
Test Recognizing Search Results

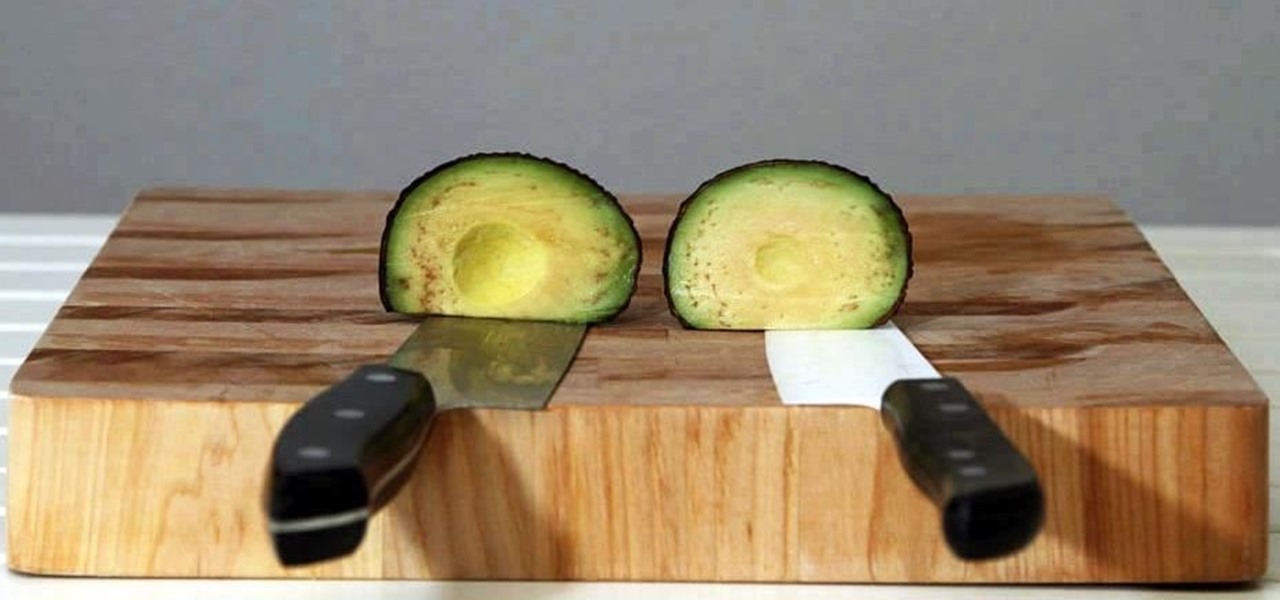
How To: Reduce Browning in Avocados & Other Fruits by Switching Your Knives
Keeping apples or avocados from browning after being cut is impossible; within minutes of being exposed to air, these fruits (yes, avocado is a fruit) begin to brown. No matter what you try—adding lemon juice, keeping the pits in place, immediately sealing the produce in an airtight bag—brown discoloration always occurs. However, air is not the only reason that foods like apples, avocados, and lettuce brown: it's also due to the knife you're using.
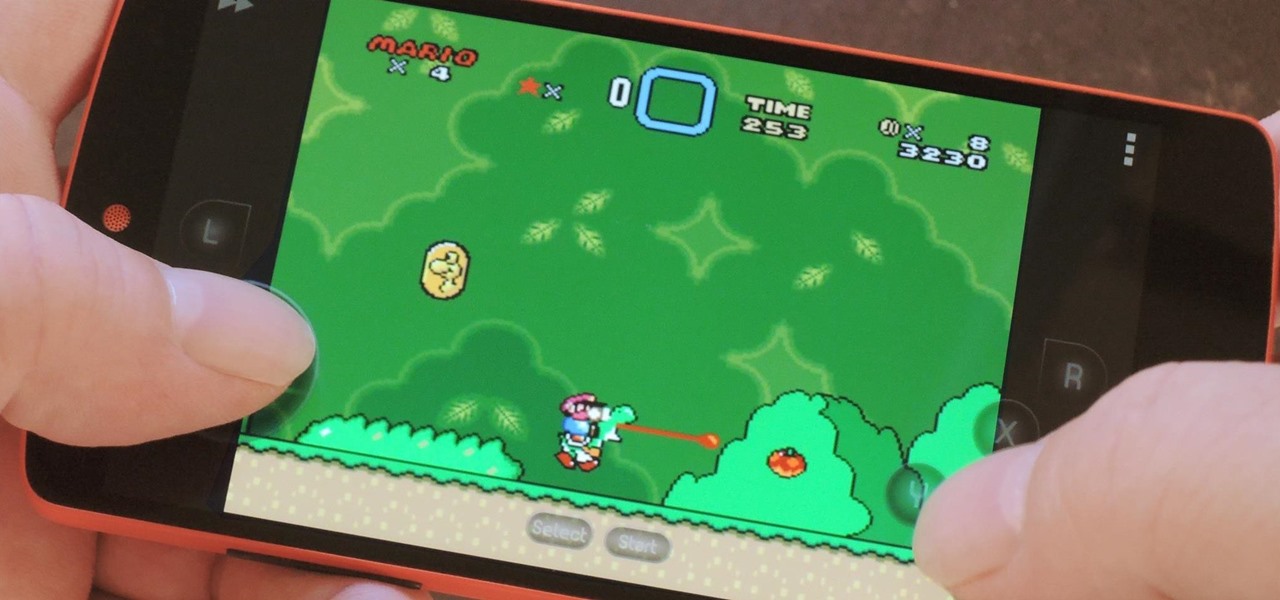
How To: The Ultimate Guide to Playing Classic Video Games on Android
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

