Backpacker magazine associate editors Jason Stevenson and Shannon Davis demonstrate how to estimate your VO2 Max in this April 2007 SkillsCast. Find out how a simple running test can determine your VO2 Max, and why raising your score can make you a better backpacker, increase your endurance and fitness level.

Backpacker editor-in-chief Jon Dorn explains 5 field-tested techniques for eliminating the three main causes of blisters: heat, moisture, and friction. Learn more from Backpacker's Gear School in the March 2007 Gear Guide, and at www.backpacker.com/video.

It is argued that sun exposure and warm weather helps people cope with and fight multiple sclerosis. Sun is important to produce vitamin D. There are arguments that vitamin D deficiency is connected with cases of multiple sclerosis. Get a blood test to make sure your vitamin levels are optimum and you are suffering from no mineral or vitamin toxicity.

See how much tar and smoke stuff goes into your lungs when you inhale just one cigarette. This is brought to you by an ex smoker who lost his larynx.

Oscilloscopes visualize electronic signals. This information can be useful for tests, debugging, and reverse engineering. If you work with electronic circuitry, being able to use an oscilloscope is a must have skill. Here Bre Pettis and Make Magazine hook you up with great tips.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Though Microsoft has had trouble keeping up with the demand for HoloLens 2, the company has been able to supply modified headsets to the US Army.

Less than a month after the worldwide launch of HoloLens 2, call center consultant BellSystem24 has already prepared an augmented reality solution for one of its clients.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

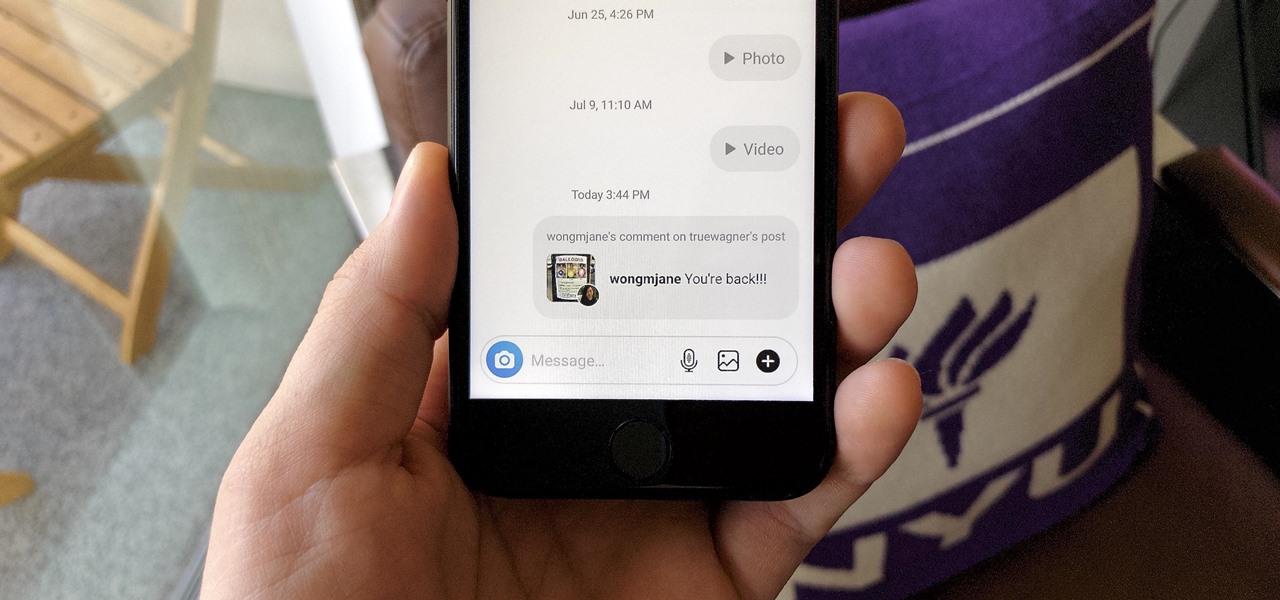
Sometimes, you'll see a comment on Instagram that you really need to share. Maybe it's something funny, possibly offensive. Whatever the case, the only thing to do is screenshot it and share that, right? Hopefully, not for long. Instagram is currently testing a feature that would allow you to share comments with others via a direct message and maybe even to stories and other apps.

Fresh off of shipping version 2019.1 in April, Unity has already dropped the beta of 2019.2, and it has a bunch of new AR Foundation toys to test.

