The host in this video uses an electric metronome to keep his tempo steady and accurate, something that he recommends you try at home. Don't forget...
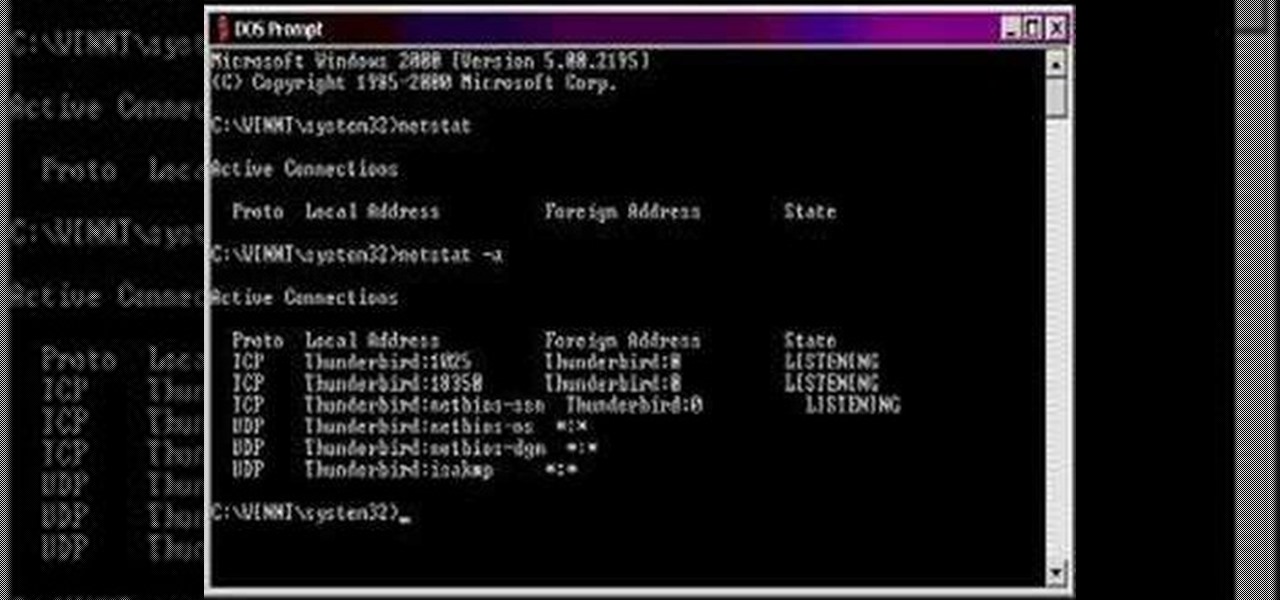
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

Rick Steinau with Ask the Exterminator demonstrates how to prevent yellow jackets from nesting in your home's walls. In mid to late summer yellow jacket populations increase. Yellow jackets can find spaces in the veneer or in cracks in bricks or siding. You can hear scratching noises in your walls as the wasps move. Observe wasp activity late in the day when they return to their nest for the night. Treat reachable holes with pesticide dust and a bellows. Leave the hole open to let the wasps f...

The moonwalk has been written in history and will go down as one of the most well-known dance crazes next to the Macarena and the jitterbug. In order to moonwalk like Michael Jackson, it's important to focus on the pivot and push of the feet and legs while sliding. Make your moonwalk smooth with the tips and tricks given in this free dance lesson.

This video shows tips on how to use insects to benefit your garden. This will teach you ways to reduce the insect load in gardens without the use of chemicals. Rose aphids can be controlled with lady beetles, for example. Although these techniques have been used for agricultural use, they will work in your home garden. Asian Lady Beetle, tend to stay put. They won’t migrate. They will attack Pecan Aphids. Trichograma, a wasp that is effective against larvae and eggs.

This video demonstrates the cross court backhand shot in a Racquetball match. It demonstrates the proper form and timing in an actual racquetball match. It provides helpful tips: for example, the cross court backhand shot should be employed strategically. The best time to consider using the cross court backhand shot is when you see your opponent leaning on the down line: i.e. use the cross court backhand, if it appears that your opponent has already committed to a line of attack. If it appear...