How To: This Is Why Your TSA-Approved Luggage Locks Are Useless
Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

How To: Build a DNS Packet Sniffer with Scapy and Python
In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

Hack Like a Pro: How to Build Your Own Exploits, Part 3 (Fuzzing with Spike to Find Overflows)
Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

How To: Make a Locked File Cracker with Python
Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

How To: Build an ARP Scanner Using Scapy and Python
As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

How To: Links to Help You Hacking
This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

How To: Crack Any Master Combination Lock in 8 Tries or Less Using This Calculator
Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

Hack Like a Pro: How to Anonymously Torrent Files with Tribler
Welcome back, my nascent hackers!

How To: Speed Up the Stock TouchWiz Launcher on Your Galaxy Note 3
Does your Samsung Galaxy Note 3 feel slower than it used to? Background processes, cached files, malicious applications, and buggy updates can all lead to a sluggish smartphone. It's just what happens over time.
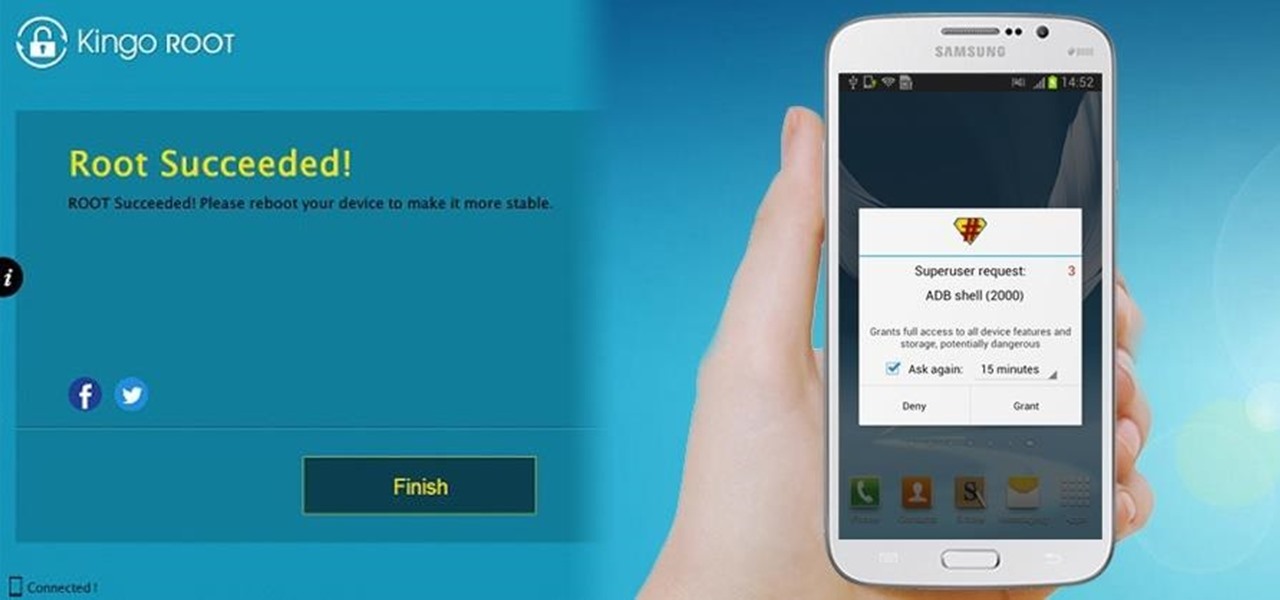
How To: 1-Click Root Many Android Devices with Kingo Android Root
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experience when rooting your Android.