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

Among all the new Magic Leap app announcements made at the recent L.E.A.P. conference, an update to one of the company's major in-house apps went mostly unnoticed: Create 1.1.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Magic Leap and AT&T have lifted the lid on multiple parts of their mysterious relationship today. According to AT&T Communications CEO John Donovan, the company is planning to launch a beta version of DirectTV Now for the Magic Leap One in 2019.

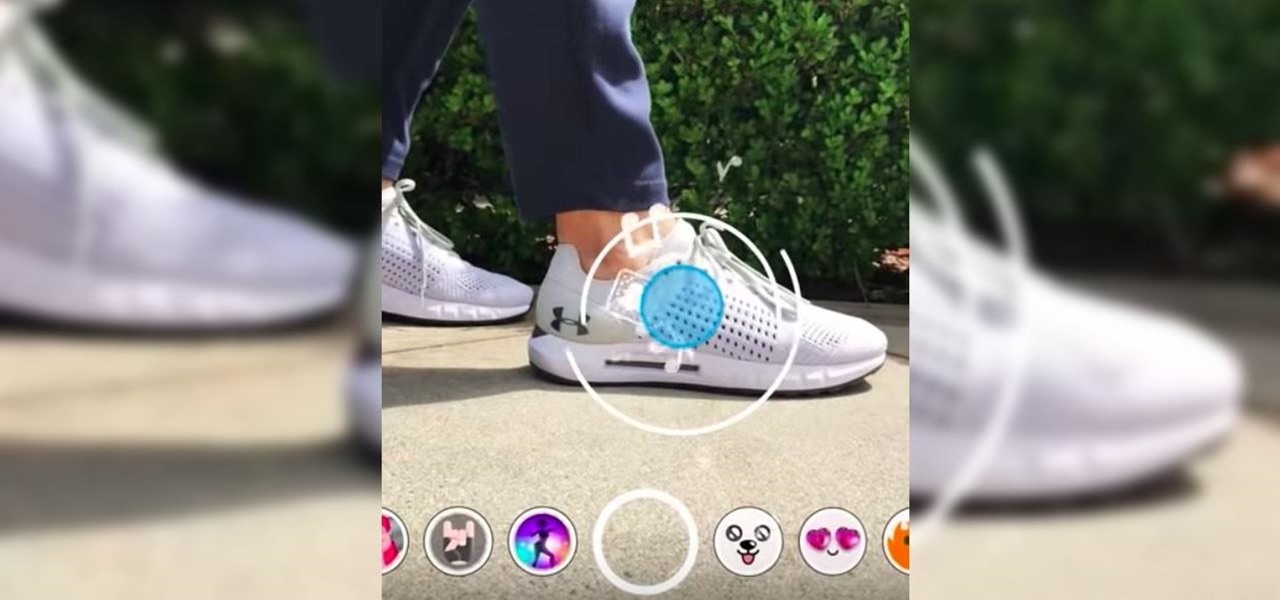
Snapchat has officially unveiled its Visual Search service for Amazon (teased a month ago), a tool the company began testing on Monday.

In the tech world, upgrades are normally a good thing. On iOS, it means bug fixes and security patches that protect your iPhone and keep it up with the times. In the jailbreak world, however, upgrades can mean certain death, as we are reminded today when Apple stopped signing iOS 11.4. That means if you upgrade to 11.4.1, you will no longer be able to jailbreak your iPhone.

Magic Leap just did something it didn't do during its recent Twitch hardware demo: show us some new demo footage of what augmented reality really looks like through the Magic Leap One.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

The Tesla-riding Starman that was launched into space via Elon Musk's SpaceX last week will miss its Mars target and is instead headed toward a lonely asteroid belt in the void of space. But if you missed the initial launch and would like to get a taste of what Starman is seeing, you can now take a short ride along thanks to a new Snapchat Lens.

Last month, BMW rolled out its playful take on augmented reality with Snapchat, and now the automaker is bringing that same immersive computing whimsy to iOS directly.

Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

"Valar morghulis." Don't know what that means? You should probably download Duolingo for Android or iPhone.

A spokesperson from the Nissan and Renault Alliance told Driverless the group is testing self-driving electric "robo-vehicles" for future mobility services and is "not ruling out anything" for future services the group might offer, as the alliance widens its driverless business model to include both fleets and private sales.

