It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

While not cuddly to most, bats are shy, skilled flyers that fill an important role in their environments. A new study reveals a deadly disease decimating North American bat populations has stepped up its attack on vulnerable bat populations in the summer months.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Even before we are born, our immune system is hard at work. New research shows how the developing fetal immune system takes advantage of the time and opportunity of gestation — in the presence of mom's cells and tissues — to develop a sense of self.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Drug-resistant bacteria have made curing some infections challenging, if not nearly impossible. By 2050, it's estimated that 10 million people will be dying annually from infections with antibiotic-resistant organisms.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

One day, you may find yourself in an emergency situation where you need to undo the chain lock of your home's front door, or somebody else's front door. Maybe someone forgot the unlock it when exiting the back door. Maybe you're grandfather is having a heart attack. Maybe your wife is cheating on you. Whatever the reason, it's fairly simple to break in by undoing the chain lock.

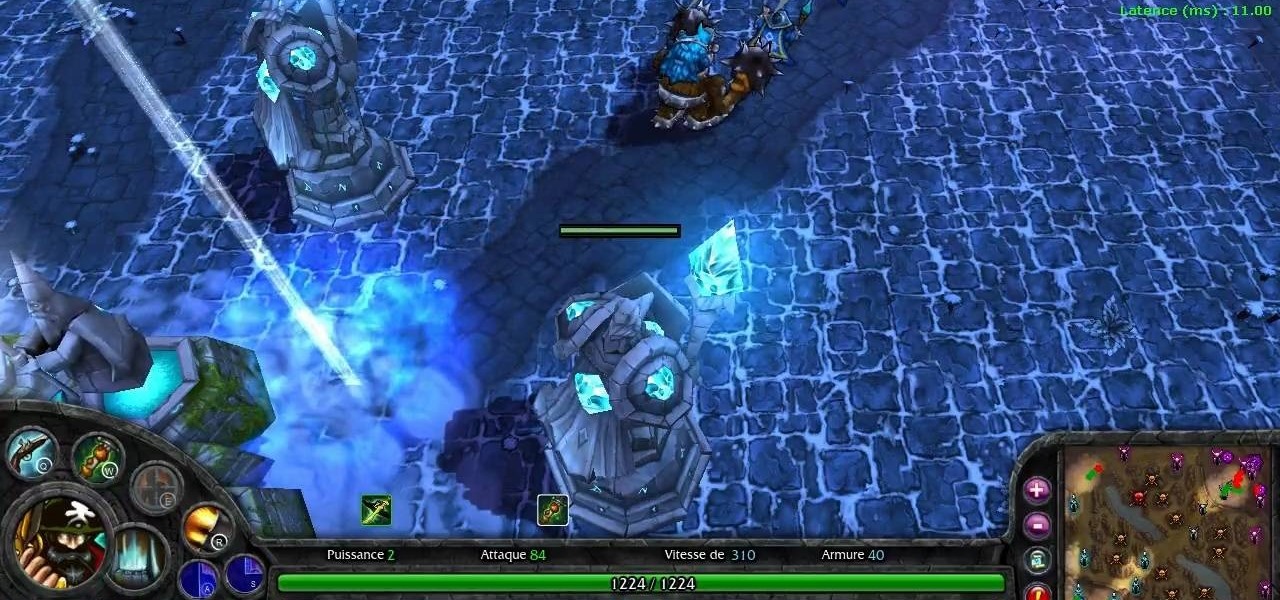
Minions are computer generated NPCs that spawn from the base nexus and attack enemies. You can't control your minions, but you can influence them by using smite and heal on them. Use your minions well and you'll win your games on the Fields of Justice!

In the City of Olympia, you'll find Helios. This is one hard battle Kratos must endure, and your want to get the Head of Helios. At first, Helios will be protected by a bunch of men with shields who you can't immediately attack. Once you win, you'll need to lay your hand over Helios to block out the sunlight. Watch the walkthrough for Helios's Head in God of War III on PS3.

In this video from nmsuaces we learn how to identify problems with weevils and leaf cutter bees. Weevils attack all kinds of plants in a J shape on leaves. To tell a difference between a weevil and leaf cutter bee is the bee will make a perfect round cut, whereas a weevil makes more of a J shape. If it starts doing serious damage you may need to control them. The weevil works at night. In this video she also discusses vines. A potato vine needs to be tied up as it grows. It's good for around ...