How To: Enable the Hidden Notification LED on Your Nexus 6
The Nexus 6 uses an Ambient Display notification system that was heavily inspired by the Active Display feature on the Moto X. Essentially, the device shows a black-and-white version of the lock screen whenever you receive a new notification or pick the phone up. This is all made possible by the N6's AMOLED display that doesn't have to waste any battery to power black pixels on the screen.

How To: 5 Ways You're Making Yourself Dumber
No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

How To: Install Flash on Any Kindle Fire
With so much Flash content still available on the web, it's unfortunate that Google no longer supports mobile Flash Player on Android. Loading a webpage only to be met with a "Plug-in Error" is never fun, and it can inhibit your mobile browsing experience as you attempt to watch a video or play an addicting Flash game.
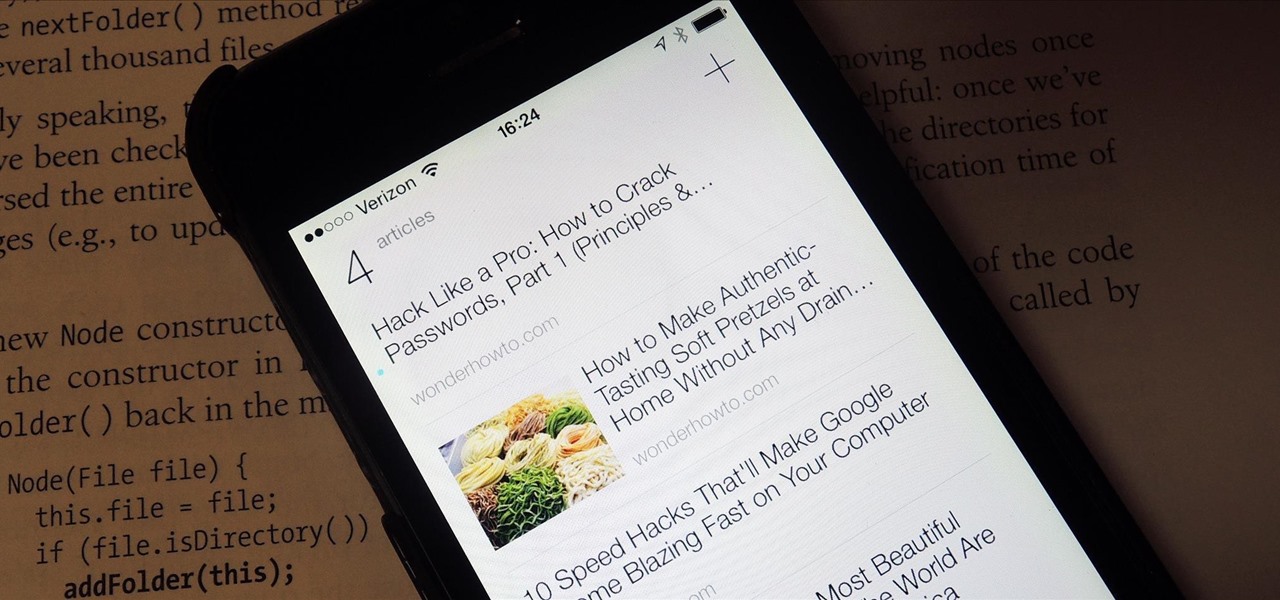
How To: Taking Screenshots Is the Fastest Way to Save Full Web Articles for Offline Reading on Your iPhone
With just a swipe and tap of a finger, we can access enormous libraries of information on our smartphones like never before. Whether we want more info about gluten sensitivity or just want to brush up on 18th century philosophers, there's an article somewhere in the vast ocean of the internet that can lend us a hand.
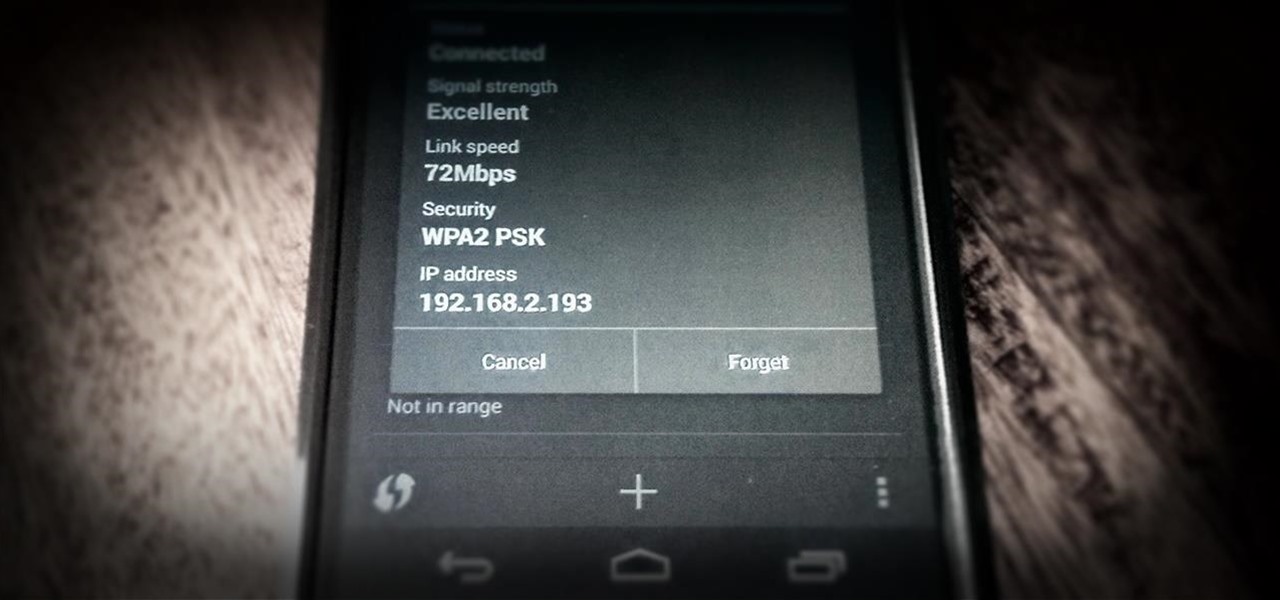
How To: Improve Wi-Fi Performance on Your Rooted Nexus 4
One of the most common complaints that people have about the Nexus 4 would have to be its intermittently poor Wi-Fi performance, a problem that for many, persists through the installation of updates and even custom ROMs.