The Dahlia Guy is going to show you step by step how to plant dahlias. First, you want to bury your tubers at 2-4inches of depth and place a stick right next to the eye so you know exactly where the dahlia will be. Also, you want to place a timed release fertilizer in the hole and then cover it up with the dirt. Now, take a 16inch long stick and use that to space out the dahlias in your garden. Some tips to use are use name tags at the beginning of the of the planting and at the end of the di...

How To Set Intonation on a "Gibson Style" Fixed Bridge. A step by step video tutorial that will teach you how to change the strings on a fixed bridge guitar and also set the intonation. Andrew Wasson walks you through a series of instructions that include cutting the strings off your guitar, tightening the bolts on your tuners, polishing frets and fret board and more. He then goes on to show you how to put strings on your guitar, tune the guitar with a tuner, set the bridge saddle, and settin...

Let’s try to thread the needle, as in give a choke hole. First get your opponent down on the mat facing upwards and sit in the mountain position. Hold your opponent's left hand with yours around his head to block him/her. Get your right hand through your opponent's left hand (needle in the hole) and push your chest towards the ground. This will put pressure on your opponent. It will help in your attack as well as defense techniques.

In this tutorial, viewers will learn how to use the synthesizer functions of the Yamaha PSS-780 keyboard. Starting with the basic piano voice, the presenter shows how this can be modified to create a new sound. He shows how the attack rate of the sound can be modified with one setting, how the modulation button affects the tones of the sound, and how sounds can be further modified with the frequency control. The presenter concludes by noting that with practice the user will learn to create ot...

Want tour-like spin on your swing? There are several keys to imparting tour-like spin on your wedge shots, including proper set up, a correct angle of attack, and quality contact. Tim Mahoney, Director of Education for Troon Golf, explains these keys and how you can make them part of your game.

It's time to smash that iPhone, but wait… you don't really want to break your iPhone, do you? That's were a fake iPhone prop comes in, perfect for any homemade movie. Just make this, and switch it out with the real one during the anger attack. Watch this video tutorial to learn how to build a breakable iPhone movie prop. Also works with a fake smashable iPod.

This is a Cheat Engine guide on how to hack this flash game - P.O.D. Kongregate Acheatment shows you how to hack P.O.D. with Cheat Engine (09/23/09). This P.O.D. cheat will give you a level hack.

Cary Kolat demonstrates wrestling technique for collegiate defense. This covers defending single leg attack on the mat. Coach Kolat shows you how to practice funk roll same side as single leg move

Learn how to deal with a black bear or grizzly encounter with Shannon Davis and Ted the Bear. Black bears are distinguished from brown bears by lack of a prominent shoulder hump; a Roman profile or sloping nose and forehead instead of a dished forehead; and shorter, thicker claws for climbing versus longer, more slender claws for digging. Although brown bears are generally bigger, size is not a dependable indicator. Also, fetal position is often recommended as opposed to lying prone as shown.

You never know when you'll have to defend yourself against one of these bloodsuckers, so be prepared to bring a vampire to his knees. While you may not believe in vampires, there are those that do. In any case, prepare now for a hypothetical attack from the un-dead and you won't have to kick yourself later. You will need garlic, a cross, rice, grain, or seeds, holy water, a wooden stake, an axe, matches, and some water. Watch this video survival training tutorial and learn how to fight off a ...

Grandmaster Alexandra Kosteniuk teaches you how to... you guessed it, play a game of chess. This chess video tutorial will show you how to take the initiative in a chess game to win.

Trying to eat healthy and lose weight when you're a foodie is hard. Because when it comes down to it, most good food (we're thinking sweet, salty, fried, and crispy) is essentially a heart attack in a box. But every now and then you find a recipe that's both delicious and relatively healthy.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

It feels like someone reached into your chest and squeezed. Your head throbs in unison with your heartbeat. Clammy dread coats your body in sweat. Whether you call 911 or someone does it for you, the ER is your next stop.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

When Penguins Attack - TD hacks, cheats, glitches. How to hack the flash game When Penguins Attack - TD. Defend the human race against the onslaught of evil penguins. Watch this video tutorial to learn how to hack When Penguins Attack - TD with Cheat Engine (09/27/09).