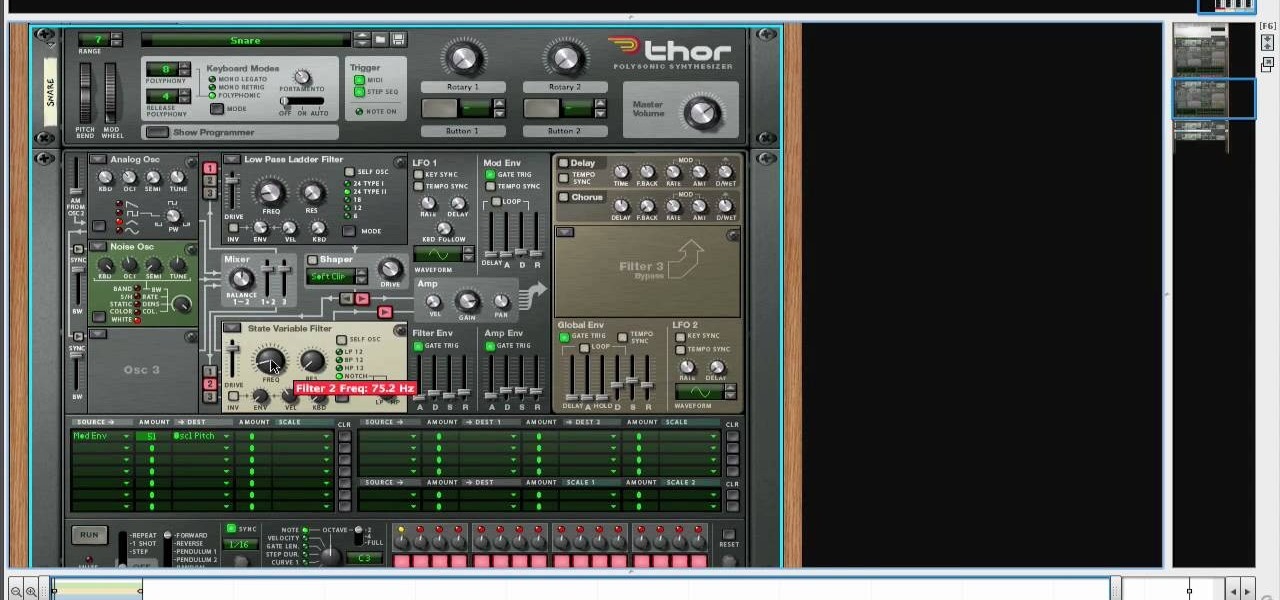
Create drums sounds using Reason's Thor synthesizerYou can use the Thor synthesizer to make a kick, snare, hat and clap sound.Kick:Use the analog oscillator with triple wave form octave3. Set the source to mod envelope 45 destination oscillator 1.Use a very short attack to K and release time. You get the short effect of pitch. Try different oscillator types to get different textures.Snare: Use the same basic patch that we created for the kick. We will keep it as the basis for most patches for...

Mark demonstrates how to draw flapping flags or scrolls. He starts with a paper in a binder but any paper will work. In this demonstration he uses a pencil to create his drawing but any pen or pencil will do. He draws the flagpole first starting on the left side of the page. He draws multiple circles creating cylinders that you may have learned how to draw in a previous lesion by Mark Kistler. He uses shading to create the effect of a curve and depth of the flag. He shows how to create the ef...

In its heyday the Atari gaming console was the Playstation of the 80s. Sure, you could download some wannabe emulator, but why not go a step further and purchase an actual Atari. They're still floating around and just think how cool it'll be to play pong in hi-definition.

Fighting Straga is the main boss fight In the Xbox 360 game Darksiders - The Black Throne. Can you beat him? Quickly shoot a portal onto one of the floor stations in front of Straga. Watch his mace carefully and you'll see another orange portal point on the side of it. Shoot a second portal onto the mace then wait for Straga to raise the mace back behind his head. When he does this, drop through the portal you made on the ground so your pop out of the portal on his mace and land on the platfo...

Get ready for car throwing in this Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

This Shadow Arena Challenge isn't the easiest in the Choking Ground on the Xbox 360 game Darksiders. Meet the requirements of each portal to free the Tormented Gate so that you may proceed.

Keep your crossblade near for this level of the Xbox 360 game Darksiders, In the sub-boss fight in Twilight Cathedral - The Jailor, make sure to target the sores. This grotesque monstrosity towers over War. It is almost as wide as it is tall. You'll want to keep your distance from the Jailer as it has a powerful attack in which it slams the cage it carries onto the ground. You'll want to spend most of you time here with the monster targeted while you backpedal away from it. The biggest annoya...

In this level on the Xbox 360 game Bayonetta, make sure the bullet enters Balder's head. In Chapter 16 - The Lumen Sage, keep that bullet in line. Father Balder doesn't do much damage, but he tends to stay out of range. When you do have him in range do as much damage as you can. Keep fighting until you get his health meter down to zero and can do a climax attack. For more info, watch the whole gameplay.

Defeat Iustitia in this installment for the Xbox 360 game Bayonetta. In Chapter 11 - The Cardinal Virtue of Justice, attack the tongue. The first part of this fight is against one Ardor and a bunch of smaller enemies. After defeating them you'll see another cinematic and face the boss named Iustitia.

Fight Enchant Angels, Trash Mobs, and Fortitudo in the Xbox 360 game Bayonetta. In Chapter 2 - Vigrid, City of Deja Vu, it's time to shine as one mean mama-san. In the first battle you can walk on walls. To get back to the floor quickly press down on the left stick while jumping. Because this fight takes place on six different surfaces it can sometimes be hard to locate Jeanne (your opponent). If you don't know where she is, just shoot her. Your guns don't do any damage, but you will see wher...

Right off the bat you have a horrendously hard battle against Straga in the Xbox 360 game Darksiders. The Prologue battle with Straga is difficult, unless you have your car throwing skills down. Straga is a massive demon that looms over the streets and War. During the battle, hold the Focus Button to keep the camera locked on this massive creature which also gives you a nice wide perspective so you can really see your surroundings. You'll want to get used to using the Dash Button to dart left...