How To: Get LG's "Knock Code" Feature on Your Galaxy S3 for Increased Lock Screen Security
LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!
How To: Turn Your Android Phone into a Personal Distress Beacon with Motorola's "Exclusive" Alert App
Loving parents can suffer bouts of insomnia when their children leave the house. Not just when they move out, but when hanging out with friends or during out-of-town weekends. Others may worry about their significant other who has to work late all week and their only option for getting home is that sketchy nighttime bus.
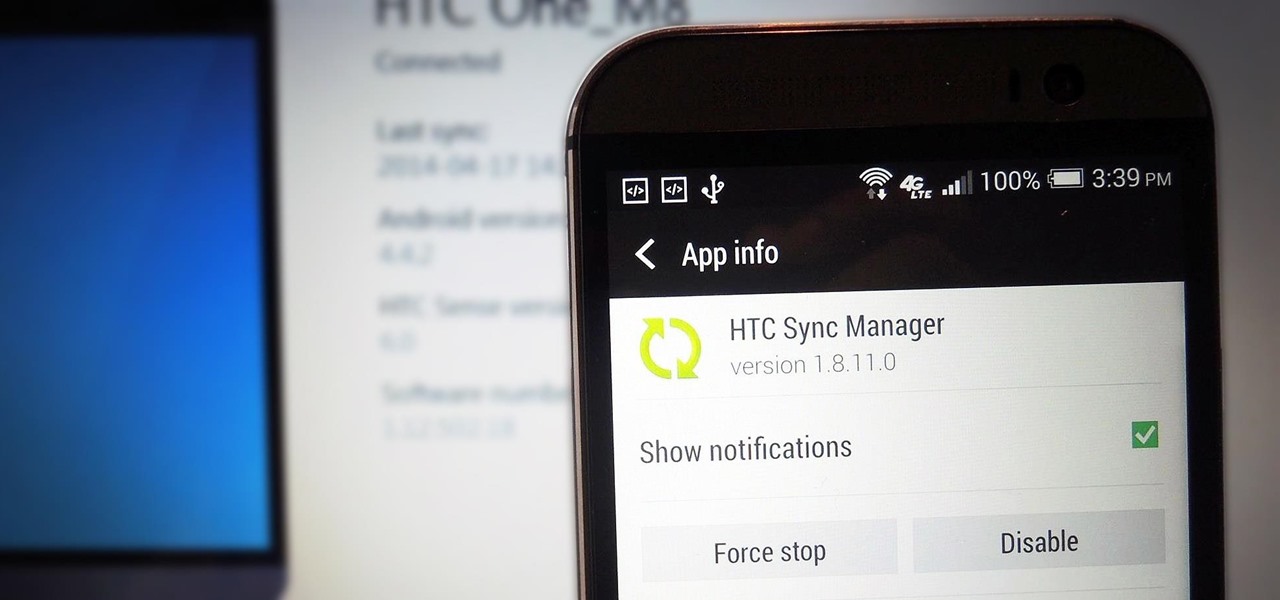
How To: The Easiest Way to Back Up, Restore, & Sync Files Between Your Computer & HTC One
If you've just upgraded to an HTC One M8, chances are you've got some media files you want transferred over from your computer or previous phone. Even after you've done that, there will be times when you want to transfer content back to your computer for safe keeping.