General Motors (GM) has begun production of 130 Chevrolet Bolt EV driverless test vehicles at its Orion Township, Mich. plant as it expands its fleet to total 180 models deployed in San Francisco; Scottsdale, Arizona; and Detroit.

Las Vegas is known as the city of sin, a place for gambling, fine dining, and decadence. Now, you can add another notable characteristic to that list: West Nile. You may want to hold off on scheduling your trip to the Sin City — or at least stock up on bug spray — because health officials have reported that mosquitoes in Southern Nevada have tested positive for the virus.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Online lives could be made easier now that Facebook, Instagram, and Messenger are testing merged app notifications. 'Could' being the operative word!

In a video released Tuesday, Microsoft arguably began to position the HoloLens and Windows Mixed Reality as the future of education. A smart tactic meant to coincide with their other education-related announcements made on the same day.

The Galaxy S8, with all its new features, is shining in the news right now as one of the best phones of the year. However, users in the US may be at a disadvantage to those overseas, as it seems that the Snapdragon 835-powered S8 models underperform variants with Exynos processors in almost every category.

It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

Lyft is experimenting with commuter ride sharing by debuting a new "Shuttle" option, which offers pickups and drop-offs along select routes, much like a metro bus would do. The company is trying out the new option in San Francisco and Chicago, but if all goes well, we might all be ordering a pickup soon through Lyft's new Line ride share option.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

The OnePlus 3T was released about five months after the OnePlus 3 with several noticeable upgrades. Firstly, it has a new processor, the Qualcomm Snapdragon 821, which is the same one that the Pixel and Pixel XL sport. Second is the 16 MP front-facing camera with a different sensor. And the next big change was a slightly larger 3,400 mAh capacity battery.

Walking while taking a video is always a pain. But it doesn't have to be, especially with Google's new Pixel smartphone and its new and improved Electronic Image Stabilization (EIS) feature. A new video, released on Reddit, pitted the Pixel's EIS against the Nexus 6P with some incredible results.

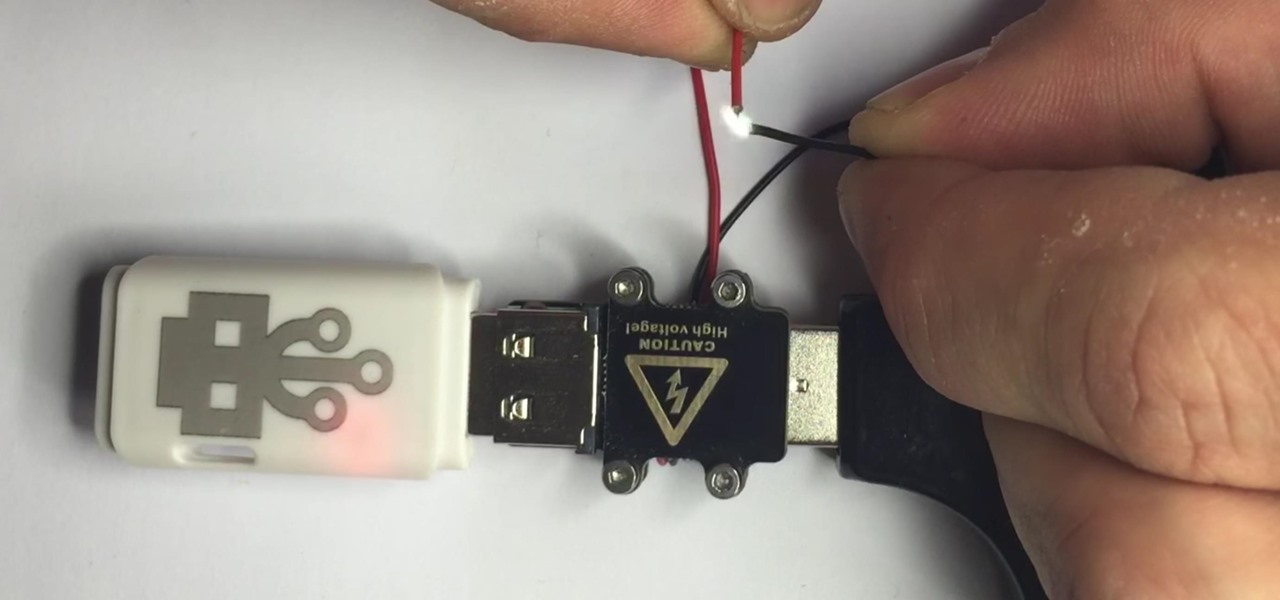
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!