Hack Like a Pro: How to Fingerprint Web Servers Using Httprint
Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Hack Like a Pro: Scripting for the Aspiring Hacker, Part 3 (Windows PowerShell)
Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

How To: Prevent Friends from Snooping Through Your Galaxy S3 When Showing Them a Photo
If you have friends like mine, letting them check out one photo on your phone means they're going to check out all of the photos on your phone. Before you realize what they're doing, it's too late, and they're sending out perverted emails to your coworkers, making you look like a newb at Candy Crush Saga, and viewing your Snapchats for you.

How To: Forward Missed Call Alerts & Text Messages on Your Samsung Galaxy S3 to an Email Address
There are some calls you really don't want to miss. Whether it's "I'm going into labor" or "We have some questions about your résumé," not being able to answer or respond to certain messages can cause some serious problems.

How To: 8 Nerdy Halloween Costumes That Even the Geekiest of Geeks Wouldn't Touch
Nerds get a bad rap most of the time, but on Halloween, everyone wants to be one. However, not everyone knows how to geek it out without going too far. There is a limit, even for nerds, and these eight Halloween costumes are nerdy times pi.
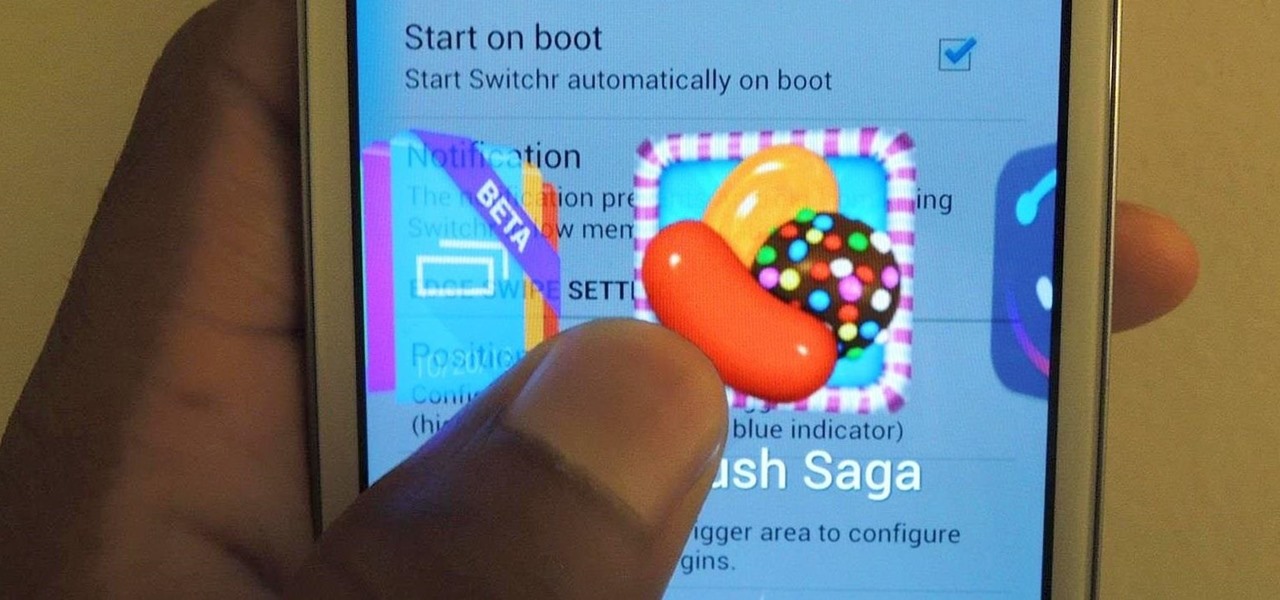
How To: Switch Between Running Apps on Your Samsung Galaxy S3 Without Ever Lifting a Finger
I've covered a few multitasking app switchers before, but none of them are as sleek and smooth as the aptly titled Switchr, a new app developed by Mohammad Adib that lets you move from one app to another quickly and smoothly—just like how I switch between my women. Well, not really, but I would.
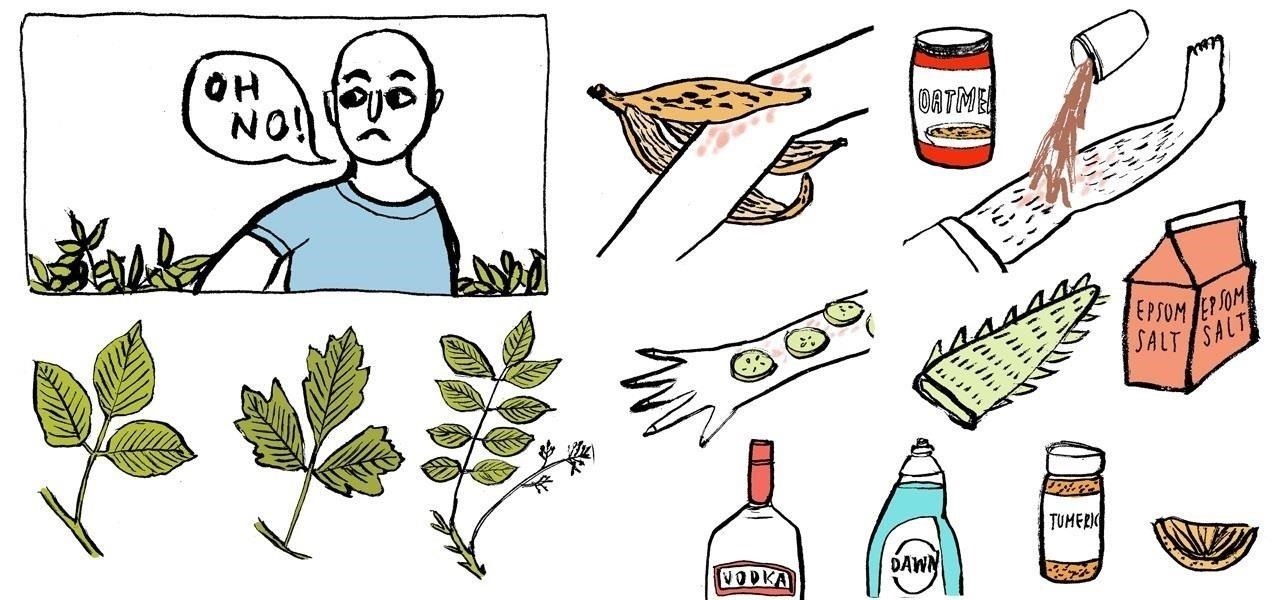
How To: 16 Home Remedies for Treating Poison Ivy, Oak & Sumac Rashes
Poison ivy, poison oak, and the lesser known skin irritator, poison sumac, can all cause a conundrum in the search of itch relief: to scratch or not to scratch. Fortunately, there are a number of home remedies one can try to help alleviate the itch(ing), with many like coffee, a banana, baking soda, or mouthwash likely already in-house for most.

How to Hack Wi-Fi: Cracking WEP Passwords with Aircrack-Ng
Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

How To: Save Battery Power on a Samsung Galaxy S4 with Moto X Style "Active Display" Notifications
According to a new study, the majority of smartphone users check their devices 150 times a day. While that number may seem incredibly high at first glance, the influx of notifications and amount of social media apps available reduce the initial shock and make the number seem not so preposterous after all. Yeah, even on a date.

How To: Easily Access Your Camera from the Lock Screen on Your Samsung Galaxy Note 2
The transition from an iPhone to a Samsung Galaxy Note 2 or other Android device can be a tough one. A vastly different operating system and the ability to customize anything and everything might be too much for some people. Taking in all that new, while having to let go of the old, can be as daunting as climbing Mount Everest.
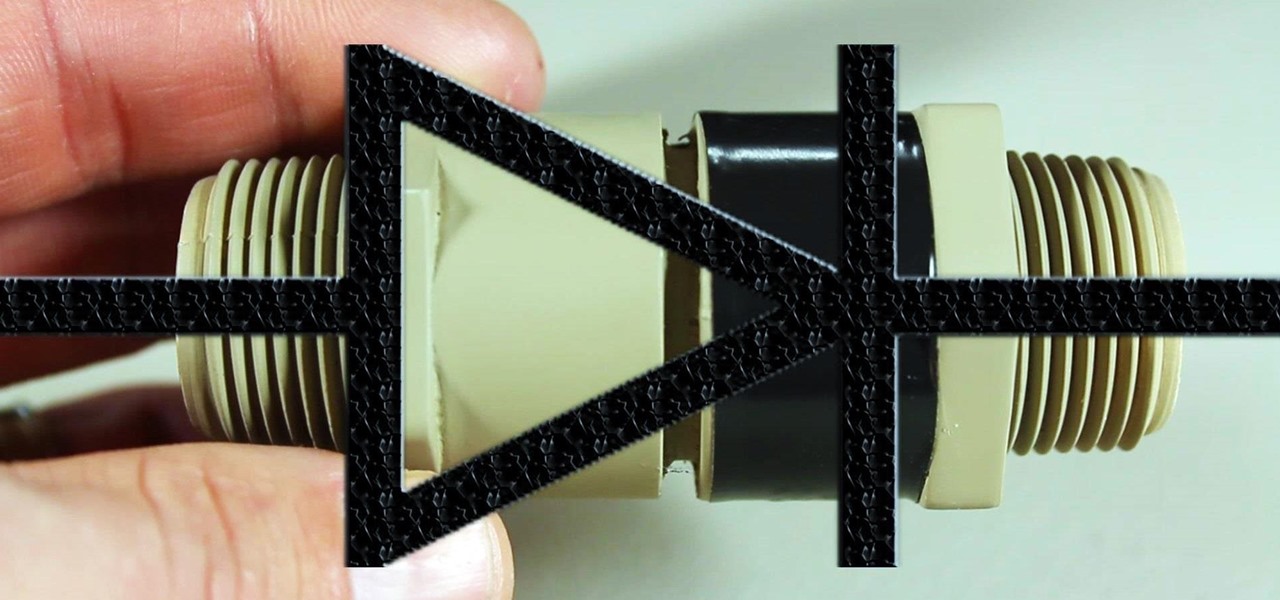
How To: Make a Super Cheap One-Way Check Valve
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.

How To: The Best Investigatory Projects in Science: 16 Fun & Easy Ideas to Kickstart Your Project
Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

How To: Download & Play Game Boy Advance ROMs on Your iPad or iPhone—No Jailbreak Required
If you want to play games that aren't in the iOS App Store, Apple makes it pretty tough for you. Usually, the only solution is to jailbreak your iPad or iPhone, but that's something most avoid because it will void the warranty and may cause potential bricking issues.

How To: DIY Stick Welder from Old Microwave Parts
Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

Hack Like a Pro: How to Remotely Install an Auto-Reconnecting Persistent Back Door on Someone's PC
Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.
How To: Get Unlimited Free Trial Subscriptions to Netflix, Spotify, and More Using Gmail
Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

Beat Box Office Prices: How to Save Money on Movie Tickets
The cost of movie tickets in North America are currently at an all-time high, but with so many great films coming out, just not going doesn't seem like a probable option. Luckily, there's more than a few resources on the Internet to help you mitigate some of those costs.

How To: Turn Water into Fuel by Building This DIY Oxyhydrogen Generator
Here's how to build a sexy looking water-fuel generator that will convert your tap water into an extremely powerful, clean burning gas!

How To: Turn Your Spare Pocket Change into DIY Batteries with This Penny Power Hack
What's a penny worth these days? Not much. But could there be some free energy hidden inside your spare pennies? You'd be surprised! See how I hack together stacks of pennies into makeshift batteries that can drive small-current devices like LEDs and calculators.

